Enable attack surface reduction rules
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender Antivirus
Platforms
- Windows
Tip
Want to experience Defender for Endpoint? Sign up for a free trial.
Attack surface reduction rules help prevent actions that malware often abuses to compromise devices and networks.
Requirements
Attack surface reduction features across Windows versions
You can set attack surface reduction rules for devices that are running any of the following editions and versions of Windows:
- Windows 11 Pro
- Windows 11 Enterprise
- Windows 10 Pro, version 1709 or later
- Windows 10 Enterprise, version 1709 or later
- Windows Server, version 1803 (Semi-Annual Channel) or later
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
To use the entire feature-set of attack surface reduction rules, you need:
- Microsoft Defender Antivirus as primary AV (real-time protection on)
- Cloud-Delivery Protection on (some rules require that)
- Windows 10 Enterprise E5 or E3 License
Although attack surface reduction rules don't require a Windows E5 license, with a Windows E5 license, you get advanced management capabilities including monitoring, analytics, and workflows available in Defender for Endpoint, as well as reporting and configuration capabilities in the Microsoft Defender XDR portal. These advanced capabilities aren't available with an E3 license, but you can still use Event Viewer to review attack surface reduction rule events.
Each attack surface reduction rule contains one of four settings:
- Not configured | Disabled: Disable the attack surface reduction rule
- Block: Enable the attack surface reduction rule
- Audit: Evaluate how the attack surface reduction rule would impact your organization if enabled
- Warn: Enable the attack surface reduction rule but allow the end user to bypass the block
We recommend using attack surface reduction rules with a Windows E5 license (or similar licensing SKU) to take advantage of the advanced monitoring and reporting capabilities available in Microsoft Defender for Endpoint (Defender for Endpoint). However, if you have another license, such as Windows Professional or Windows E3 that doesn't include advanced monitoring and reporting capabilities, you can develop your own monitoring and reporting tools on top of the events that are generated at each endpoint when attack surface reduction rules are triggered (for example, Event Forwarding).
Tip
To learn more about Windows licensing, see Windows 10 Licensing and get the Volume Licensing guide for Windows 10.
You can enable attack surface reduction rules by using any of these methods:
- Microsoft Intune
- Mobile Device Management (MDM)
- Microsoft Configuration Manager
- Group Policy
- PowerShell
Enterprise-level management such as Intune or Microsoft Configuration Manager is recommended. Enterprise-level management overwrites any conflicting Group Policy or PowerShell settings on startup.
Exclude files and folders from attack surface reduction rules
You can exclude files and folders from being evaluated by most attack surface reduction rules. This means that even if an attack surface reduction rule determines the file or folder contains malicious behavior, it doesn't block the file from running.
Important
Excluding files or folders can severely reduce the protection provided by attack surface reduction rules. Excluded files will be allowed to run, and no report or event will be recorded. If attack surface reduction rules are detecting files that you believe shouldn't be detected, you should use audit mode first to test the rule. An exclusion is applied only when the excluded application or service starts. For example, if you add an exclusion for an update service that is already running, the update service continues to trigger events until the service is stopped and restarted.
When adding exclusions, keep these points in mind:
- Exclusions are typically based on individual files or folders (using folder paths or the full path of the file to be excluded).
- Exclusion paths can use environment variables and wildcards. See Use wildcards in the file name and folder path or extension exclusion lists
- When deployed through Group Policy or PowerShell, exclusions apply to all attack surface reduction rules. Using Intune, it is possible to configure an exclusion for a specific attack surface reduction rule. See Configure attack surface reduction rules per-rule exclusions
- Exclusions can be added based on certificate and file hashes, by allowing specified Defender for Endpoint file and certificate indicators. See Manage indicators.
Policy Conflict
If a conflicting policy is applied via MDM and GP, the setting applied from GP takes precedence.
Attack surface reduction rules for managed devices now support behavior for merger of settings from different policies, to create a superset of policy for each device. Only the settings that aren't in conflict are merged, while those that are in conflict aren't added to the superset of rules. Previously, if two policies included conflicts for a single setting, both policies were flagged as being in conflict, and no settings from either profile would be deployed. Attack surface reduction rule merge behavior is as follows:
- Attack surface reduction rules from the following profiles are evaluated for each device to which the rules apply:
- Devices > Configuration profiles > Endpoint protection profile > Microsoft Defender Exploit Guard > Attack Surface Reduction.
