Configure Exchange on-premises access for Intune
Important
Support for the on-premises Intune Exchange connector is ending on February 19, 2024. After this date, the Exchange connector will no longer sync with Intune. If you use the Exchange connector, we recommend taking one of the following actions before February 19, 2024:
This article shows you how to configure Conditional Access for Exchange on-premises based on device compliance.
If you have an Exchange Online Dedicated environment and need to find out whether it is in the new or the legacy configuration, contact your account manager. To control email access to Exchange on-premises or to your legacy Exchange Online Dedicated environment, configure Conditional Access to Exchange on-premises in Intune.
Before you begin
Before you can configure Conditional Access, verify the following configurations exist:
Your Exchange version is Exchange 2010 SP3 or later. Exchange server Client Access Server (CAS) array is supported.
You have installed and use the Exchange ActiveSync on-premises Exchange connector, which connects Intune to on-premises Exchange.
Important
Intune supports multiple on-premises Exchange connectors per subscription. However, each on-premises Exchange connector is specific to a single Intune tenant and cannot be used with any other tenant. If you have more than one on-premises Exchange organization, you can set up a separate connector for each Exchange organization.
The connector for an on-premises Exchange organization can install on any machine as long as that machine can communicate with the Exchange server.
The connector supports Exchange CAS environment. Intune supports installing the connector on the Exchange CAS server directly. We recommend you install it on a separate computer because of the additional load the connector puts on the server. When configuring the connector, you must set it up to communicate to one of the Exchange CAS servers.
Exchange ActiveSync must be configured with certificate-based authentication, or user credential entry.
When Conditional Access policies are configured and targeted to a user, before a user can connect to their email, the device they use must be:
- Either enrolled with Intune or is a domain joined PC.
- Registered in Microsoft Entra ID. Additionally, the client Exchange ActiveSync ID must be registered with Microsoft Entra ID.
Microsoft Entra Device Registration Service (DRS) is activated automatically for Intune and Microsoft 365 customers. Customers who have already deployed the ADFS Device Registration Service don't see registered devices in their on-premises Active Directory. This does not apply to Windows PCs and devices.
Compliant with device compliance policies deployed to that device.
If the device doesn't meet Conditional Access settings, the user is presented with one of the following messages when they sign in:
- If the device isn't enrolled with Intune, or isn't registered in Microsoft Entra ID, a message displays with instructions about how to install the Company Portal app, enroll the device, and activate email. This process also associates the device's Exchange ActiveSync ID with the device record in Microsoft Entra ID.
- If the device isn't compliant, a message displays that directs the user to the Intune Company Portal website, or the Company Portal app. From the company portal, they can find information about the problem and how to remediate it.
Support for mobile devices
Native email app on iOS/iPadOS - To create Conditional Access policy, see Create Conditional Access policies
EAS mail clients such as Gmail on Android 4 or later - To create Conditional Access policy, see Create Conditional Access policies
EAS mail clients on Android Enterprise Personally-Owned Work Profile devices - Only Gmail and Nine Work for Android Enterprise are supported on Android Enterprise personally owned work profile devices. For Conditional Access to work with Android Enterprise personally owned work profiles, you must deploy an email profile for the Gmail or Nine Work for Android Enterprise app, and also deploy those apps as a required installation. After you deploy the app, you can set up device-based Conditional Access.
EAS mail clients on Android device administrator - To create Conditional Access policy, see Create Conditional Access policies
Important
Microsoft Intune is ending support for Android device administrator management on devices with access to Google Mobile Services (GMS) on December 31, 2024. After that date, device enrollment, technical support, bug fixes, and security fixes will be unavailable. If you currently use device administrator management, we recommend switching to another Android management option in Intune before support ends. For more information, see Ending support for Android device administrator on GMS devices.
To set up Conditional Access for Android Enterprise personally owned work profile devices
Sign in to the Microsoft Intune admin center.
Deploy the Gmail or Nine Work app as Required.
Go to Devices > Manage devices > Configuration and choose *Create.
Enter a Name and Description for the profile.
Select Android enterprise in Platform, select Email in Profile type.
Configure the email profile settings.
When you're done, select OK > Create to save your changes.
After you create the email profile, assign it to groups.
