Set Git repository permissions
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
Manage access to repositories to lock down who can contribute to your source code and manage other features. You can set permissions across all Git repositories by making changes to the top-level Git repositories entry. Individual repositories inherit permissions from the top-level Git Repositories entry.
Note
Branches inherit a subset of permissions from assignments made at the repository level. For branch permissions and policies, see Set branch permissions and Improve code quality with branch policies.
For guidance on who to provide greater permission levels, see Manage access using permissions.
Prerequisites
- You must have a project. If you don't have a project yet, create one in Azure DevOps or set one up in an on-premises Azure DevOps.
- You must be a member of the Project Administrators Group or have your Manage permissions set to Allow for Git repositories.
To contribute to the source code, you must be granted Basic access level or greater. Users granted Stakeholder access for private projects have no access to source code. Users granted Stakeholder access for public projects have the same access as Contributors and those granted Basic access. For more information, see About access levels.
To contribute to the source code, you must be granted Basic access level or greater. Users granted Stakeholder access have no access to source code. For more information, see About access levels.
Default repository permissions
By default, members of the project Contributors group have permissions to contribute to a repository. This includes the ability to create branches, create tags, and manage notes. For a description of each security group and permission level, see Permissions and group reference.
Permission
Readers
Contributors
Build Admins
Project Admins
Read (clone, fetch, and explore the contents of a repository); also, can create, comment on, vote, and Contribute to pull requests
✔️
✔️
✔️
✔️
Contribute, Create branches, Create tags, and Manage notes
✔️
✔️
✔️
Create repository, Delete repository, and Rename repository
✔️
Edit policies, Manage permissions, Remove others' locks
✔️
Bypass policies when completing pull requests, Bypass policies when pushing, Force push (rewrite history, delete branches and tags)
(not set for any security group)
Starting with Azure DevOps sprint 224 (Azure DevOps Services and Azure DevOps Server 2022.1 and higher), Edit policies permission is no longer granted automatically to branch creators. Previously, when you created a new branch, you were granted permission to edit policies on that branch. With this update, we are changing the default behavior to not grant this permission even if the Permission management setting is switched on for the repository. You will need the Edit policies permission granted explicitly (either manually or through REST API) by security permission inheritance or through a group membership.
Open Security for a repository
You set Git repository permissions from Project Settings>Repositories.
Open the web portal and choose the project where you want to add users or groups. To choose another project, see Switch project, repository, team.
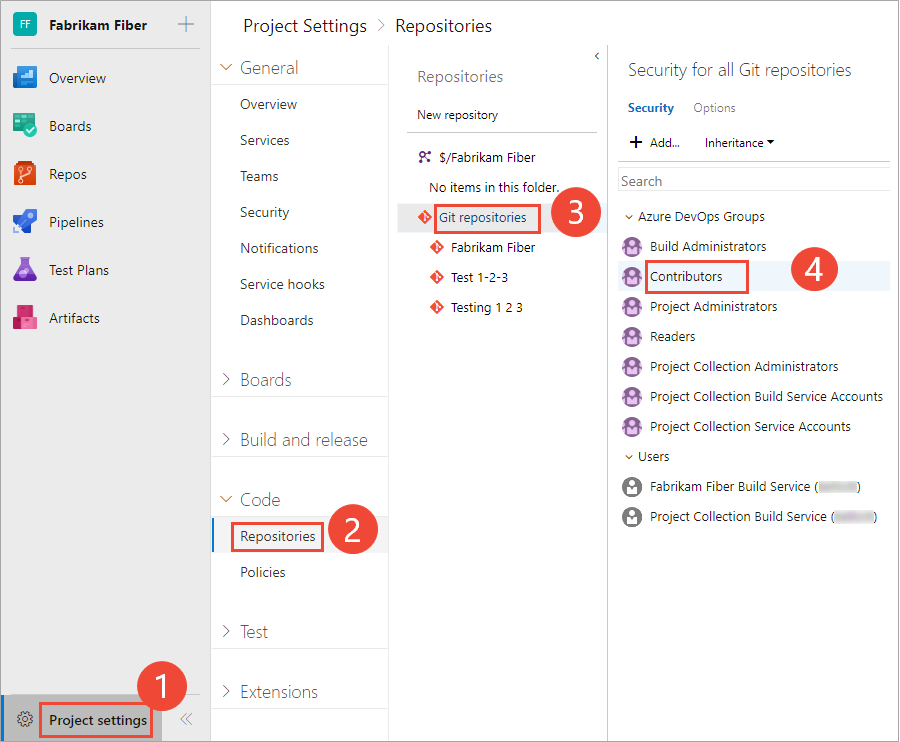
Open Project settings>Repositories.
To set the permissions for all Git repositories, choose Security.
For example, here we choose (1) Project settings, (2) Repositories, and then (3) Security.
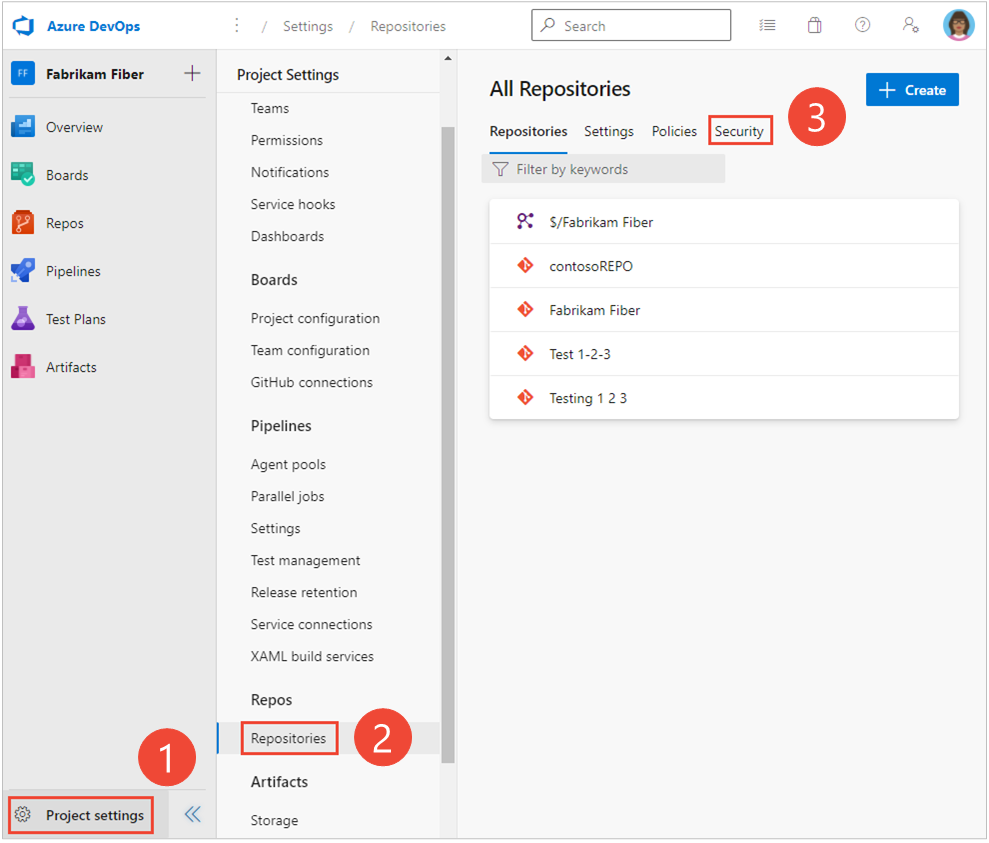
Otherwise, to set permissions for a specific repository, choose (1) the repository and then choose (2) Security.
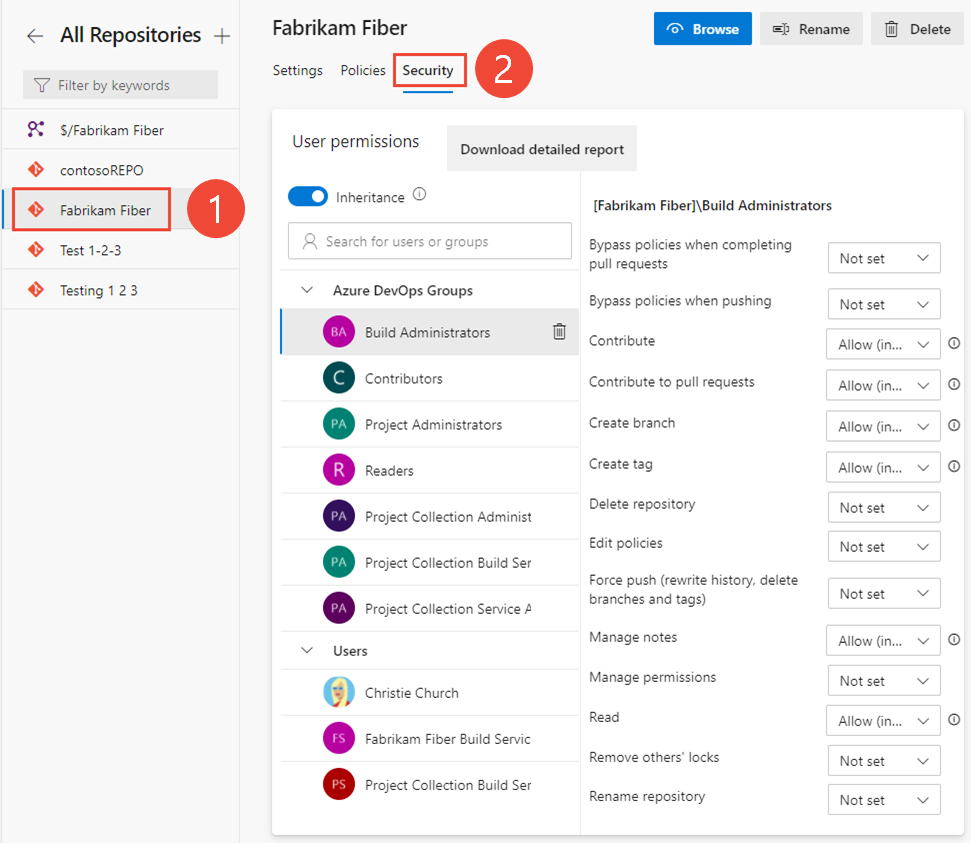
Set permissions for a repository
You can manage access to a repository by setting the permission state to Allow or Deny for a single user or a security group.
Open the web portal and choose the project where you want to add users or groups. To choose another project, see Switch project, repository, team.
To set the permissions for all Git repositories for a project, choose Git Repositories and then choose the security group whose permissions you want to manage.
For example, here we choose (1) Project Settings, (2) Repositories, (3) Git repositories, (4) the Contributors group, and then (5) the permission for Create repository.
To see the full image, click the image to expand. Choose the
 close icon to close.
close icon to close.Note
You may not be able to find a user from a permissions page or identity field if the user hasn't been added to the project—either by adding it to a security group or to a project team. Also, when a user is added to Microsoft Entra ID or Active Directory, there can be a delay between the time they are added to the project and when they are searchable from an identity field. The delay can be between 5 minutes to 7 days.
Otherwise, choose a specific repository and choose the security group whose permissions you want to manage.
Note
If you add a user or group, and don't change any permissions for that user or group, then upon refresh of the permissions page, the user or group you added no longer appears.
When done, choose Save changes.
Change permissions for a security group
To set permissions for a custom security group, you must have defined that group previously. See Set permissions at the project-level.
To set permissions for a specific group, choose the group. For example, here we choose the Contributors group.
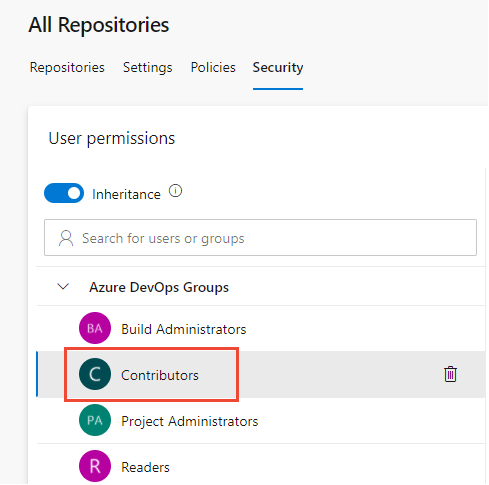
Change one or more permissions. To grant a permissions, change Not Set to Allow. To restrict permissions, change Allow to Deny.
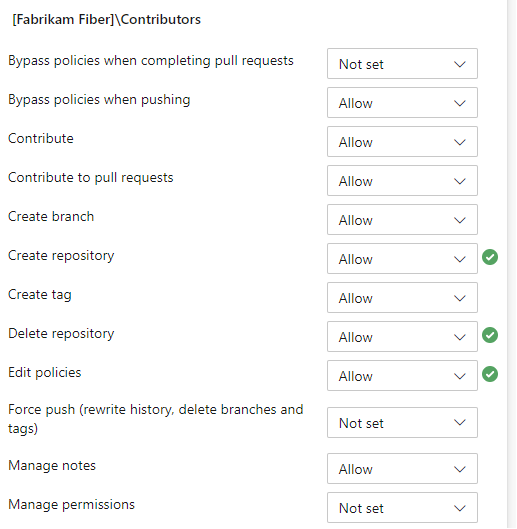
When done, navigate away from the page. The permission changes are automatically saved for the selected group.
Set permissions for a specific user
To set permissions for a specific user, enter the name of the user into the search filter and select from the identities that appear.
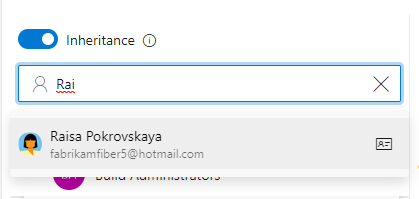
Then make the changes to the permission set.
Note
You may not be able to find a user from a permissions page or identity field if the user hasn't been added to the project—either by adding it to a security group or to a project team. Also, when a user is added to Microsoft Entra ID or Active Directory, there can be a delay between the time they are added to the project and when they are searchable from an identity field. The delay can be between 5 minutes to 7 days.
When done, navigate away from the page. The permission changes are automatically saved for the selected group.
Note
If you add a user or group, and don't change any permissions for that user or group, then upon refresh of the permissions page, the user or group you added no longer appears.
Enable or disable inheritance for a specific repository
To enable or disable inheritance for a specific repository, select the repository and then move the Inheritance slider to either an on or off position.
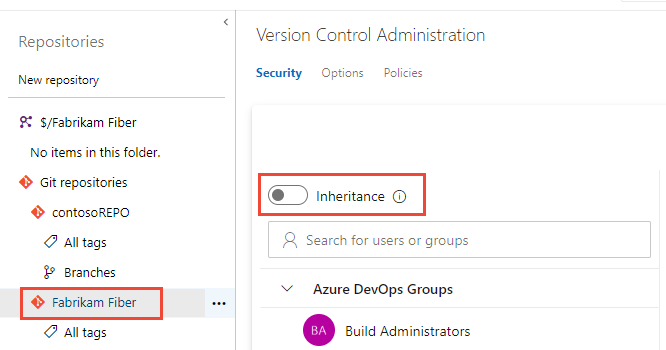
To learn about inheritance, see About permissions and groups, Inheritance and security groups.
Exempt from policy enforcement and bypass policy permissions
There are many scenarios where you have the occasional need to bypass a branch policy. For example, when reverting a change that caused a build break or applying a hotfix in the middle of the night. Previously, the Exempt from policy enforcement permission helped teams manage which users were granted the ability to bypass branch policies when completing a pull request. However, that permission also granted the ability to push directly to the branch, bypassing the PR process entirely.
To improve this experience, we split the Exempt from policy enforcement permission to offer more control to teams that are granting bypass permissions. The following two permissions replace the former permission:
- Bypass policies when completing pull requests. Users with this permission will be able to use the "Override" experience for pull requests.
- Bypass policies when pushing. Users with this permission will be able to push directly to branches that have required policies configured.
By granting the first permission and denying the second, a user can use the bypass option when necessary, but will still have the protection from accidentally pushing to a branch with policies.
Note
This change does not introduce any behavior changes. Users that were formerly granted Allow for Exempt from policy enforcement are granted Allow for both new permissions, so they'll be able to both override completion on PRs and push directly to branches with policies.
Related articles
Σχόλια
Σύντομα διαθέσιμα: Καθ' όλη τη διάρκεια του 2024 θα καταργήσουμε σταδιακά τα ζητήματα GitHub ως μηχανισμό ανάδρασης για το περιεχόμενο και θα το αντικαταστήσουμε με ένα νέο σύστημα ανάδρασης. Για περισσότερες πληροφορίες, ανατρέξτε στο θέμα: https://aka.ms/ContentUserFeedback.
Υποβολή και προβολή σχολίων για