Users in Microsoft Entra ID have two distinct sets of contact information:
- Public profile contact information, which is managed in the user profile and visible to members of your organization. For users synced from on-premises Active Directory, this information is managed in on-premises Windows Server Active Directory Domain Services.
- Authentication methods, which are always kept private and only used for authentication, including multifactor authentication. Administrators can manage these methods in a user's authentication method blade and users can manage their methods in Security Info page of MyAccount.
When managing Microsoft Entra multifactor authentication methods for your users, Authentication administrators can:
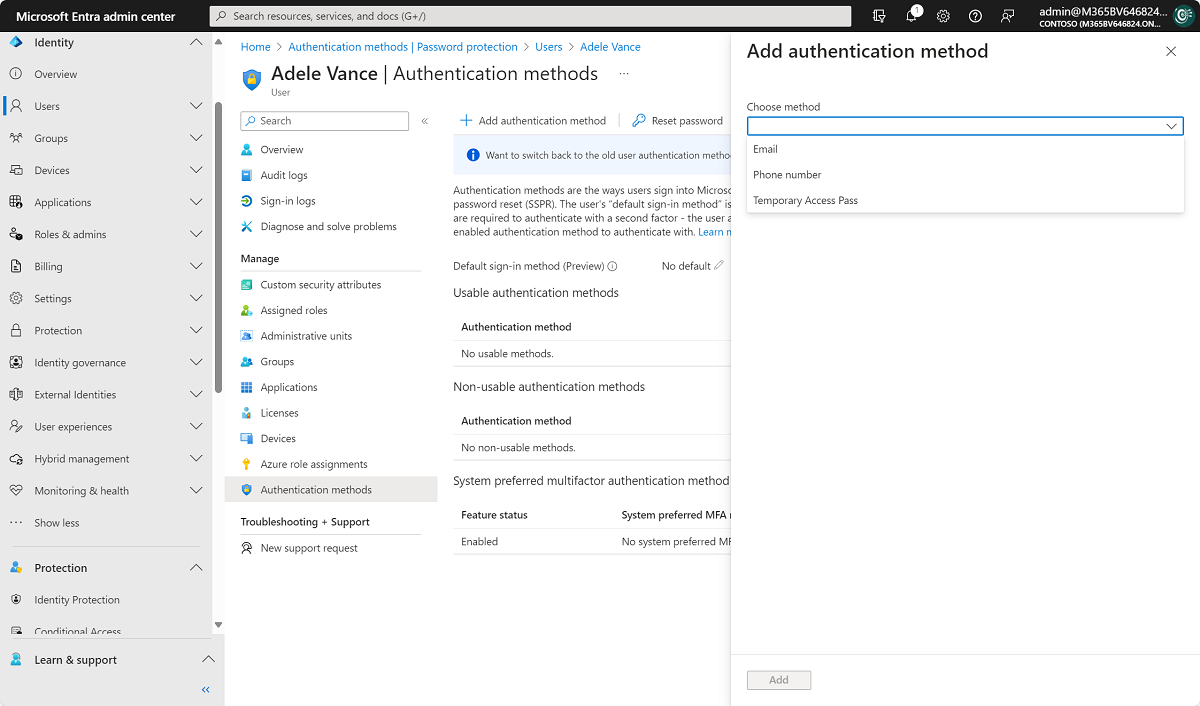
- Add authentication methods for a specific user, including phone numbers used for MFA.
