Create interactive reports with Azure Monitor workbooks
Azure workbooks are flexible canvas that you can use to analyze data and create rich, visual reports in the Azure portal. In workbooks, you can access multiple data sources across Azure. Combine workbooks into unified, interactive experiences.
Workbooks provide a rich set of capabilities for visualizing your Azure data. For detailed information about each visualization type, see the visualizations examples and documentation.
In Microsoft Defender for Cloud, you can access built-in workbooks to track your organization’s security posture. You can also build custom workbooks to view a wide range of data from Defender for Cloud or other supported data sources.
For pricing, see the pricing page.
Prerequisites
Required roles and permissions: To save a workbook, you must have at least Workbook Contributor permissions for the relevant resource group.
Cloud availability: ![]() Commercial clouds
Commercial clouds ![]() National (Azure Government, Microsoft Azure operated by 21Vianet)
National (Azure Government, Microsoft Azure operated by 21Vianet)
Use Defender for Cloud gallery workbooks
In Defender for Cloud, you can use integrated Azure workbooks functionality to build custom, interactive workbooks that display your security data. Defender for Cloud includes a workbooks gallery that has the following workbooks ready for you to customize:
- Coverage workbook: Track the coverage of Defender for Cloud plans and extensions across your environments and subscriptions.
- Secure Score Over Time workbook: Track your subscription scores and changes to recommendations for your resources.
- System Updates workbook: View missing system updates by resource, OS, severity, and more.
- Vulnerability Assessment Findings workbook: View the findings of vulnerability scans of your Azure resources.
- Compliance Over Time workbook: View the status of a subscription's compliance with regulatory standards or industry standards that you select.
- Active Alerts workbook: View active alerts by severity, type, tag, MITRE ATT&CK tactics, and location.
- Price Estimation workbook: View monthly, consolidated price estimations for plans in Defender for Cloud, based on the resource telemetry in your environment. The numbers are estimates that are based on retail prices and don't represent actual billing or invoice data.
- Governance workbook: Use the governance report in the governance rules settings to track progress of the rules that affect your organization.
- DevOps Security (preview) workbook: View a customizable foundation that helps you visualize the state of your DevOps posture for the connectors that you set up.
Along with built-in workbooks, you can find useful workbooks in the Community category. These workbooks are provided as-is and have no SLA or support. You can choose one of the provided workbooks or create your own workbook.

Tip
To customize any of the workbooks, select the Edit button. When you're done editing, select Save. The changes are saved in a new workbook.

