Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure role-based access control (Azure RBAC) is the way that you manage access to Azure resources. In this tutorial, you grant a user access to view everything in a subscription and manage everything in a resource group using Azure PowerShell.
In this tutorial, you learn how to:
- Grant access for a user at different scopes
- List access
- Remove access
If you don't have an Azure subscription, create a free account before you begin.
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Prerequisites
To complete this tutorial, you will need:
- Permissions to create users in Microsoft Entra ID (or have an existing user)
- Azure Cloud Shell
- Microsoft Graph PowerShell SDK
Role assignments
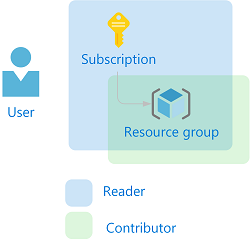
In Azure RBAC, to grant access, you create a role assignment. A role assignment consists of three elements: security principal, role definition, and scope. Here are the two role assignments you will perform in this tutorial:
| Security principal | Role definition | Scope |
|---|---|---|
| User (RBAC Tutorial User) |
Reader | Subscription |
| User (RBAC Tutorial User) |
Contributor | Resource group (rbac-tutorial-resource-group) |
Create a user
To assign a role, you need a user, group, or service principal. If you don't already have a user, you can create one.
In Azure Cloud Shell, create a password that complies with your password complexity requirements.
$PasswordProfile = @{ Password = "<Password>" }Create a new user for your domain using the New-MgUser command.
New-MgUser -DisplayName "RBAC Tutorial User" -PasswordProfile $PasswordProfile ` -UserPrincipalName "rbacuser@example.com" -AccountEnabled:$true -MailNickName "rbacuser"DisplayName Id Mail UserPrincipalName ----------- -- ---- ----------------- RBAC Tutorial User aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb rbacuser@example.com
Create a resource group
You use a resource group to show how to assign a role at a resource group scope.
Get a list of region locations using the Get-AzLocation command.
Get-AzLocation | select LocationSelect a location near you and assign it to a variable.
$location = "westus"Create a new resource group using the New-AzResourceGroup command.
New-AzResourceGroup -Name "rbac-tutorial-resource-group" -Location $locationResourceGroupName : rbac-tutorial-resource-group Location : westus ProvisioningState : Succeeded Tags : ResourceId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group
Grant access
To grant access for the user, you use the New-AzRoleAssignment command to assign a role. You must specify the security principal, role definition, and scope.
Get the ID of your subscription using the Get-AzSubscription command.
Get-AzSubscriptionName : Pay-As-You-Go Id : 00000000-0000-0000-0000-000000000000 TenantId : aaaabbbb-0000-cccc-1111-dddd2222eeee State : EnabledSave the subscription scope in a variable.
$subScope = "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e"Assign the Reader role to the user at the subscription scope.
New-AzRoleAssignment -SignInName rbacuser@example.com ` -RoleDefinitionName "Reader" ` -Scope $subScopeRoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial User SignInName : rbacuser@example.com RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : User CanDelegate : FalseAssign the Contributor role to the user at the resource group scope.
New-AzRoleAssignment -SignInName rbacuser@example.com ` -RoleDefinitionName "Contributor" ` -ResourceGroupName "rbac-tutorial-resource-group"RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group DisplayName : RBAC Tutorial User SignInName : rbacuser@example.com RoleDefinitionName : Contributor RoleDefinitionId : b24988ac-6180-42a0-ab88-20f7382dd24c ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : User CanDelegate : False
List access
To verify the access for the subscription, use the Get-AzRoleAssignment command to list the role assignments.
Get-AzRoleAssignment -SignInName rbacuser@example.com -Scope $subScopeRoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/ffffffff-eeee-dddd-cccc-bbbbbbbbbbb0 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial User SignInName : rbacuser@example.com RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : User CanDelegate : FalseIn the output, you can see that the Reader role has been assigned to the RBAC Tutorial User at the subscription scope.
To verify the access for the resource group, use the Get-AzRoleAssignment command to list the role assignments.
Get-AzRoleAssignment -SignInName rbacuser@example.com -ResourceGroupName "rbac-tutorial-resource-group"RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group DisplayName : RBAC Tutorial User SignInName : rbacuser@example.com RoleDefinitionName : Contributor RoleDefinitionId : b24988ac-6180-42a0-ab88-20f7382dd24c ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : User CanDelegate : False RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/ffffffff-eeee-dddd-cccc-bbbbbbbbbbb0 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial User SignInName : rbacuser@example.com RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : User CanDelegate : FalseIn the output, you can see that both the Contributor and Reader roles have been assigned to the RBAC Tutorial User. The Contributor role is at the rbac-tutorial-resource-group scope and the Reader role is inherited at the subscription scope.
