Specify connection parameters
Before you use a connector in Azure Logic Apps, Microsoft Power Automate, or Microsoft Power Apps, you need to create a connection by authenticating to the backend service. This information on how the authentication with the backend service happens, needs to be defined while creating the connector as part of connection parameters. When creating a custom connector with the user nterface on the Power Automate or Power Apps portal, in the Security tab, you can specify which type of authentication you want to use when creating the connection.
Authentication types
The different types of authentication that are currently supported are:
- No authentication
- Basic authentication
- API Key based authentication
- Oauth 2.0
No authentication
The user doesn't need authentication to create a connection to the connector. An anonymous user can use your connector in this case.
Basic authentication
This is the simplest type of authentication. The user just has to provide the username and password to create the connection.
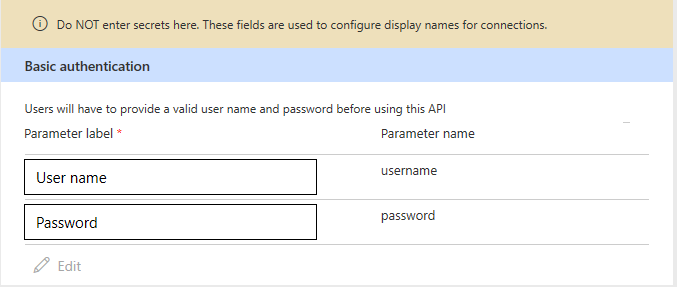
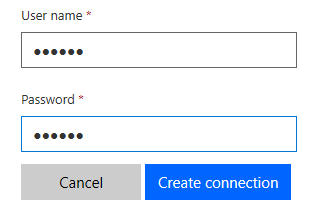
The values you enter under Parameter label are the names for the "username" and "password" fields that the user sees while creating the connection. For the previous example, this is what the user sees when creating a connection:
Api Key based authentication
The user doesn't need to provide the API key while creating the connection. The Parameter location field gives you the option to send the API key to your service in headers or a query string when the request is made.
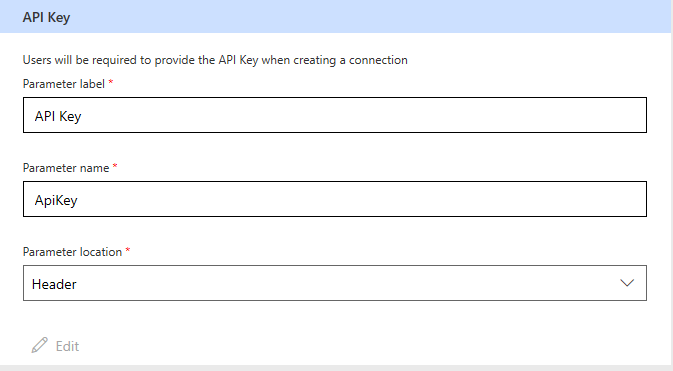
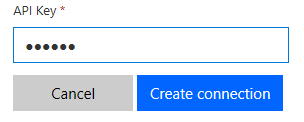
The value you enter under Parameter label is the name of the field the user sees. For example, the following image shows to the user at connection creation time. When a request is made to your service, a header with name 'ApiKey' and value as entered by the user are added to the request.
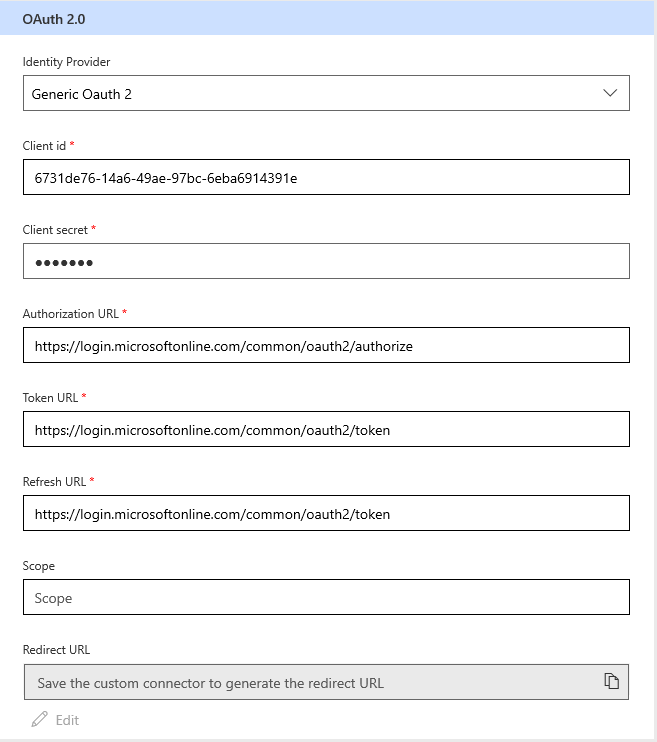
Oauth 2.0
This is the most frequently used type, which uses the Oauth 2 authentication framework to authenticate with the service. Before using this authentication type, you need to register your application with the service so that it can receive access tokens for the users. For example, Register the application in Microsoft Entra ID shows how to register an application with the Microsoft Entra ID service. You need to provide following information:
Identity Provider: The user interface currently supports multiple identity providers. The general ones are Generic Oauth 2, which can be used for any service, and Microsoft Entra ID, which can be used for all Azure services. A few specific identity providers like Facebook, GitHub, Google, and so on, are also supported.
Client id: The client ID of the application you have registered with the service.
Client secret: The client secret of the application you have registered with the service.
Authorization Url: The API authorization endpoint to authenticate with the service.
Token Url: The API endpoint to get the access token after the authorization has been done.
Refresh Url: The API endpoint to refresh the access token once it has expired.
Note
Currently, client credentials grant type is not supported by custom connectors.
The following example demonstrates using the Generic Oauth 2 identity provider to authenticate with the Microsoft Entra ID service.
During the connection creation process, the user is asked to enter the credentials for login to the service. These credentials are used by the application to get an authorization token. For every request, this authorization token is sent to your service through the Authorization header.
Provide feedback
We greatly appreciate feedback on issues with our connector platform, or new feature ideas. To provide feedback, go to Submit issues or get help with connectors and select your feedback type.