Review Docker host hardening recommendations
Microsoft Defender for Cloud identifies unmanaged containers hosted on IaaS Linux VMs, or other Linux machines running Docker containers. Defender for Cloud continuously assesses the configurations of these containers. It then compares them with the Center for Internet Security (CIS) Docker Benchmark.
Defender for Cloud includes the entire ruleset of the CIS Docker Benchmark and alerts you if your containers don't satisfy any of the controls. When it finds misconfigurations, Defender for Cloud generates security recommendations. Use Defender for Cloud's recommendations page to view recommendations and remediate issues.
When vulnerabilities are found, they're grouped inside a single recommendation.
Note
These CIS benchmark checks will not run on AKS-managed instances or Databricks-managed VMs.
Availability
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) |
| Pricing: | Requires Microsoft Defender for Servers Plan 2 |
| Required roles and permissions: | Reader on the workspace to which the host connects |
| Clouds: |
Identify and remediate security vulnerabilities in your Docker configuration
From Defender for Cloud's menu, open the Recommendations page.
Filter to the recommendation Vulnerabilities in container security configurations should be remediated and select the recommendation.
The recommendation page shows the affected resources (Docker hosts).
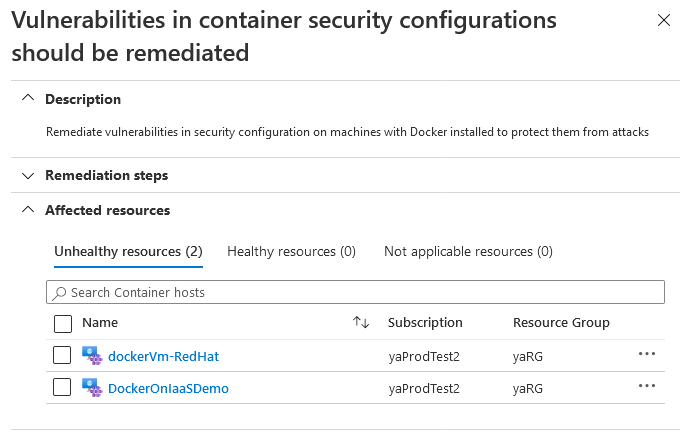
Note
Machines that aren't running Docker will be shown in the Not applicable resources tab. They'll appear in Azure Policy as Compliant.
To view and remediate the CIS controls that a specific host failed, select the host you want to investigate.
Tip
If you started at the asset inventory page and reached this recommendation from there, select the Take action button on the recommendation page.
Log Analytics opens with a custom operation ready to run. The default custom query includes a list of all failed rules that were assessed, along with guidelines to help you resolve the issues.
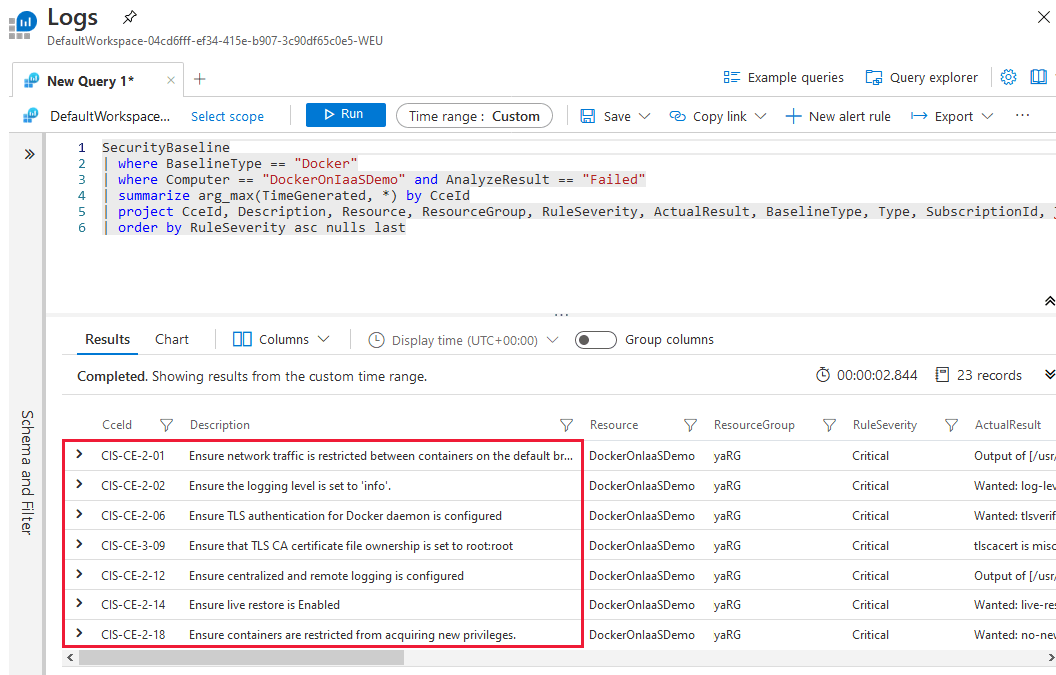
Tweak the query parameters if necessary.
When you're sure the command is appropriate and ready for your host, select Run.
Next step
Docker hardening is just one aspect of Defender for Cloud's container security features.
Learn more Container security in Defender for Cloud.