Securing the DevOps platform environment for Zero Trust
This article will help you, as a DevOps team member, to implement the Zero Trust principle of least privilege and secure the DevOps platform environment. It features content from our Securing Enterprise DevOps Environments eBook and highlights best practices for secret and certificate management.
Modern enterprises rely on DevOps platforms for deployment, including pipelines and production environments that developers require to be productive. In the past, application security methods didn't consider the increased attack surface that present day pipelines and production environments expose. As hackers shift left and target upstream tools, you need innovative approaches to secure your DevOps platform environments.
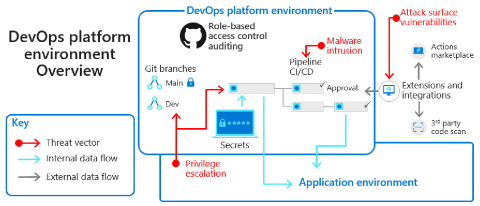
In the diagram below, notice that the DevOps platform environment connects to the application environment and to continuous integration and continuous delivery (CI/CD) pipeline extensions.
CICD pipeline extensions present hackers with opportunities to engage in privilege escalations from the application environment. Extensions and integrations increase attack surface vulnerabilities. It's critical to defend against malware intrusion threats.
How and why attackers target pipelines
Pipelines and production environments may be independent of standard application security practices and processes. They typically require high-level access credentials that can provide deep and meaningful access to attackers.
While attackers find new ways to compromise systems, the most common attack vectors for pipelines include:
- Extracting runtime variables and argument injection.
- Scripts that retrieve service principles or credentials from pipelines.
- Misconfigured personal access tokens that allow anyone with the key to access the DevOps platform environment.
- Vulnerabilities and misconfigurations in third-party integrated tools that require access to the code (often read-only, but sometimes write access). Integrated tools can include test frameworks, static application security testing (SAST), and dynamic application security testing (DAST).
Best practices for secret and certificate management
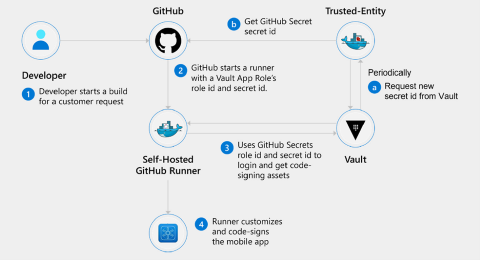
Avoiding a catastrophic breach can be as simple as effective secret management. The diagram below illustrates an example of effective secret, password, access token, and certificate management.
As shown in the above diagram, the developer starts a build for a customer request. GitHub then starts a runner with a Vault App Role's role ID and secret ID. The Trusted Entity periodically requests a new secret ID from the Vault and gets the GitHub Secret secret ID from GitHub. The Vault uses the GitHub Secrets role ID and secret ID to sign in and get code-signing assets. The Runner customizes and code-signs the mobile app.
The following best practices will help you to build a secure setup that minimizes secret and parameter exposure.
- Provide secure storage for secrets and certificates at each application lifecycle stage. Always develop as if it's an open-source project. Ensure that teams are storing secrets in key vaults rather than in the code or on team environments. Use the Azure Key Vault cloud service for securely storing and accessing secrets.
- Configure Azure to trust GitHub's OIDC as a federated identity. OpenID Connect (OIDC) allows your GitHub Actions workflows to access resources in Azure without needing to store the Azure credentials as long-lived GitHub secrets.
More best practices for DevOps environment security
To help defend against security incidents, below are more best practices to fortify your DevOps platform environments. Find a detailed discussion of these recommendations in our Securing Enterprise DevOps Environments eBook.
- Equip every DevOps platform environment with audit trails. Review audit logs to track who gained access, what change occurred, and the date/time for any active system. Specifically include DevOps platforms with CI/CD pipelines that flow into production. Audit trails for DevOps tools provide robust ways to remediate threats quicker, find and alert on suspicious activities to possible breaches or vulnerabilities, and find potential data or privilege misuse. Ensure granular control and audit trails are available across each environment.
- Secure the software supply chain. With every library you bring into your codebase, you expand the software supply chain and inherit dependencies from each open-source project or tool. With caution, remove unnecessary libraries and open-source components to reduce the attack surface of your software supply chain.
- Automate Infrastructure-as-Code (IaC) template scans. With IaC environments, it's easy to scan for misconfigurations, compliance audits, and policies issues. Implementing compliance checks and access controls raises the security posture of your entire infrastructure. Verify the security of third-party tool integrations that fulfill automation system requirements.
- Automate approval workflows. For any approval workflow to push code into production, certain automatic or manual checks must confirm security, business value, status, and quality of each request. These checks function as a gate between development and production to prevent denial-of-service attacks and hackers injecting code into production environments without flagging or triggering an alert.
- Allow only verified DevOps tool integrations. As in developer environments, DevOps tools come with extensions and integrations to make the DevOps team efficient and secure. Confirm that verified integrations require the least privilege possible to execute their work. Implement least privilege access when possible and ensure the right level of read/write permissions. Learn how to disable or limit GitHub Actions for your organization.
Next steps
- Securing the developer environment helps you to implement Zero Trust principles in your development environments with best practices for least privilege, branch security, and trusting tools, extensions, and integrations.
- Embedding Zero Trust security into your developer workflow helps you to innovate quickly and securely.
- Securing DevOps environments for Zero Trust describes best practices for securing your DevOps environments with a Zero Trust approach for preventing hackers from compromising developer boxes, infecting release pipelines with malicious scripts, and gaining access to production data via test environments.
- Implement Zero Trust principles as described in memorandum 22-09 (in support of US executive order 14028, Improving the Nation's Cyber Security) by using Microsoft Entra ID as a centralized identity management system.
- Accelerate and secure your code with Azure DevOps with tools that give developers the fastest and most secure code to cloud experience.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for