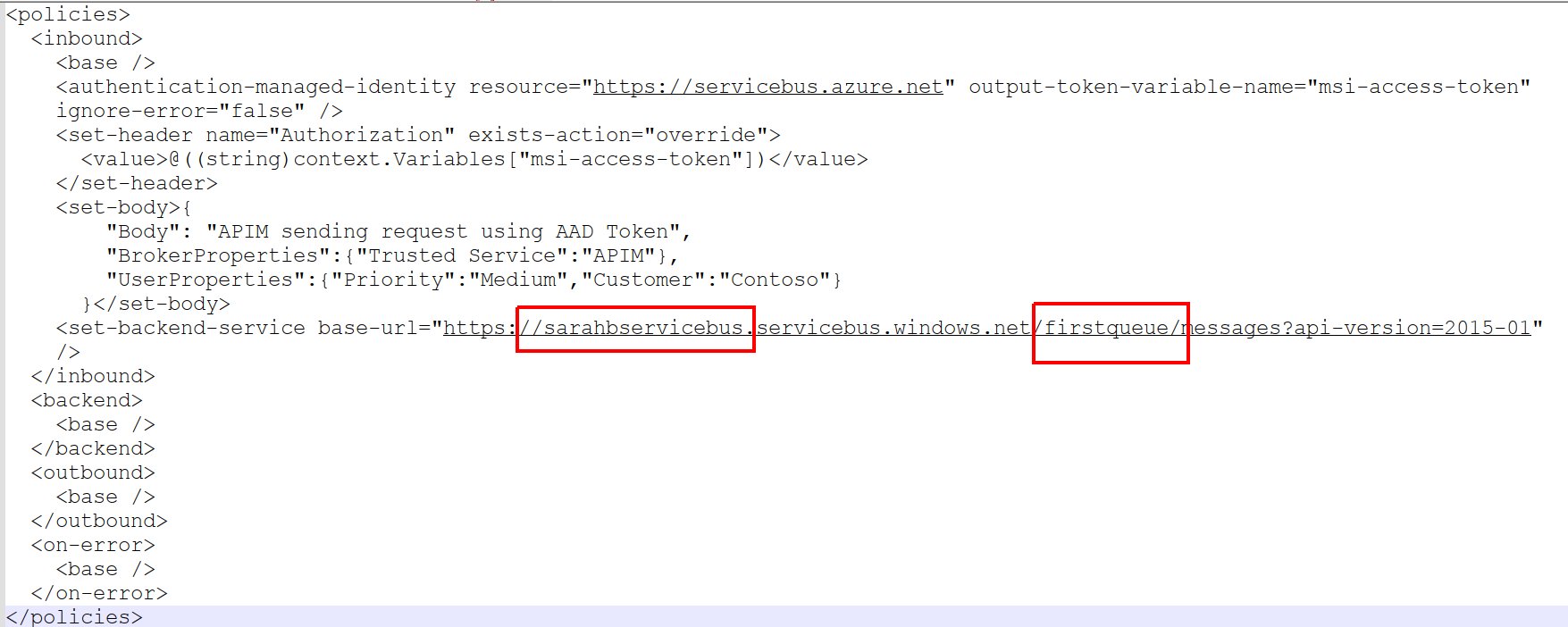
@Sumit Bharti Thanks for reaching out. It looks like the 500 error is coming from the backend service where your request URL is not correctly formed and the backend request might be generated as below which is resulting in 500 errors as the endpoint is incorrect.
https://{servicebusname}.servicebus.windows.net/{topic/queue name}/messages?api-version=2015-01/{operationName}
You can always refer to the service bus send message REST document and make sure you are using the POST method, if not then you need to use <set-method>POST</set-method> in your policy. Further, you can always check OCP-APIM traces to debug your APIs
API management preserves the operation URL template while forwarding requests to the backend API. You can use rewrite-uri policy to control that behavior.
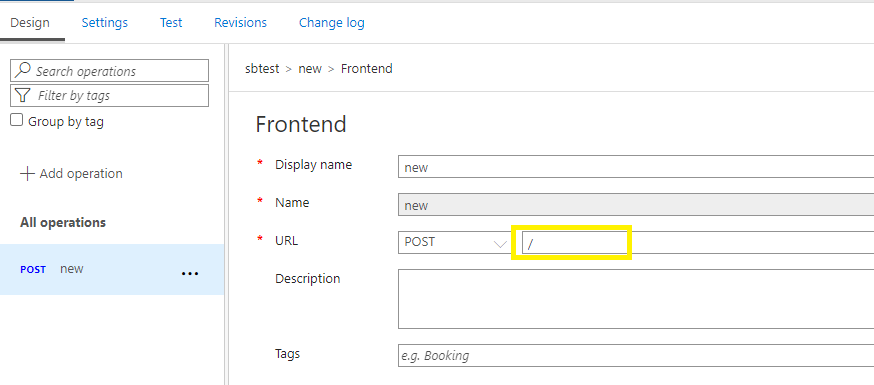
Either you can remove URL value from your operation as below and only use '/' if it works for you then the policy that you are using (GitHub example) will work.
Alternative you need to leverage the rewrite-uri as below:
<inbound>
<base />
<authentication-managed-identity resource="https://servicebus.azure.net" output-token-variable-name="msi-access-token" ignore-error="false" />
<set-header name="Authorization" exists-action="override">
<value>@((string)context.Variables["msi-access-token"])</value>
</set-header>
<set-body>{
"Body": "APIM sending request using AAD Token",
"BrokerProperties":{"Trusted Service":"APIM"},
"UserProperties":{"Priority":"Medium","Customer":"Contoso"}
}</set-body>
<set-backend-service base-url="https://{servicebusname}.servicebus.windows.net" />
<rewrite-uri template="/{topic/queue name}/messages?api-version=2015-01" />
</inbound>
In case if you still observe issues then please let me know so I can initiate a private comment and you can share OCP APIM traces content only to my private comment to assist you further.
For Community: You can refer to this document and follow two steps on how to leverage system identity
Enable system-assigned identity on the API Management instance. For instructions, see Use managed identities in Azure API Management.
Add the identity to the Azure Service Bus Data Sender role on the Service Bus namespace