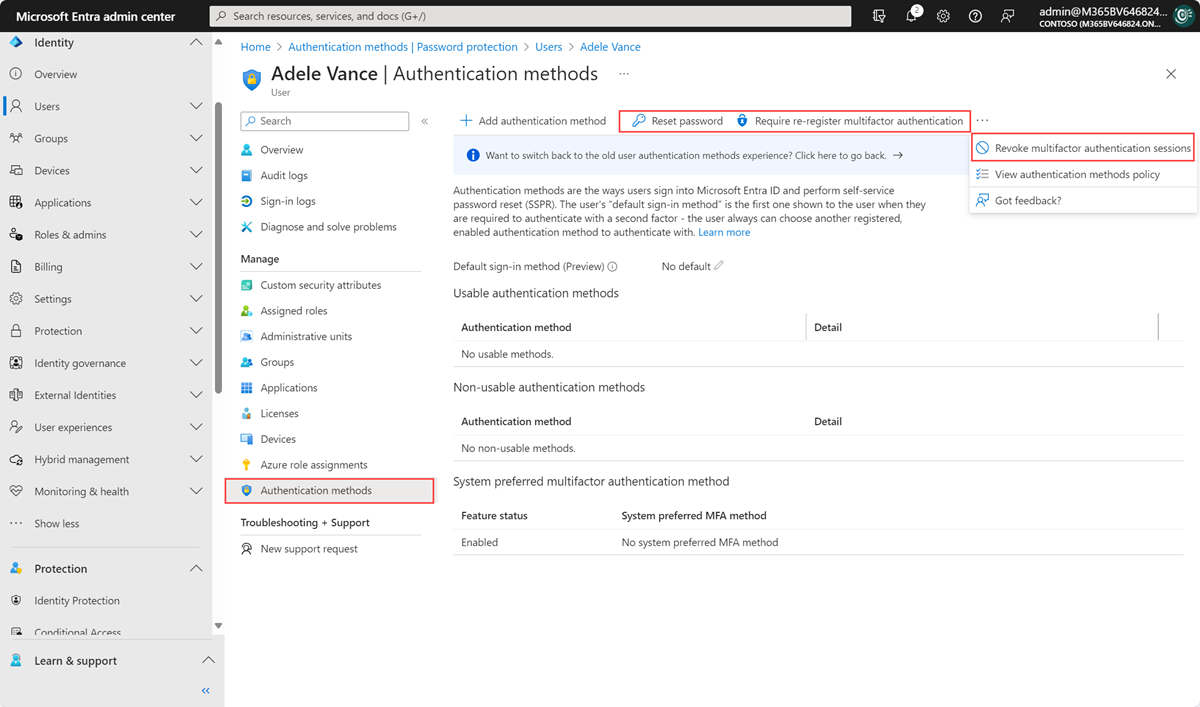
- Reset a user's password.
- Require a user to re-register for MFA.
- Revoke existing MFA sessions.
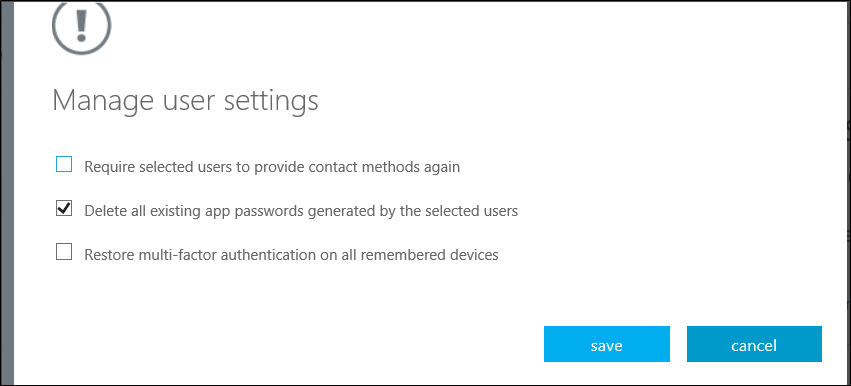
- Delete a user's existing app passwords
Note
The screenshots in this topic show how to manage user authentication methods by using an updated experience in the Microsoft Entra admin center. There's also a legacy experience, and admins can toggle between the two using a banner in the admin center. The modern experience has full parity with the legacy experience, and it manages modern methods like Temporary Access Pass, passkeys, and other settings. The legacy experience in the Microsoft Entra admin center will be retired starting Oct 31, 2024. There's no action required by organizations before the retirement.