Coverage workbook
If you enable Defender for Cloud across multiple subscriptions and environments (Azure, Amazon Web Services, and Google Cloud Platform), you might find it challenging to keep track of which plans are active. It's especially true if you have multiple subscriptions and environments.
The Coverage workbook helps you keep track of which Defender for Cloud plans are active in which parts of your environments. This workbook can help you ensure that your environments and subscriptions are fully protected. By having access to detailed coverage information, you can identify areas that might need more protection so that you can take action to address those areas.
In this workbook, you can select a subscription (or all subscriptions), and then view the following tabs:
- Additional information: Shows release notes and an explanation of each toggle.
- Relative coverage: Shows the percentage of subscriptions or connectors that have a specific Defender for Cloud plan enabled.
- Absolute coverage: Shows each plan's status per subscription.
- Detailed coverage: Shows additional settings that can be enabled or that must need to be enabled on relevant plans to get each plan's full value.
You also can select the Azure, Amazon Web Services, or Google Cloud Platform environment in each or all subscriptions to see which plans and extensions are enabled for the environments.
Secure Score Over Time workbook
The Secure Score Over Time workbook uses secure score data from your Log Analytics workspace. The data must be exported by using the continuous export tool as described in Set up continuous export for Defender for Cloud in the Azure portal.
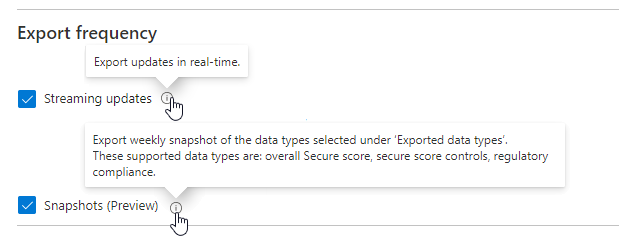
When you set up continuous export, under Export frequency, select both Streaming updates and Snapshots (Preview).
Note
Snapshots are exported weekly. There's a delay of at least one week after the first snapshot is exported before you can view data in the workbook.
Tip
To configure continuous export across your organization, use the provided DeployIfNotExist policies in Azure Policy that are described in Set up continuous export at scale.
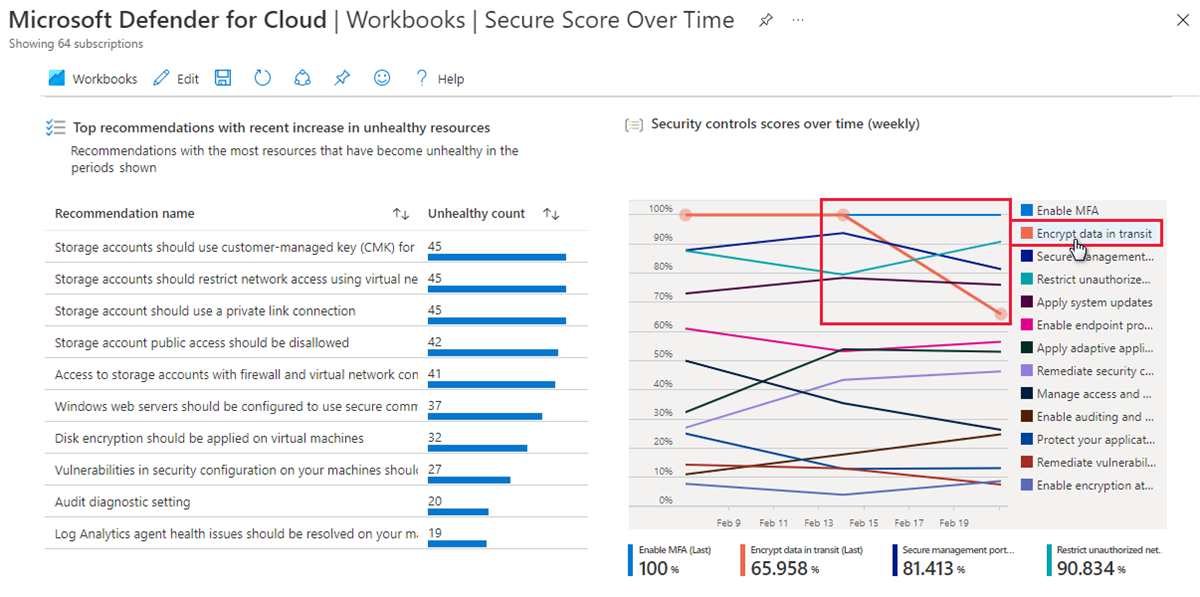
The Secure Score Over Time workbook has five graphs for the subscriptions that report to the selected workspaces:
| Graph | Example |
|---|---|
| Score trends for the last week and month Use this section to monitor the current score and general trends of the scores for your subscriptions. |

|
| Aggregated score for all selected subscriptions Hover your mouse over any point in the trend line to see the aggregated score at any date in the selected time range. |

|
| Recommendations with the most unhealthy resources This table helps you triage the recommendations that had the most resources that changed to an unhealthy status in the selected period. |

|
| Scores for specific security controls The security controls in Defender for Cloud are logical groupings of recommendations. This chart shows you at a glance the weekly scores for all your controls. |

|
| Resources changes Recommendations that have the most resources that changed state (healthy, unhealthy, or not applicable) during the selected period are listed here. Select any recommendation in the list to open a new table that lists the specific resources. |

|
System Updates workbook
The System Updates workbook is based on the security recommendation that system updates should be installed on your machines. The workbook helps you identify machines that have updates to apply.
You can view the update status for selected subscriptions by:
- A list of resources that have outstanding updates to apply.
- A list of updates that are missing from your resources.

