Hello Aarush,
Greetings! Welcome to Microsoft Q&A Platform.
The 403 error you encountered indicates that you don’t have the necessary permissions.
Please ensure that you are able to access the Extension Microsoft_AAD_IAM blade if not, it could mean that the admin of the tenant has not given the permission to access the "Admin Portal" with a non-administrator account. This can happen even if you are an Owner of the subscription since the IAM policy of the Entra ID/Azure AD tenant will still block you in this scenario.
If this is the case, the admin needs to either set "restrict access to Microsoft Entra ID administration center" to "No" or grant you an admin role.
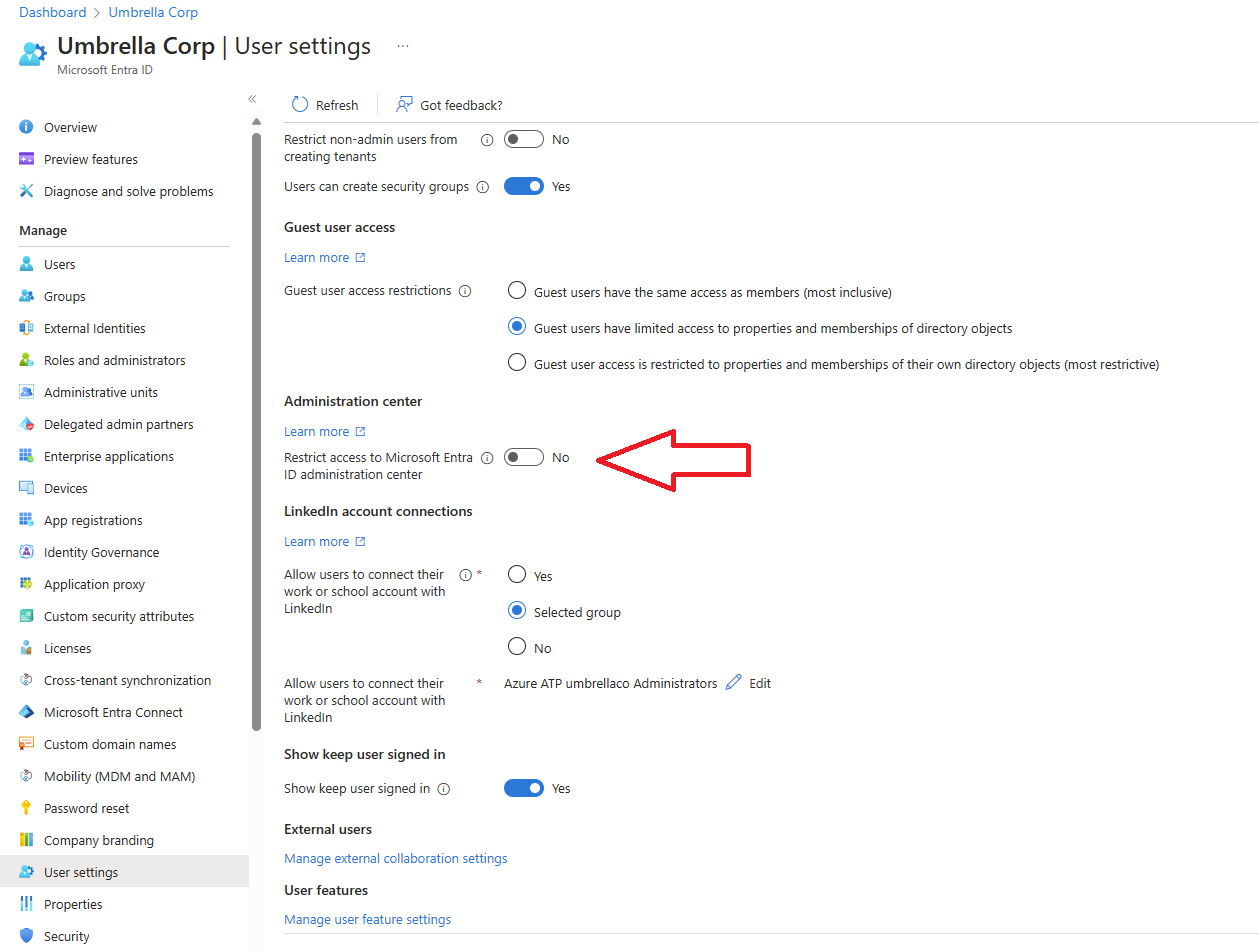
Also consider the following to troubleshoot the issue,
- Sometimes this issue occurs if there is something blocking the network connection. If this is the case, this issue can often be resolved by whitelisting the required endpoints as mentioned in our Microsoft documentation: https://learn.microsoft.com/en-us/azure/azure-portal/azure-portal-safelist-urls?tabs=public-cloud#azure-portal-framework
- Also do check if you have all the required RBAC roles
To request the user delegation key, you must assign to a security principal the Microsoft.Storage/storageAccounts/blobServices/generateUserDelegationKey action. The following built-in RBAC roles include the Microsoft.Storage/storageAccounts/blobServices/generateUserDelegationKey action, either explicitly or as part of a wildcard definition: Contributor, Storage Account Contributor, Storage Blob Data Contributor, Storage Blob Data Owner, Storage Blob Data Reader, Storage Blob Delegator. reference document: https://learn.microsoft.com/en-us/rest/api/storageservices/create-user-delegation-sas#assign-permissions-with-rbac
- Please try updating the browser to the latest version and check using the Chrome browser instead of Edge to see if you get the same results.
- Please try to load the "Entra ID" blade from the Search bar by searching for "Microsoft Entra ID" and confirm if you get the same results that way.
Additional information: When using Azure Storage account shared key auth, HTTP requests sent by this library will generate a string to sign based on subset of HTTP headers and finally sign with account key. Modifying headers after the signing will lead to auth errors.
Authorize requests to Azure Storage : https://learn.microsoft.com/en-us/rest/api/storageservices/authorize-requests-to-azure-storage
403 is seen when authorizing with a shared key because "All authorized requests must include the Coordinated Universal Time (UTC) timestamp for the request." Information about this can be found in Authorize with Shared Key and also you can try using storage explorer to generate SAS with the same configuration and see if it works.
Hope this answer helps! Please let us know if you have any further queries. I’m happy to assist you further.
Please "Accept the answer” and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.