Assign multiple IP addresses to virtual machines using Azure PowerShell
An Azure Virtual Machine (VM) has one or more network interfaces (NIC) attached to it. Any NIC can have one or more static or dynamic public and private IP addresses assigned to it.
Assigning multiple IP addresses to a VM enables the following capabilities:
Hosting multiple websites or services with different IP addresses and TLS/SSL certificates on a single server.
Serve as a network virtual appliance, such as a firewall or load balancer.
The ability to add any of the private IP addresses for any of the NICs to an Azure Load Balancer back-end pool. In the past, only the primary IP address for the primary NIC could be added to a back-end pool. For more information about load balancing multiple IP configurations, see Load balancing multiple IP configurations.
Every NIC attached to a VM has one or more IP configurations associated to it. Each configuration is assigned one static or dynamic private IP address. Each configuration may also have one public IP address resource associated to it. To learn more about IP addresses in Azure, see IP addresses in Azure.
Note
All IP configurations on a single NIC must be associated to the same subnet. If multiple IPs on different subnets are desired, multiple NICs on a VM can be used. To learn more about multiple NICs on a VM in Azure, see Create VM with Multiple NICs.
There's a limit to how many private IP addresses can be assigned to a NIC. There's also a limit to how many public IP addresses that can be used in an Azure subscription. See the Azure limits article for details.
This article explains how to add multiple IP addresses to a virtual machine using PowerShell.
Prerequisites
An Azure account with an active subscription. Create an account for free.
PowerShell environment in Azure Cloud Shell or Azure PowerShell installed locally. To learn more about using PowerShell in Azure Cloud Shell, see Azure Cloud Shell Quickstart.
- If you choose to install and use PowerShell locally, this article requires the Azure PowerShell module version 5.4.1 or later. Run
Get-InstalledModule -Name Azto find the installed version. If you need to upgrade, see Install Azure PowerShell module. Ensure your Az.Network module is 4.3.0 or later. To verify the installed module, use the commandGet-InstalledModule -Name "Az.Network". If the module requires an update, use the commandUpdate-Module -Name "Az.Network"if necessary.
- If you choose to install and use PowerShell locally, this article requires the Azure PowerShell module version 5.4.1 or later. Run
Sign in to Azure PowerShell and ensure you've selected the subscription with which you want to use this feature. For more information, see Sign in with Azure PowerShell.
Note
Though the steps in this article assigns all IP configurations to a single NIC, you can also assign multiple IP configurations to any NIC in a multi-NIC VM. To learn how to create a VM with multiple NICs, see Create a VM with multiple NICs.
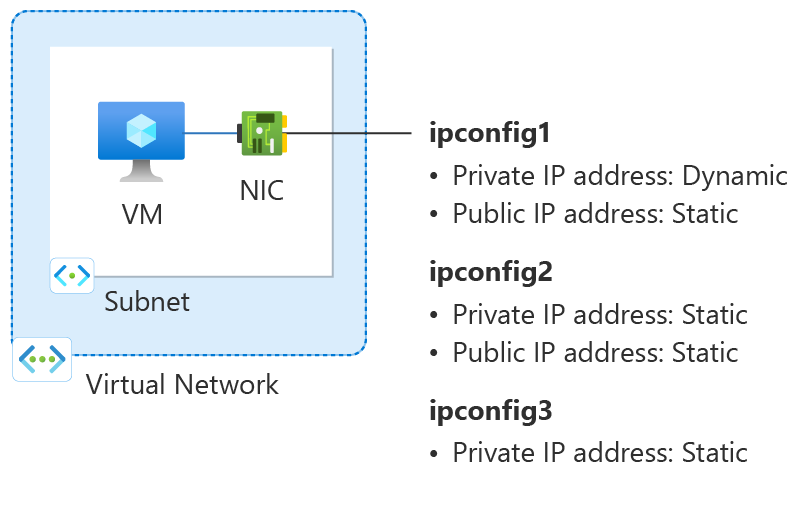
Figure: Diagram of network configuration resources created in this How-to article.
Create a resource group
An Azure resource group is a logical container into which Azure resources are deployed and managed.
Create a resource group with New-AzResourceGroup named myResourceGroup in the eastus2 location.
$rg =@{
Name = 'myResourceGroup'
Location = 'eastus2'
}
New-AzResourceGroup @rg
Create a virtual network
In this section, you create a virtual network for the virtual machine.
