IIS Service Alerts From Servers Where IIS is not Installed
NOTE: I believe the IIS 6 Management Pack exhibits similar behaviors. In the interest of simplicity I am going to confine my comments to the IIS 7 Management Pack, but you should easily be able to extend the concepts if you need to.
One frequent complaint about the IIS management pack for SCOM is that it raises alerts on servers where IIS is not installed. The two alerts usually seen are "Web Management service is stopped" and "IIS 7 server role is unavailable." These alerts are raised due to inconsistent behavior in the Microsoft.Windows.Win32ServiceInformationProvider Data Source when the service to be monitored doesn't exist.
For more information, please see https://msdn.microsoft.com/en-us/library/jj130359.aspx
The IIS 7 Management Pack performs an initial discovery against all Windows 2008 (and 2008 R2) Server computers. It simply checks to see if the registry key HKLM\SOFTWARE\MICROSOFT\InetStp exists. If that key exists, it believes it has found the IIS 7 Server Role class, to which it applies a pair of basic service monitors that check to see if the WMSvc and IISADMIN services are running. These monitors work correctly if those services exist, but can behave unpredictably if they don't exist.
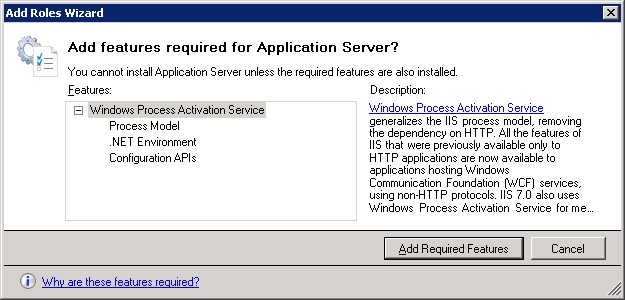
If you add the Application Server Role to your server, it will install the Windows Process Activation Service (also known as WAS) which came from IIS, but can exist separately from IIS. Since the service came from IIS, installing it creates the HKLM\SOFTWARE\Microsoft\InetStp\Components\WASConfigurationAPI REG_DWORD. That is enough to get the IIS 7 Management Pack to believe it has discovered an IIS 7 Server Role, and apply the two service monitors mentioned above.
So what can we do about this? There are two options.
The first option is more simple, but also more presumptuous. You can disable Microsoft.Windows.InternetInformationServices.2008.ServerRole.Discovery.Rule (IIS 7 Server Role Discovery) and replace it with a discovery that checks for any of the following REG_DWORDs exist:
- HKLM\SYSTEM\CurrentControlSet\services\W3SVC\Start
- HKLM\SYSTEM\CurrentControlSet\services\ftpsvc\Start
- HKLM\SYSTEM\CurrentControlSet\services\msftpsvc\Start
- HKLM\SYSTEM\CurrentControlSet\services\SMTPSVC\Start
Those are the services that are discovered by targeting the IIS 7 Server Role.
The other method is to extend the IIS 7 Computer Role class, and then create groups that contain instances of it where WMSvc and IISADMIN actually exist. Then use those to override the monitors. This method is more complex, but makes less invasive changes to the management pack in case a future release of the IIS 7 management pack significantly changes how discovery works. This is the method I chose.