- Endpoint security > Attack surface reduction policy > Attack surface reduction rules.
- Endpoint security > Security baselines > Microsoft Defender ATP Baseline > Attack Surface Reduction Rules.
- Settings that don't have conflicts are added to a superset of policy for the device.
- When two or more policies have conflicting settings, the conflicting settings aren't added to the combined policy, while settings that don't conflict are added to the superset policy that applies to a device.
- Only the configurations for conflicting settings are held back.
- Attack surface reduction rules from the following profiles are evaluated for each device to which the rules apply:
Configuration methods
This section provides configuration details for the following configuration methods:
The following procedures for enabling attack surface reduction rules include instructions for how to exclude files and folders.
Intune
Device Configuration Profiles
Select Device configuration > Profiles. Choose an existing endpoint protection profile or create a new one. To create a new one, select Create profile and enter information for this profile. For Profile type, select Endpoint protection. If you've chosen an existing profile, select Properties and then select Settings.
In the Endpoint protection pane, select Windows Defender Exploit Guard, then select Attack Surface Reduction. Select the desired setting for each attack surface reduction rule.
Under Attack Surface Reduction exceptions, enter individual files and folders. You can also select Import to import a CSV file that contains files and folders to exclude from attack surface reduction rules. Each line in the CSV file should be formatted as follows:
C:\folder,%ProgramFiles%\folder\file,C:\pathSelect OK on the three configuration panes. Then select Create if you're creating a new endpoint protection file or Save if you're editing an existing one.
Endpoint security policy
Select Endpoint Security > Attack surface reduction. Choose an existing attack surface reduction rule or create a new one. To create a new one, select Create Policy and enter information for this profile. For Profile type, select Attack surface reduction rules. If you've chosen an existing profile, select Properties and then select Settings.
In the Configuration settings pane, select Attack Surface Reduction and then select the desired setting for each attack surface reduction rule.
Under List of additional folders that need to be protected, List of apps that have access to protected folders, and Exclude files and paths from attack surface reduction rules, enter individual files and folders. You can also select Import to import a CSV file that contains files and folders to exclude from attack surface reduction rules. Each line in the CSV file should be formatted as follows:
C:\folder,%ProgramFiles%\folder\file,C:\pathSelect Next on the three configuration panes, then select Create if you're creating a new policy or Save if you're editing an existing policy.
Custom profile in Intune
You can use Microsoft Intune OMA-URI to configure custom attack surface reduction rules. The following procedure uses the rule Block abuse of exploited vulnerable signed drivers for the example.
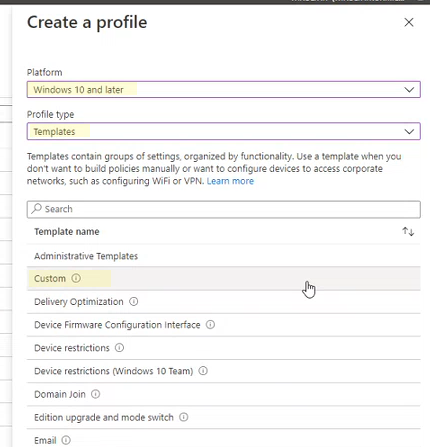
Open the Microsoft Intune admin center. In the Home menu, click Devices, select Configuration profiles, and then click Create profile.
In Create a profile, in the following two drop-down lists, select the following:
- In Platform, select Windows 10 and later
- In Profile type, select Templates
- If attack surface reduction rules are already set through Endpoint security, in Profile type, select Settings Catalog.
Select Custom, and then select Create.
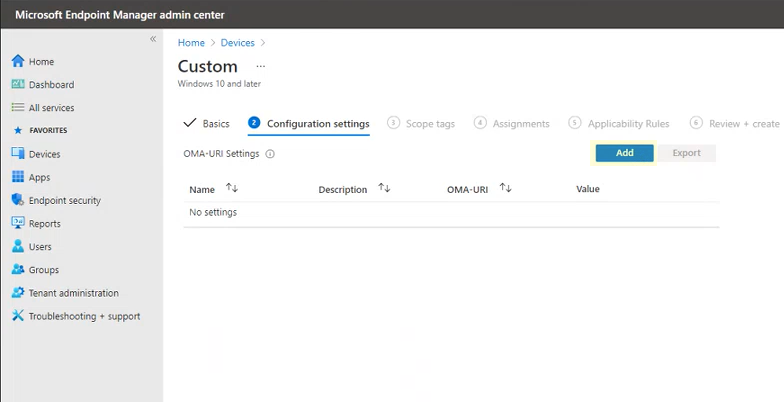
The Custom template tool opens to step 1 Basics. In 1 Basics, in Name, type a name for your template, and in Description you can type a description (optional).
Click Next. Step 2 Configuration settings opens. For OMA-URI Settings, click Add. Two options now appear: Add and Export.
Click Add again. The Add Row OMA-URI Settings opens. In Add Row, do the following:
In Name, type a name for the rule.
In Description, type a brief description.
In OMA-URI, type or paste the specific OMA-URI link for the rule that you're adding. Refer to the MDM section in this article for the OMA-URI to use for this example rule. For attack surface reduction rule GUIDS, see Per rule descriptions in the article: Attack surface reduction rules.
In Data type, select String.
In Value, type or paste the GUID value, the = sign and the State value with no spaces (GUID=StateValue). Where:
- 0: Disable (Disable the attack surface reduction rule)
- 1: Block (Enable the attack surface reduction rule)
- 2: Audit (Evaluate how the attack surface reduction rule would impact your organization if enabled)
- 6: Warn (Enable the attack surface reduction rule but allow the end-user to bypass the block)
Select Save. Add Row closes. In Custom, select Next. In step 3 Scope tags, scope tags are optional. Do one of the following:
- Select Select Scope tags, select the scope tag (optional) and then select Next.
- Or select Next
In step 4 Assignments, in Included Groups, for the groups that you want this rule to apply, select from the following options:
- Add groups
- Add all users
- Add all devices
In Excluded groups, select any groups that you want to exclude from this rule, and then select Next.
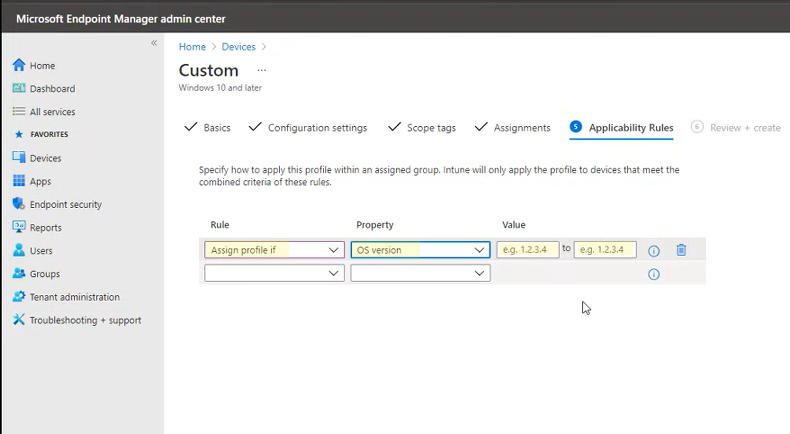
In step 5 Applicability Rules for the following settings, do the following:
In Rule, select either Assign profile if, or Don't assign profile if
In Property, select the property to which you want this rule to apply
In Value, enter the applicable value or value range
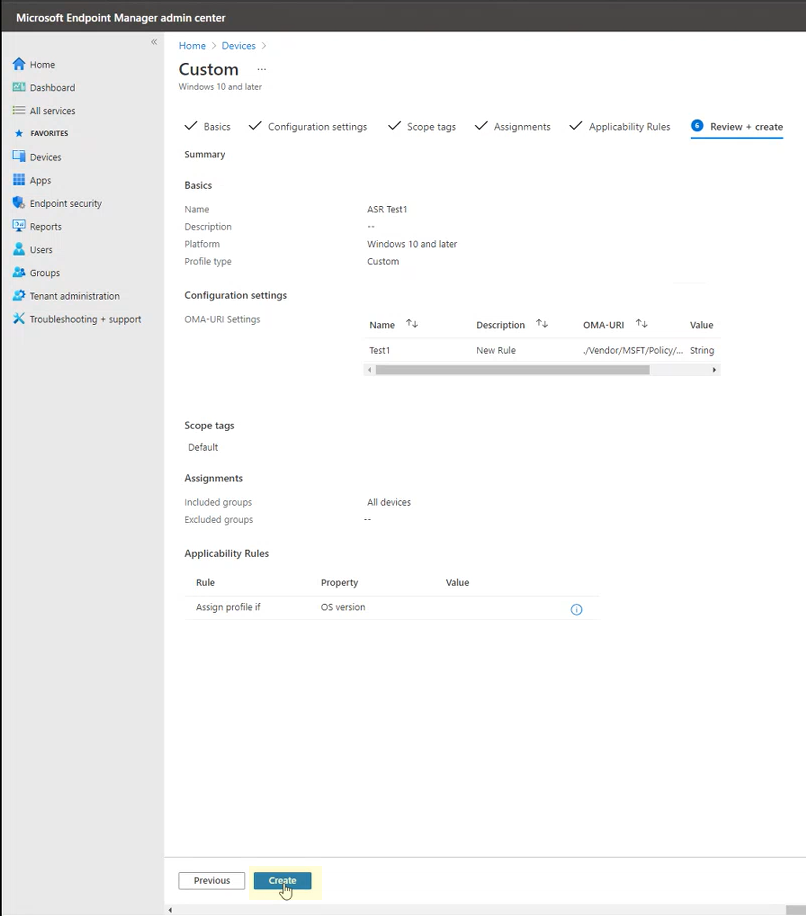
Select Next. In step 6 Review + create, review the settings and information you've selected and entered, and then select Create.
Rules are active and live within minutes.
Note
Conflict handling:
If you assign a device two different attack surface reduction policies, potential policy conflicts can occur, depending on whether rules are assigned different states, whether conflict management is in place, and whether the result is an error. Nonconflicting rules do not result in an error, and such rules are applied correctly. The first rule is applied, and subsequent nonconflicting rules are merged into the policy.
MDM
Use the ./Vendor/MSFT/Policy/Config/Defender/AttackSurfaceReductionRules configuration service provider (CSP) to individually enable and set the mode for each rule.
The following is a sample for reference, using GUID values for Attack surface reduction rules reference.
OMA-URI path: ./Vendor/MSFT/Policy/Config/Defender/AttackSurfaceReductionRules
Value: 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84=2|3b576869-a4ec-4529-8536-b80a7769e899=1|d4f940ab-401b-4efc-aadc-ad5f3c50688a=2|d3e037e1-3eb8-44c8-a917-57927947596d=1|5beb7efe-fd9a-4556-801d-275e5ffc04cc=0|be9ba2d9-53ea-4cdc-84e5-9b1eeee46550=1
The values to enable (Block), disable, warn, or enable in audit mode are:
- 0: Disable (Disable the attack surface reduction rule)
- 1: Block (Enable the attack surface reduction rule)
- 2: Audit (Evaluate how the attack surface reduction rule would impact your organization if enabled)
- 6: Warn (Enable the attack surface reduction rule but allow the end-user to bypass the block). Warn mode is available for most of the attack surface reduction rules.
Use the ./Vendor/MSFT/Policy/Config/Defender/AttackSurfaceReductionOnlyExclusions configuration service provider (CSP) to add exclusions.
Example:
OMA-URI path: ./Vendor/MSFT/Policy/Config/Defender/AttackSurfaceReductionOnlyExclusions
Value: c:\path|e:\path|c:\Exclusions.exe
Note
Be sure to enter OMA-URI values without spaces.
Microsoft Configuration Manager
In Microsoft Configuration Manager, go to Assets and Compliance > Endpoint Protection > Windows Defender Exploit Guard.
Select Home > Create Exploit Guard Policy.
Enter a name and a description, select Attack Surface Reduction, and select Next.
