Hi, I managed to fix the issue. I found that the resource ID was needed in the auth URL:
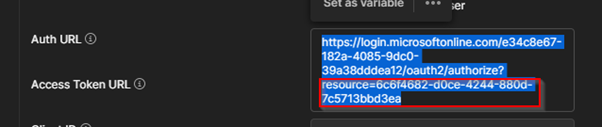
This can be obtained from Enterprise Applications:
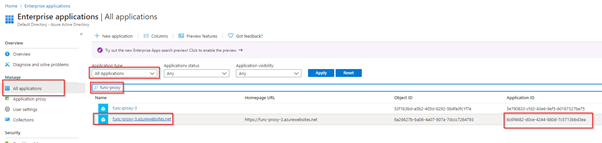
Also, creating two separate app registrations:

This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi,
I have created an instance of Azure API for FHIR with an Azure FHIR proxy following this tutorial:
https://github.com/microsoft/health-architectures/tree/master/FHIR/FHIRProxy##configuration
I am able to browse to the proxy URL through a browser after being prompted to log in to view the metadata as shown below:
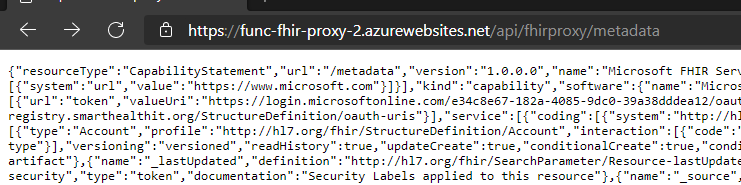
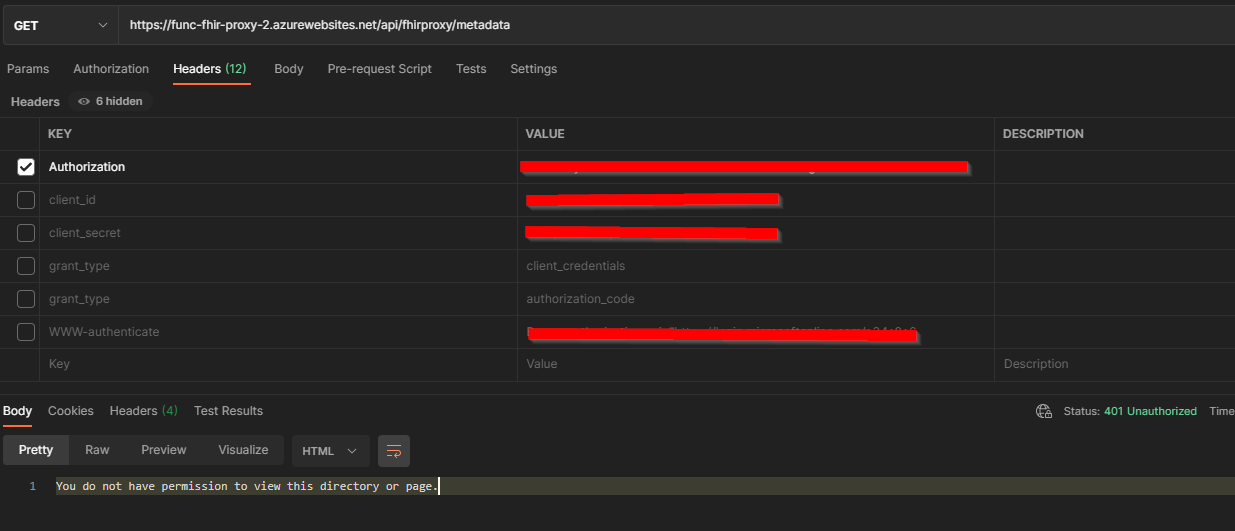
However, when trying to access it through the Postman API tool I keep getting the same error:
You do not have permission to view this directory or page.
I have tried generating an authorization Bearer token using the following:
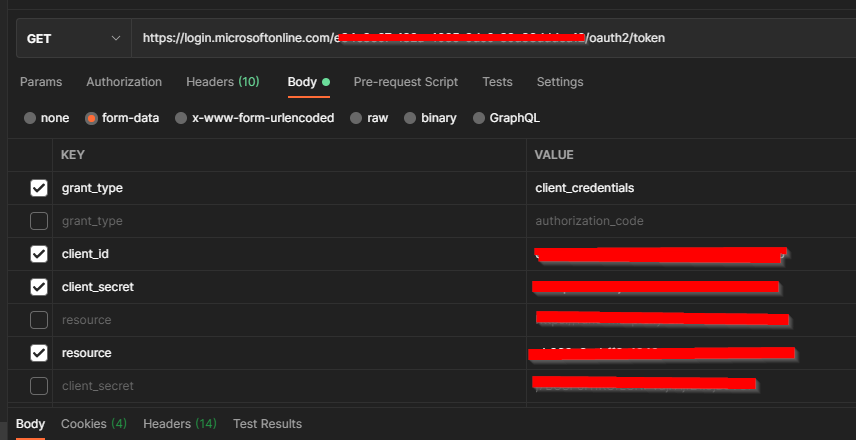
The authorization token looks fine, but when adding it to my API call it errors as shown below:
 ]3
]3
Does anyone have any idea how I can successfully call my API with a proper authorization token that works or know a tutorial that actually explains this part of the process?
The tutorial does not give much information.
Thanks
Hi, I managed to fix the issue. I found that the resource ID was needed in the auth URL:

This can be obtained from Enterprise Applications:

Also, creating two separate app registrations:


Looks like the FHIR Proxy is deployed with WebApp Authentication/Authorization (also called Easy Auth) enabled. If you have deployed as is too, the authentication flow is slightly different and is documented.
To quote the docs for reference, after getting the access token from Azure AD, you need to validate the token against easy auth which returns another authentication token that needs to be set in the X-ZUMO-AUTH header to make the actual request.
From the browser directly, a cookie is set with the required authentication token as mentioned in the same doc.