Azure VMware Solution identity concepts
Azure VMware Solution private clouds are provisioned with a vCenter Server and NSX Manager. You use vCenter Server to manage virtual machine (VM) workloads and NSX Manager to manage and extend the private cloud. The CloudAdmin role is used for vCenter Server and the CloudAdmin role (with restricted permissions) is used for NSX Manager.
vCenter Server access and identity
In Azure VMware Solution, VMware vCenter Server has a built-in local user account called CloudAdmin that's assigned the CloudAdmin role. You can configure users and groups in Windows Server Active Directory with the CloudAdmin role for your private cloud. In general, the CloudAdmin role creates and manages workloads in your private cloud. But in Azure VMware Solution, the CloudAdmin role has vCenter Server privileges that are different from other VMware cloud solutions and on-premises deployments.
Important
The local CloudAdmin user account should be used as an emergency access account for "break glass" scenarios in your private cloud. It's not intended to be used for daily administrative activities or for integration with other services.
In a vCenter Server and ESXi on-premises deployment, the administrator has access to the vCenter Server administrator@vsphere.local account and the ESXi root account. The administrator might also be assigned to more Windows Server Active Directory users and groups.
In an Azure VMware Solution deployment, the administrator doesn't have access to the Administrator user account or the ESXi root account. But the administrator can assign Windows Server Active Directory users and groups the CloudAdmin role in vCenter Server. The CloudAdmin role doesn't have permissions to add an identity source like an on-premises Lightweight Directory Access Protocol (LDAP) or Secure LDAP (LDAPS) server to vCenter Server. However, you can use Run commands to add an identity source and assign the CloudAdmin role to users and groups.
A user account in a private cloud can't access or manage specific management components that Microsoft supports and manages. Examples include clusters, hosts, datastores, and distributed virtual switches.
Note
In Azure VMware Solution, the vsphere.local single sign-on (SSO) domain is provided as a managed resource to support platform operations. You can't use it to create or manage local groups and users except for the ones that are provided by default with your private cloud.
Important
Azure VMware Solution offers custom roles on vCenter Server but currently doesn't offer them on the Azure VMware Solution portal. For more information, see the Create custom roles on vCenter Server section later in this article.
View the vCenter Server privileges
Use the following steps to view the privileges granted to the Azure VMware Solution CloudAdmin role on your Azure VMware Solution private cloud vCenter.
Sign in to the vSphere Client and go to Menu > Administration.
Under Access Control, select Roles.
From the list of roles, select CloudAdmin and then select Privileges.
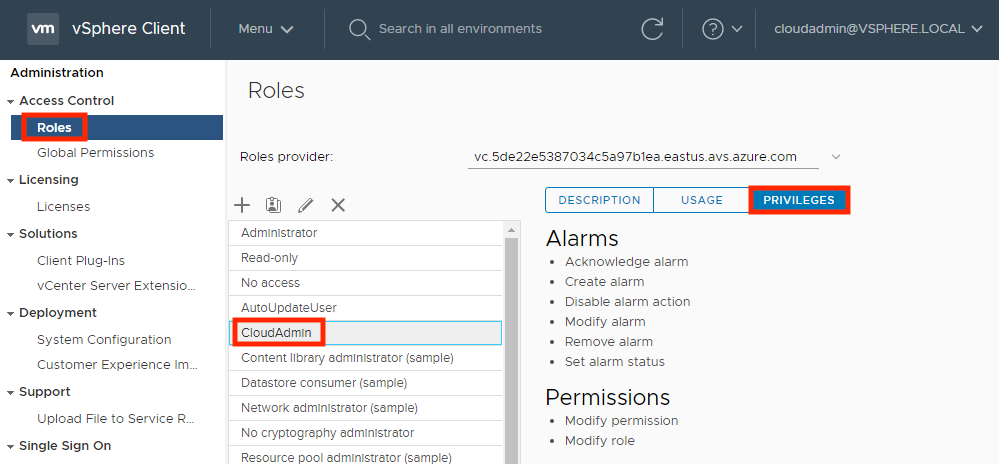
The CloudAdmin role in Azure VMware Solution has the following privileges on vCenter Server. For more information, see the VMware product documentation.
