Quickstart: Direct web traffic with Azure Application Gateway using Azure PowerShell
In this quickstart, you use Azure PowerShell to create an application gateway. Then you test it to make sure it works correctly.
The application gateway directs application web traffic to specific resources in a backend pool. You assign listeners to ports, create rules, and add resources to a backend pool. For the sake of simplicity, this article uses a simple setup with a public frontend IP address, a basic listener to host a single site on the application gateway, a basic request routing rule, and two virtual machines in the backend pool.
You can also complete this quickstart using Azure CLI or the Azure portal.
Note
Application Gateway frontend now supports dual-stack IP addresses (Preview). You can now create up to four frontend IP addresses: Two IPv4 addresses (public and private) and two IPv6 addresses (public and private).
Prerequisites
- An Azure account with an active subscription. Create an account for free.
- Azure PowerShell version 1.0.0 or later (if you run Azure PowerShell locally).
Azure Cloud Shell
Azure hosts Azure Cloud Shell, an interactive shell environment that you can use through your browser. You can use either Bash or PowerShell with Cloud Shell to work with Azure services. You can use the Cloud Shell preinstalled commands to run the code in this article, without having to install anything on your local environment.
To start Azure Cloud Shell:
| Option | Example/Link |
|---|---|
| Select Try It in the upper-right corner of a code or command block. Selecting Try It doesn't automatically copy the code or command to Cloud Shell. |  |
| Go to https://shell.azure.com, or select the Launch Cloud Shell button to open Cloud Shell in your browser. |  |
| Select the Cloud Shell button on the menu bar at the upper right in the Azure portal. |  |
To use Azure Cloud Shell:
Start Cloud Shell.
Select the Copy button on a code block (or command block) to copy the code or command.
Paste the code or command into the Cloud Shell session by selecting Ctrl+Shift+V on Windows and Linux, or by selecting Cmd+Shift+V on macOS.
Select Enter to run the code or command.
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Connect to Azure
To connect with Azure, run Connect-AzAccount.
Create a resource group
In Azure, you allocate related resources to a resource group. You can either use an existing resource group or create a new one.
To create a new resource group, use the New-AzResourceGroup cmdlet:
New-AzResourceGroup -Name myResourceGroupAG -Location eastus
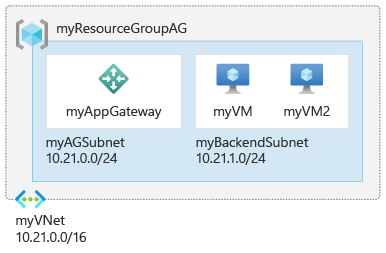
Create network resources
For Azure to communicate between the resources that you create, it needs a virtual network. The application gateway subnet can contain only application gateways. No other resources are allowed. You can either create a new subnet for Application Gateway or use an existing one. You create two subnets in this example: one for the application gateway, and another for the backend servers. You can configure the Frontend IP address of the Application Gateway to be Public or Private as per your use case. In this example, you'll choose a Public Frontend IP address.
- Create the subnet configurations using
New-AzVirtualNetworkSubnetConfig. - Create the virtual network with the subnet configurations using
New-AzVirtualNetwork. - Create the public IP address using
New-AzPublicIpAddress.
Note
Virtual network service endpoint policies are currently not supported in an Application Gateway subnet.
$agSubnetConfig = New-AzVirtualNetworkSubnetConfig `
-Name myAGSubnet `
-AddressPrefix 10.21.0.0/24
$backendSubnetConfig = New-AzVirtualNetworkSubnetConfig `
-Name myBackendSubnet `
-AddressPrefix 10.21.1.0/24
New-AzVirtualNetwork `
-ResourceGroupName myResourceGroupAG `
-Location eastus `
-Name myVNet `
-AddressPrefix 10.21.0.0/16 `
-Subnet $agSubnetConfig, $backendSubnetConfig
New-AzPublicIpAddress `
-ResourceGroupName myResourceGroupAG `
-Location eastus `
-Name myAGPublicIPAddress `
-AllocationMethod Static `
-Sku Standard
Create an application gateway
The Standard v2 SKU is used in this example.