Vulnerability Assessment Findings workbook
Defender for Cloud includes vulnerability scanners for your machines, containers in container registries, and computers running SQL Server.
Learn more about using these scanners:
- Find vulnerabilities with Microsoft Defender Vulnerability Management
- Scan your SQL resources for vulnerabilities
Findings for each resource type are reported in separate recommendations:
- Vulnerabilities in your virtual machines should be remediated (includes findings from Microsoft Defender Vulnerability Management, the integrated Qualys scanner, and any configured BYOL VA solutions)
- Container registry images should have vulnerability findings resolved
- SQL databases should have vulnerability findings resolved
- SQL servers on machines should have vulnerability findings resolved
The Vulnerability Assessment Findings workbook gathers these findings and organizes them by severity, resource type, and category.

Compliance Over Time workbook
Microsoft Defender for Cloud continually compares the configuration of your resources with requirements in industry standards, regulations, and benchmarks. Built-in standards include NIST SP 800-53, SWIFT CSP CSCF v2020, Canada Federal PBMM, HIPAA HITRUST, and more. You can select standards that are relevant to your organization by using the regulatory compliance dashboard. Learn more in Customize the set of standards in your regulatory compliance dashboard.
The Compliance Over Time workbook tracks your compliance status over time by using the various standards that you add to your dashboard.

When you select a standard from the overview area of the report, the lower pane displays a more detailed breakdown:
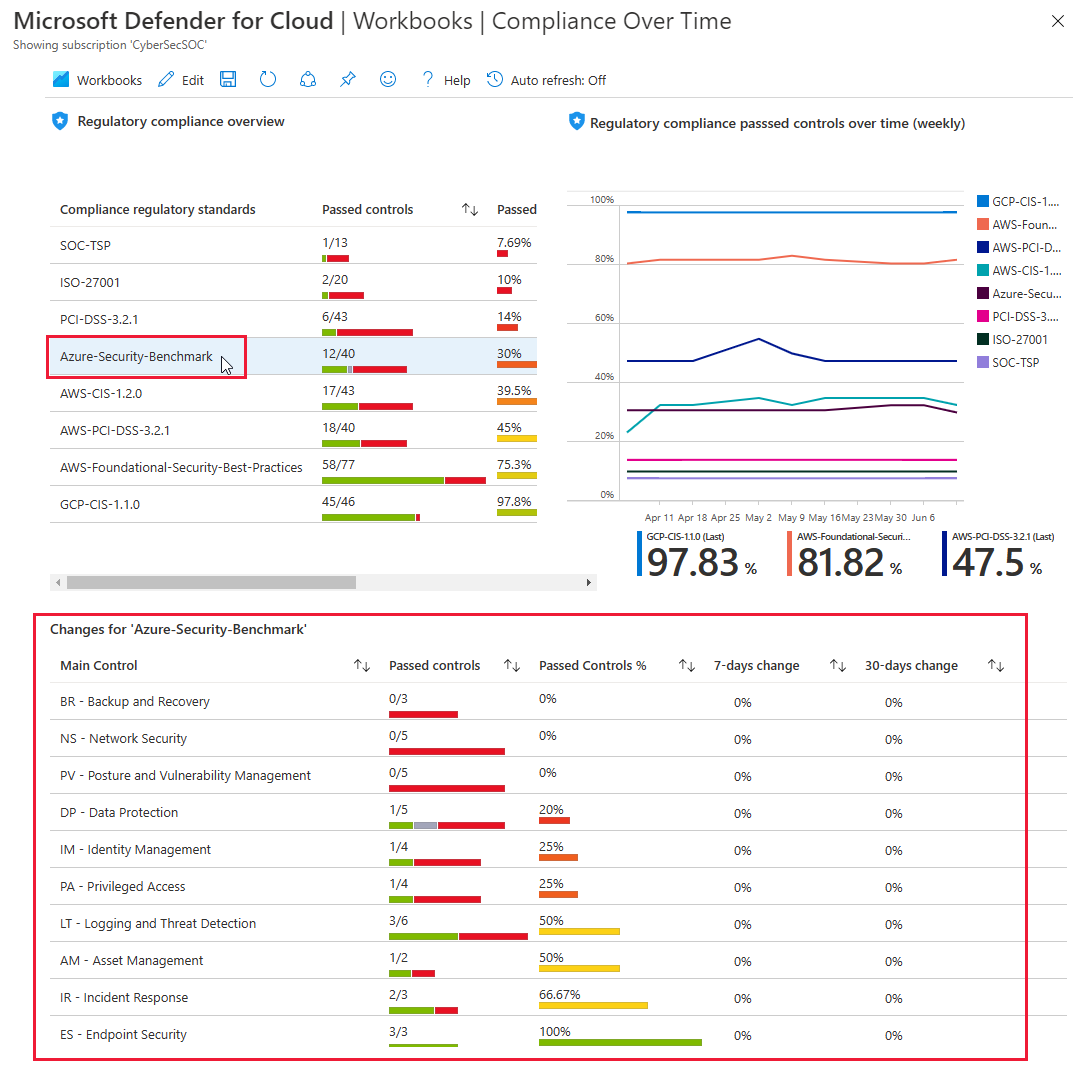
To view the resources that passed or failed each control, you can keep drilling down, all the way to the recommendation level.
Tip
For each panel of the report, you can export the data to Excel by using the Export to Excel option.

