Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Restricted site access control lets you prevent oversharing by designating access of SharePoint sites and its content to users in a specific group. Users not in the specified group can't access the site or its content, even if they had prior permissions or a shared link. This policy can be applied on Microsoft 365 group-connected, Teams-connected, and nongroup connected sites using Microsoft 365 groups or Microsoft Entra security groups.
Site access restriction policies are applied when a user attempts to open a site or access a file. Users with direct permissions to the file can still view files in search results. However, they can't access the files if they're not part of the specified group.
Restricting site access via group membership can minimize the risk of oversharing content. For insights into data sharing, see Data access governance reports.
What do you need to restrict site access?
What are the license requirements?
Your organization needs to have the right license and meet certain administrative permissions or roles to use the feature described in this article.
First, your organization must have one of the following base licenses:
- Office 365 E3, E5, or A5
- Microsoft 365 E1, E3, E5, or A5
Additionally, you need at least one of these licenses:
- Microsoft 365 Copilot license: At least one user in your organization must be assigned a Copilot license (this user doesn't need to be a SharePoint administrator).
- Microsoft SharePoint Advanced Management license: Available as a standalone purchase.
Administrator requirements
You must be a SharePoint administrator or have equivalent permissions.
Additional information
If your organization has a Copilot license and at least one person in your organization is assigned a Copilot license, SharePoint administrators automatically gain access to the SharePoint Advanced Management features needed for Copilot deployment.
For organizations without a Copilot license, you can use SharePoint Advanced Management features by purchasing a standalone SharePoint Advanced Management license.
Enable site-level access restriction for your organization
You must enable site-level access restriction for your organization before you can configure it for individual sites. You can also delegate site access restriction control to all the site admins of your organization.
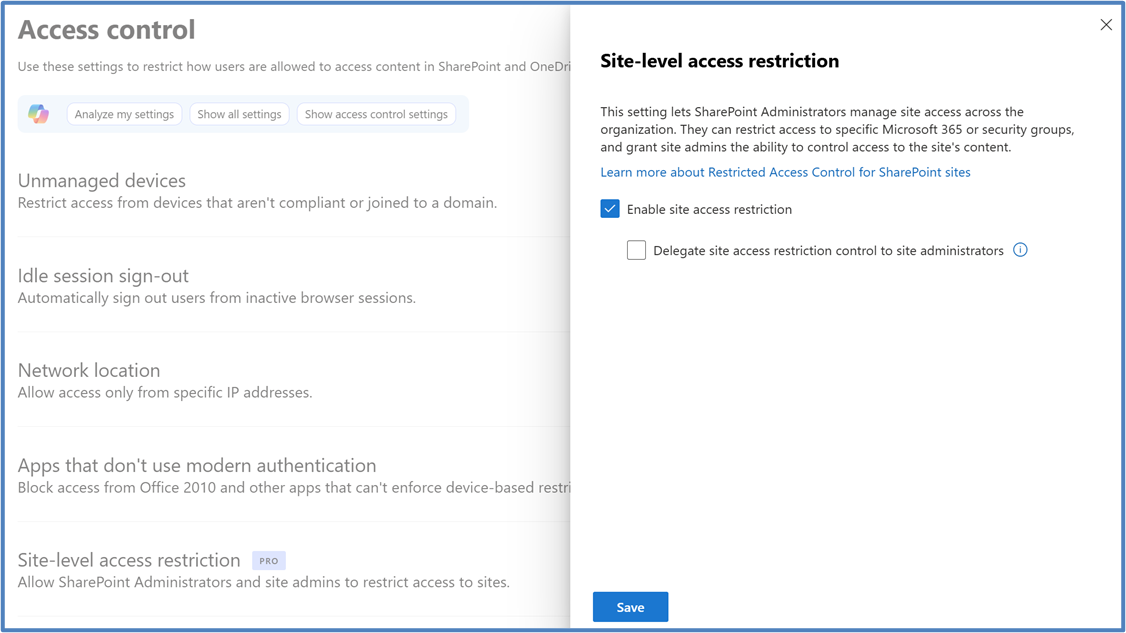
To enable site-level access restriction for your organization in the SharePoint admin center, follow these steps:
Expand Policies and select Access control.
Select Site-level access restriction.
Select Allow access restriction and then select Save.
To enable site-level access restriction for your organization using PowerShell, run the following command:
Set-SPOTenant -EnableRestrictedAccessControl $true
It might take up to one hour for the command to take effect.
