Configure Advanced Threat Protection for Azure SQL Database
Applies to:
Azure SQL Database
Advanced Threat Protection for Azure SQL Database detects anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases. Advanced Threat Protection can identify Potential SQL injection, Access from unusual location or data center, Access from unfamiliar principal or potentially harmful application, and Brute force SQL credentials - see more details in Advanced Threat Protection alerts.
You can receive notifications about the detected threats via email notifications or Azure portal
Advanced Threat Protection is part of the Microsoft Defender for SQL offering, which is a unified package for advanced SQL security capabilities. Advanced Threat Protection can be accessed and managed via the central Microsoft Defender for SQL portal.
Set up Advanced Threat Protection in the Azure portal
Sign into the Azure portal.
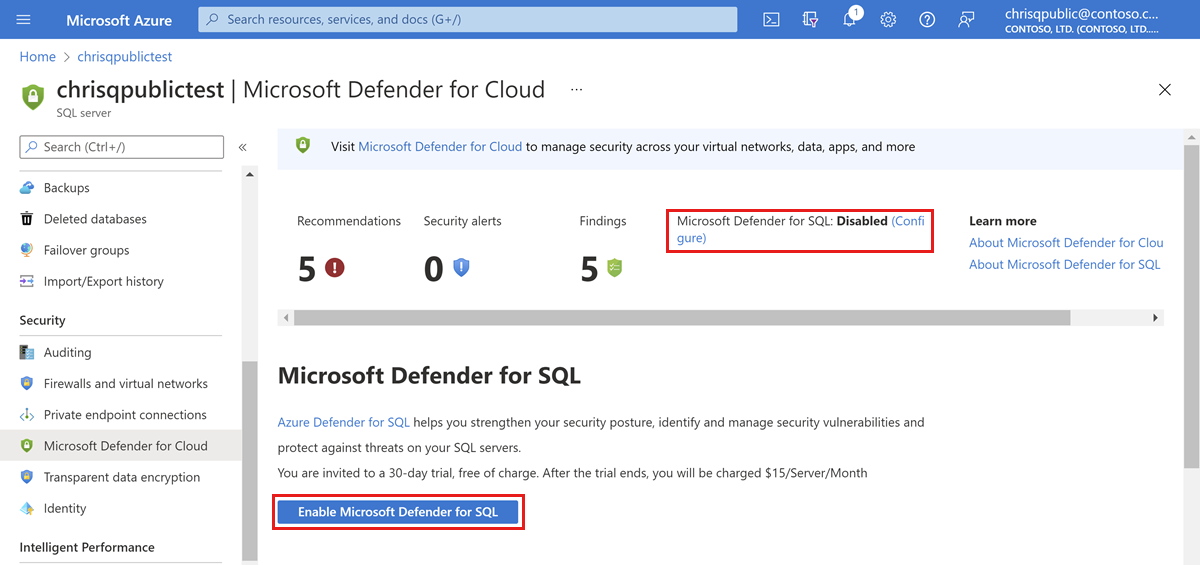
Navigate to the configuration page of the server you want to protect. In the security settings, select Microsoft Defender for Cloud.
On the Microsoft Defender for Cloud configuration page:
If Microsoft Defender for SQL hasn't yet been enabled, select Enable Microsoft Defender for SQL.
Select Configure.
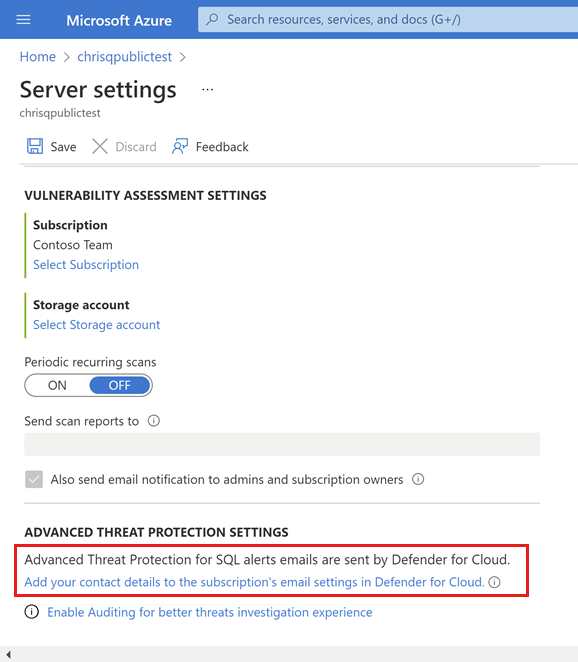
Under ADVANCED THREAT PROTECTION SETTINGS, select Add your contact details to the subscription's email settings in Defender for Cloud.
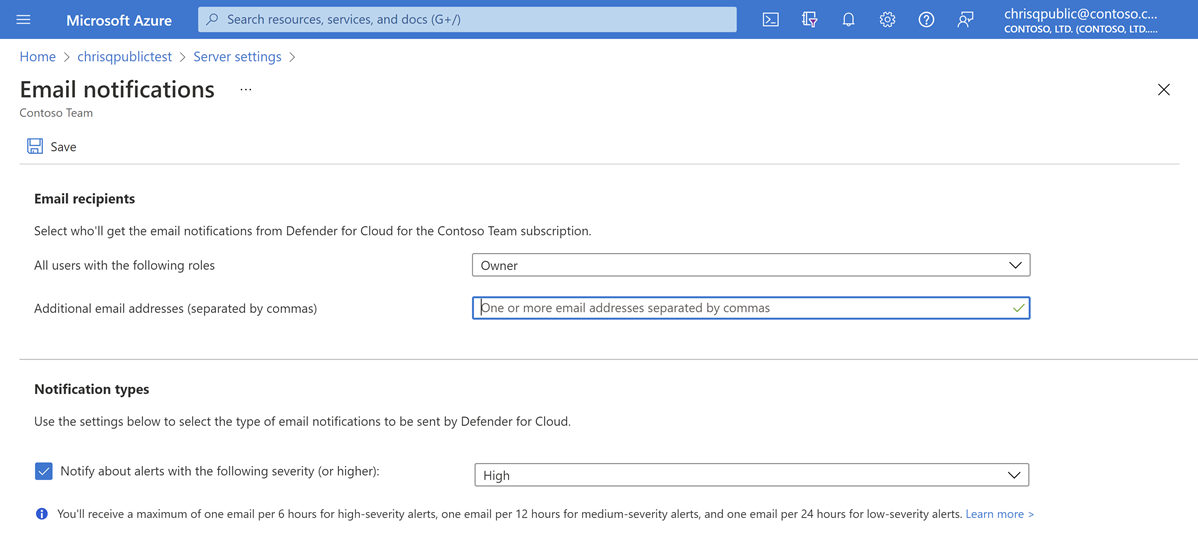
Provide the list of emails to receive notifications upon detection of anomalous database activities in the Additional email addresses (separated by commas) text box.
Optionally customize the severity of alerts that will trigger notifications to be sent under Notification types.
Select Save.
Set up Advanced Threat Protection using PowerShell
For a script example, see Configure auditing and Advanced Threat Protection using PowerShell.
Next steps
Learn more about Advanced Threat Protection and Microsoft Defender for SQL in the following articles: