Delegate Azure access management to others
In Azure role-based access control (Azure RBAC), to grant access to Azure resources, you assign Azure roles. For example, if a user needs to create and manage websites in a subscription, you assign the Website Contributor role.
Assigning Azure roles to grant access to Azure resources is a common task. As an administrator, you might get several requests to grant access that you want to delegate to someone else. However, you want to make sure the delegate has just the permissions they need to do their job. This article describes a more secure way to delegate role assignment management to other users in your organization.
Why delegate role assignment management?
Here are some reasons why you might want to delegate role assignment management to others:
- You get several requests to assign roles in your organization.
- Users are blocked waiting for the role assignment they need.
- Users within their respective departments, teams, or projects have more knowledge about who needs access.
- Users have permissions to create Azure resources, but need an additional role assignment to fully use that resource. For example:
- Users with permission to create virtual machines can't immediately sign in to the virtual machine without the Virtual Machine Administrator Login or Virtual Machine User Login role. Instead of tracking down an administrator to assign them a login role, it's more efficient if the user can assign the login role to themselves.
- A developer has permissions to create an Azure Kubernetes Service (AKS) cluster and an Azure Container Registry (ACR), but needs to assign the AcrPull role to a managed identity so that it can pull images from the ACR. Instead of tracking down an administrator to assign the AcrPull role, it's more efficient if the developer can assign the role themselves.
How you currently can delegate role assignment management
The Owner and User Access Administrator roles are built-in roles that allow users to create role assignments. Members of these roles can decide who can have write, read, and delete permissions for any resource in a subscription. To delegate role assignment management to another user, you can assign the Owner or User Access Administrator role to a user.
The following diagram shows how Alice can delegate role assignment responsibilities to Dara. For specific steps, see Assign a user as an administrator of an Azure subscription.
- Alice assigns the User Access Administrator role to Dara.
- Dara can now assign any role to any user, group, or service principal at the same scope.
What are the issues with the current delegation method?
Here are the primary issues with the current method of delegating role assignment management to others in your organization.
- Delegate has unrestricted access at the role assignment scope. This violates the principle of least privilege, which exposes you to a wider attack surface.
- Delegate can assign any role to any user within their scope, including themselves.
- Delegate can assign the Owner or User Access Administrator roles to another user, who can then assign roles to other users.
Instead of assigning the Owner or User Access Administrator roles, a more secure method is to constrain a delegate's ability to create role assignments.
A more secure method: Delegate role assignment management with conditions
Delegating role assignment management with conditions is a way to restrict the role assignments a user can create. In the preceding example, Alice can allow Dara to create some role assignments on her behalf, but not all role assignments. For example, Alice can constrain the roles that Dara can assign and constrain the principals that Dara can assign roles to. This delegation with conditions is sometimes referred to as constrained delegation and is implemented using Azure attribute-based access control (Azure ABAC) conditions.
This video provides an overview of delegating role assignment management with conditions.
Why delegate role assignment management with conditions?
Here are some reasons why delegating role assignment management to others with conditions is more secure:
- You can restrict the role assignments the delegate is allowed to create.
- You can prevent a delegate from allowing another user to assign roles.
- You can enforce compliance of your organization's policies of least privilege.
- You can automate the management of Azure resources without having to grant full permissions to a service account.
Conditions example
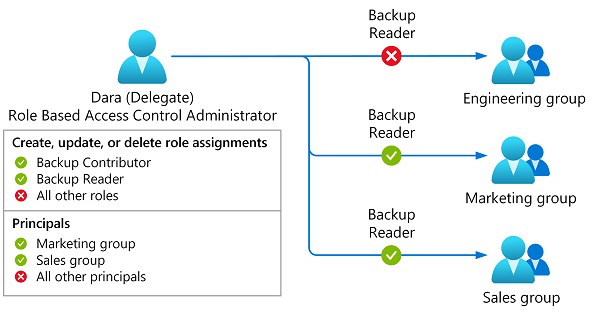
Consider an example where Alice is an administrator with the User Access Administrator role for a subscription. Alice wants to grant Dara the ability to assign specific roles for specific groups. Alice doesn't want Dara to have any other role assignment permissions. The following diagram shows how Alice can delegate role assignment responsibilities to Dara with conditions.
- Alice assigns the Role Based Access Control Administrator role to Dara. Alice adds conditions so that Dara can only assign the Backup Contributor or Backup Reader roles to the Marketing and Sales groups.
- Dara can now assign the Backup Contributor or Backup Reader roles to the Marketing and Sales groups.
- If Dara attempts to assign other roles or assign any roles to different principals (such as a user or managed identity), the role assignment fails.