Delegate Management of Restricted Access Control to Site Admins
As a SharePoint administrator, you can also delegate management of Restricted Access Control to site admin. Upon managing the policy, the site admins would need to provide appropriate justification on why the policy is being updated.
By default, the delegation is turned off. If you decide to enable it, run the following command:
Set-SPOTenant -DelegateRestrictedAccessControlManagement $true
Once the Restricted Access Control is delegated to all the site admins, they can manage the policy.
Check status of Delegate management of Restricted Access Control to site admins
To check the delegation status, run the following command:
Get-SPOTenant | Select-Object DelegateRestrictedAccessControlManagement
Note
For Microsoft 365 Multi-Geo users, run this command separately for each desired geo-location.
Restrict access to all SharePoint sites using Microsoft 365 group or Microsoft Entra security groups
You can restrict access to a SharePoint site by specifying Microsoft Entra security groups or Microsoft 365 groups as the Restricted Access Control group. The control group should have the users who should be allowed access to the site and its content.
For a site, you can configure up to 10 Microsoft Entra security groups or Microsoft 365 groups. Once the policy is applied, users in the specified group who have access permission to the content are allowed access.
Important
Adding people to the Restricted Access Control group (Microsoft Entra security group or Microsoft 365 group) doesn't automatically give the users access permission to the site or the content. For a user to be able to access the content protected with this policy, the user would need to have both the site or content access permission AND be a member of the Restricted Access Control group.
Note
You can also use dynamic security groups as a Restricted Access Control group if you want to base group membership on user properties.
Manage site access for a site
To manage site access for a site, follow these steps:
In SharePoint admin center, expand Sites and select Active sites.
Select the site you want to manage and the site details panel appears.
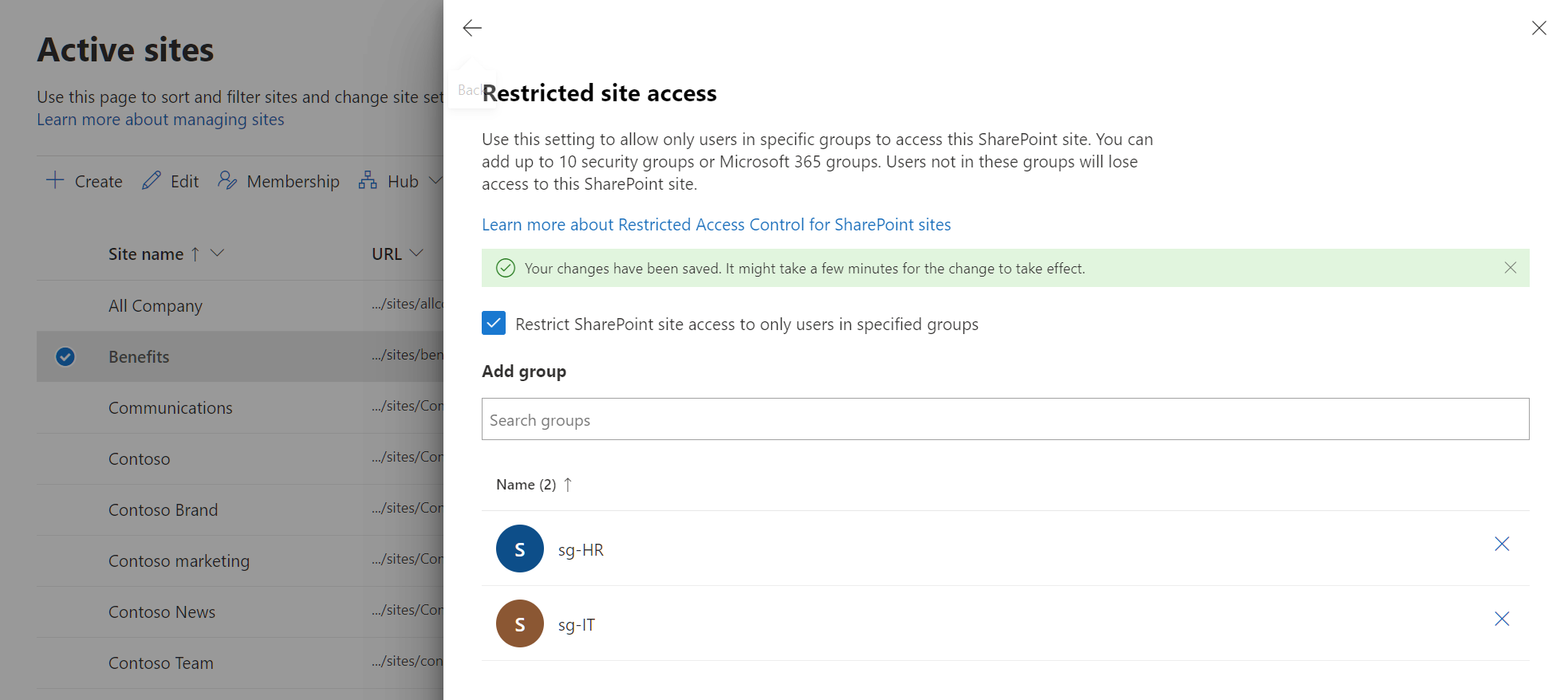
In Settings tab, select Edit in the Restricted site access section.