Use New-AzVirtualNetwork and New-AzVirtualNetworkSubnetConfig to create a virtual network with one subnet.
## Create backend subnet config ##
$subnet = @{
Name = 'myBackendSubnet'
AddressPrefix = '10.1.0.0/24'
}
$subnetConfig = New-AzVirtualNetworkSubnetConfig @subnet
## Create the virtual network ##
$vnet = @{
Name = 'myVNet'
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
AddressPrefix = '10.1.0.0/16'
Subnet = $subnetConfig
}
New-AzVirtualNetwork @vnet
Create a primary public IP address
Use New-AzPublicIpAddress to create a primary public IP address.
$ip1 = @{
Name = 'myPublicIP-1'
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
Sku = 'Standard'
AllocationMethod = 'Static'
IpAddressVersion = 'IPv4'
Zone = 1,2,3
}
New-AzPublicIpAddress @ip1
Create a network security group
In this section, you create a network security group for the virtual machine and virtual network. You create a rule to allow connections to the virtual machine on port 22 for SSH.
Use New-AzNetworkSecurityGroup and New-AzNetworkSecurityRuleConfig to create the network security group and rules.
## Create rule for network security group and place in variable. ##
$nsgrule1 = @{
Name = 'myNSGRuleSSH'
Description = 'Allow SSH'
Protocol = '*'
SourcePortRange = '*'
DestinationPortRange = '22'
SourceAddressPrefix = 'Internet'
DestinationAddressPrefix = '*'
Access = 'Allow'
Priority = '200'
Direction = 'Inbound'
}
$rule1 = New-AzNetworkSecurityRuleConfig @nsgrule1
## Create network security group ##
$nsg = @{
Name = 'myNSG'
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
SecurityRules = $rule1
}
New-AzNetworkSecurityGroup @nsg
Create a network interface
Use New-AzNetworkInterface and New-AzNetworkInterfaceIpConfig to create a network interface (NIC) for the virtual machine. The public IP address and network security group created previously are associated with the network interface. The network interface is attached to the virtual network you created previously.
## Place the virtual network into a variable. ##
$net = @{
Name = 'myVNet'
ResourceGroupName = 'myResourceGroup'
}
$vnet = Get-AzVirtualNetwork @net
## Place the network security group into a variable. ##
$ns = @{
Name = 'myNSG'
ResourceGroupName = 'myResourceGroup'
}
$nsg = Get-AzNetworkSecurityGroup @ns
## Place the primary public IP address into a variable. ##
$pub1 = @{
Name = 'myPublicIP-1'
ResourceGroupName = 'myResourceGroup'
}
$pubIP1 = Get-AzPublicIPAddress @pub1
## Create a primary IP configuration for the network interface. ##
$IP1 = @{
Name = 'ipconfig1'
Subnet = $vnet.Subnets[0]
PrivateIpAddressVersion = 'IPv4'
PublicIPAddress = $pubIP1
}
$IP1Config = New-AzNetworkInterfaceIpConfig @IP1 -Primary
## Create a secondary IP configuration for the network interface. ##
$IP3 = @{
Name = 'ipconfig3'
Subnet = $vnet.Subnets[0]
PrivateIpAddressVersion = 'IPv4'
PrivateIpAddress = '10.1.0.6'
}
$IP3Config = New-AzNetworkInterfaceIpConfig @IP3
## Command to create a network interface. ##
$nic = @{
Name = 'myNIC1'
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
NetworkSecurityGroup = $nsg
IpConfiguration = $IP1Config,$IP3Config
}
New-AzNetworkInterface @nic
Note
When adding a static IP address, you must specify an unused, valid address on the subnet the NIC is connected to.
Create a virtual machine
Use the following commands to create the virtual machine:
$cred = Get-Credential
## Place network interface into a variable. ##
$nic = @{
Name = 'myNIC1'
ResourceGroupName = 'myResourceGroup'
}
$nicVM = Get-AzNetworkInterface @nic
## Create a virtual machine configuration for VMs ##
$vmsz = @{
VMName = 'myVM'
VMSize = 'Standard_DS1_v2'
}
$vmos = @{
ComputerName = 'myVM'
Credential = $cred
}
$vmimage = @{
PublisherName = 'Debian'
Offer = 'debian-11'
Skus = '11'
Version = 'latest'
}
$vmConfig = New-AzVMConfig @vmsz `
| Set-AzVMOperatingSystem @vmos -Linux `
| Set-AzVMSourceImage @vmimage `
| Add-AzVMNetworkInterface -Id $nicVM.Id
## Create the virtual machine for VMs ##
$vm = @{
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
VM = $vmConfig
SshKeyName = 'mySSHKey'
}
New-AzVM @vm -GenerateSshKey
Add secondary private and public IP address
Use New-AzPublicIpAddress to create a secondary public IP address.
$ip2 = @{
Name = 'myPublicIP-2'
ResourceGroupName = 'myResourceGroup'
Location = 'eastus2'
Sku = 'Standard'
AllocationMethod = 'Static'
IpAddressVersion = 'IPv4'
Zone = 1,2,3
}
New-AzPublicIpAddress @ip2
Use New-AzNetworkInterfaceIpConfig to create the secondary IP configuration for the virtual machine.
## Place the virtual network into a variable. ##
$net = @{
Name = 'myVNet'
ResourceGroupName = 'myResourceGroup'
}
$vnet = Get-AzVirtualNetwork @net
## Place your virtual network subnet into a variable. ##
$sub = @{
Name = 'myBackendSubnet'
VirtualNetwork = $vnet
}
$subnet = Get-AzVirtualNetworkSubnetConfig @sub
## Place the secondary public IP address you created previously into a variable. ##
$pip = @{
Name = 'myPublicIP-2'
ResourceGroupName = 'myResourceGroup'
}
$pubIP2 = Get-AzPublicIPAddress @pip
## Place the network interface into a variable. ##
$net = @{
Name = 'myNIC1'
ResourceGroupName = 'myResourceGroup'
}
$nic = Get-AzNetworkInterface @net
## Create a secondary IP configuration for the network interface. ##
$IPc2 = @{
Name = 'ipconfig2'
Subnet = $vnet.Subnets[0]
PrivateIpAddressVersion = 'IPv4'
PrivateIpAddress = '10.1.0.5'
PublicIPAddress = $pubIP2
}
$IP2Config = New-AzNetworkInterfaceIpConfig @IPc2
## Add the IP configuration to the network interface. ##
$nic.IpConfigurations.Add($IP2Config)
## Save the configuration to the network interface. ##
$nic | Set-AzNetworkInterface
Add IP addresses to a VM operating system
Connect and sign in to a VM you created with multiple private IP addresses. You must manually add all the private IP addresses, including the primary, that you added to the VM. Complete the following steps for your VM operating system.
Windows Server
Expand
Open a command prompt or PowerShell.
Enter
ipconfig /allat the command line. You'll see the Primary private IP address that was assigned through DHCP.Enter
ncpa.cplat the command line to open the Network Connections configuration.Open the Properties for the network adapter assigned the new IP addresses.
Double-click Internet Protocol Version 4 (TCP/IPv4).
Select Use the following IP address:. Enter the following values.
Setting Value IP address: Enter the Primary private IP address. Subnet mask: Enter a subnet mask based on your IP address.
For example, if the subnet is a /24 subnet then the subnet mask is 255.255.255.0.Default gateway: The first IP address in the subnet.
If your subnet is 10.0.0.0/24, then the gateway IP address is 10.0.0.1.Select Use the following DNS server addresses:. Enter the following values.
Setting Value Preferred DNS server: Enter your primary DNS server.
Enter the IP address of 168.63.129.16 to use the default Azure provided DNS.Select the Advanced button.
Select Add.
Enter the private IP address you added to the Azure network interface. Enter the corresponding Subnet mask. Select Add.
Repeat the previous steps to add any additional private IP addresses that you added to the Azure network interface.
Important
You should never manually assign the public IP address assigned to an Azure virtual machine within the virtual machine's operating system. When you manually set the IP address within the operating system, ensure that it's the same address as the private IP address assigned to the Azure network interface. Failure to assign the address correctly can cause loss of connectivity to the virtual machine. For more information, see Change IP address settings.
For more information about private IP addresses, see Private IP address.
Select OK to close the secondary IP address settings.
Select OK to close the adapter settings. Your RDP connection will re-establish.
Open a command prompt or PowerShell.
Enter
ipconfig /allat the command line.Verify the primary and secondary private IP addresses have been added to the configuration.