Create the IP configurations and frontend port
- Use
New-AzApplicationGatewayIPConfigurationto create the configuration that associates the subnet you created with the application gateway. - Use
New-AzApplicationGatewayFrontendIPConfigto create the configuration that assigns the public IP address that you previously created for the application gateway. - Use
New-AzApplicationGatewayFrontendPortto assign port 80 to access the application gateway.
$vnet = Get-AzVirtualNetwork -ResourceGroupName myResourceGroupAG -Name myVNet
$subnet = Get-AzVirtualNetworkSubnetConfig -VirtualNetwork $vnet -Name myAGSubnet
$pip = Get-AzPublicIPAddress -ResourceGroupName myResourceGroupAG -Name myAGPublicIPAddress
$gipconfig = New-AzApplicationGatewayIPConfiguration `
-Name myAGIPConfig `
-Subnet $subnet
$fipconfig = New-AzApplicationGatewayFrontendIPConfig `
-Name myAGFrontendIPConfig `
-PublicIPAddress $pip
$frontendport = New-AzApplicationGatewayFrontendPort `
-Name myFrontendPort `
-Port 80
Note
Application Gateway frontend now supports dual-stack IP addresses (Public Preview). You can now create up to four frontend IP addresses: Two IPv4 addresses (public and private) and two IPv6 addresses (public and private).
Create the backend pool
- Use
New-AzApplicationGatewayBackendAddressPoolto create the backend pool for the application gateway. The backend pool is empty for now. When you create the backend server NICs in the next section, you'll add them to the backend pool. - Configure the settings for the backend pool with
New-AzApplicationGatewayBackendHttpSetting.
$backendPool = New-AzApplicationGatewayBackendAddressPool `
-Name myAGBackendPool
$poolSettings = New-AzApplicationGatewayBackendHttpSetting `
-Name myPoolSettings `
-Port 80 `
-Protocol Http `
-CookieBasedAffinity Enabled `
-RequestTimeout 30
Create the listener and add a rule
Azure requires a listener to enable the application gateway for routing traffic appropriately to the backend pool. Azure also requires a rule for the listener to know which backend pool to use for incoming traffic.
- Create a listener using
New-AzApplicationGatewayHttpListenerwith the frontend configuration and frontend port that you previously created. - Use
New-AzApplicationGatewayRequestRoutingRuleto create a rule named rule1.
$defaultlistener = New-AzApplicationGatewayHttpListener `
-Name myAGListener `
-Protocol Http `
-FrontendIPConfiguration $fipconfig `
-FrontendPort $frontendport
$frontendRule = New-AzApplicationGatewayRequestRoutingRule `
-Name rule1 `
-RuleType Basic `
-Priority 100 `
-HttpListener $defaultlistener `
-BackendAddressPool $backendPool `
-BackendHttpSettings $poolSettings
Create the application gateway
Now that you've created the necessary supporting resources, create the application gateway:
- Use
New-AzApplicationGatewaySkuto specify parameters for the application gateway. - Use
New-AzApplicationGatewayto create the application gateway.
$sku = New-AzApplicationGatewaySku `
-Name Standard_v2 `
-Tier Standard_v2 `
-Capacity 2
New-AzApplicationGateway `
-Name myAppGateway `
-ResourceGroupName myResourceGroupAG `
-Location eastus `
-BackendAddressPools $backendPool `
-BackendHttpSettingsCollection $poolSettings `
-FrontendIpConfigurations $fipconfig `
-GatewayIpConfigurations $gipconfig `
-FrontendPorts $frontendport `
-HttpListeners $defaultlistener `
-RequestRoutingRules $frontendRule `
-Sku $sku
Tip
You can modify values of the Name and Tier parameters to use a different SKU. For example: Basic.
