Start planning multicloud protection
This article introduces guidance to help you design a solution for securing and protecting a multicloud environment with Microsoft Defender for Cloud. The guidance can be used by cloud solution and infrastructure architects, security architects and analysts, and anyone else involved in designing a multicloud security solution.
As you capture your functional and technical requirements, the articles provide an overview of multicloud capabilities, planning guidance, and prerequisites.
Follow the guides in order. They build on each other to help you make design decisions. We recommend that you reread the articles as needed, to understand and incorporate all considerations.
What should I get from this guide?
Use this guide as an aid as you design Cloud Security Posture Management (CSPM) and Cloud Workload Protection Plan (CWPP) solutions across multicloud environments. After reading the articles you should have answers to the following:
- What questions should I ask and answer as I design my multicloud solution?
- What steps do I need to complete to design a solution?
- What technologies and capabilities are available to me?
- What trade-offs do I need to consider?
Problem space
As organizations span multiple cloud providers, it becomes increasingly complex to centralize security, and for security teams to work across multiple environments and vendors.
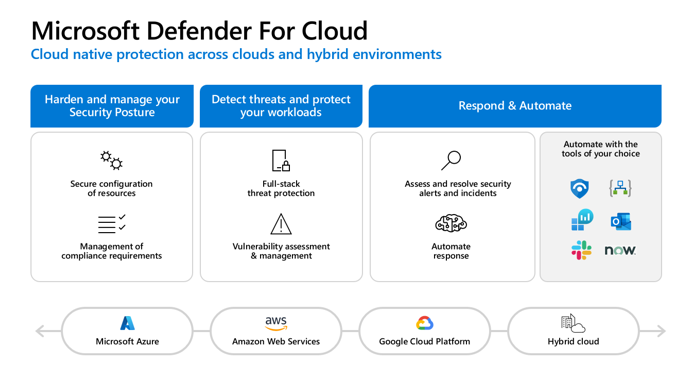
Defender for Cloud helps you to protect your multicloud environment by strengthening your security posture and protecting your workloads. Defender for Cloud provides a single dashboard to manage protection across all environments.
Before you begin
Before working through these articles, you should have a basic understanding of Azure, Defender for Cloud, Azure Arc, and your multicloud AWS/GCP environment.
Next steps
In this article, you have been provided an introduction to begin your path to designing a multicloud security solution. Continue with the next step to determine business needs.