συμβάν
9 Απρ, 3 μ.μ. - 10 Απρ, 12 μ.μ.
Κωδικοποιήστε το μέλλον με τεχνητή νοημοσύνη και συνδεθείτε με συναδέλφους java και ειδικούς στο JDConf 2025.
Εγγραφή τώραΑυτό το πρόγραμμα περιήγησης δεν υποστηρίζεται πλέον.
Κάντε αναβάθμιση σε Microsoft Edge για να επωφεληθείτε από τις τελευταίες δυνατότητες, τις ενημερώσεις ασφαλείας και την τεχνική υποστήριξη.
Conditional Access is widely used by our customers to stay secure by applying the right access controls in the right circumstances. However one of the challenges with deploying a Conditional Access policy in your organization is determining the impact to end users. It can be difficult to anticipate the number and names of users impacted by common security initiatives. These initiatives might include: blocking legacy authentication, requiring multifactor authentication for a population of users, or implementing sign-in risk policies.
Report-only mode is a new Conditional Access policy state that allows administrators to evaluate the impact of Conditional Access policies before enabling them in their environment.
Προειδοποίηση
Policies in report-only mode that require compliant devices may prompt users on Mac, iOS, and Android to select a device certificate during policy evaluation, even though device compliance is not enforced. These prompts may repeat until the device is made compliant. To prevent end users from receiving prompts during sign-in, exclude device platforms Mac, iOS and Android from report-only policies that perform device compliance checks. Note that report-only mode is not applicable for Conditional Access policies with "User Actions" scope.
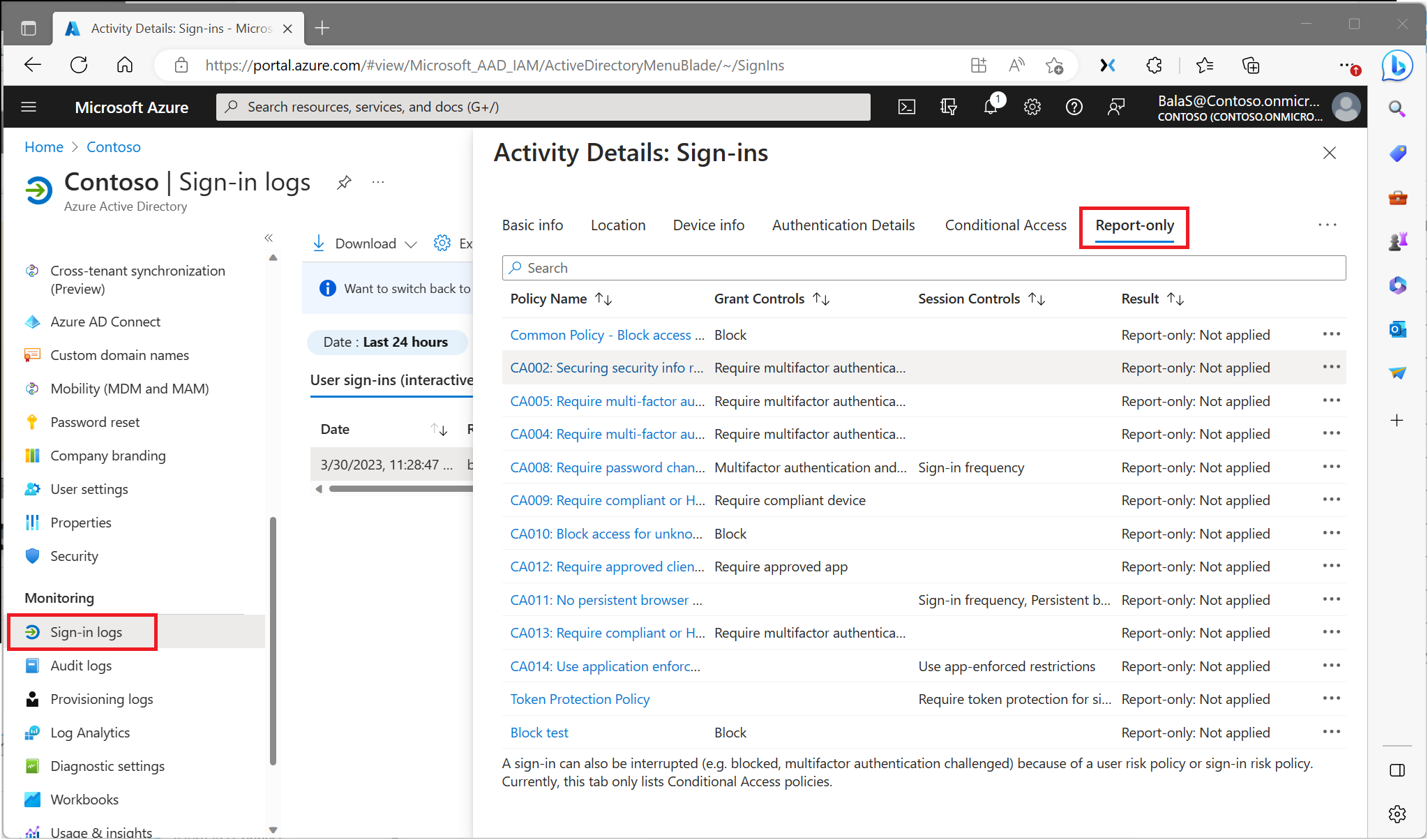
When a policy in report-only mode is evaluated for a given sign-in, there are four new possible result values:
| Result | Description |
|---|---|
| Report-only: Success | All configured policy conditions, required non-interactive grant controls, and session controls were satisfied. For example, a multifactor authentication requirement is satisfied by an MFA claim already present in the token, or a compliant device policy is satisfied by performing a device check on a compliant device. |
| Report-only: Failure | All configured policy conditions were satisfied but not all the required non-interactive grant controls or session controls were satisfied. For example, a policy applies to a user where a block control is configured, or a device fails a compliant device policy. |
| Report-only: User action required | All configured policy conditions were satisfied but user action would be required to satisfy the required grant controls or session controls. With report-only mode, the user isn't prompted to satisfy the required controls. For example, users aren't prompted for multifactor authentication challenges or terms of use. |
| Report-only: Not applied | Not all configured policy conditions were satisfied. For example, the user is excluded from the policy or the policy only applies to certain trusted named locations. |
Administrators have the capability to create multiple policies in report-only mode, so it's necessary to understand both the individual impact of each policy and the combined impact of multiple policies evaluated together. The new Conditional Access Insights workbook enables administrators to visualize Conditional Access queries and monitor the impact of a policy for a given time range, set of applications, and users.
συμβάν
9 Απρ, 3 μ.μ. - 10 Απρ, 12 μ.μ.
Κωδικοποιήστε το μέλλον με τεχνητή νοημοσύνη και συνδεθείτε με συναδέλφους java και ειδικούς στο JDConf 2025.
Εγγραφή τώραΕκπαίδευση
Λειτουργική μονάδα
Plan, implement, and administer Conditional Access - Training
Conditional Access gives a fine granularity of control over which users can do specific activities, access which resources, and how to ensure data and systems are safe.
Πιστοποίηση
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.