Σημείωση
Η πρόσβαση σε αυτή τη σελίδα απαιτεί εξουσιοδότηση. Μπορείτε να δοκιμάσετε να συνδεθείτε ή να αλλάξετε καταλόγους.
Η πρόσβαση σε αυτή τη σελίδα απαιτεί εξουσιοδότηση. Μπορείτε να δοκιμάσετε να αλλάξετε καταλόγους.
Security baselines are standardized documents for Azure product offerings, describing the available security capabilities and the optimal security configurations to help you strengthen security through improved tooling, tracking, and security features. We currently have service baselines available for Azure only.
Security baselines for Azure focus on cloud-centric control areas in Azure environments. These controls are consistent with well-known industry standards such as: Center for Internet Security (CIS) or National Institute for Standards in Technology (NIST). Our baselines provide guidance for the control areas listed in the Microsoft cloud security benchmark v1.
Each baseline consists of the following components:
- How does a service behave?
- Which security features are available?
- What configurations are recommended to secure the service?
What's new in the Microsoft cloud security benchmark v1 baselines?
Note
Microsoft cloud security benchmark is the successor of Azure Security Benchmark (ASB), which was rebranded in October 2022.
The v1 baselines will follow the Microsoft cloud security benchmark v1 control requirements, which also map to newer industry frameworks such as NIST and PCI. These baselines are security feature driven (unlike the baselines for the Azure Security Benchmarks v1 and v2), which is more intuitive and easier to use.
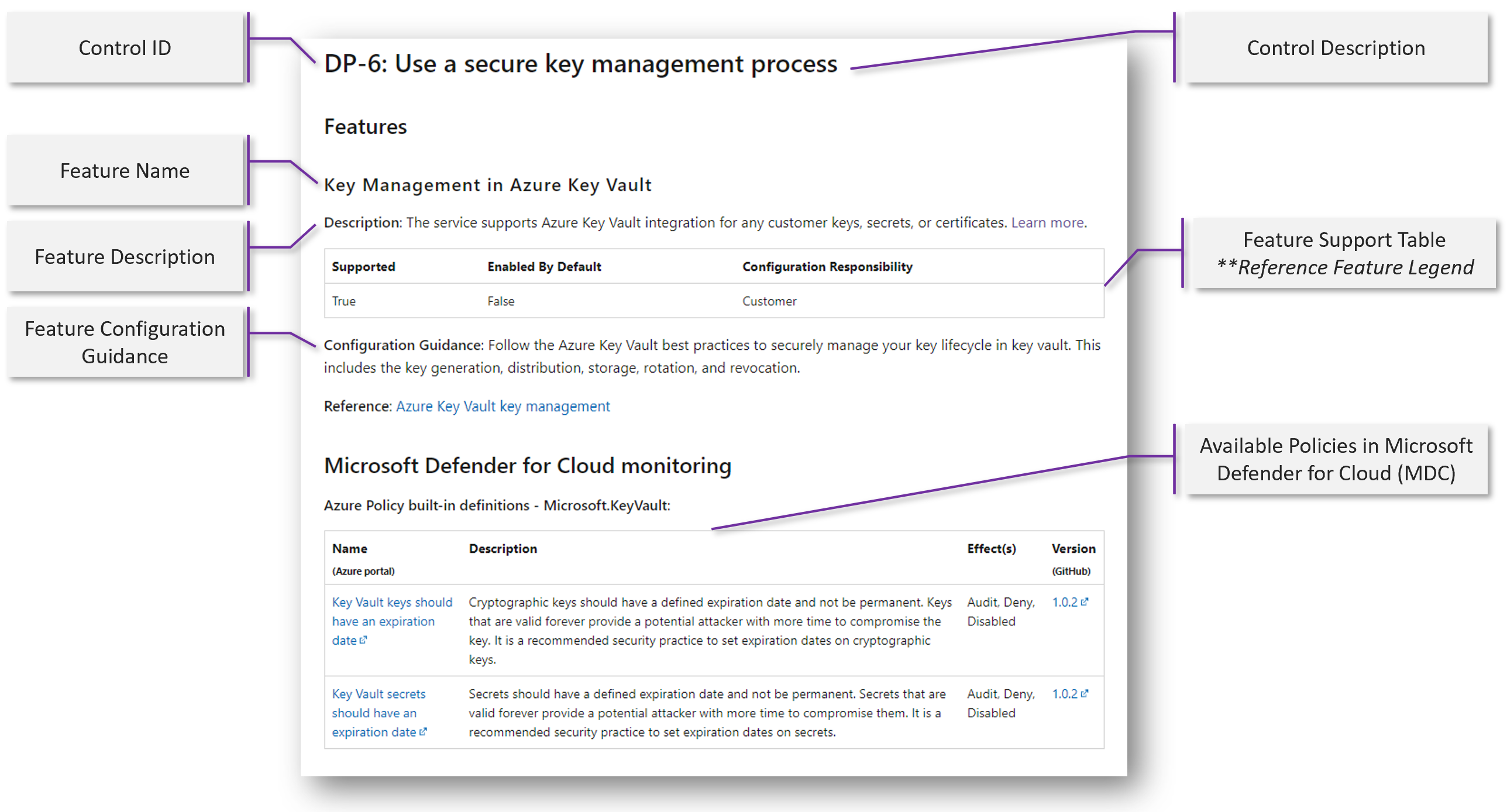
Each Security Benchmark control includes the following information, except where noted:
- Control ID: The Microsoft cloud security benchmark ID that corresponds to the control in the Microsoft cloud security benchmark.
- Feature: Security feature(s) that can help you meet that control requirement.
- Feature Description: A high-level description of the feature and how it fits into the product offering.
- Supported: A true/false value indicating if this feature is supported to secure this product offering.
- Enabled by Default: A true/false value indicating if this feature is enabled in a default deployment by Microsoft.
- Configuration Responsibility: Who is responsible for implementing the configuration guidance (where possible scenarios are Customer responsibility, Microsoft responsibility, or Shared responsibility).
- Configuration Guidance: Actionable guidance to implement the configurations.
- Microsoft Defender for Cloud monitoring Note: Microsoft Defender for Cloud policy / monitoring information. (Note: If a feature is not monitored by Microsoft Defender for Cloud for the service, this section is omitted.)
- Reference: A reference link to dive deeper into how to implement the configuration guidance.
Feature Legend:
| True | False | Not Applicable | |
|---|---|---|---|
| Supported | This feature is supported to secure this product offering. | This feature is not supported to secure this product offering. | This feature has no use cases in this product offering. |
| Enabled by Default | This feature’s security configuration is enabled or deployed by default. (Note: some default configurations can be changed or managed by customers.) | This feature’s security configurations are not enabled or deployed by default. The customer is responsible for implementing configuration guidance. | This feature is either not supported or not applicable to secure the product, so the feature's 'Enabled by Default' value is also marked as 'Not Applicable'. |
To access a list of all Security Benchmark controls, including controls that are not applicable to this specific service, see the full security baseline mapping file. There may occasionally be controls that are not applicable for various reasons—for example, IaaS/compute-centric controls (such as controls specific to OS configuration management) may not be applicable to PaaS services.
We welcome your feedback on the security baselines for Azure services. We encourage you to provide comments in the feedback area below. Or, if you prefer to share your input more privately with the us, email us at benchmarkfeedback@microsoft.com.