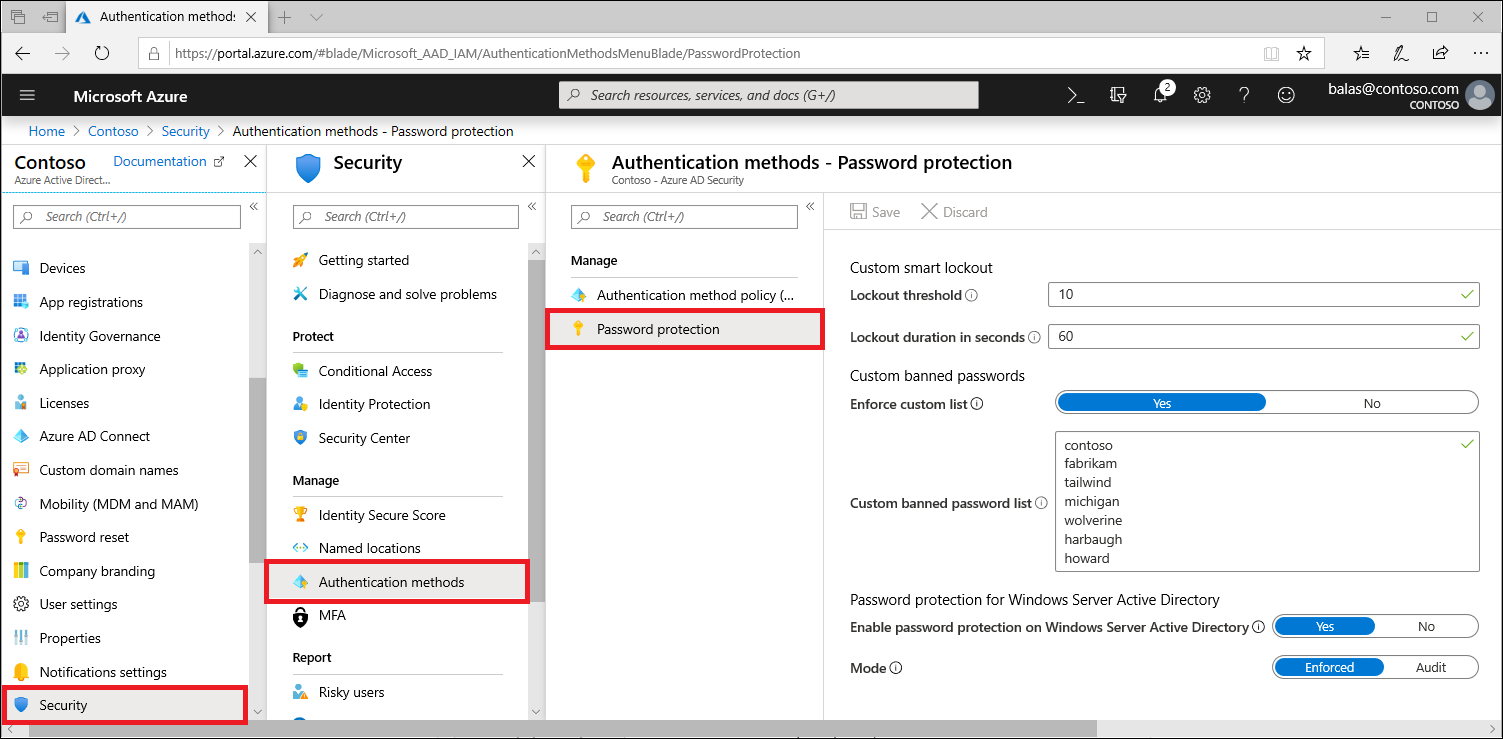
Hi @brichardi
Please take a look at using Conditional Access Policies to restrict IP addresses (with Named locations):
Location condition in policy
This would be ideal if you don't require your students to login outside of the school, but may not work if you need them to login at home. You could combo this together with a Student only Azure AD Dynamic group so that this only applies to Students (who don't have MFA enabled, assuming your staff do).
As @!Daniel Bradley stated above, you cannot stop a spray attack as Conditional Access Policies are triggered AFTER the event (not before). You can however use what I mentioned to block outside countries from authenticating to mitigate some risk.
---------------------------------------------
If this is helpful please accept answer.