See if this helps
https://learn.microsoft.com/en-us/mem/intune/fundamentals/role-based-access-control?WT.mc_id=Portal-Microsoft_Intune_DeviceSettings
Endpoint Admin Center and Tenant Attach permissions
Looking for clarity on what Roles or Permissions are required to allow use of Endpoint Admin Center and the Client Actions on MECM Clients using Tenant Attach, I have:
Installed Azure AD Connect
Added a UPN
Created an account on my on-premise AD with the @Arjan Suffix
Sync'd the account in MECM and AAD
Applied MECM permissions to be able to see collection's run scripts etc..
But I am struggling to understand what the min permissions are required through Azure to allow the account to access Endpoint Admin Center, see the devices and then be able to run the features such as:
• View Client Details
• Install Applications
• View a devices timeline
• View Resource Explorer
• Run Scripts
• Use CMPivot
So far the only way I can do this is if the account has either the Global Administrator role or the Intune Service Administrator role. These permissions are to much and need to be more granular for our general admin staff.
I can only assume we will need to create a custom role but cant seem to find a definitive list of what the min permissions are required to create this role.
4 answers
Sort by: Most helpful
-
-
Sumner, Ann 31 Reputation points
2021-02-14T19:16:46.53+00:00 No this does not help, I have looked at this before. Thanks Anyway.
For example it suggests, "Help Desk Operator: Performs remote tasks on users and devices, and can assign applications or policies to users or devices." Yet I can not see this role, I can only see "Helpdesk administrator: Users with this role can change passwords, invalidate refresh tokens, manage service requests, and monitor service health."
The roles in the link don't seem to match the roles in Azure.
I have tried the use the Helpdesk administrator role, but when logging into Admin Center it tells me I have not enabled Device Management yet, I can not see any devices but I can see the Sync's Users and Groups.
As I have stated the only way I can get my accounts to see and perform the actions from Admin Center is by giving them Global Admin or Intune Admin, which is way to much permissions for a helpdesk person who only needs to be able to see devices and run the device client actions.
-
 Simon Ren-MSFT 31,601 Reputation points Microsoft Vendor
Simon Ren-MSFT 31,601 Reputation points Microsoft Vendor2021-02-15T06:57:13.437+00:00 Hi,
Thanks for posting in Microsoft MECM Q&A forum.
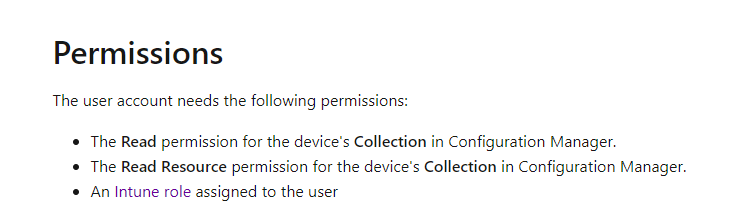
The user account needs the following permissions:
For more detailed information, please refer to:
Tenant attach: Resource explorer in the admin center (preview)
Role-based access control (RBAC) with Microsoft IntuneThanks for your time.
Best regards,
Simon
If the response is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread. -
Sumner, Ann 31 Reputation points
2021-02-15T08:55:06.103+00:00 Hi Many Thanks for the response, again I have read this, however this is where the confusion is coming from and clarity is required.
The "user" account, where should this be created? In AAD or the on prem AD?
If it is AAD, how do we get this seen in the on prem AD, to be able to apply the permissions for MECM?
I have an the account on the on prem AD who has full administrator permissions for MECM (the account can login to my primary server and perform all the actions through the MECM console), I have AD Connect installed and Sync'd so this account can be seen in AAD, the account can login to Admin Center but this is where we seem to fail the only roles that will allow the account to view devices and run the client actions is Global Administrator or Intune Service Administrator. This is to much permissions from the Azure side.
So we need more clarity on how this "user" account should be created, where it should be created, how this account can be seen by both AAD (So the account can login to admin center) and on prem AD (So MECM permissions can be applied) and what the minimum role is required from a AAD side to be able to use Admin Center?
Thanks