We are trying to implement SSO Azure AD B2C using Custom policies. We have a single App Registration with 2 redirect URIs for 2 Single Page Applications. The Single Sign In Process is working as expected. But we are facing an issue with Single Sign Out.
Our requirement is to perform logout from one of the SPA then it should be signed out from other applications as well. But with our current implementation other Single Page Applications still have active sessions and are not redirected as expected.
Our current implementation steps are given below
- Added below Redirect URLs
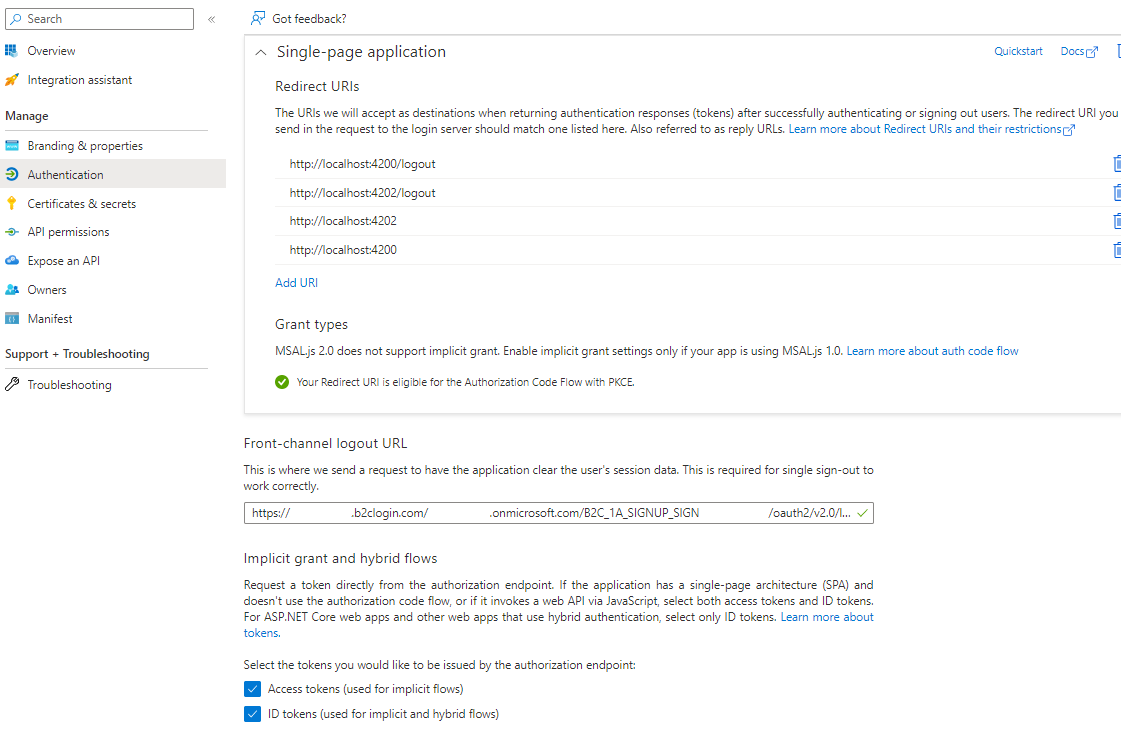
- Added Front-channel logout URL
https://{tenantname}.b2clogin.com/{tenantname}.onmicrosoft.com/{PolicyName}/oauth2/v2.0/logout
- Added below Claims Provider in the policy
<ClaimsProvider>
<DisplayName>Local Account SignIn</DisplayName>
<TechnicalProfiles>
<!-- JWT Token Issuer -->
<TechnicalProfile Id="JwtIssuer">
<DisplayName>JWT token Issuer</DisplayName>
<Protocol Name="OpenIdConnect" />
<OutputTokenFormat>JWT</OutputTokenFormat>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-jwt-issuer" />
</TechnicalProfile>
<!-- Session management technical profile for OIDC based tokens -->
<TechnicalProfile Id="SM-jwt-issuer">
<DisplayName>Session Management Provider</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.SSO.OAuthSSOSessionProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
</TechnicalProfile>
<!--SAML token issuer-->
<TechnicalProfile Id="Saml2AssertionIssuer">
<DisplayName>SAML token issuer</DisplayName>
<Protocol Name="SAML2" />
<OutputTokenFormat>SAML2</OutputTokenFormat>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-Saml-issuer" />
</TechnicalProfile>
<!-- Session management technical profile for SAML based tokens -->
<TechnicalProfile Id="SM-Saml-issuer">
<DisplayName>Session Management Provider</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.SSO.SamlSSOSessionProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
</TechnicalProfile>
</TechnicalProfiles>
</ClaimsProvider>
- Added the User journey code in Policy
<UserJourneyBehaviors>
<SingleSignOn Scope="TrustFramework" EnforceIdTokenHintOnLogout="true" />
</UserJourneyBehaviors>
- Added the below piece of code in our SPA(Angular)
signOut(): void {
localStorage.removeItem("currentUser");
const request = {
redirectStartPage: "/",
scopes: ["openid", "profile", ${environment.AppClientId}]
};
this.msalService.acquireTokenSilent(request as SilentRequest).subscribe({
next: (result: AuthenticationResult) => {
this.msalService.logoutRedirect({idTokenHint: result.idToken, postLogoutRedirectUri: 'http://localhost:4200/logout'});
},
error: (error) => {
}
});
}
Please guide me to fix this issue and please correct me if I am doing something wrong here.