Set up device-based conditional access.
Note
Microsoft Outlook for Android and iOS/iPadOS is not supported via the Exchange on-premises connector. If you want to leverage Microsoft Entra Conditional Access policies and Intune App Protection Policies with Outlook for iOS/iPadOS and Android for your on-premises mailboxes, please see Using hybrid Modern Authentication with Outlook for iOS/iPadOS and Android.
Support for PCs
It currently supports the native Mail application on Windows 8.1 and later (when enrolled into MDM with Intune).
Important
On October 22, 2022, Microsoft Intune ended support for devices running Windows 8.1. Technical assistance and automatic updates on these devices aren't available.
If you currently use Windows 8.1, then move to Windows 10/11 devices. Microsoft Intune has built-in security and device features that manage Windows 10/11 client devices.
Configure Exchange on-premises access
Support for new installations of the Exchange connector was deprecated in July of 2020, and the connector installation package is no longer available for download. Instead, use Exchange hybrid modern authentication (HMA).
Before you can use the following procedure to set up Exchange on-premises access control, you must install and configure at least one Intune on-premises Exchange connector for Exchange on-premises.
Sign in to the Microsoft Intune admin center.
Go to Tenant administration > Exchange access, and then select Exchange On-premises access.
On the Exchange on-premises access pane, choose Yes to Enable Exchange on-premises access control.
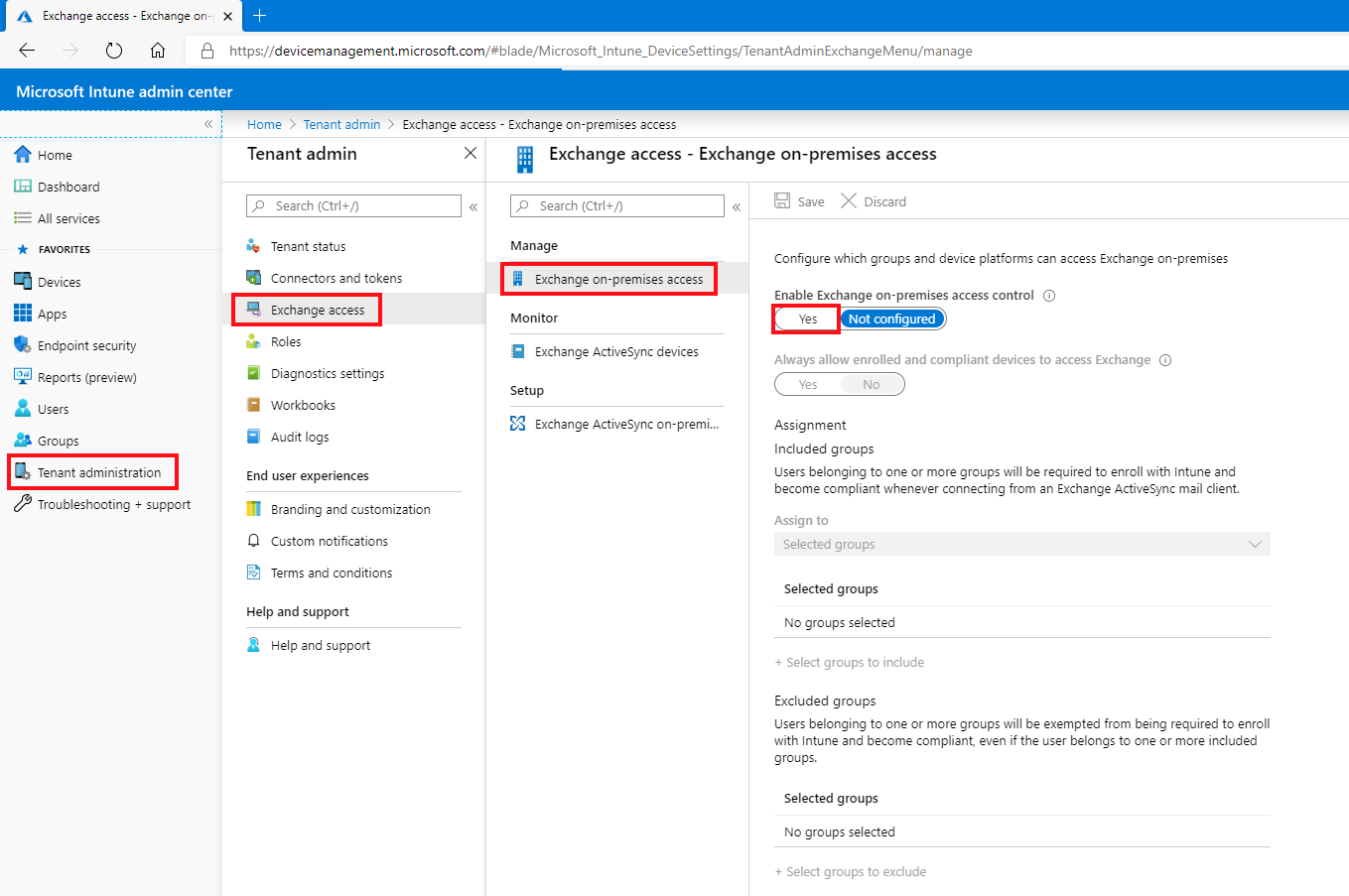
Under Assignment, choose Select groups to include, and then select one or more groups to configure access.
