Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Use Conditional Access with Microsoft Intune compliance policies to control the devices and apps that can connect to your email and company resources. When integrated, you can gate access to keep your corporate data secure, while giving users an experience that allows them to do their best work from any device, and from any location.
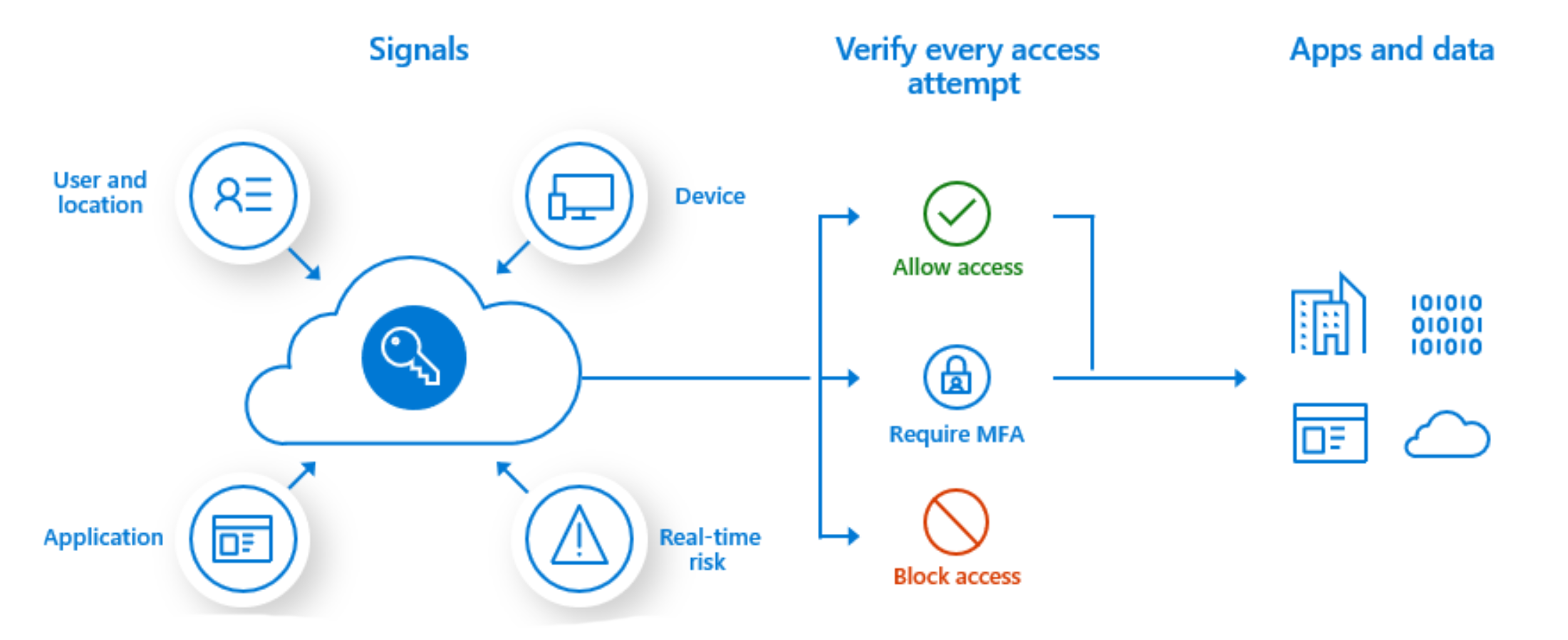
Conditional Access is a Microsoft Entra capability that is included with a Microsoft Entra ID P1 or P2 license. Through Microsoft Entra ID, Conditional Access brings signals together to make decisions, and enforce organizational policies. Intune enhances this capability by adding mobile device compliance and mobile app management data to the solution. Common signals include:
- User or group membership.
- IP location information.
- Device details, including device compliance or configuration status.
- Application details, including requiring use of managed apps to access corporate data.
- Real-time and calculated risk detection, when you also use a mobile threat defense partner.
Note
Conditional Access also extends its capabilities to Microsoft 365 services.
Ways to use Conditional Access with Intune
Conditional Access works with Intune device configuration and compliance policies, and with Intune Application protection policies.
Device-based Conditional Access
Intune and Microsoft Entra ID work together to make sure only managed and compliant devices can access email, Microsoft 365 services, Software as a service (SaaS) apps, and on-premises apps. Additionally, you can set a policy in Microsoft Entra ID to enable only domain-joined computers or mobile devices that have enrolled in Intune to access Microsoft 365 services. Including:
Conditional Access based on network access control
Conditional Access based on device risk
Conditional Access for Windows PCs. Both corporate-owned and bring your own device (BYOD).
Conditional Access for Exchange on-premises
Learn more about device-based Conditional Access with Intune
App-based Conditional Access
Intune and Microsoft Entra ID work together to make sure only managed apps can access corporate e-mail or other Microsoft 365 services.
Learn more about app-based Conditional Access with Intune.
Known limitations
The compliant network location condition is only supported for devices enrolled in mobile device management (MDM). If you configure a Conditional Access policy using the compliant network location condition, users with devices that aren't yet MDM-enrolled might be affected. Users on these devices might fail the Conditional Access policy check, and be blocked. Ensure that you exclude the affected users or devices when using the compliant network location condition.