Hello @Aakriti Verma ,
There are 3 ways to use IPSec encryption over ExpressRoute:
1.IPSec can be done over ExpressRoute Microsoft peering:
https://learn.microsoft.com/en-us/azure/expressroute/site-to-site-vpn-over-microsoft-peering
2.IPSec can also be done over Private peering, but you will need to use Virtual WAN:
https://learn.microsoft.com/en-us/azure/virtual-wan/vpn-over-expressroute
3.MACsec can be used with ExpressRoute Direct and you can also use IPSec in addition to MACSec with ExpressRoute direct:
https://learn.microsoft.com/en-us/azure/expressroute/expressroute-about-encryption
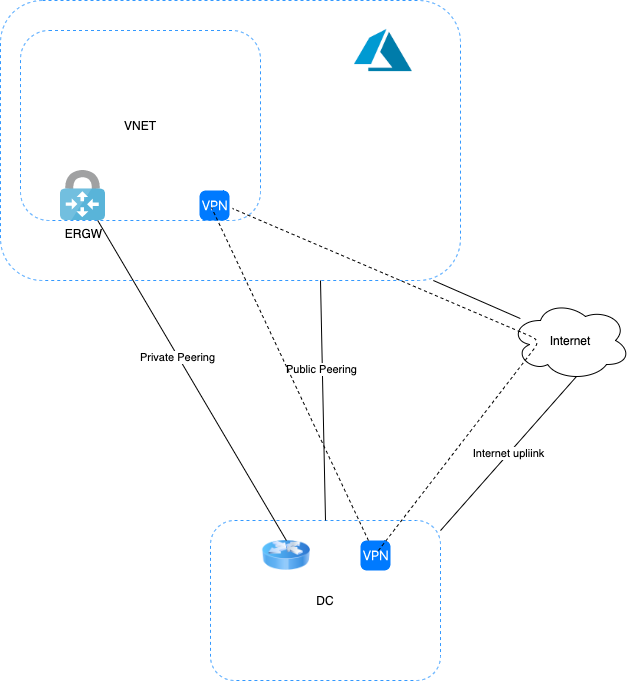
If you use IPSec VPN over MS peering, it is specifically a S2S VPN between on-premise VPN device and Azure VNET's VPN gateway. So by this way you can have S2S VPN established over MS peering (in normal scenarios S2S VPN established over Internet). It is meant for communication with VNET resources only.
Using this method, the traffic for PaaS services from on-premises will not be encrypted but it will traverse as normal traffic over MS peering.
If you use IPSec over Private peering for Virtual WAN, it provides encrypted transit between the on-premises networks and Azure virtual networks over ExpressRoute, without going over the public internet or using public IP addresses.
On the other hand, MacSec with ER Direct provides point to point encryption between your device and Microsoft device. So in this case all traffic such as, BGP control traffic, Private peering traffic , MS peering traffic - which includes PaaS service traffic as well, gets encrypted using MacSec keys.
Since you already have an ExpressRoute gateway with private peering, you can go for IPSec VPN over MS peering (if interested).
Configuring a site-to-site VPN over ExpressRoute helps you secure encrypted connectivity between your on-premises network and your Azure virtual networks (VNets) over an ExpressRoute private connection. You can use Microsoft peering to establish a site-to-site IPsec/IKE VPN tunnel between your selected on-premises networks and Azure VNets. Configuring a secure tunnel over ExpressRoute allows for data exchange with confidentiality, anti-replay, authenticity, and integrity.
To configure a site-to-site VPN connection over ExpressRoute, you must leverage ExpressRoute Microsoft peering. VPN tunnels over Microsoft peering can be terminated either using VPN gateway, or using an appropriate Network Virtual Appliance (NVA) available through Azure Marketplace. You can exchange routes statically or dynamically over the encrypted tunnels without exposing the route exchange to the underlying Microsoft peering.
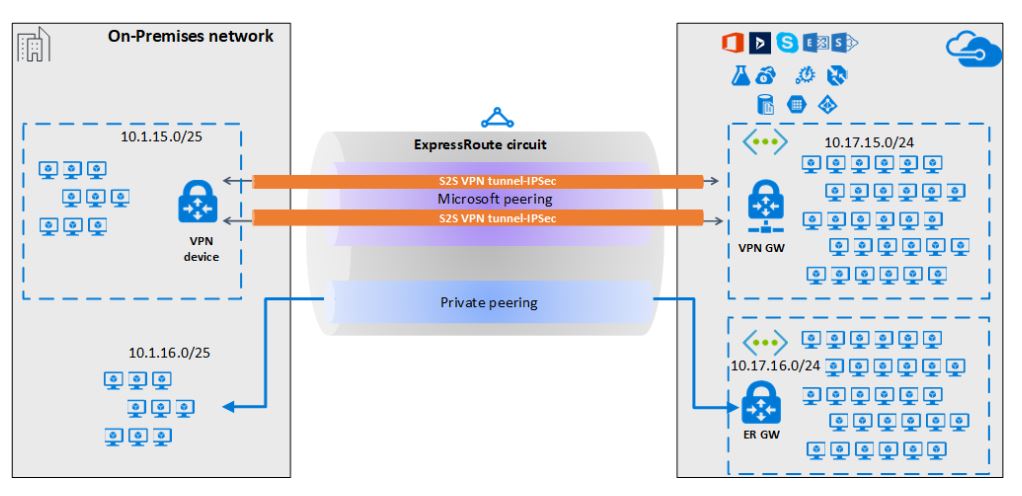
Co-existence of S2S and ExpressRoute helps you in use the Site-to-Site VPN as a secure failover path for ExpressRoute, or use Site-to-Site VPNs to connect to sites that are not connected through ExpressRoute.
Please refer : https://learn.microsoft.com/en-us/azure/expressroute/expressroute-howto-coexist-resource-manager
Hope this helps!
Kindly let us know if the above helps or you need further assistance on this issue.
Please don’t forget to "Accept the answer" wherever the information provided helps you, this can be beneficial to other community members.