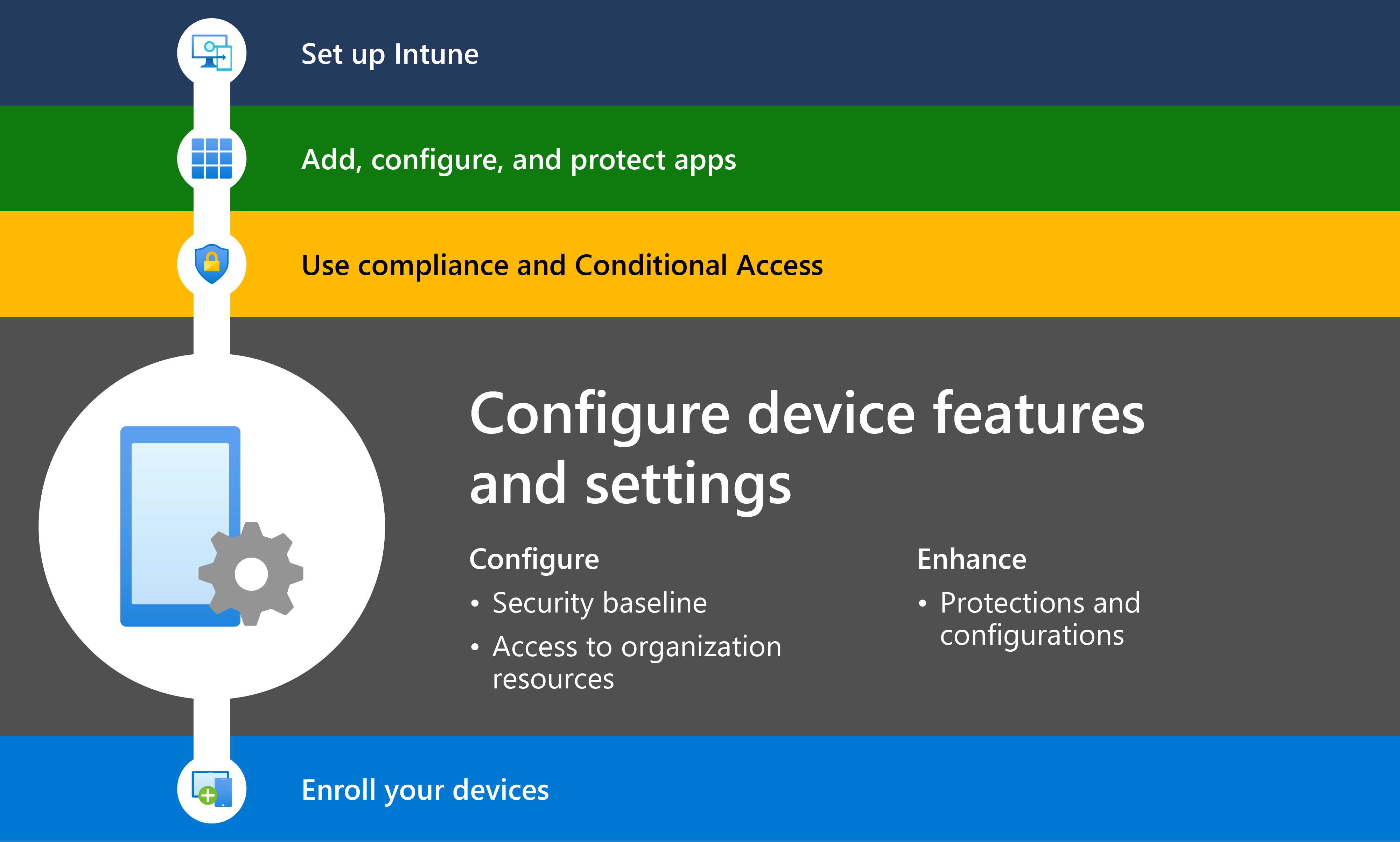
Step 4 - Configure device features and settings to secure devices and access resources
So far, you set up your Intune subscription, created app protection policies, and created device compliance policies.
In this step, you're ready to configure a minimum or baseline set of security and device features that all devices must have.
This article applies to:
- Android
- iOS/iPadOS
- macOS
- Windows
When you create device configuration profiles, there are different levels and types of policies available. These levels are the minimum Microsoft recommended policies. Know that your environment and business needs can be different.
Level 1 - Minimum device configuration: In this level, Microsoft recommends you create policies that:
- Focus on device security, including installing antivirus, creating a strong password policy, and regularly installing software updates.
- Give users access to their organization email and controlled secure access to your network, wherever they are.
