Overview: On-premises Active Directory Domain Services authentication over SMB for Azure file shares
Azure Files supports identity-based authentication for Windows file shares over Server Message Block (SMB) using the Kerberos authentication protocol through the following methods:
- On-premises Active Directory Domain Services (AD DS)
- Microsoft Entra Domain Services
- Microsoft Entra Kerberos for hybrid user identities
We strongly recommend that you review the How it works section to select the right AD source for authentication. The setup is different depending on the domain service you choose. This article focuses on enabling and configuring on-premises AD DS for authentication with Azure file shares.
If you're new to Azure Files, we recommend reading our planning guide.
Applies to
| File share type | SMB | NFS |
|---|---|---|
| Standard file shares (GPv2), LRS/ZRS | ||
| Standard file shares (GPv2), GRS/GZRS | ||
| Premium file shares (FileStorage), LRS/ZRS |
Supported scenarios and restrictions
- AD DS identities used for Azure Files on-premises AD DS authentication must be synced to Microsoft Entra ID or use a default share-level permission. Password hash synchronization is optional.
- Supports Azure file shares managed by Azure File Sync.
- Supports Kerberos authentication with AD with AES 256 encryption (recommended) and RC4-HMAC. AES 128 Kerberos encryption isn't yet supported.
- Supports single sign-on experience.
- Only supported on Windows clients running OS versions Windows 8/Windows Server 2012 or newer, or Linux VMs (Ubuntu 18.04+ or an equivalent RHEL or SLES VM).
- Only supported against the AD forest that the storage account is registered to. Users belonging to different domains within the same forest should be able to access the file share and underlying directories/files as long as they have the appropriate permissions.
- You can only access Azure file shares with the AD DS credentials from a single forest by default. If you need to access your Azure file share from a different forest, make sure that you have the proper forest trust configured. For details, see Use Azure Files with multiple Active Directory forests.
- Doesn't support assigning share-level permissions to computer accounts (machine accounts) using Azure RBAC. You can either use a default share-level permission to allow computer accounts to access the share, or consider using a service logon account instead.
- Doesn't support authentication against Network File System (NFS) file shares.
When you enable AD DS for Azure file shares over SMB, your AD DS-joined machines can mount Azure file shares using your existing AD DS credentials. This capability can be enabled with an AD DS environment hosted either in on-premises machines or hosted on a virtual machine (VM) in Azure.
Videos
To help you set up identity-based authentication for some common use cases, we published two videos with step-by-step guidance for the following scenarios. Note that Azure Active Directory is now Microsoft Entra ID. For more info, see New name for Azure AD.
Prerequisites
Before you enable AD DS authentication for Azure file shares, make sure you've completed the following prerequisites:
Select or create your AD DS environment and sync it to Microsoft Entra ID using either the on-premises Microsoft Entra Connect Sync application or Microsoft Entra Connect cloud sync, a lightweight agent that can be installed from the Microsoft Entra Admin Center.
You can enable the feature on a new or existing on-premises AD DS environment. Identities used for access must be synced to Microsoft Entra ID or use a default share-level permission. The Microsoft Entra tenant and the file share that you're accessing must be associated with the same subscription.
Domain-join an on-premises machine or an Azure VM to on-premises AD DS. For information about how to domain-join, refer to Join a Computer to a Domain.
If a machine isn't domain joined, you can still use AD DS for authentication if the machine has unimpeded network connectivity to the on-premises AD domain controller and the user provides explicit credentials. For more information, see Mount the file share from a non-domain-joined VM or a VM joined to a different AD domain.
Select or create an Azure storage account. For optimal performance, we recommend that you deploy the storage account in the same region as the client from which you plan to access the share. Then, mount the Azure file share with your storage account key. Mounting with the storage account key verifies connectivity.
Make sure that the storage account containing your file shares isn't already configured for identity-based authentication. If an AD source is already enabled on the storage account, you must disable it before enabling on-premises AD DS.
If you experience issues in connecting to Azure Files, refer to the troubleshooting tool we published for Azure Files mounting errors on Windows.
Make any relevant networking configuration prior to enabling and configuring AD DS authentication to your Azure file shares. See Azure Files networking considerations for more information.
Regional availability
Azure Files authentication with AD DS is available in all Azure Public, China and Gov regions.
Overview
If you plan to enable any networking configurations on your file share, we recommend you read the networking considerations article and complete the related configuration before enabling AD DS authentication.