(Optional) List access using the Azure Portal
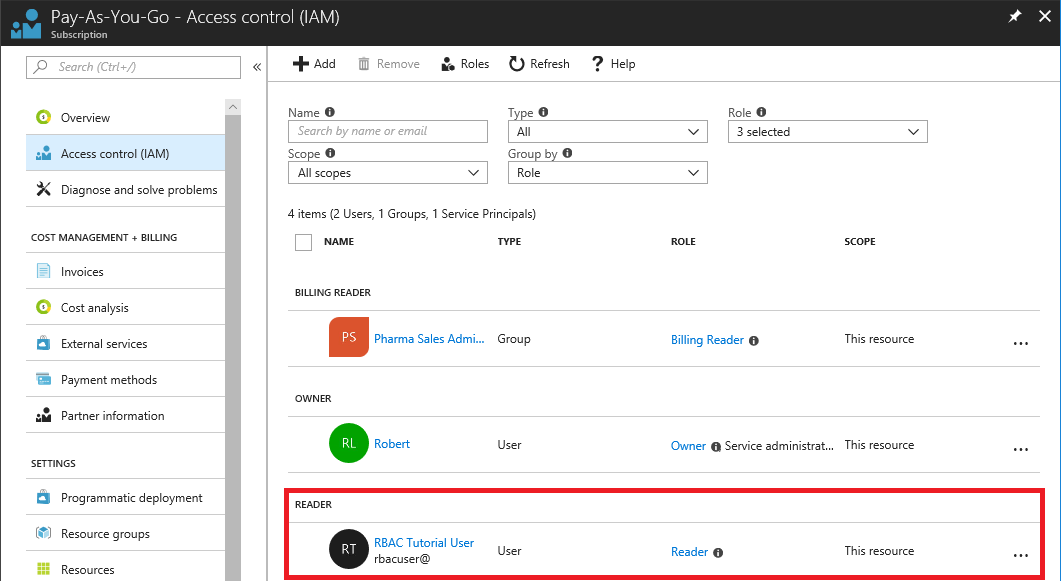
To see how the role assignments look in the Azure portal, view the Access control (IAM) blade for the subscription.
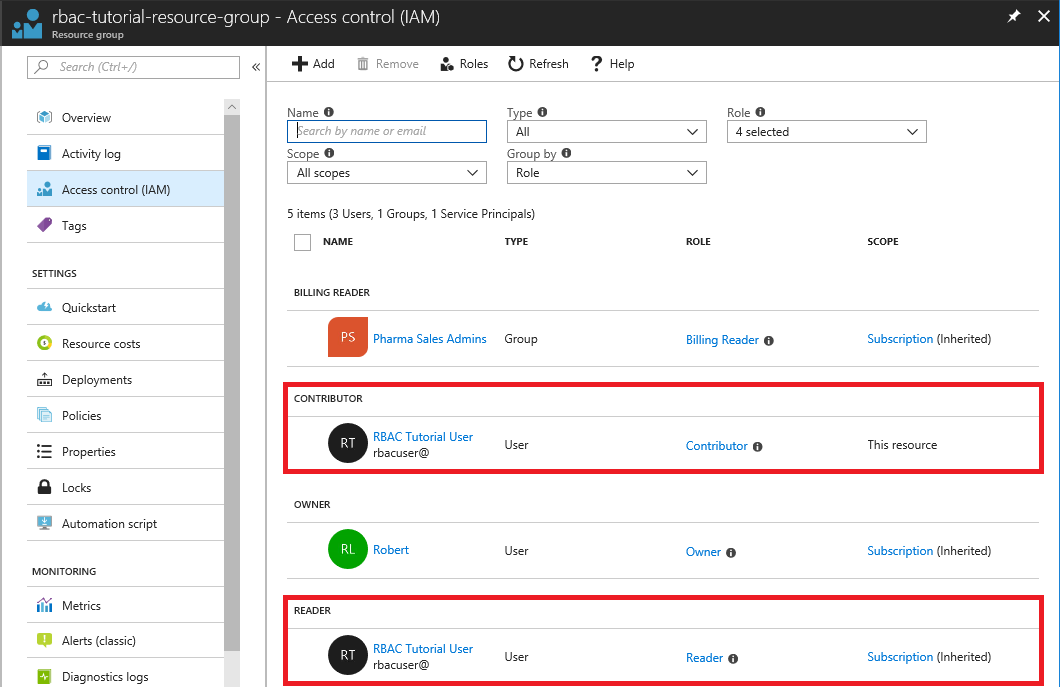
View the Access control (IAM) blade for the resource group.
Remove access
To remove access for users, groups, and applications, use Remove-AzRoleAssignment to remove a role assignment.
Use the following command to remove the Contributor role assignment for the user at the resource group scope.
Remove-AzRoleAssignment -SignInName rbacuser@example.com ` -RoleDefinitionName "Contributor" ` -ResourceGroupName "rbac-tutorial-resource-group"Use the following command to remove the Reader role assignment for the user at the subscription scope.
Remove-AzRoleAssignment -SignInName rbacuser@example.com ` -RoleDefinitionName "Reader" ` -Scope $subScope
Clean up resources
To clean up the resources created by this tutorial, delete the resource group and the user.
Delete the resource group using the Remove-AzResourceGroup command.
Remove-AzResourceGroup -Name "rbac-tutorial-resource-group"Confirm Are you sure you want to remove resource group 'rbac-tutorial-resource-group' [Y] Yes [N] No [S] Suspend [?] Help (default is "Y"):When asked to confirm, type Y. It will take a few seconds to delete.
Delete the user using the Remove-MgUser command.
$User = Get-MgUser -Filter "DisplayName eq 'RBAC Tutorial User'" Remove-MgUser -UserId $User.Id