Select the Restrict SharePoint site access to only users in specified groups check box.
Add or remove your security groups or Microsoft 365 groups and select Save.
In order for site access restriction to be applied to the site, you must add at least one group to the site access restriction policy.
For a group connected site, the Microsoft 365 group connected to the site is added as the default Restricted Access Control group. You can choose to keep this group and add more Microsoft 365 or Microsoft Entra Security groups as Restricted Access Control group.
Note
There's a tag labeled as Default group marked against the Microsoft 365 group connected to the site as shown in the previous image.
To manage site access restriction for a SharePoint site using PowerShell, use the following commands:
| Action | PowerShell command |
|---|---|
| Enable site access restriction | Set-SPOSite -Identity <siteurl> -RestrictedAccessControl $true |
| Add group | Set-SPOSite -Identity <siteurl> -AddRestrictedAccessControlGroups <comma separated group GUIDS> |
| Edit group | Set-SPOSite -Identity <siteurl> -RestrictedAccessControlGroups <comma separated group GUIDS> |
| View group | Get-SPOSite -Identity <siteurl> Select RestrictedAccessControl, RestrictedAccessControlGroups |
| Remove group | Set-SPOSite -Identity <siteurl> -RemoveRestrictedAccessControlGroups <comma separated group GUIDS> |
| Reset site access restriction | Set-SPOSite -Identity <siteurl> -ClearRestrictedAccessControl |
Site admin experience
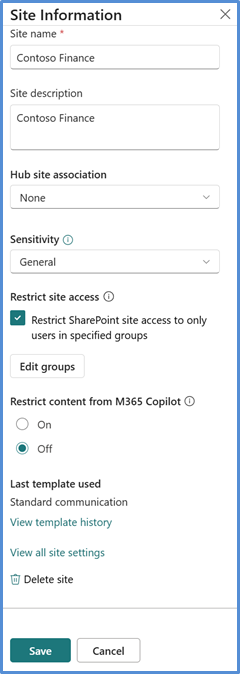
Once the site access restriction control is delegated to site admins, they can configure the site access restriction setting at the Site Information panel.
To restrict access to a SharePoint site:
You can limit who can access a site by using Microsoft Entra security groups or Microsoft 365 groups.
Add the groups that contain the users who should have access.
You can add up to 10 groups for each site.
When the site access restriction setting configuration is saved, only users in those groups and those who already have permission to the content can access the site.
You would also need to provide justification whenever the site access restriction setting is updated.
Site owner experience:
Once the policy is applied to the site, the policy status and all configured control groups are displayed for site owners on the Site access panel in addition to the Site Information and Permissions panels.
Shared and private channel sites
Shared and private channel sites are separate from the Microsoft 365 group-connected site that standard channels use. Because shared and private channel sites aren't connected to the Microsoft 365 group, site access restriction policies applied to the team don't affect them. You must enable site access restriction for each shared or private channel site separately as nongroup connected sites.
For shared channel sites, only internal users in the resource tenant are subject to site access restriction. External channel participants are excluded from site access restriction policy and only evaluated per the site's existing site permissions.
Important
Adding people to the security group or Microsoft 365 group doesn't give users access to the channel in Teams. We recommend adding or removing the same users of the Teams channel in Teams and the security group or Microsoft 365 group, so users have access to both Teams and SharePoint sites.