PS C:\Users\azureuser> ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : myVM Primary Dns Suffix . . . . . . . : Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No Ethernet adapter Ethernet: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft Hyper-V Network Adapter Physical Address. . . . . . . . . : 00-0D-3A-E6-CE-A3 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::a8d1:11d5:3ab2:6a51%5(Preferred) IPv4 Address. . . . . . . . . . . : 10.1.0.4(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 IPv4 Address. . . . . . . . . . . : 10.1.0.5(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 IPv4 Address. . . . . . . . . . . : 10.1.0.6(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 10.1.0.1 DHCPv6 IAID . . . . . . . . . . . : 100666682 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2A-A8-26-B1-00-0D-3A-E6-CE-A3 DNS Servers . . . . . . . . . . . : 168.63.129.16 NetBIOS over Tcpip. . . . . . . . : EnabledEnsure the primary private IP address used in windows is the same as the primary IP address of the Azure VM network interface. For more information, see No Internet access from Azure Windows VM that has multiple IP addresses.
Validation (Windows Server)
To validate connectivity to the internet from the secondary IP configuration via the public IP, use the following command. Replace 10.1.0.5 with the secondary private IP address you added to the Azure VM network interface.
ping -S 10.1.0.5 outlook.com
Note
For secondary IP configurations, you can ping to the Internet if the configuration has a public IP address associated with it. For primary IP configurations, a public IP address is not required to ping to the Internet.
SUSE Linux Enterprise and openSUSE
Expand
SUSE-based distributions use thecloud-netconfig plugin from the cloud-netconfig-azure package to manage additional IP addresses. No manual configuration is required on the part of the administrator. The first IP address of an interface set on the platform is assigned via DHCP. The cloud-netconfig plugin then probes the Azure Instance Metadata Service API continuously (once per minute) for additional IP addresses assigned to the interface and adds/removes them as secondary IP addresses automatically.
This plugin should be installed and enabled on new images by default. Configuration steps for old workloads can be found here: https://www.suse.com/c/multi-nic-cloud-netconfig-ec2-azure/.
Ubuntu 14/16
Expand
We recommend looking at the latest documentation for your Linux distribution.
Open a terminal window.
Ensure you're the root user. If you aren't, enter the following command:
sudo -iUpdate the configuration file of the network interface (assuming ‘eth0’).
Keep the existing line item for dhcp. The primary IP address remains configured as it was previously.
Add a configuration for an additional static IP address with the following commands:
cd /etc/network/interfaces.d/ lsYou should see a .cfg file.
Open the file. You should see the following lines at the end of the file:
auto eth0 iface eth0 inet dhcpAdd the following lines after the lines that exist in the file. Replace
10.1.0.5with your private IP address and subnet mask.iface eth0 inet static address 10.1.0.5 netmask 255.255.255.0To add additional private IP addresses, edit the file and add the new private IP addresses on subsequent lines:
iface eth0 inet static address 10.1.0.5 netmask 255.255.255.0 iface eth0 inet static address 10.1.0.6 netmask 255.255.255.0Save the file by using the following command:
:wqReset the network interface with the following command:
ifdown eth0 && ifup eth0Important
Execute both ifdown and ifup in the same line if using a remote connection.
Verify the IP address is added to the network interface with the following command:
ip addr list eth0You should see the IP address you added as part of the list. Example:
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:0d:3a:04:45:16 brd ff:ff:ff:ff:ff:ff inet 10.1.0.5/24 brd 10.1.0.255 scope global eth0 valid_lft forever preferred_lft forever inet 10.1.0.6/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet 10.1.0.4/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet6 fe80::20d:3aff:fe04:4516/64 scope link valid_lft forever preferred_lft forever
Validation (Ubuntu 14/16)
To ensure you're able to connect to the internet from your secondary IP configuration via the public IP associated with it, use the following command:
ping -I 10.1.0.5 outlook.com
Note
For secondary IP configurations, you can only ping to the Internet if the configuration has a public IP address associated with it. For primary IP configurations, a public IP address is not required to ping to the Internet.
For Linux VMs, when attempting to validate outbound connectivity from a secondary NIC, you may need to add appropriate routes. See appropriate documentation for your Linux distribution. The following is one method to accomplish this:
echo 150 custom >> /etc/iproute2/rt_tables
ip rule add from 10.1.0.5 lookup custom
ip route add default via 10.1.0.1 dev eth2 table custom
Ensure to replace:
10.1.0.5 with the private IP address that has a public IP address associated to it
10.1.0.1 to your default gateway
eth2 to the name of your secondary NIC
Ubuntu 18.04+
Expand
Ubuntu 18.04 and above have changed to netplan for OS network management. We recommend looking at the latest documentation for your Linux distribution.
Open a terminal window.
Ensure you're the root user. If you are not, enter the following command:
sudo -iCreate a file for the second interface and open it in a text editor:
vi /etc/netplan/60-static.yamlAdd the following lines to the file, replacing
10.1.0.5/24with your IP and subnet mask:network: version: 2 ethernets: eth0: addresses: - 10.1.0.5/24To add additional private IP addresses, edit the file and add the new private IP addresses on subsequent lines:
network: version: 2 ethernets: eth0: addresses: - 10.1.0.5/24 - 10.1.0.6/24Save the file by using the following command:
:wqTest the changes with netplan try to confirm syntax:
netplan tryNote
netplan trywill apply the changes temporarily and roll the changes back after 120 seconds. If there is a loss of connectivity, please wait 120 seconds, and then reconnect. At that time, the changes will have been rolled back.Assuming no issues with
netplan try, apply the configuration changes:netplan applyVerify the IP address is added to the network interface with the following command:
ip addr list eth0You should see the IP address you added as part of the list. Example:
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:0d:3a:04:45:16 brd ff:ff:ff:ff:ff:ff inet 10.1.0.5/24 brd 10.1.0.255 scope global eth0 valid_lft forever preferred_lft forever inet 10.1.0.6/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet 10.1.0.4/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet6 fe80::20d:3aff:fe04:4516/64 scope link valid_lft forever preferred_lft forever
Validation (Ubuntu 18.04+)
To ensure you're able to connect to the internet from your secondary IP configuration via the public IP associated with it, use the following command:
ping -I 10.1.0.5 outlook.com
Note
For secondary IP configurations, you can only ping to the Internet if the configuration has a public IP address associated with it. For primary IP configurations, a public IP address isn't required to ping to the Internet.
For Linux VMs, when trying to validate outbound connectivity from a secondary NIC, you may need to add appropriate routes. There are many ways to do this. Please see appropriate documentation for your Linux distribution. The following is one method to accomplish this:
echo 150 custom >> /etc/iproute2/rt_tables
ip rule add from 10.1.0.5 lookup custom
ip route add default via 10.1.0.1 dev eth2 table custom
Ensure you replace:
10.1.0.5 with the private IP address that has a public IP address associated to it
10.1.0.1 to your default gateway
eth2 to the name of your secondary NIC
Red Hat Enterprise Linux and others
Expand
Open a terminal window.
Ensure you're the root user. If you aren't, enter the following command:
sudo -iEnter your password and follow instructions as prompted. Once you're the root user, go to the network scripts folder with the following command:
cd /etc/sysconfig/network-scriptsList the related ifcfg files using the following command:
ls ifcfg-*You should see ifcfg-eth0 as one of the files.
To add an IP address, create a configuration file for it as shown below. Note that one file must be created for each IP configuration.
touch ifcfg-eth0:0Open the ifcfg-eth0:0 file with the following command:
vi ifcfg-eth0:0Add content to the file, eth0:0 in this case, with the following command. Replace
10.1.0.5with your additional private IP address and subnet mask.DEVICE=eth0:0 BOOTPROTO=static ONBOOT=yes IPADDR=10.1.0.5 NETMASK=255.255.255.0Save the file with the following command:
:wqTo add additional private IP addresses to the network configuration, create additional config files and add the IP information into the file.
touch ifcfg-eth0:1vi ifcfg-eth0:1DEVICE=eth0:1 BOOTPROTO=static ONBOOT=yes IPADDR=10.1.0.6 NETMASK=255.255.255.0:wqRestart the network services and make sure the changes are successful by running the following commands:
systemctl restart NetworkManager.service ifconfigYou should see the IP address or addresses you added in the list returned.
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.1.0.4 netmask 255.255.255.0 broadcast 10.1.0.255 inet6 fe80::6245:bdff:fe7d:704a prefixlen 64 scopeid 0x20<link> ether 60:45:bd:7d:70:4a txqueuelen 1000 (Ethernet) RX packets 858 bytes 244215 (238.4 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1021 bytes 262077 (255.9 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eth0:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.1.0.5 netmask 255.255.255.0 broadcast 10.1.0.255 ether 60:45:bd:7d:70:4a txqueuelen 1000 (Ethernet) eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.1.0.6 netmask 255.255.255.0 broadcast 10.1.0.255 ether 60:45:bd:7d:70:4a txqueuelen 1000 (Ethernet)
Validation (Red Hat and others)
To ensure you're able to connect to the internet from your secondary IP configuration via the public IP associated with it, use the following command:
ping -I 10.0.0.5 outlook.com
Note
For secondary IP configurations, you can only ping to the Internet if the configuration has a public IP address associated with it. For primary IP configurations, a public IP address is not required to ping to the Internet.
For Linux VMs, when attempting to validate outbound connectivity from a secondary NIC, you may need to add appropriate routes. Please see appropriate documentation for your Linux distribution. The following is one method to accomplish this:
echo 150 custom >> /etc/iproute2/rt_tables
ip rule add from 10.1.0.5 lookup custom
ip route add default via 10.1.0.1 dev eth2 table custom
Ensure to replace:
10.0.0.5 with the private IP address that has a public IP address associated to it
10.0.0.1 to your default gateway
eth2 to the name of your secondary NIC
Debian GNU/Linux
Expand
We recommend looking at the latest documentation for your Linux distribution.
Open a terminal window.
Ensure you're the root user. If you aren't, enter the following command:
sudo -iUpdate the configuration file of the network interface (assuming ‘eth0’).
Keep the existing line item for dhcp. The primary IP address remains configured as it was previously.
Add a configuration for an additional static IP address with the following commands:
cd /etc/network/interfaces.d/ lsYou should see a .cfg file.
Open the file. You should see the following lines at the end of the file:
auto eth0 iface eth0 inet dhcpAdd the following lines after the lines that exist in the file. Replace
10.1.0.5with your private IP address and subnet mask.iface eth0 inet static address 10.1.0.5 netmask 255.255.255.0To add additional private IP addresses, edit the file and add the new private IP addresses on subsequent lines:
iface eth0 inet static address 10.1.0.5 netmask 255.255.255.0 iface eth0 inet static address 10.1.0.6 netmask 255.255.255.0Save the file by using the following command:
:wqRestart networking services for the changes to take effect. For Debian 8 and above, this can be done using below command :
systemctl restart networkingFor prior versions of Debian, you can use below commands:
service networking restartVerify the IP address is added to the network interface with the following command:
ip addr list eth0You should see the IP address you added as part of the list. Example:
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:0d:3a:04:45:16 brd ff:ff:ff:ff:ff:ff inet 10.1.0.5/24 brd 10.1.0.255 scope global eth0 valid_lft forever preferred_lft forever inet 10.1.0.6/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet 10.1.0.4/24 brd 10.1.0.255 scope global secondary eth0 valid_lft forever preferred_lft forever inet6 fe80::20d:3aff:fe04:4516/64 scope link valid_lft forever preferred_lft forever
Validation (Debian GNU/Linux)
To ensure you're able to connect to the internet from your secondary IP configuration via the public IP associated with it, use the following command:
ping -I 10.1.0.5 outlook.com
Note
For secondary IP configurations, you can only ping to the Internet if the configuration has a public IP address associated with it. For primary IP configurations, a public IP address is not required to ping to the Internet.
For Linux VMs, when attempting to validate outbound connectivity from a secondary NIC, you may need to add appropriate routes. See appropriate documentation for your Linux distribution. The following is one method to accomplish this:
echo 150 custom >> /etc/iproute2/rt_tables
ip rule add from 10.1.0.5 lookup custom
ip route add default via 10.1.0.1 dev eth2 table custom
Ensure to replace:
10.1.0.5 with the private IP address that has a public IP address associated to it
10.1.0.1 to your default gateway
eth2 to the name of your secondary NIC
Next steps
- Learn more about public IP addresses in Azure.
- Learn more about private IP addresses in Azure.
- Learn how to Configure IP addresses for an Azure network interface.
Σχόλια
Σύντομα διαθέσιμα: Καθ' όλη τη διάρκεια του 2024 θα καταργήσουμε σταδιακά τα ζητήματα GitHub ως μηχανισμό ανάδρασης για το περιεχόμενο και θα το αντικαταστήσουμε με ένα νέο σύστημα ανάδρασης. Για περισσότερες πληροφορίες, ανατρέξτε στο θέμα: https://aka.ms/ContentUserFeedback.
Υποβολή και προβολή σχολίων για