Prerequisites to deploy the data controller in direct connectivity mode
This article describes how to prepare to deploy a data controller for Azure Arc-enabled data services in direct connect mode. Before you deploy an Azure Arc data controller understand the concepts described in Plan to deploy Azure Arc-enabled data services.
At a high level, the prerequisites for creating Azure Arc data controller in direct connectivity mode include:
- Have access to your Kubernetes cluster. If you do not have a Kubernetes cluster, you can create a test/demonstration cluster on Azure Kubernetes Service (AKS).
- Connect Kubernetes cluster to Azure using Azure Arc-enabled Kubernetes.
Follow the instructions at Quickstart: Deploy Azure Arc-enabled data services - directly connected mode - Azure portal
Connect Kubernetes cluster to Azure using Azure Arc-enabled Kubernetes
To connect your Kubernetes cluster to Azure, use Azure CLI az with the following extensions or Helm.
Install tools
Add extensions for Azure CLI
Install the latest versions of the following az extensions:
k8s-extensionconnectedk8sk8s-configurationcustomlocation
Run the following commands to install the az CLI extensions:
az extension add --name k8s-extension
az extension add --name connectedk8s
az extension add --name k8s-configuration
az extension add --name customlocation
If you've previously installed the k8s-extension, connectedk8s, k8s-configuration, customlocation extensions, update to the latest version using the following command:
az extension update --name k8s-extension
az extension update --name connectedk8s
az extension update --name k8s-configuration
az extension update --name customlocation
Connect your cluster to Azure
Connect Kubernetes cluster to Azure using Azure Arc-enabled Kubernetes
To connect your Kubernetes cluster to Azure, use Azure CLI az or PowerShell.
Run the following command:
az connectedk8s connect --name <cluster_name> --resource-group <resource_group_name>
<pre>
Helm release deployment succeeded
{
"aadProfile": {
"clientAppId": "",
"serverAppId": "",
"tenantId": ""
},
"agentPublicKeyCertificate": "xxxxxxxxxxxxxxxxxxx",
"agentVersion": null,
"connectivityStatus": "Connecting",
"distribution": "gke",
"id": "/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/AzureArcTest/providers/Microsoft.Kubernetes/connectedClusters/AzureArcTest1",
"identity": {
"principalId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"tenantId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"type": "SystemAssigned"
},
"infrastructure": "gcp",
"kubernetesVersion": null,
"lastConnectivityTime": null,
"location": "eastus",
"managedIdentityCertificateExpirationTime": null,
"name": "AzureArcTest1",
"offering": null,
"provisioningState": "Succeeded",
"resourceGroup": "AzureArcTest",
"tags": {},
"totalCoreCount": null,
"totalNodeCount": null,
"type": "Microsoft.Kubernetes/connectedClusters"
}
</pre>
Tip
The above command without the location parameter specified creates the Azure Arc-enabled Kubernetes resource in the same location as the resource group. To create the Azure Arc-enabled Kubernetes resource in a different location, specify either --location <region> or -l <region> when running the az connectedk8s connect command.
Note
If you are logged into Azure CLI using a service principal, an additional parameter needs to be set for enabling the custom location feature on the cluster.
A more thorough walk-through of this task is available at Connect an existing Kubernetes cluster to Azure arc.
Verify azure-arc namespace pods are created
Before you proceed to the next step, make sure that all of the azure-arc- namespace pods are created. Run the following command.
kubectl get pods -n azure-arc
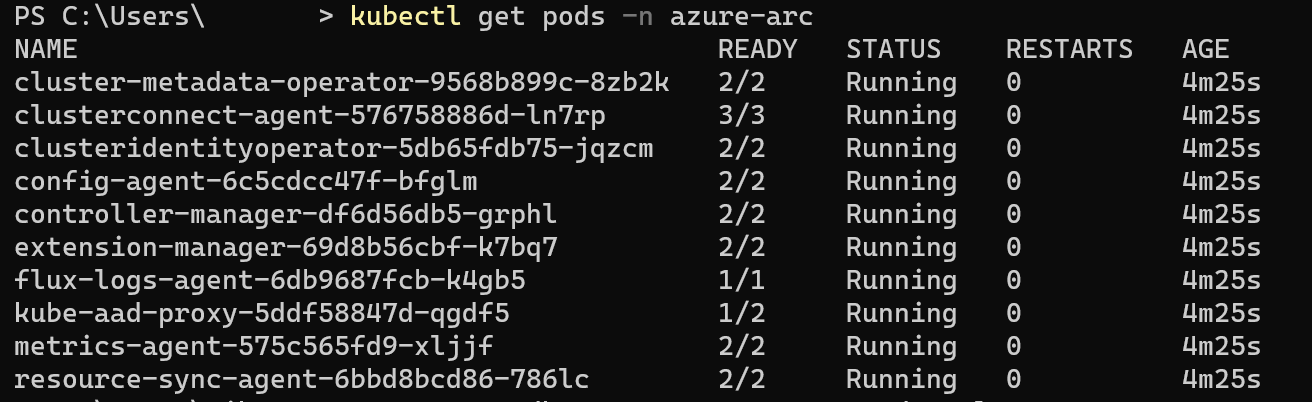
When all containers return a status of running, you can connect the cluster to Azure.
Optionally, keep the Log Analytics workspace ID and Shared access key ready
When you deploy Azure Arc-enabled data controller, you can enable automatic upload of metrics and logs during setup. Metrics upload uses the system assigned managed identity. However, uploading logs requires a Workspace ID and the access key for the workspace.
You can also enable or disable automatic upload of metrics and logs after you deploy the data controller.
For instructions, see Create a log analytics workspace.
Create Azure Arc data services
After you have completed these prerequisites, you can Deploy Azure Arc data controller | Direct connect mode - Azure Portal or using the Azure CLI.