Auditing
Audit events are available in the Microsoft Purview portal to help you monitor site access restriction activities. Audit events are logged for the following activities:
- Applying site access restriction for site
- Removing site access restriction for site
- Changing site access restriction groups for site
- Site admin's justification for updating site access restriction
Reporting
Restricted site access policy insights
As an IT administrator, you can view the following reports to gain more insight about SharePoint sites protected with restricted site access policy:
- Sites protected by restricted site access policy (RACProtectedSites)
- Details of access denials due to restricted site access policy (ActionsBlockedByPolicy)
Restricted site access policy reports are available in nongovernment cloud environments, and GCC, GCC-High, and DoD government cloud environments. The reports are currently unavailable for Gallatin, even if you have the required licenses.
Note
It can take a few hours to generate each report.
Sites protected by restricted site access policy report
You can run the following commands in SharePoint PowerShell to generate, view, and download the reports:
| Action | PowerShell command | Description |
|---|---|---|
| Generate report | Start-SPORestrictedAccessForSitesInsights -RACProtectedSites |
Generates a list of sites protected by restricted site access policy |
| View report | Get-SPORestrictedAccessForSitesInsights -RACProtectedSites -ReportId <Report GUID> |
The report shows the top 100 sites with the highest page views that are protected by the policy. |
| Download report | Get-SPORestrictedAccessForSitesInsights -RACProtectedSites -ReportId <Report GUID> -Action Download |
This command must be run as an administrator. The downloaded report is located on the path where the command was run. |
| Percentage of site protected with restricted site access report | Get-SPORestrictedAccessForSitesInsights -RACProtectedSites -ReportId <Report GUID> -InsightsSummary |
This report shows the percentage of sites that are protected by the policy out of the total number of sites |
Access denials due to restricted site access policy report
You can run the following commands to create, fetch, and view report for access denials due to restricted site access reports:
| Action | PowerShell command | Description |
|---|---|---|
| Create access denials report | Start-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy |
Creates a new report for fetching access denial details |
| Fetch access denials report status | Get-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy |
Fetches the status of the generated report. |
| Latest access denials in the past 28 days | Get-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy -ReportId <Report ID> -Content AllDenials |
Gets a list of the most recent 100 access denials that occurred in the past 28 days |
| View list of top users who were denied access | Get-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy -ReportId <Report ID> -Content TopUsers |
Gets a list of the top 100 users who received the most access denials |
| View list of top sites that received the most access denials | Get-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy -ReportId <Report ID> -Content TopSites |
Gets a list of the top 100 sites that had the most access denials |
| Distribution of access denials across different types of sites | Get-SPORestrictedAccessForSitesInsights -ActionsBlockedByPolicy -ReportId <Report ID> -Content SiteDistribution |
Shows the distribution of access denials across different types of sites |
Note
To view up to 10,000 denials, you must download the reports. Run the download command as an administrator and the downloaded reports are located on the path from where command was run.
Sharing of site and content with users outside of Restricted Access Control Groups (opt-in capability)
Sharing of SharePoint sites and its content doesn't honor restricted site access policy by default. The SharePoint administrator can choose to restrict sharing of site and its content with users who aren't members of the Restricted Access Control group.
To restrict sharing capability with users outside of the Restricted Access Control group, enable it, run the following PowerShell command in SharePoint Online Management Shell as an Administrator:
Set-SPOTenant -AllowSharingOutsideRestrictedAccessControlGroups $false
Sharing with users
Once sharing restriction is applied, sharing is blocked for users who aren't members of the Restricted Access Control group.
Sharing with groups
Sharing is allowed with Microsoft Entra Security or Microsoft 365 groups that are part of the Restricted Access Control groups list. Thus, sharing with all other groups including Everyone except external users or SharePoint groups aren't allowed.
Note
Sharing of a site and its content is now allowed for the nested security groups that are part of the Restricted Access Control groups.
Configure the Learn more link for access denial error page (opt-in capability)
Configure the Learn more link to inform users who were denied access to a SharePoint site due to the restricted site access control policy. With this customizable error link, you can provide more information and guidance to your users.
Note
The Learn more link is a tenant-level setting that applies to all sites with Restricted Access Control policy enabled.
To configure the link, run the following command in SharePoint PowerShell:
Set-SPOTenant -RestrictedAccessControlForSitesErrorHelpLink "<Learn more URL>"
To fetch the value of the link, run the following command:
Get-SPOTenant | select RestrictedAccessControlForSitesErrorHelpLink
The configured learn more link is launched when the user selects the Know more about your organization's policies here link.