Enabling AD DS authentication for your Azure file shares allows you to authenticate to your Azure file shares with your on-premises AD DS credentials. Further, it allows you to better manage your permissions to allow granular access control. Doing this requires synching identities from on-premises AD DS to Microsoft Entra ID using either the on-premises Microsoft Entra Connect Sync application or Microsoft Entra Connect cloud sync, a lightweight agent that can be installed from the Microsoft Entra Admin Center. You assign share-level permissions to hybrid identities synced to Microsoft Entra ID while managing file/directory-level access using Windows ACLs.
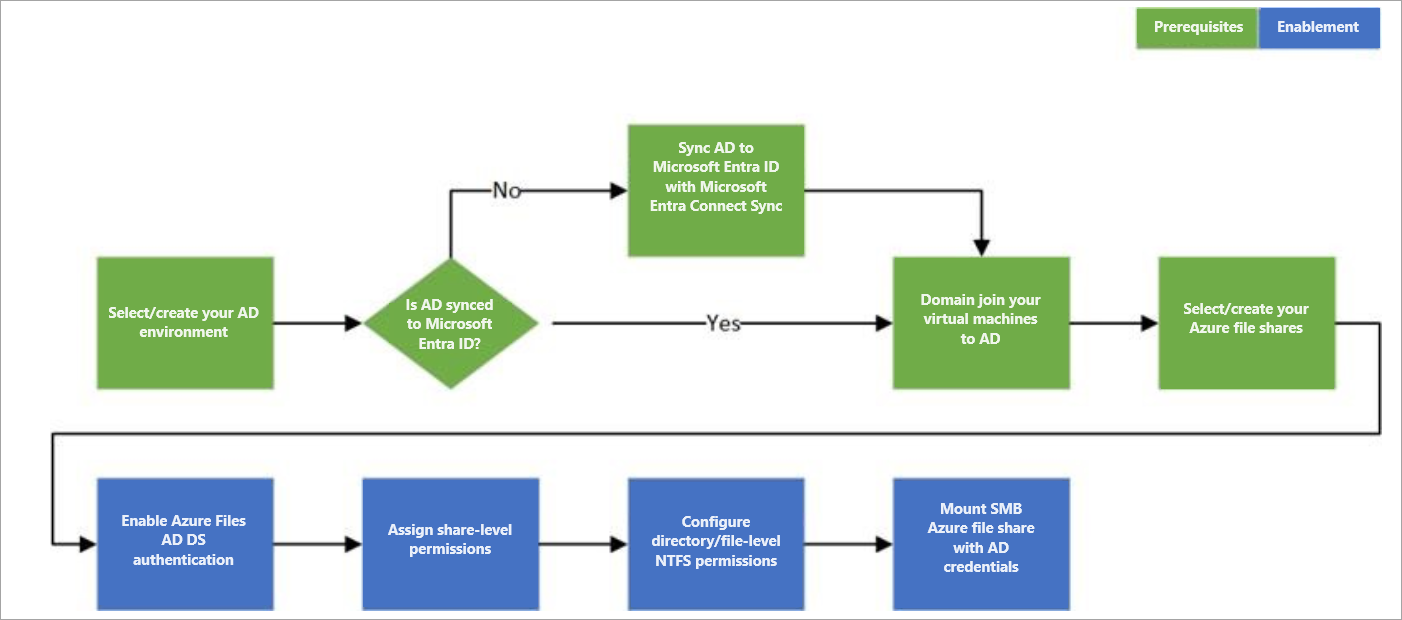
Follow these steps to set up Azure Files for AD DS authentication:
The following diagram illustrates the end-to-end workflow for enabling AD DS authentication over SMB for Azure file shares.
Identities used to access Azure file shares must be synced to Microsoft Entra ID to enforce share-level file permissions through the Azure role-based access control (Azure RBAC) model. Alternatively, you can use a default share-level permission. Windows-style DACLs on files/directories carried over from existing file servers will be preserved and enforced. This offers seamless integration with your enterprise AD DS environment. As you replace on-premises file servers with Azure file shares, existing users can access Azure file shares from their current clients with a single sign-on experience, without any change to the credentials in use.
Next step
To get started, you must enable AD DS authentication for your storage account.
Σχόλια
Σύντομα διαθέσιμα: Καθ' όλη τη διάρκεια του 2024 θα καταργήσουμε σταδιακά τα ζητήματα GitHub ως μηχανισμό ανάδρασης για το περιεχόμενο και θα το αντικαταστήσουμε με ένα νέο σύστημα ανάδρασης. Για περισσότερες πληροφορίες, ανατρέξτε στο θέμα: https://aka.ms/ContentUserFeedback.
Υποβολή και προβολή σχολίων για