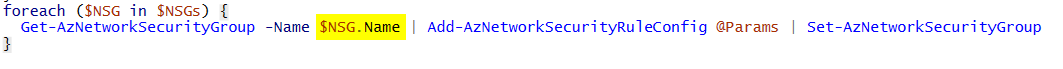
Hi @Anonymous ,
this script is working here with the two NSGs (testNSG1 and testNSG2):
$NSGs = "testNSG1", "testNSG2"
$Params = @{
'Name' = 'Allow_NessusScanner_IN'
'Protocol' = '*'
'Direction' = 'Inbound'
'Priority' = 2970
'SourceAddressPrefix' = '10.96.2.69'
'SourcePortRange' = '1234'
'DestinationAddressPrefix' = 'VirtualNetwork'
'DestinationPortRange' = '*'
'Access' = 'Allow'
}
foreach ($NSG in $NSGs) {
Get-AzNetworkSecurityGroup -Name $NSG | Add-AzNetworkSecurityRuleConfig @Params | Set-AzNetworkSecurityGroup
}
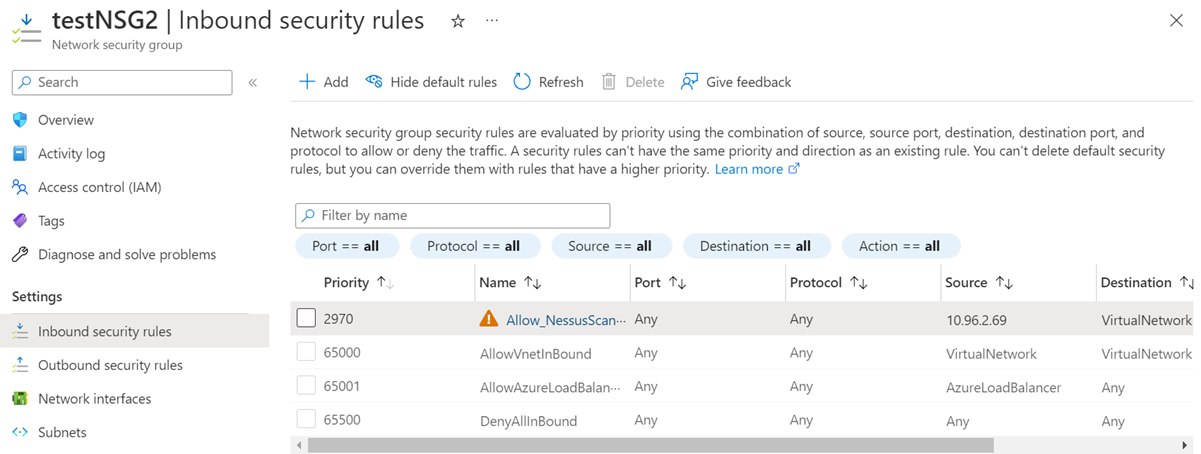
The result looks like this:
(If the reply was helpful please don't forget to upvote and/or accept as answer, thank you)
Regards
Andreas Baumgarten