Use Defender for Cloud Apps Conditional Access app control
This article provides an overview of how to use Microsoft Defender for Cloud Apps app control to create access and session policies. Conditional Access app control provides real-time monitoring and control over user access to cloud apps.
Conditional Access app control usage flow (Preview)
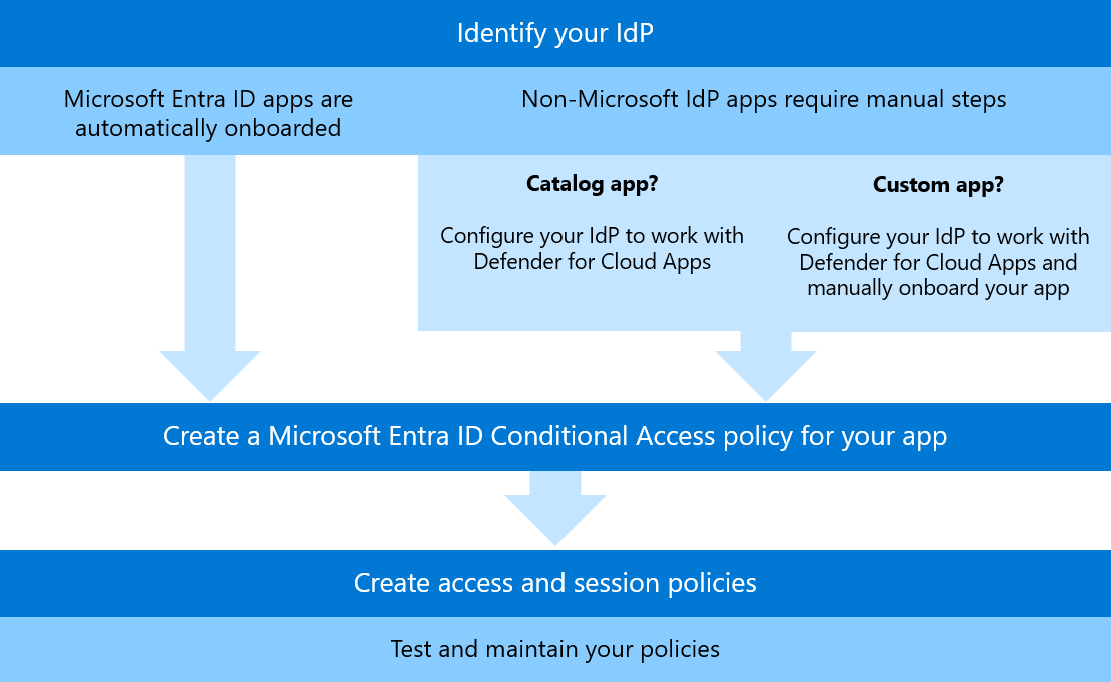
The following image shows the high level process for configuring and implementing Conditional Access app control:
Which identity provider are you using?
Before you start using Conditional Access app control, understand whether your apps are managed by Microsoft Entra or another identity provider (IdP).
Microsoft Entra apps are automatically onboarded for Conditional Access app control, and are immediately available for you to use in your access and session policy conditions (Preview). Can be manually onboarded before you can select them in your access and session policy conditions.
Apps that use non-Microsoft IdPs must be manually onboarded before you can select them in your access and session policy conditions.
If you're working with a catalog app from a non-Microsoft IdP, configure the integration between your IdP and Defender for Cloud Apps to onboard all catalog apps. For more information, see Onboard non-Microsoft IdP catalog apps for Conditional Access app control.
If you're working with custom apps, you need to both configure the integration between your IdP and Defender for Cloud Apps, and also onboard each custom app. For more information, see Onboard non-Microsoft IdP custom apps for Conditional Access app control.
Sample procedures
The following articles provide sample processes for configuring a non-Microsoft IdP to work with Defender for Cloud Apps:
Prerequisites:
- Ensure your firewall configurations allow traffic from all the IP addresses listed on Network requirements.
- Confirm that your application possesses a complete certificate chain. Incomplete or partial certificate chains may lead to unexpected behavior in applications when monitored with Conditional Access app control policies.
Create a Microsoft Entra ID Conditional Access policy
In order for your access or session policy to work, you must also have Microsoft Entra ID Conditional Access policy, which creates the permissions to control traffic.
We embedded a sample of this process in the access and session policy creation documentation.
For more information, see Conditional Access policies and Building a Conditional Access policy.
Create your access and session policies
After you've confirmed that your apps are onboarded, either automatically because they're Microsoft Entra ID apps, or manually, and you have a Microsoft Entra ID Conditional Access policy ready, you can continue with creating access and session policies for any scenario you need.
For more information, see:
Test your policies
Make sure to test your policies and update any conditions or settings as needed. For more information, see:
Related content
For more information, see Protect apps with Microsoft Defender for Cloud Apps Conditional Access app control.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for