Active Alerts workbook
The Active Alerts workbook displays the active security alerts for your subscriptions on one dashboard. Security alerts are the notifications that Defender for Cloud generates when it detects threats against your resources. Defender for Cloud prioritizes and lists the alerts with the information that you need to quickly investigate and remediate.
This workbook benefits you by helping you be aware of and prioritize the active threats in your environment.
Note
Most workbooks use Azure Resource Graph to query data. For example, to display a map view, data is queried in a Log Analytics workspace. Continuous export should be enabled. Export the security alerts to the Log Analytics workspace.
You can view active alerts by severity, resource group, and tag.

You can also view your subscription's top alerts by attacked resources, alert types, and new alerts.
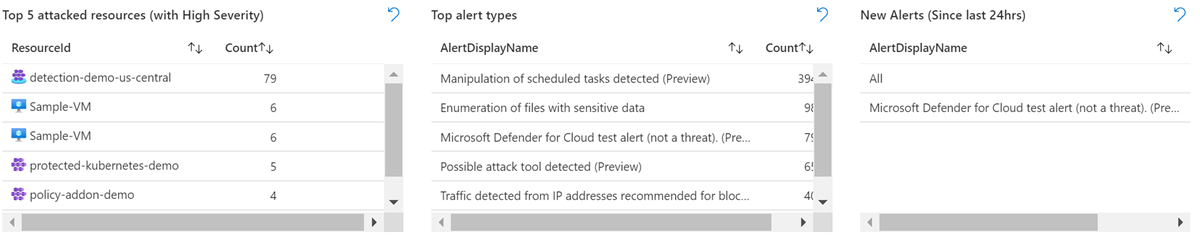
To see more details about an alert, select the alert.

The MITRE ATT&CK tactics tab lists alerts in the order of the "kill chain" and the number of alerts that the subscription has at each stage.

You can see all the active alerts in a table and filter by columns.

To see details for a specific alert, select the alert in the table, and then select the Open Alert View button.

To see all alerts by location in a map view, select the Map View tab.

Select a location on the map to view all the alerts for that location.