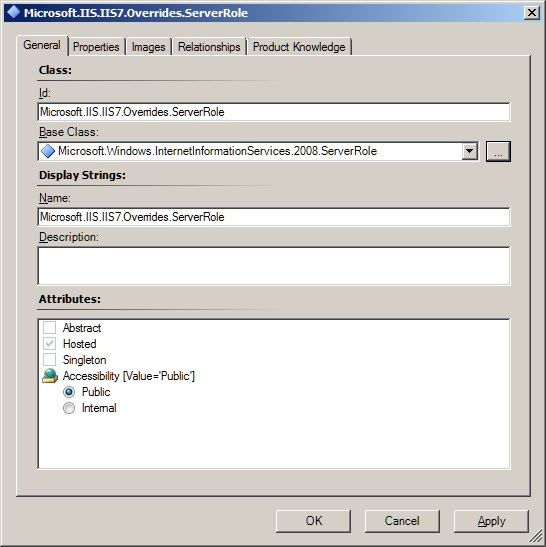
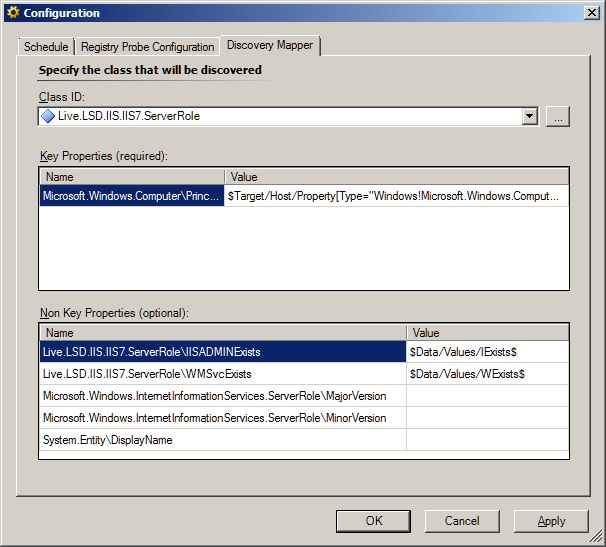
First we need to make a custom class that extends the Microsoft.Windows.InternetInformationServices.2008.ServerRole class so we can add properties to it.
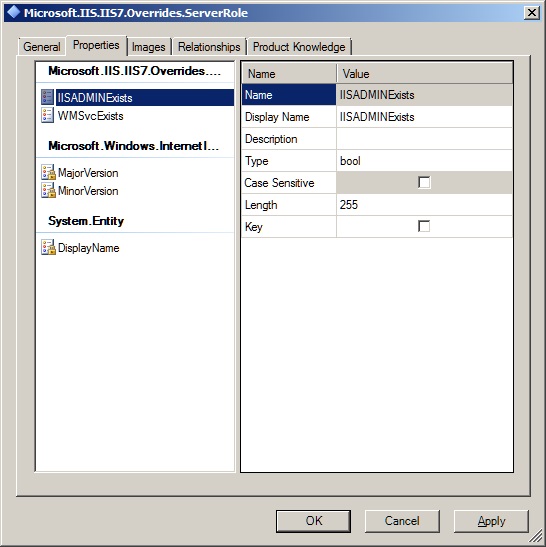
Now we add a pair of Boolean properties to the class.
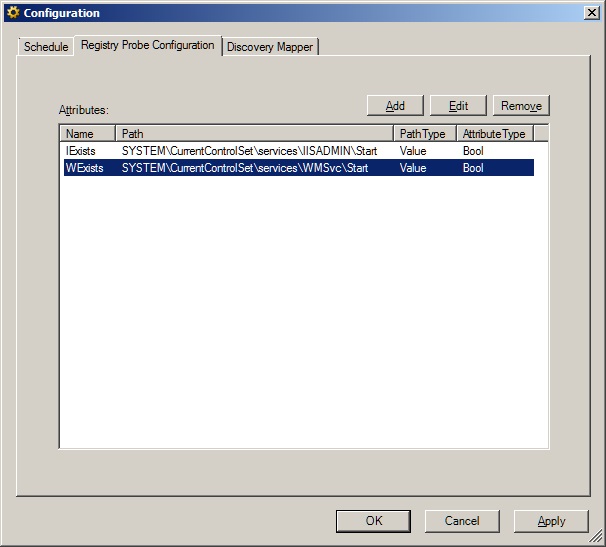
The discovery is quite simple. Just make an unfiltered registry discovery that targets the IIS 7 Computer Role. We discover two Boolean attributes for the existence of SYSTEM\CurrentControlSet\services\IISADMIN\Start and SYSTEM\CurrentControlSet\services\WMSvc\Start and map those to our new class properties.
Now that we have discovered the properties, we can use them to populate our groups. I'll spare you all the screenshots, as I am attaching an example management pack that has all of the classes, relationships, discoveries, and overrides that I am referencing.