Level 2 - Enhanced device configuration: In this level, Microsoft recommends you create policies that:
- Expand device security, including configuring disk encryption, enabling secure boot, and adding more password rules.
- Use the built-in features and templates to configure more settings that are important for your organization, including analyzing on-premises Group Policy Objects (GPOs).
Level 3 - High device configuration: In this level, Microsoft recommends you create policies that:
- Move to password-less authentication, including using certificates, configuring single sign-on (SSO) to apps, enabling multifactor authentication (MFA), and configuring Microsoft Tunnel.
- Add extra layers of security using Android common criteria mode or creating DFCI policies for Windows devices.
- Use the built-in features to configure kiosk devices, dedicated devices, shared devices, and other specialized devices.
- Deploy existing shell scripts.
This article lists the different levels of device configuration policies that organizations should use. Most of these policies in this article focus on access to organization resources and security.
These features are configured in device configuration profiles in the Microsoft Intune admin center. When the Intune profiles are ready, they can be assigned to your users and devices.
Level 1 - Create your security baseline
To help keep your organization data and devices secure, you create different policies that focus on security. You should create a list of security features that all users and/or all devices must have. This list is your security baseline.
In your baseline, at a minimum, Microsoft recommends the following security policies:
- Install antivirus (AV) and regularly scan for malware
- Use detection and response
- Turn on the firewall
- Install software updates regularly
- Create a strong PIN/password policy
This section lists the Intune and Microsoft services you can use to create these security policies.
For a more granular list of Windows settings and their recommended values, go to Windows security baselines.
Antivirus and scanning
✅ Install antivirus software and regularly scan for malware
All devices should have antivirus software installed and be regularly scanned for malware. Intune integrates with third party partner mobile threat defense (MTD) services that provide AV and threat scanning. For macOS and Windows, antivirus and scanning are built in to Intune with Microsoft Defender for Endpoint.
Your policy options:
| Platform | Policy type |
|---|---|
| Android Enterprise | - Mobile threat defense partner - Microsoft Defender for Endpoint for Android can scan for malware |
| iOS/iPadOS | Mobile threat defense partner |
| macOS | Intune Endpoint Security antivirus profile (Microsoft Defender for Endpoint) |
| Windows client | - Intune security baselines (recommended) - Intune Endpoint Security antivirus profile (Microsoft Defender for Endpoint) - Mobile threat defense partner |
For more information on these features, go to:
- Android Enterprise:
- iOS/iPadOS Mobile threat defense integration
- macOS Antivirus policy
- Windows:
Detection and response
✅ Detect attacks and act on these threats
When you detect threats quickly, you can help minimize the impact of the threat. When you combine these policies with Conditional Access, you can block users and devices from accessing organization resources if a threat is detected.
Your policy options:
| Platform | Policy type |
|---|---|
| Android Enterprise | - Mobile threat defense partner - Microsoft Defender for Endpoint on Android |
| iOS/iPadOS | - Mobile threat defense partner - Microsoft Defender for Endpoint on iOS/iPadOS |
| macOS | Not available |
| Windows client | - Intune security baselines (recommended) - Intune endpoint detection and response profile (Microsoft Defender for Endpoint) - Mobile threat defense partner |
For more information on these features, go to:
- Android Enterprise:
- iOS/iPadOS:
- Windows:
Firewall
✅ Enable the firewall on all devices
Some platforms come with a built-in firewall and on others, you might have to install a firewall separately. Intune integrates with third party partner mobile threat defense (MTD) services that can manage a firewall for Android and iOS/iPadOS devices. For macOS and Windows, firewall security is built in to Intune with Microsoft Defender for Endpoint.
Your policy options:
| Platform | Policy type |
|---|---|
| Android Enterprise | Mobile threat defense partner |
| iOS/iPadOS | Mobile threat defense partner |
| macOS | Intune Endpoint Security firewall profile (Microsoft Defender for Endpoint) |
| Windows client | - Intune security baselines (recommended) - Intune Endpoint Security firewall profile (Microsoft Defender for Endpoint) - Mobile threat defense partner |
For more information on these features, go to:
- Android Enterprise Mobile threat defense integration
- iOS/iPadOS Mobile threat defense integration
- macOS Firewall policy
- Windows:
Password policy
✅ Create a strong password/PIN policy and block simple passcodes
PINs unlock devices. On devices that access organization data, including personally owned devices, you should require strong PINs/passcodes and support biometrics to unlock devices. Using biometrics is part of a password-less approach, which is recommended.
Intune uses device restrictions profiles to create and configure password requirements.
Your policy options:
| Platform | Policy type |
|---|---|
| Android Enterprise | Intune device restrictions profile to manage the: - Device password - Work profile password |
| Android Open-Source Project (AOSP) | Intune device restrictions profile |
| iOS/iPadOS | Intune device restrictions profile |
| macOS | Intune device restrictions profile |
| Windows client | - Intune security baselines (recommended) - Intune device restrictions profile |
For a list of the settings you can configure, go to:
- Android Enterprise device restrictions profile:
- Android AOSP Device restrictions profile > Device password
- iOS/iPadOS Device restrictions profile > Password
- macOS Device restrictions profile > Password
- Windows:
Software updates
✅ Regularly install software updates
All devices should be updated regularly and policies should be created to make sure these updates are successfully installed. For most platforms, Intune has policy settings that focus on managing and installing updates.
Your policy options:
| Platform | Policy type |
|---|---|
| Android Enterprise organization owned devices | System update settings using Intune device restrictions profile |
| Android Enterprise personally owned devices | Not available Can use compliance policies to set a minimum patch level, min/max OS version, and more. |
| iOS/iPadOS | Intune update policy |
| macOS | Intune update policy |
| Windows client | - Intune feature updates policy - Intune expedited updates policy |
For more information on these features and/or the settings you can configure, go to:
- Android Enterprise Device restrictions profile > System update
- iOS/iPadOS Software update policies
- macOS Software update policies
- Windows:
Level 1 - Access organization email, connect to VPN or Wi-Fi
This section focuses on accessing resources in your organization. These resources include:
- Email for work or school accounts
- VPN connection for remote connectivity
- Wi-Fi connection for on-premises connectivity
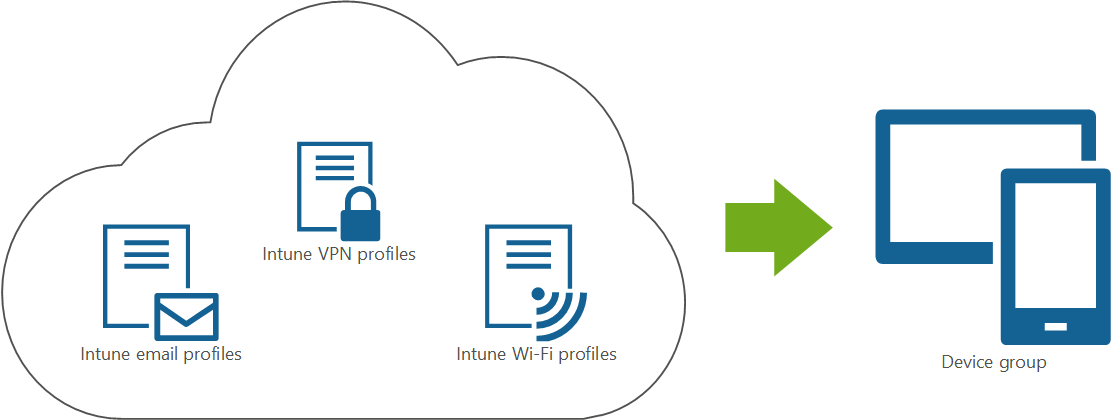
Many organizations deploy email profiles with preconfigured settings to user devices.
✅ Automatically connect to user email accounts
The profile includes the email configuration settings that connect to your email server.
Depending on the settings you configure, the email profile can also automatically connect the users to their individual email account settings.
✅ Use enterprise level email apps
Email profiles in Intune use common and popular email apps, like Outlook. The email app is deployed to user devices. After the app is deployed, you deploy the email device configuration profile with the settings that configure the email app.
The email device configuration profile includes settings that connect to your Exchange.
✅ Access work or school email
Creating an email profile is a common minimum baseline policy for organizations with users that use email on their devices.
Intune has built-in email settings for Android, iOS/iPadOS, and Windows client devices. When users open their email app, they can automatically connect, authenticate, and synchronize their organizational email accounts on their devices.
✅ Deploy anytime
On new devices, we recommended you deploy the email app during the enrollment process. When enrollment completes, then deploy the email device configuration policy.
If you have existing devices, then deploy the email app at any time, and deploy the email device configuration policy.
Get started with email profiles
To get started:
Deploy an email app to your devices. For some guidance, go to Add email settings to devices using Intune.
Create an email device configuration profile in Intune. Depending on the email app your organization uses, the email device configuration profile might not be needed.
For some guidance, go to Add email settings to devices using Intune.
In the email device configuration profile, configure the settings for your platform:
Android Enterprise personally owned devices with a work profile email settings
Android Enterprise organization-owned devices don't use email device configuration profiles.
Assign the email device configuration profile to your users or user groups.
VPN
Many organizations deploy VPN profiles with preconfigured settings to user devices. The VPN connects your devices to your internal organization network.
If your organization uses cloud services with modern authentication and secure identities, then you probably don't need a VPN profile. Cloud-native services don't require a VPN connection.
If your apps or services aren't cloud-based or aren't cloud-native, then deploy a VPN profile to connect to your internal organization network.
✅ Work from anywhere
Creating a VPN profile is a common minimum baseline policy for organizations with remote workers and hybrid workers.
As users work from anywhere, they can use the VPN profile to securely connect to your organization's network to access resources.
Intune has built-in VPN settings for Android, iOS/iPadOS, macOS, and Windows client devices. On user devices, your VPN connection is shown as an available connection. Users select it. And, depending on the settings in your VPN profile, users can automatically authenticate and connect to the VPN on their devices.
✅ Use enterprise level VPN apps
VPN profiles in Intune use common enterprise VPN apps, like Check Point, Cisco, Microsoft Tunnel, and more. The VPN app is deployed to user devices. After the app is deployed, then you deploy the VPN connection profile with settings that configure the VPN app.
The VPN device configuration profile includes settings that connect to your VPN server.
✅ Deploy anytime
On new devices, we recommended you deploy the VPN app during the enrollment process. When enrollment completes, then deploy the VPN device configuration policy.
If you have existing devices, deploy the VPN app at any time, and then deploy the VPN device configuration policy.
Get started with VPN profiles
To get started:
Deploy a VPN app to your devices.
- For a list of supported VPN apps, go to Supported VPN connection apps in Intune.
- For the steps to add apps to Intune, go to Add apps to Microsoft Intune.
In the VPN device configuration profile, configure the settings for your platform:
Assign the VPN device configuration profile to your users or user groups.
Wi-Fi
Many organizations deploy Wi-Fi profiles with preconfigured settings to user devices. If your organization has a remote-only workforce, then you don't need to deploy Wi-Fi connection profiles. Wi-Fi profiles are optional and are used for on-premises connectivity.
✅ Connect wirelessly
As users work from different mobile devices, they can use the Wi-Fi profile to wirelessly and securely connect to your organization's network.
The profile includes the Wi-Fi configuration settings that automatically connect to your network and/or SSID (service set identifier). Users don't have to manually configure their Wi-Fi settings.
✅ Support mobile devices on-premises
Creating a Wi-Fi profile is a common minimum baseline policy for organizations with mobile devices that work on-premises.
Intune has built-in Wi-Fi settings for Android, iOS/iPadOS, macOS, and Windows client devices. On user devices, your Wi-Fi connection is shown as an available connection. Users select it. And, depending on the settings in your Wi-Fi profile, users can automatically authenticate and connect to the Wi-Fi on their devices.
✅ Deploy anytime
On new devices, we recommended you deploy the Wi-Fi device configuration policy when devices enroll in Intune.
If you have existing devices, you can deploy the Wi-Fi device configuration policy at any time.
Get started with Wi-Fi profiles
To get started:
Configure the settings for your platform:
Assign the Wi-Fi device configuration profile to your users or user groups.
Level 2 - Enhanced protection and configuration
This level expands on what you configured in level 1 and adds more security for your devices. In this section, you create a level 2 set of policies that configure more security settings for your devices.
Microsoft recommends the following level 2 security policies:
Enable disk encryption, secure boot, and TPM on your devices. These features combined with a strong PIN policy or biometric unlocking are recommended at this level.
On Android devices, disk encryption and Samsung Knox might be built into the operating system. Disk encryption might be automatically enabled when you configure the lock screen settings. In Intune, you can create a device restrictions policy that configures lock screen settings.
For a list of the password and lock screen settings you can configure, go to the following articles:
Expire passwords and regulate reusing old passwords. In Level 1, you created a strong PIN or password policy. If you haven't already, be sure you configure your PINs & passwords to expire and set some password-reuse rules.
You can use Intune to create a device restrictions policy or a settings catalog policy that configures these settings. For more information on the password settings you can configure, go to the following articles:
On Android devices, you can use device restrictions policies to set password rules:
Intune includes hundreds of settings that can manage devices features and settings, like disabling the built-in camera, controlling notifications, allowing bluetooth, blocking games, and more.
You can use the built-in templates or the settings catalog to see and configure the settings.
Device restrictions templates have many built-in settings that can control different parts of the devices, including security, hardware, data sharing, and more.
You can use these templates on the following platforms:
- Android
- iOS/iPadOS
- macOS
- Windows
Use the Settings catalog to see and configure all the available settings. You can use the settings catalog on the following platforms:
- iOS/iPadOS
- macOS
- Windows
Use the built-in administrative templates, similar to configuring ADMX templates on-premises. You can use the ADMX templates on the following platform:
- Windows
If you use on-premises GPOs and want to know if these same settings are available in Intune, then use Group Policy analytics. This feature analyzes your GPOs and depending on the analysis, can import them into an Intune settings catalog policy.
For more information, go to Analyze your on-premises GPOs and import them in Intune.
Level 3 - High protection and configuration
This level expands on what you configured in levels 1 and 2. It adds extra security features used in enterprise level organizations.
Expand password-less authentication to other services used by your workforce. In level 1, you enabled biometrics so users can sign in to their devices with a fingerprint or facial recognition. In this level, expand password-less to other parts of the organization.
Use certificates to authenticate email, VPN, and Wi-Fi connections. Certificates are deployed to users and devices, and are then used by users to get access to resources in your organization through the email, VPN, and Wi-Fi connections.
To learn more about using certificates in Intune, go to:
Configure single sign-on (SSO) for a more seamless experience when users open business apps, like Microsoft 365 apps. Users sign-in once and then are automatically signed-in to all the apps that support your SSO configuration.
To learn about using SSO in Intune and Microsoft Entra ID, go to:
Use multifactor authentication (MFA). When you move to password-less, MFA adds an extra layer of security, and can help protect your organization from phishing attacks. You can use MFA with authenticator apps, like Microsoft Authenticator, or with a phone call or text message. You can also use MFA when users enroll their devices in Intune.
Multifactor authentication is a feature of Microsoft Entra ID and can be used with Microsoft Entra accounts. For more information, go to:
Set up Microsoft Tunnel for your Android and iOS/iPadOS devices. Microsoft Tunnel uses Linux to allow these devices access to on-premises resources using modern authentication and Conditional Access.
Microsoft Tunnel uses Intune, Microsoft Entra ID, and Active Directory Federation Services (AD FS). For more information, go to Microsoft Tunnel for Microsoft Intune.
In addition to Microsoft Tunnel for devices enrolled with Intune, you can use Microsoft Tunnel for Mobile Application Management (Tunnel for MAM) to extend tunnel capabilities to Android and iOS/iPad devices that are not enrolled with Intune. Tunnel for MAM is available as an Intune add-on that requires an extra license.
For more information, go to Use Intune Suite add-on capabilities.
Use Windows Local Administrator Password Solution (LAPS) policy to manage and back up the built-in local administrator account on your Windows devices. Because the local admin account can't be deleted and has full permissions to the device, management of the built-in Windows administrator account is an important step in securing your organization. Intune policy for Windows LAPS uses the capabilities that are available for Windows devices that run version 21h2 or later.
For more information, go to Intune support for Windows LAPS.
Use Microsoft Intune Endpoint Privilege Management (EPM) to reduce the attack surface of your Windows devices. EPM empowers you to have users that run as standard users (without administrator rights) yet remain productive by determining when those users can run apps in an elevated context.
EPM elevation rules can be based on file hashes, certificate rules, and more. The rules you configure help to ensure that only the expected and trusted applications you allow can run as elevated. Rules can:
- Manage the child processes that an app creates.
- Support requests by users to elevate a managed process.
- Allow for automatic elevations of files that just need to run without any user interruption.
Endpoint Privilege Management is available as an Intune add-on that requires an extra license. For more information, go to Use Intune Suite add-on capabilities.
Use Android Common Criteria mode on Android devices that are used by highly sensitive organizations, like government establishments.
For more information on this feature, go to Android Common Criteria mode.
Create policies that apply to the Windows firmware layer. These policies can help prevent malware from communicating with the Windows OS processes.
For more information on this feature, go to Use Device Firmware Configuration Interface (DFCI) profiles on Windows devices.
Configure kiosks, shared devices, and other specialized devices:
Android Enterprise:
Android device administrator
Device settings to run as a kiosk
Important
Microsoft Intune is ending support for Android device administrator management on devices with access to Google Mobile Services (GMS) on December 31, 2024. After that date, device enrollment, technical support, bug fixes, and security fixes will be unavailable. If you currently use device administrator management, we recommend switching to another Android management option in Intune before support ends. For more information, see Ending support for Android device administrator on GMS devices.
Deploy shell scripts:
Follow the minimum recommended baseline policies
- Set up Microsoft Intune
- Add, configure, and protect apps
- Plan for compliance policies
- 🡺 Configure device features (You are here)
- Enroll devices