Backend servers
Now that you have created the Application Gateway, create the backend virtual machines which will host the websites. A backend can be composed of NICs, virtual machine scale sets, public IP address, internal IP address, fully qualified domain names (FQDN), and multitenant backends like Azure App Service.
In this example, you create two virtual machines to use as backend servers for the application gateway. You also install IIS on the virtual machines to verify that Azure successfully created the application gateway.
Create two virtual machines
- Get the recently created Application Gateway backend pool configuration with
Get-AzApplicationGatewayBackendAddressPool. - Create a network interface with
New-AzNetworkInterface. - Create a virtual machine configuration with
New-AzVMConfig. - Create the virtual machine with
New-AzVM.
When you run the following code sample to create the virtual machines, Azure prompts you for credentials. Enter a user name and a password:
$appgw = Get-AzApplicationGateway -ResourceGroupName myResourceGroupAG -Name myAppGateway
$backendPool = Get-AzApplicationGatewayBackendAddressPool -Name myAGBackendPool -ApplicationGateway $appgw
$vnet = Get-AzVirtualNetwork -ResourceGroupName myResourceGroupAG -Name myVNet
$subnet = Get-AzVirtualNetworkSubnetConfig -VirtualNetwork $vnet -Name myBackendSubnet
$cred = Get-Credential
for ($i=1; $i -le 2; $i++)
{
$nic = New-AzNetworkInterface `
-Name myNic$i `
-ResourceGroupName myResourceGroupAG `
-Location EastUS `
-Subnet $subnet `
-ApplicationGatewayBackendAddressPool $backendpool
$vm = New-AzVMConfig `
-VMName myVM$i `
-VMSize Standard_DS2_v2
Set-AzVMOperatingSystem `
-VM $vm `
-Windows `
-ComputerName myVM$i `
-Credential $cred
Set-AzVMSourceImage `
-VM $vm `
-PublisherName MicrosoftWindowsServer `
-Offer WindowsServer `
-Skus 2016-Datacenter `
-Version latest
Add-AzVMNetworkInterface `
-VM $vm `
-Id $nic.Id
Set-AzVMBootDiagnostic `
-VM $vm `
-Disable
New-AzVM -ResourceGroupName myResourceGroupAG -Location EastUS -VM $vm
Set-AzVMExtension `
-ResourceGroupName myResourceGroupAG `
-ExtensionName IIS `
-VMName myVM$i `
-Publisher Microsoft.Compute `
-ExtensionType CustomScriptExtension `
-TypeHandlerVersion 1.4 `
-SettingString '{"commandToExecute":"powershell Add-WindowsFeature Web-Server; powershell Add-Content -Path \"C:\\inetpub\\wwwroot\\Default.htm\" -Value $($env:computername)"}' `
-Location EastUS
}
Test the application gateway
Although IIS isn't required to create the application gateway, you installed it in this quickstart to verify if Azure successfully created the application gateway.
Use IIS to test the application gateway:
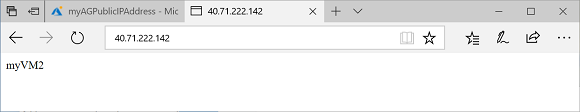
- Run
Get-AzPublicIPAddressto get the public IP address of the application gateway. - Copy and paste the public IP address into the address bar of your browser. When you refresh the browser, you should see the name of the virtual machine. A valid response verifies that the application gateway was successfully created and it can successfully connect with the backend.
Get-AzPublicIPAddress -ResourceGroupName myResourceGroupAG -Name myAGPublicIPAddress
Clean up resources
When you no longer need the resources that you created with the application gateway, delete the resource group. When you delete the resource group, you also delete the application gateway and all its related resources.
To delete the resource group, call the Remove-AzResourceGroup cmdlet:
Remove-AzResourceGroup -Name myResourceGroupAG