Role Based Access Control Administrator role
The Role Based Access Control Administrator role is a built-in role that has been designed for delegating role assignment management to others. It has fewer permissions than User Access Administrator, which follows least privilege best practices. The Role Based Access Control Administrator role has following permissions:
- Create a role assignment at the specified scope
- Delete a role assignment at the specified scope
- Read resources of all types, except secrets
- Create and update a support ticket
Ways to constrain role assignments
Here are the ways that role assignments can be constrained with conditions. You can also combine these conditions to fit your scenario.
Constrain the roles that can be assigned
Constrain the roles and types of principals (users, groups, or service principals) that can be assigned roles
Constrain the roles and specific principals that can be assigned roles
Specify different conditions for the add and remove role assignment actions
How to delegate role assignment management with conditions
To delegate role assignment management with conditions, you assign roles as you currently do, but you also add a condition to the role assignment.
Determine the permissions the delegate needs
- What roles can the delegate assign?
- What types of principals can the delegate assign roles to?
- Which principals can the delegate assign roles to?
- Can delegate remove any role assignments?
Start a new role assignment
Select the Role Based Access Control Administrator role
You can select any role that includes the
Microsoft.Authorization/roleAssignments/writeaction, but Role Based Access Control Administrator has fewer permissions.Select the delegate
Select the user that you want to delegate role assignment management to.
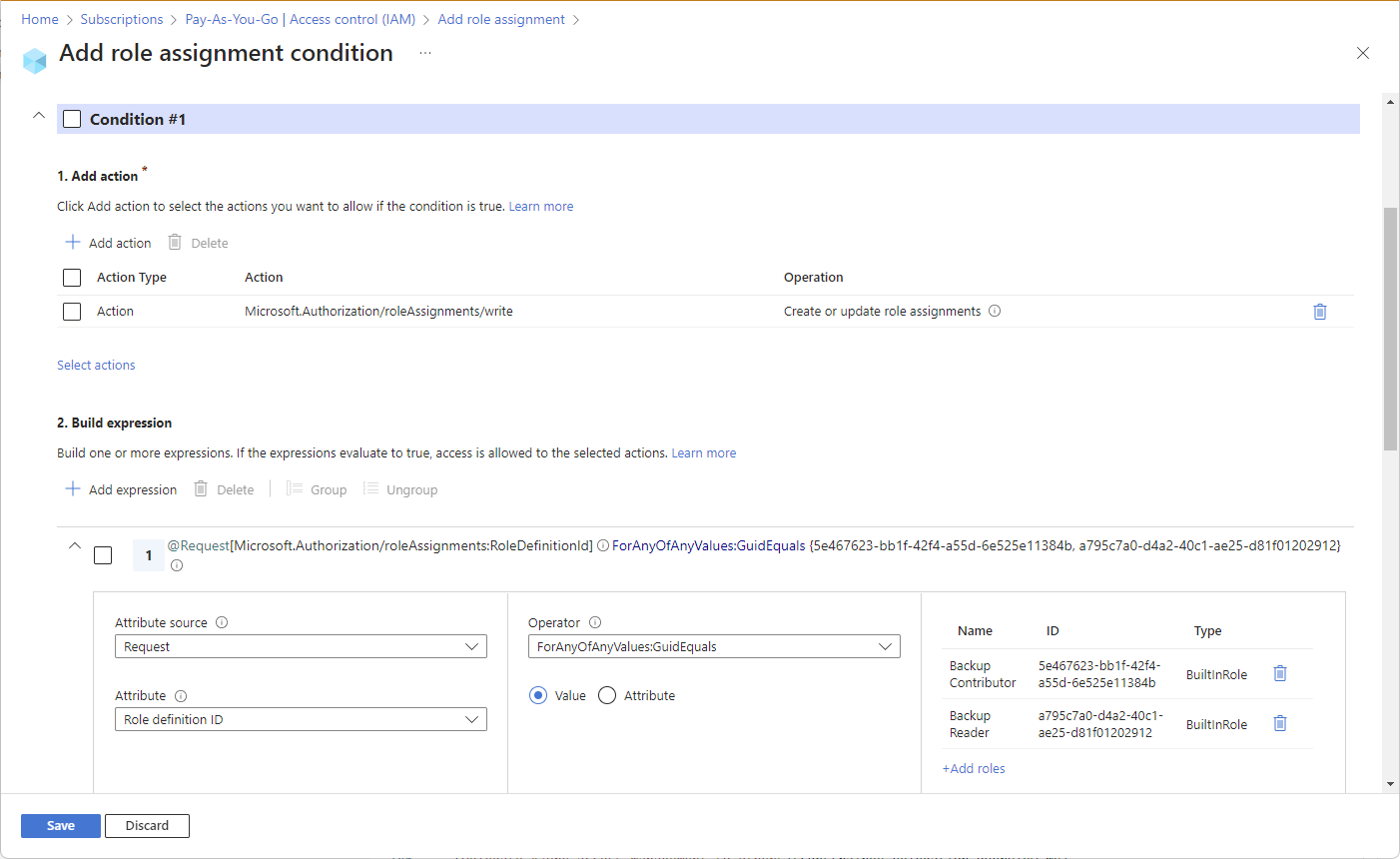
Add a condition
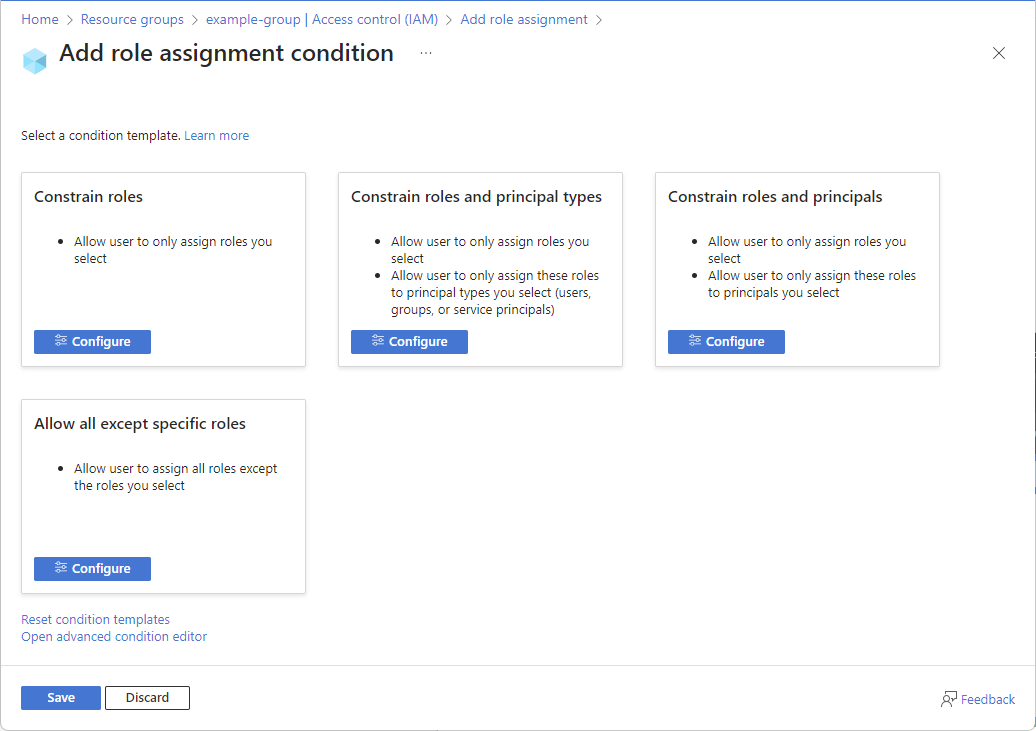
There are multiple ways that you can add a condition. For example, you can use a condition template in the Azure portal, the advanced condition editor in the Azure portal, Azure PowerShell, Azure CLI, Bicep, or REST API.
Choose from a list of condition templates. Select Configure to specify the roles, principal types, or principals.
For more information, see Delegate Azure role assignment management to others with conditions.
Assign role with condition to delegate
Once you have specified your condition, complete the role assignment.
Contact the delegate
Let the delegate know that they can now assign roles with conditions.
Built-in roles with conditions
The Key Vault Data Access Administrator and Virtual Machine Data Access Administrator (preview) roles already have a built-in condition to constrain role assignments.
The Key Vault Data Access Administrator role enables you to manage access to Key Vault secrets, certificates, and keys. It's exclusively focused on access control without the ability to assign privileged roles such as Owner or User Access Administrator roles. It allows better separation of duties for scenarios like managing encryption at rest across data services to further comply with least privilege principle. The condition constrains role assignments to the following Azure Key Vault roles:
- Key Vault Administrator
- Key Vault Certificates Officer
- Key Vault Crypto Officer
- Key Vault Crypto Service Encryption User
- Key Vault Crypto User
- Key Vault Reader
- Key Vault Secrets Officer
- Key Vault Secrets User
If you want to further constrain the Key Vault Data Access Administrator role assignment, you can add your own condition to constrain the types of principals (users, groups, or service principals) or specific principals that can be assigned the Key Vault roles.
Known issues
Here are the known issues related to delegating role assignment management with conditions:
- You can't delegate role assignment management for custom roles with conditions using Privileged Identity Management.
- You can't have a role assignment with a Microsoft.Storage data action and an ABAC condition that uses a GUID comparison operator. For more information, see Troubleshoot Azure RBAC.
License requirements
Using this feature is free and included in your Azure subscription.