| Privilege | Description |
|---|---|
| Alarms | Acknowledge alarm Create alarm Disable alarm action Modify alarm Remove alarm Set alarm status |
| Content Library | Add library item Add root certificate to trust store Check in a template Check out a template Create a subscription for a published library Create local library Create or delete a Harbor registry Create subscribed library Create, delete or purge a Harbor registry project Delete library item Delete local library Delete root certificate from trust store Delete subscribed library Delete subscription of a published library Download files Evict library items Evict subscribed library Import storage Manage Harbor registry resources on specified compute resource Probe subscription information Publish a library item to its subscribers Publish a library to its subscribers Read storage Sync library item Sync subscribed library Type introspection Update configuration settings Update files Update library Update library item Update local library Update subscribed library Update subscription of a published library View configuration settings |
| Cryptographic operations | Direct access |
| Datastore | Allocate space Browse datastore Configure datastore Low-level file operations Remove files Update virtual machine metadata |
| Folder | Create folder Delete folder Move folder Rename folder |
| Global | Cancel task Global tag Health Log event Manage custom attributes Service managers Set custom attribute System tag |
| Host | vSphere Replication Manage replication |
| Network | Assign network |
| Permissions | Modify permissions Modify role |
| Profile Driven Storage | Profile driven storage view |
| Resource | Apply recommendation Assign vApp to resource pool Assign virtual machine to resource pool Create resource pool Migrate powered off virtual machine Migrate powered on virtual machine Modify resource pool Move resource pool Query vMotion Remove resource pool Rename resource pool |
| Scheduled task | Create task Modify task Remove task Run task |
| Sessions | Message Validate session |
| Storage view | View |
| vApp | Add virtual machine Assign resource pool Assign vApp Clone Create Delete Export Import Move Power off Power on Rename Suspend Unregister View OVF environment vApp application configuration vApp instance configuration vApp managedBy configuration vApp resource configuration |
| Virtual machine | Change Configuration Acquire disk lease Add existing disk Add new disk Add or remove device Advanced configuration Change CPU count Change memory Change settings Change swapfile placement Change resource Configure host USB device Configure raw device Configure managedBy Display connection settings Extend virtual disk Modify device settings Query fault tolerance compatibility Query unowned files Reload from paths Remove disk Rename Reset guest information Set annotation Toggle disk change tracking Toggle fork parent Upgrade virtual machine compatibility Edit inventory Create from existing Create new Move Register Remove Unregister Guest operations Guest operation alias modification Guest operation alias query Guest operation modifications Guest operation program execution Guest operation queries Interaction Answer question Back up operation on virtual machine Configure CD media Configure floppy media Connect devices Console interaction Create screenshot Defragment all disks Drag and drop Guest operating system management by VIX API Inject USB HID scan codes Install VMware tools Pause or Unpause Wipe or shrink operations Power off Power on Record session on virtual machine Replay session on virtual machine Reset Resume Fault Tolerance Suspend Suspend fault tolerance Test failover Test restart secondary VM Turn off fault tolerance Turn on fault tolerance Provisioning Allow disk access Allow file access Allow read-only disk access Allow virtual machine download Clone template Clone virtual machine Create template from virtual machine Customize guest Deploy template Mark as template Modify customization specification Promote disks Read customization specifications Service configuration Allow notifications Allow polling of global event notifications Manage service configuration Modify service configuration Query service configurations Read service configuration Snapshot management Create snapshot Remove snapshot Rename snapshot Revert snapshot vSphere Replication Configure replication Manage replication Monitor replication |
| vService | Create dependency Destroy dependency Reconfigure dependency configuration Update dependency |
| vSphere tagging | Assign and unassign vSphere tag Create vSphere tag Create vSphere tag category Delete vSphere tag Delete vSphere tag category Edit vSphere tag Edit vSphere tag category Modify UsedBy field for category Modify UsedBy field for tag |
Create custom roles on vCenter Server
Azure VMware Solution supports the use of custom roles with equal or lesser privileges than the CloudAdmin role. Use the CloudAdmin role to create, modify, or delete custom roles with privileges less than or equal to their current role.
