Hello ArnaudSynetis-3880,
Thank you for posting here.
I am sorry, we are only familiar with WIndows CA ( with AD CS role), and we are not familiar with other three-part CA (such as EJBCA sub CA you mentioned).
However, I will try my best to help you. To further narrow down our issue, we would like to get more detailed information. Would you please help to collect the following information:
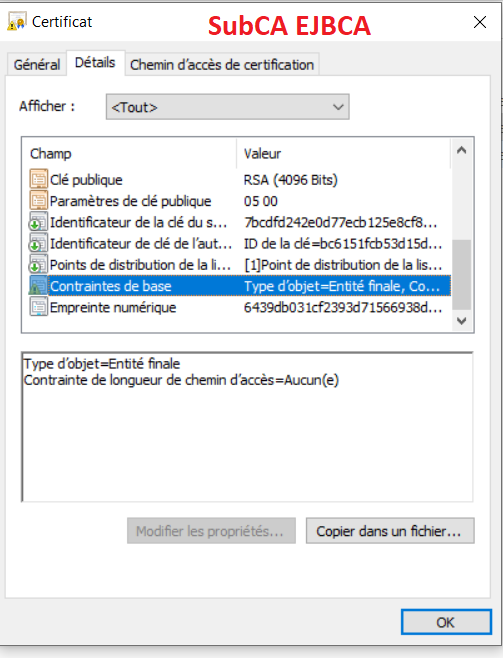
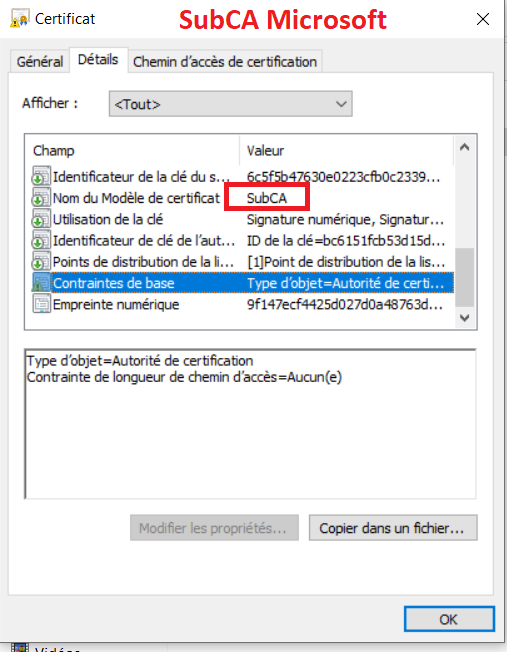
- Based on the description above, I understand we have a standalone root CA, now we want to add a AD CS sub CA and a EJBCA sub CA (we have done it, but it is not the sub CA that we want, because the information related to parameters is not what we want, the value of Basic Constraints about your EJBCA sub CA is 0), is that right?
- Based on "we are not able to specify the parameters we want, they are being overwritten by AD CS without any possibility of configuration.", what parameter do you mean? Do you mean they are overriten by standalone root CA?
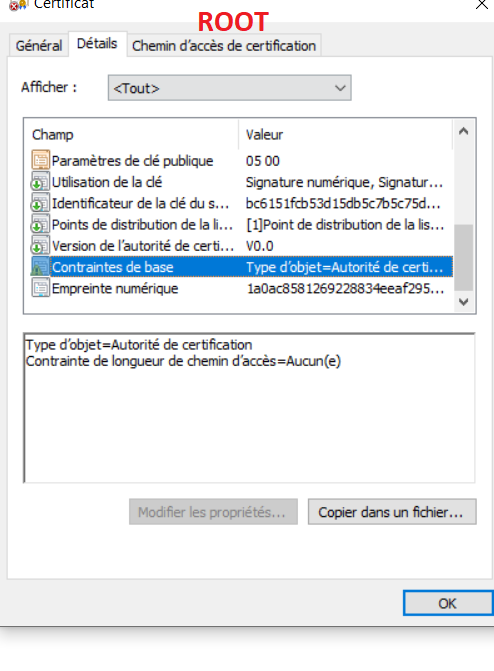
- What is the value of Basic Constraints about your root CA?
Meanwhile, based on my understand,
1.If the value of Basic Constraints about your root CA is 0, pathLenConstraintof 0 does still allow the CA to issue certificates, but these certificates must be end-entity-certificates (I mean EJCBA sub CA must be end-entity-certificate, EJCBA sub CA can not issue certificates).
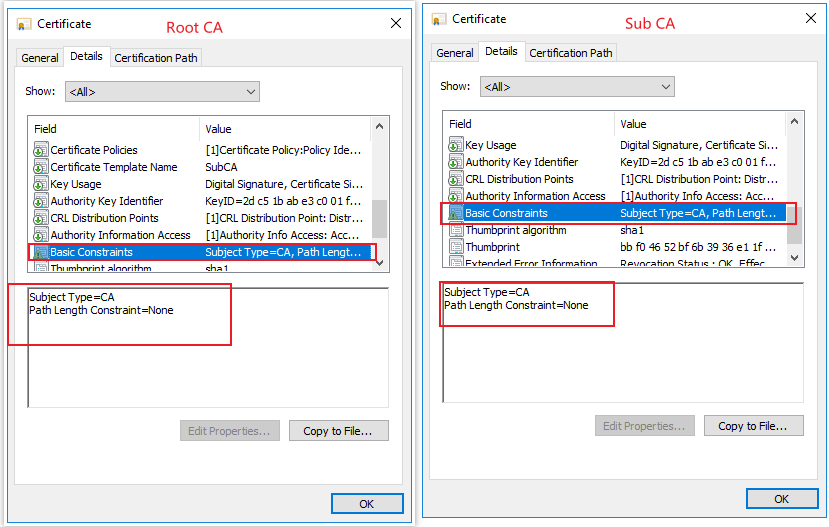
2.After viewing the Basic Constraints in my lab (one offline root CA and one online sub CA). By default Basic Constraints =None on both offline root CA and online sub CA.
We see that subject type is set to CA and there is no defined path length constraint. It means that unlimited certificates are allowed in certificate chain below the current CA certificate.
3.Usually, if it is a Windows sub CA, we can define Basic Constraints in CAPolicy.inf file as below (for example), then deploy this Windows sub CA.
[Version]
Signature="$Windows NT$"
[PolicyStatementExtension]
Policies=InternalPolicy
[InternalPolicy]
OID= 1.2.3.4.1455.67.89.5
URL=http://pki.fabrikam.com/cps.txt
[Certsrv_Server]
RenewalKeyLength=2048
RenewalValidityPeriod=Years
RenewalValidityPeriodUnits=10
LoadDefaultTemplates=0
AlternateSignatureAlgorithm=0
[BasicConstraintsExtension]
PathLength=1
Critical=Yes
4.If the value of Basic Constraints about your root CA is None, it is recommended to consult EJBCA engineers if there is another way to issue EJBCA sub CA certificate from Windows standalone root CA.
References:
AD CS Step by Step Guide: Two Tier PKI Hierarchy Deployment
https://social.technet.microsoft.com/wiki/contents/articles/15037.ad-cs-step-by-step-guide-two-tier-pki-hierarchy-deployment.aspx
Constraints: what they are and how they’re used
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/constraints-what-they-are-and-how-they-amp-8217-re-used/ba-p/1129048
Thank you for your understanding and support.
Best Regards,
Daisy Zhou