To view the details for an alert, select an alert, and then select the Open Alert View button.
DevOps Security workbook
The DevOps Security workbook provides a customizable visual report of your DevOps security posture. You can use this workbook to view insights about your repositories that have the highest number of common vulnerabilities and exposures (CVEs) and weaknesses, active repositories that have Advanced Security turned off, security posture assessments of your DevOps environment configurations, and much more. Customize and add your own visual reports by using the rich set of data in Azure Resource Graph to fit the business needs of your security team.
Note
To use this workbook, your environment must have a GitHub connector, GitLab connector, or Azure DevOps connector.
To deploy the workbook:
Sign in to the Azure portal.
Go to Microsoft Defender for Cloud > Workbooks.
Select the DevOps Security (Preview) workbook.
The workbook loads and displays the Overview tab. On this tab, you can see the number of exposed secrets, the code security, and DevOps security. The findings are shown by total for each repository and by severity.
To view the count by secret type, select the Secrets tab.
The Code tab displays the findings count by tool and repository. It shows the results of your code scanning by severity.
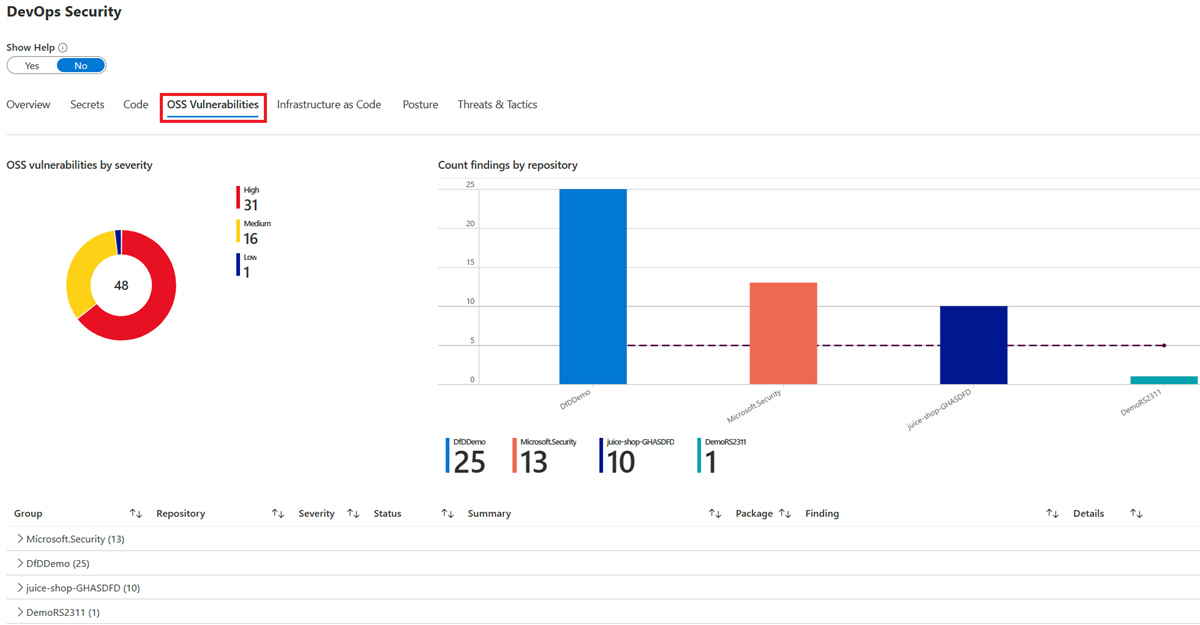
The OSS Vulnerabilities tab displays Open Source Security (OSS) vulnerabilities by severity and the count of findings by repository.
The Infrastructure as Code tab displays your findings by tool and repository.
The Posture tab displays security posture by severity and repository.
The Threats & Tactics tab displays the count of threats and tactics by repository and the total count.
Import workbooks from other workbook galleries
To move workbooks that you build in other Azure services into your Microsoft Defender for Cloud workbook gallery:
Open the workbook that you want to import.
On the toolbar, select Edit.

On the toolbar, select </> to open the advanced editor.

In the workbook gallery template, select all the JSON in the file and copy it.
Open the workbook gallery in Defender for Cloud, and then select New on the menu bar.
Select </> to open the Advanced Editor.
Paste the entire gallery template JSON code.
Select Apply.
On the toolbar, select Save As.

To save changes to the workbook, enter or select the following information:
- A name for the workbook.
- The Azure region to use.
- Any relevant information about the subscription, resource group, and sharing.
To find the saved workbook, go to the Recently modified workbooks category.
Related content
This article describes the Defender for Cloud integrated Azure workbooks page that has built-in reports and the option to build your own custom, interactive reports.
- Learn more about Azure workbooks.
Built-in workbooks get their data from Defender for Cloud recommendations.