Note
You can create roles with privileges greater than CloudAdmin. However, you can't assign the role to any users or groups or delete the role. Roles that have privileges greater than that of CloudAdmin is unsupported.
To prevent creating roles that can't be assigned or deleted, clone the CloudAdmin role as the basis for creating new custom roles.
Create a custom role
Sign in to vCenter Server with cloudadmin@vsphere.local or a user with the CloudAdmin role.
Navigate to the Roles configuration section and select Menu > Administration > Access Control > Roles.
Select the CloudAdmin role and select the Clone role action icon.
Note
Don't clone the Administrator role because you can't use it. Also, the custom role created can't be deleted by cloudadmin@vsphere.local.
Provide the name you want for the cloned role.
Remove privileges for the role and select OK. The cloned role is visible in the Roles list.
Apply a custom role
Navigate to the object that requires the added permission. For example, to apply permission to a folder, navigate to Menu > VMs and Templates > Folder Name.
Right-click the object and select Add Permission.
Select the Identity Source in the User drop-down where the group or user can be found.
Search for the user or group after selecting the Identity Source under the User section.
Select the role that you want to apply to the user or group.
Note
Attempting to apply a user or group to a role that has privileges greater than that of CloudAdmin will result in errors.
Check the Propagate to children if needed, and select OK. The added permission displays in the Permissions section.
VMware NSX Manager access and identity
When a private cloud is provisioned using Azure portal, software-defined data center (SDDC) management components like vCenter Server and VMware NSX Manager are provisioned for customers.
Microsoft is responsible for the lifecycle management of NSX appliances like, VMware NSX Manager and VMware NSX Edge appliances. They're responsible for bootstrapping network configuration, like creating the Tier-0 gateway.
You're responsible for VMware NSX software-defined networking (SDN) configuration, for example:
- Network segments
- Other Tier-1 gateways
- Distributed firewall rules
- Stateful services like gateway firewall
- Load balancer on Tier-1 gateways
You can access VMware NSX Manager using the built-in local user "cloudadmin" assigned to a custom role that gives limited privileges to a user to manage VMware NSX. While Microsoft manages the lifecycle of VMware NSX, certain operations aren't allowed by a user. Operations not allowed include editing the configuration of host and edge transport nodes or starting an upgrade. For new users, Azure VMware Solution deploys them with a specific set of permissions needed by that user. The purpose is to provide a clear separation of control between the Azure VMware Solution control plane configuration and Azure VMware Solution private cloud user.
For new private cloud deployments, VMware NSX access is provided with a built-in local user cloudadmin assigned to the cloudadmin role with a specific set of permissions to use VMware NSX functionality for workloads.
VMware NSX cloudadmin user permissions
The following permissions are assigned to the cloudadmin user in Azure VMware Solution NSX.
Note
VMware NSX cloudadmin user on Azure VMware Solution is not the same as the cloudadmin user mentioned in the VMware product documentation. The following permissions apply to the VMware NSX Policy API. Manager API functionality may be limited.
| Category | Type | Operation | Permission |
|---|---|---|---|
| Networking | Connectivity | Tier-0 Gateways Tier-1 Gateways Segments |
Read-only Full Access Full Access |
| Networking | Network Services | VPN NAT Load Balancing Forwarding Policy Statistics |
Full Access Full Access Full Access Read-only Full Access |
| Networking | IP Management | DNS DHCP IP Address Pools |
Full Access Full Access Full Access |
| Networking | Profiles | Full Access | |
| Security | East West Security | Distributed Firewall Distributed IDS and IPS Identity Firewall |
Full Access Full Access Full Access |
| Security | North South Security | Gateway Firewall URL Analysis |
Full Access Full Access |
| Security | Network Introspection | Read-only | |
| Security | Endpoint Protection | Read-only | |
| Security | Settings | Full Access | |
| Inventory | Full Access | ||
| Troubleshooting | IPFIX | Full Access | |
| Troubleshooting | Port Mirroring | Full Access | |
| Troubleshooting | Traceflow | Full Access | |
| System | Configuration Settings Settings Settings |
Identity firewall Users and Roles Certificate Management (Service Certificate only) User Interface Settings |
Full Access Full Access Full Access Full Access |
| System | All other | Read-only |
You can view the permissions granted to the Azure VMware Solution cloudadmin role on your Azure VMware Solution private cloud VMware NSX.