Choose which rules will block or audit actions and select Next.
Review the settings and select Next to create the policy.
After the policy is created, select Close.
Warning
There is a known issue with the applicability of Attack Surface Reduction on Server OS versions which is marked as compliant without any actual enforcement. Currently, there is no ETA for when this will be fixed.
Group Policy
Warning
If you manage your computers and devices with Intune, Configuration Manager, or other enterprise-level management platform, the management software will overwrite any conflicting Group Policy settings on startup.
On your Group Policy management computer, open the Group Policy Management Console, right-click the Group Policy Object you want to configure and select Edit.
In the Group Policy Management Editor, go to Computer configuration and select Administrative templates.
Expand the tree to Windows components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Attack surface reduction.
Select Configure Attack surface reduction rules and select Enabled. You can then set the individual state for each rule in the options section. Select Show... and enter the rule ID in the Value name column and your chosen state in the Value column as follows:
0: Disable (Disable the attack surface reduction rule)
1: Block (Enable the attack surface reduction rule)
2: Audit (Evaluate how the attack surface reduction rule would impact your organization if enabled)
6: Warn (Enable the attack surface reduction rule but allow the end-user to bypass the block)
To exclude files and folders from attack surface reduction rules, select the Exclude files and paths from Attack surface reduction rules setting and set the option to Enabled. Select Show and enter each file or folder in the Value name column. Enter 0 in the Value column for each item.
Warning
Do not use quotes as they are not supported for either the Value name column or the Value column. The rule ID should not have any leading or trailing spaces.
PowerShell
Warning
If you manage your computers and devices with Intune, Configuration Manager, or another enterprise-level management platform, the management software overwrites any conflicting PowerShell settings on startup.
Type powershell in the Start menu, right-click Windows PowerShell and select Run as administrator.
Type one of the following cmdlets. (For more information, such as rule ID, refer to Attack surface reduction rules reference.)
Task PowerShell cmdlet Enable attack surface reduction rules Set-MpPreference -AttackSurfaceReductionRules_Ids <rule ID> -AttackSurfaceReductionRules_Actions EnabledEnable attack surface reduction rules in audit mode Add-MpPreference -AttackSurfaceReductionRules_Ids <rule ID> -AttackSurfaceReductionRules_Actions AuditModeEnable attack surface reduction rules in warn mode Add-MpPreference -AttackSurfaceReductionRules_Ids <rule ID> -AttackSurfaceReductionRules_Actions WarnEnable attack surface reduction Block abuse of exploited vulnerable signed drivers Add-MpPreference -AttackSurfaceReductionRules_Ids 56a863a9-875e-4185-98a7-b882c64b5ce5 -AttackSurfaceReductionRules_Actions EnabledTurn off attack surface reduction rules Add-MpPreference -AttackSurfaceReductionRules_Ids <rule ID> -AttackSurfaceReductionRules_Actions DisabledImportant
You must specify the state individually for each rule, but you can combine rules and states in a comma-separated list.
In the following example, the first two rules are enabled, the third rule is disabled, and the fourth rule is enabled in audit mode:
Set-MpPreference -AttackSurfaceReductionRules_Ids <rule ID 1>,<rule ID 2>,<rule ID 3>,<rule ID 4> -AttackSurfaceReductionRules_Actions Enabled, Enabled, Disabled, AuditModeYou can also use the
Add-MpPreferencePowerShell verb to add new rules to the existing list.Warning
Set-MpPreferenceoverwrites the existing set of rules. If you want to add to the existing set, useAdd-MpPreferenceinstead. You can obtain a list of rules and their current state by usingGet-MpPreference.To exclude files and folders from attack surface reduction rules, use the following cmdlet:
Add-MpPreference -AttackSurfaceReductionOnlyExclusions "<fully qualified path or resource>"Continue to use
Add-MpPreference -AttackSurfaceReductionOnlyExclusionsto add more files and folders to the list.Important
Use
Add-MpPreferenceto append or add apps to the list. Using theSet-MpPreferencecmdlet will overwrite the existing list.
Related articles
- Attack surface reduction rules reference
- Evaluate attack surface reduction
- Attack surface reduction FAQ
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.