Members of the groups you select have the Conditional Access policy for Exchange on-premises access applied to them. Users who receive this policy must enroll their devices in Intune and be compliant with the compliance profiles before they can access Exchange on-premises.
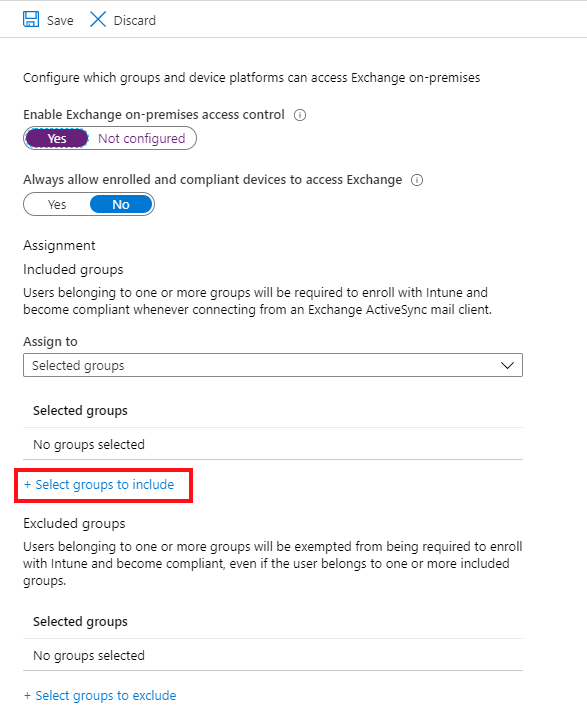
To exclude groups, choose Select groups to exclude, and then select one or more groups that are exempt from requirements to enroll devices and to be compliant with the compliance profiles before accessing Exchange on-premises.
Select Save to save your configuration, and return to the Exchange access pane.
Next, configure settings for the Intune on-premises Exchange connector. In the admin center, select Tenant administration > Exchange Access> Exchange ActiveSync on-premises connector and then select the connector for the Exchange organization that you want to configure.
For User notifications, select Edit to open the Edit Organization workflow where you can modify the User notification message.
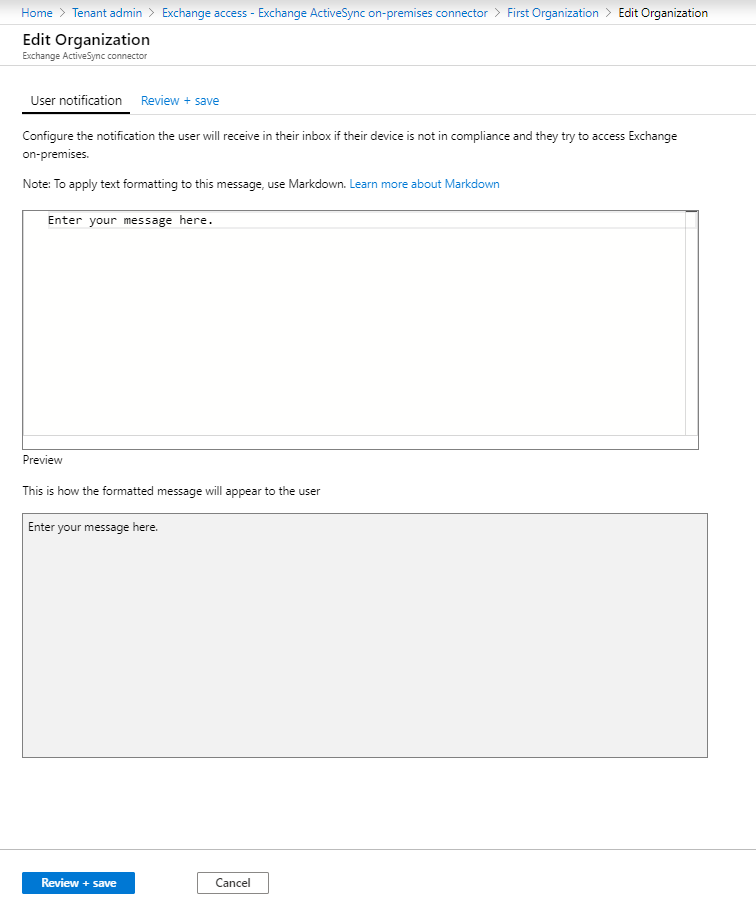
Modify the default email message that's sent to users if their device isn't compliant and they want to access Exchange on-premises. The message template uses Markup language. You can also see the preview of how the message looks as you type
Select Review + save, and then Save to save your edits to complete configuration of Exchange on-premises access.
Tip
To learn more about Markup language see this Wikipedia article.
Next, select Advanced Exchange ActiveSync access settings to open the Advanced Exchange ActiveSync access settings workflow where you configure device access rules.
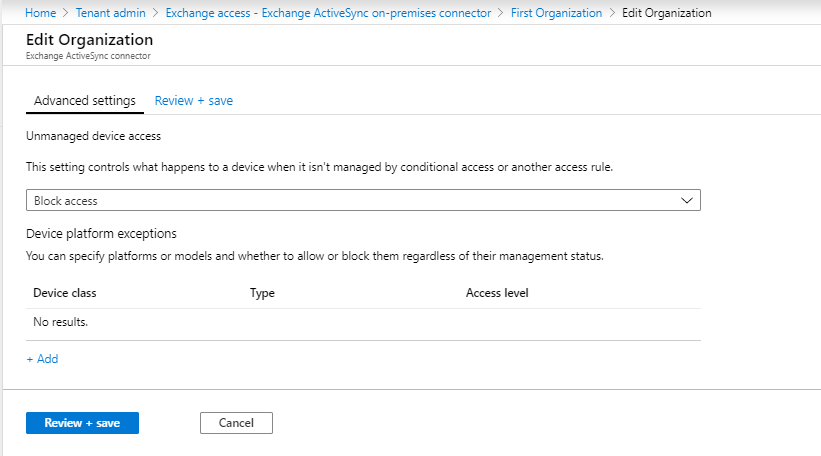
For Unmanaged device access, set the global default rule for access from devices that aren't affected by Conditional Access or other rules:
Allow access - All devices can access Exchange on-premises immediately. Devices that belong to the users in the groups you configured as included in the previous procedure are blocked if they're later evaluated as not compliant with the compliant policies or not enrolled in Intune.
Block access and Quarantine – All devices are immediately blocked from accessing Exchange on-premises initially. Devices that belong to users in the groups you configured as included in the previous procedure get access after the device enrolls in Intune and is evaluated as compliant.
This setting is supported on Android devices that run Samsung Knox standard. Other Android devices don't support this setting and are always blocked.
For Device platform exceptions, select Add, and then specify details as needed for your environment.
If the Unmanaged device access setting is set to Blocked, devices that are enrolled and compliant are allowed even if there's a platform exception to block them.
Select OK to save your edits.
Select Review + save, and then Save to save the Exchange Conditional Access policy.
Next steps
Next, create a compliance policy and assign it to the users for Intune to evaluate their mobile devices, See Get started with device compliance.
Troubleshooting Intune on-premises Exchange connector in Microsoft Intune
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for