Here's an example of using a Boolean object property in a group populator:
<RuleId>$MPElement$</RuleId>
<GroupInstanceId>$Target/Id$</GroupInstanceId>
<MembershipRules>
<MembershipRule>
<MonitoringClass>$MPElement[Name="Microsoft.IIS.IIS7.Overrides.ServerRole"]$</MonitoringClass>
<RelationshipClass>$MPElement[Name="Microsoft.IIS.IIS7.Overrides.ServerRole.IISADMIN.Exists.Group.Contains.Role"]$</RelationshipClass>
<Expression>
<SimpleExpression>
<ValueExpression>
<Property>$MPElement[Name="Microsoft.IIS.IIS7.Overrides.ServerRole"]/IISADMINExists$</Property>
</ValueExpression>
<Operator>Equal</Operator>
<ValueExpression>
<Value>True</Value>
</ValueExpression>
</SimpleExpression>
</Expression>
</MembershipRule>
</MembershipRules>
The last step is four Monitor Property Overrides. Two non-enforced overrides to disable the monitors for all IIS 7 Server Roles, and two enforced overrides to re-enable them for members of our groups where we know the services exist.
A complete management pack that contains a full implementation of my solution is attached.
Microsoft.IIS.IIS7.Overrides.xml
Comments
Anonymous
January 01, 2003
It has been out for a while, but only for IIS8, not IIS7.Anonymous
January 01, 2003
Thank you for sharing this workaround, Michael. This is very helpful to the community. When releasing the IIS8 MP we considered changing this behavior... but we were only releasing IIS8, not re-releasing the IIS7 one at that point - so we preferred to leave this behavior the same rather than have two totally different disconnected behaviors between versions. We did, however, re-target the "Web Management service availability" monitor to "IIS 8 Web Server" class as opposed to "IIS 8 Server Role" - precisely to minimize this annoyance of the irrelevant alert.Anonymous
January 01, 2003
IIS 8 MP v. 7.0.10165.0 has a variant of this issue where it assumes WMsvc feature is installed by default on a correctly discovered IIS 8 server thus generating WMsvc service stopped error messages.Anonymous
May 24, 2013
When does the new MP come out that has the "web management service availability" monitor targeted to the web server role?Anonymous
July 25, 2013
The comment has been removedAnonymous
July 26, 2013
The comment has been removedAnonymous
March 31, 2014
Thank you, Michael....much appreciated. Well done, sir.Anonymous
April 07, 2014
This was super Michael. Thanks for sharing this and the excellent explanationAnonymous
May 22, 2014
The IIS 8 MP has a similar issue with "The Web Management service is stopped". My SCOM Management Servers don't have the WMSvc installed, yet SCOM throw this alert for them.Anonymous
May 29, 2014
Pingback from IIS Service Alerts From Servers Where IIS is not Installed | ScompanionAnonymous
November 25, 2014
I'm getting "Web Management service is stopped" alerts from an IIS 8 server that doesn't have the Web Management service. Can this MP be adjusted to work with IIS 8 too?Anonymous
January 30, 2015
Thanks a lot! Works great :)Anonymous
February 19, 2015
I updated the management pack for IIS8. I was also getting this alert due to process activation being installed for a different non-IIS role (IPAM). The link is below. It contains the fix for IIS7 and IIS8. I tweaked the names a bit to make it more clear what it is. This is not an upgrade to the MP in this post. You should uninstall that one completely before installing this one. The zip contains a sealed and unsealed version. (I like to have sealed MPs for MPs don't want open for storing future overrides in, but it's up to you how you do it.) http://d-h.st/qcCOAnonymous
April 06, 2015
The comment has been removedAnonymous
June 23, 2015
Updated the Managemetn Pack for IIS 8. Download at https://www.dropbox.com/s/la4ut81mcpcd6eg/Microsoft.IIS.IIS8.Overrides.xml?dl=0Anonymous
December 17, 2015
The comment has been removedAnonymous
December 17, 2015
What about the values $Data/Value/IExists? Are they input manually? I do not set them available from the arrow menus...Anonymous
December 28, 2015
this is typical over engineered nonsense. how about a simple toggle to turn this alert off or something? why do you big heads make everything so difficult? if the service isn't present give us an easy way to ignore it.Anonymous
October 11, 2017
So... here we are at October, 2017 and this issue still exists in the form of the IIS 10 MP. Strangely, it doesn't fire for all of the machines in our infrastructure that don't have IIS installed. Why is it that you can come up with a workaround that properly identifies the instance of an installed IIS server role but the MP team at Microsoft can't do the same?