- Sign in to the NSX Manager.
- Navigate to Systems and locate Users and Roles.
- Select and expand the cloudadmin role, found under Roles.
- Select a category like, Networking or Security, to view the specific permissions.
Note
Private clouds created before June 2022 will switch from admin role to cloudadmin role. You'll receive a notification through Azure Service Health that includes the timeline of this change so you can change the NSX credentials you've used for other integration.
NSX LDAP integration for role-based access control (RBAC)
In an Azure VMware Solution deployment, the VMware NSX can be integrated with external LDAP directory service to add remote directory users or group, and assign them a VMware NSX RBAC role, like on-premises deployment. For more information on how to enable VMware NSX LDAP integration, see the VMware product documentation.
Unlike on-premises deployment, not all predefined NSX RBAC roles are supported with Azure VMware solution to keep Azure VMware Solution IaaS control plane config management separate from tenant network and security configuration. For more information, see the next section, Supported NSX RBAC roles.
Note
VMware NSX LDAP Integration is supported only with SDDC’s with VMware NSX “cloudadmin” user.
Supported and unsupported NSX RBAC roles
In an Azure VMware Solution deployment, the following VMware NSX predefined RBAC roles are supported with LDAP integration:
- Auditor
- Cloudadmin
- LB Admin
- LB Operator
- VPN Admin
- Network Operator
In an Azure VMware Solution deployment, the following VMware NSX predefined RBAC roles aren't supported with LDAP integration:
- Enterprise Admin
- Network Admin
- Security Admin
- NetX Partner Admin
- GI Partner Admin
You can create custom roles in NSX with permissions lesser than or equal to CloudAdmin role created by Microsoft. Following are examples on how to create a supported "Network Admin" and "Security Admin" role.
Note
Custom role creation will fail if you assign a permission not allowed by CloudAdmin role.
Create “AVS network admin” role
Use the following steps to create this custom role.
Navigate to System > Users and Roles > Roles.
Clone Network Admin and provide the name, AVS Network Admin.
Modify the following permissions to "Read Only" or "None" as seen in the Permission column in the following table.
Category Subcategory Feature Permission Networking Connectivity
Network ServicesTier-0 Gateways
Tier-0 Gateways > OSPF
Forwarding PolicyRead-only
None
NoneApply the changes and Save the Role.
Create “AVS security admin” role
Use the following steps to create this custom role.
Navigate to System > Users and Roles > Roles.
Clone Security Admin and provide the name, “AVS Security Admin”.
Modify the following permissions to "Read Only" or "None" as seen in the Permission column in the following table.
| Category | Subcategory | Feature | Permission |
|---|---|---|---|
| Networking | Network Services | Forwarding Policy | None |
| Security |
Network Introspection Endpoint Protection Settings |
Service profiles |
None None None |
- Apply the changes and Save the Role.
Note
The VMware NSX System > Identity Firewall AD configuration option isn't supported by the NSX custom role. The recommendation is to assign the Security Operator role to the user with the custom role to allow managing the Identity Firewall (IDFW) feature for that user.
Note
The VMware NSX Traceflow feature isn't supported by the VMware NSX custom role. The recommendation is to assign the Auditor role to the user along with the custom role to enable Traceflow feature for that user.
Note
VMware Aria Operations Automation integration with the NSX component of the Azure VMware Solution requires the “auditor” role to be added to the user with the NSX Manager cloudadmin role.
Next steps
Now that you've covered Azure VMware Solution access and identity concepts, you may want to learn about: