Microsoft Defender for Endpoint - demonstration scenarios
Applies to:
- Microsoft Defender Antivirus
- Microsoft Defender for Endpoint Plan 1 or 2
- Microsoft Defender for Servers
- Microsoft Defender for Business
- Microsoft Defender for Individuals
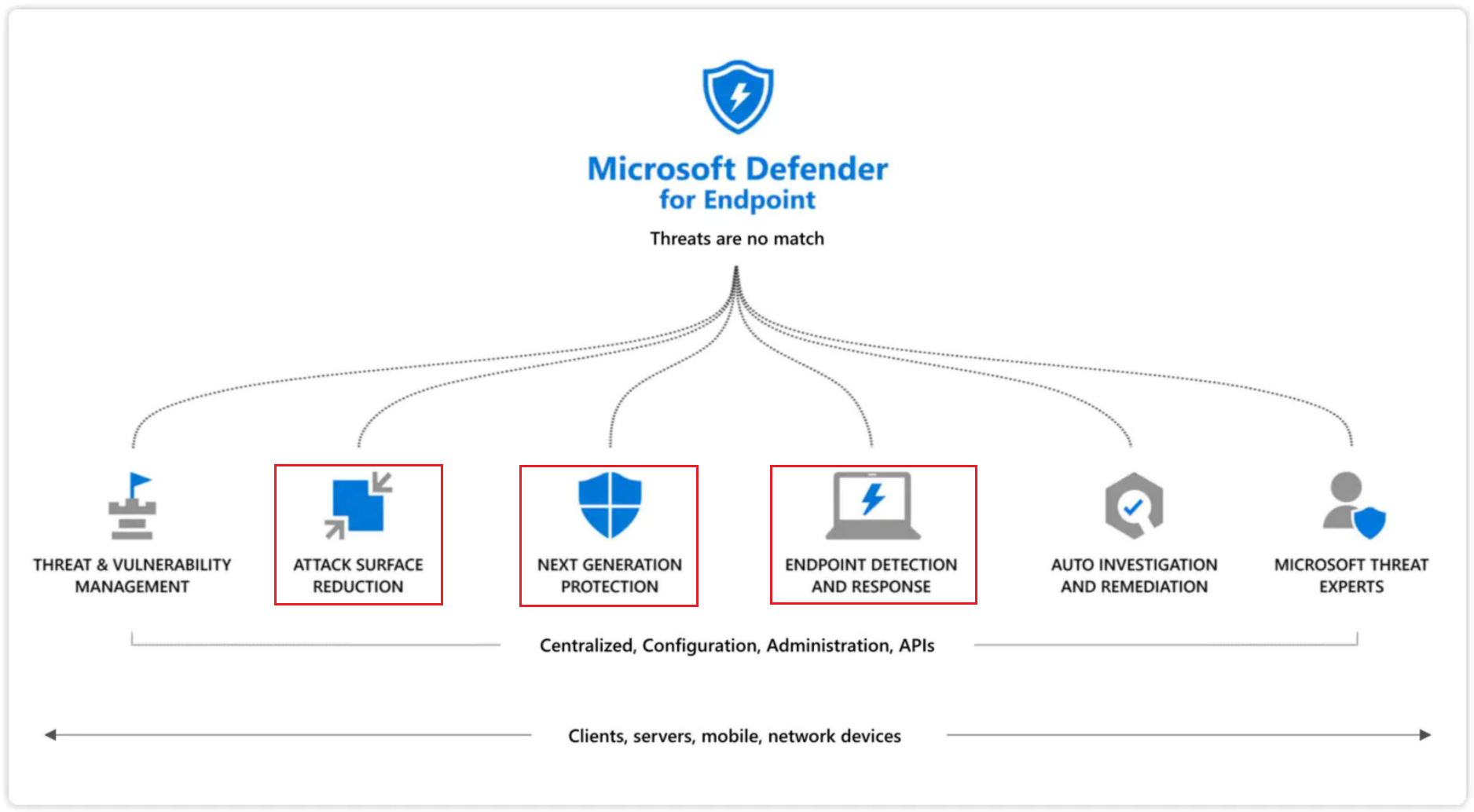
Demonstration scenarios help you learn about the capabilities of Microsoft Defender for Endpoint on Windows, Mac, and Linux. Demonstration scenarios are provided for the following Microsoft Defender for Endpoint protection areas:
- Attack surface protection (ASR)
- Next Generation Protection (NGP)
- Endpoint detection and response (EDR)
Note
None of the sample files or suspicious links provided in this collection are actually malicious; all links and demonstration files are harmless.
We encourage you to read Microsoft Defender Antivirus documentation, and to download the Evaluation guide.
Demonstrations
The following table lists the available demonstrations alphabetically, with their associated protection area.
| Demonstration name | Protection area | Description |
|---|---|---|
| AMSI demonstrations | NGP | Confirm that an AMSI script is detected and blocked. |
| Antimalware validation | NGP | Confirm that antivirus/antimalware is detecting and blocking malware. |
| Attack surface reduction rules demonstrations | ASR | Download sample files to trigger each ASR rule. |
| App reputation demonstration | NGP | Navigate to the app reputation page to see the demonstration scenario using Microsoft Edge. |
| Behavior Monitoring demonstration | NGP | Confirm that behavior monitoring is detecting and blocking malware. |
| Cloud-delivered protection demonstration | NGP | Confirm that cloud-delivered protection is working properly on your computer. |
| Controlled folder access (CFA) demonstration (block script) | ASR | Download the CFA test tool. |
| Controlled folder access (CFA) demonstrations (block ransomware) | ASR | Download and execute a sample file to trigger CFA ransomware protection. |
| Endpoint Detection and Response (EDR) detections | EDR | Confirm that EDR is detecting cyber threats such as malware. |
| Exploit protection (EP) demonstrations | ASR | Apply custom exploit protection settings. |
| Network protection demonstrations | ASR | Navigate to a suspicious URL to trigger network protection. |
| Potentially unwanted applications (PUA) demonstration | NGP | Confirm that potentially unwanted applications (PUAs) are being blocked on your network by downloading a fake (safe) PUA file. |
| URL reputation demonstrations | NGP | Navigate to the URL Reputation page to see the demonstration scenarios using Microsoft Edge. |
See also
Attack surface protection overview Test attack surface reduction rules Next Generation Protection overview Endpoint detection and response overview Microsoft Defender for Endpoint security blog
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.