Hello!
As you already may know MS has removed the possibility to create/renew certificates in GUI ( ECP certificate request has been deprecated in Exchange 2019 CU12 and higher and in Exchange 2016 CU23 and higher. ) Instead the EPS should be used and there's the example (in the article posted above) for creating a wildcard certificate request (along with the "ordinary" SAN certificate and the single-name certificate) that I followed and got the following results:
1) create a wildcard certificate:
Wildcard certificate request
These examples create certificate request files for wildcard certificates with the following properties:
SubjectName: .contoso.com in the United States, which requires the value C=US,CN=.contoso.com.
RequestFile: \FileServer01\Data\Contoso Wildcard Cert.<cer or pfx>
FriendlyName: Contoso.com Wildcard Cert
$txtrequest = New-ExchangeCertificate -PrivateKeyExportable $True -GenerateRequest -FriendlyName "Contoso.com Wildcard Cert" -SubjectName "C=US,CN=*.contoso.com"
[System.IO.File]::WriteAllBytes('\FileServer01\Data\Contoso Wildcard Cert.req', [System.Text.Encoding]::Unicode.GetBytes($txtrequest))
- I just used contoso.net instead of contoso.com:
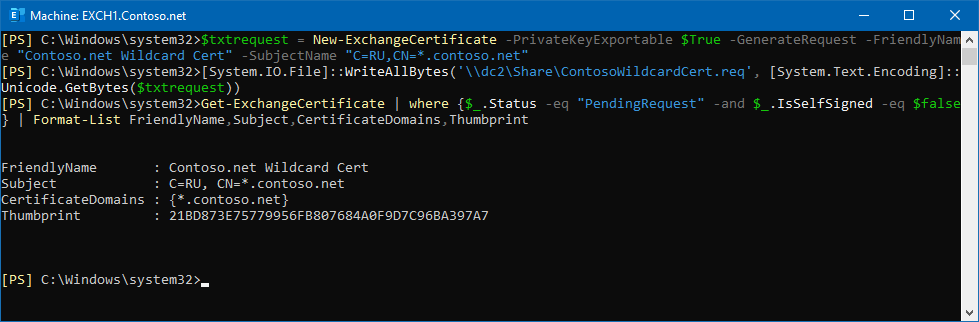
2) Since I already have in my network the configured Windows-based CA I had no issues requesting the wildcard certificate and importing it into Exchange 2019 CU12:
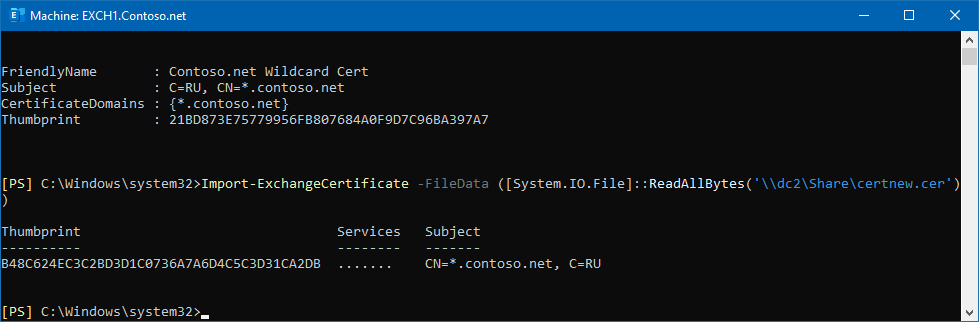
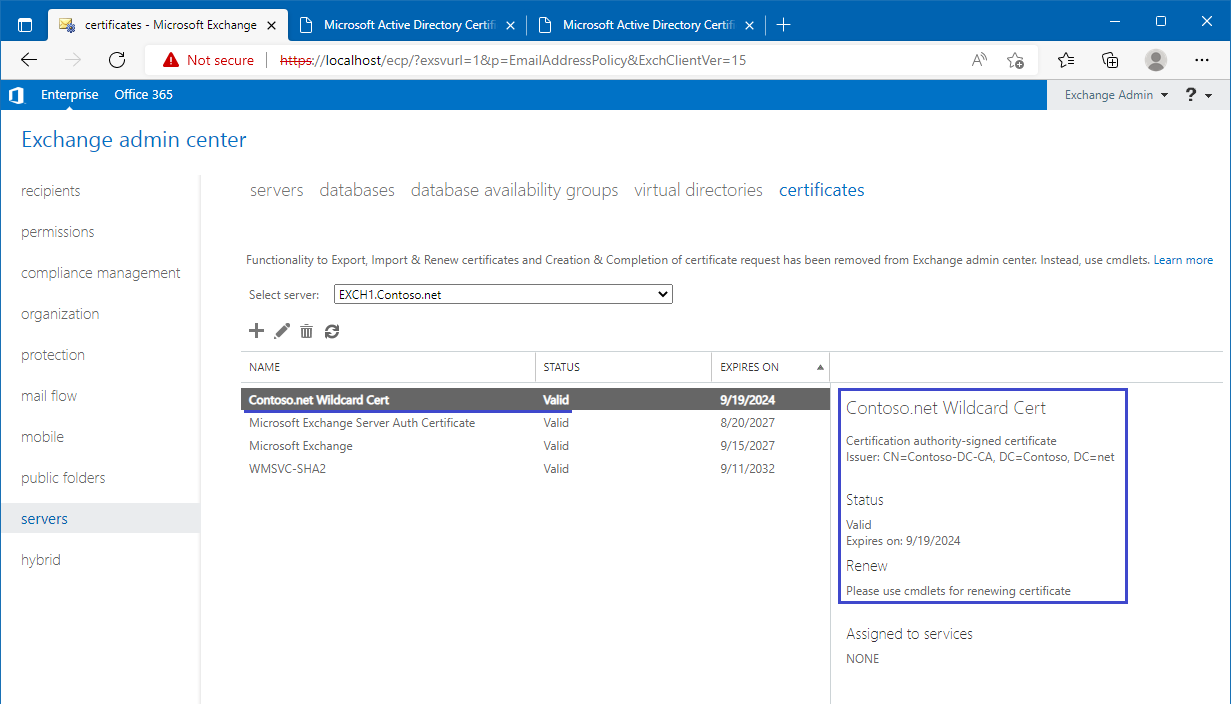
3)
No single issue - so far so good... but when I tried to access https://mail.contoso.net I got this:
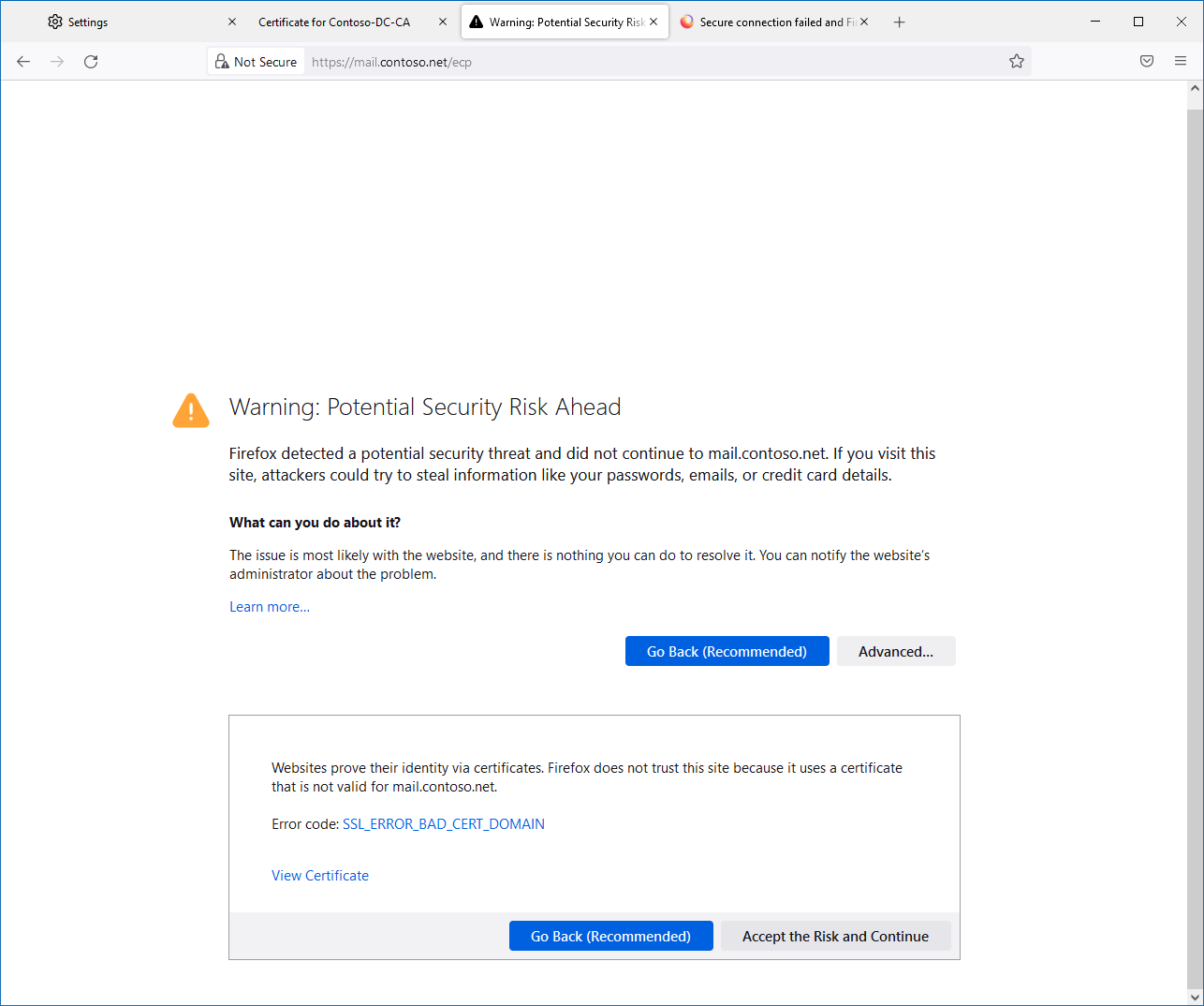
- Edge displays ~the same error (~"Certificate's common name is wrong" - can't publish a picture as it had stopped throwing it after proceeding as not secure).
4) I then created and imported the "ordinary" SAN certificate - again, according to the article above - and it worked out perfectly:
Q1: Is it a bug (either in Exchange or in the documentation) or CU12 can't work with wildcard certificates (I had not any issues with them up to CU11, even using the same CA)?
Q2: What was the purpose of removing this functionality from GUI (I know that's a rhetorical question but...) ???
Thank you in advance,
Michael






