Hi @Lars Wurm
Can you please confirm if you have followed up all the steps mentioned here
In the third step, it is mentioned as :
Enable the "Get" secret permission on this policy. Do not configure the "authorized application" or applicationId settings, as this is not compatible with a managed identity.
Yes, you need to add access policy with the Get permission for the Object ID that is generated when you have enabled the system assigned Identity.
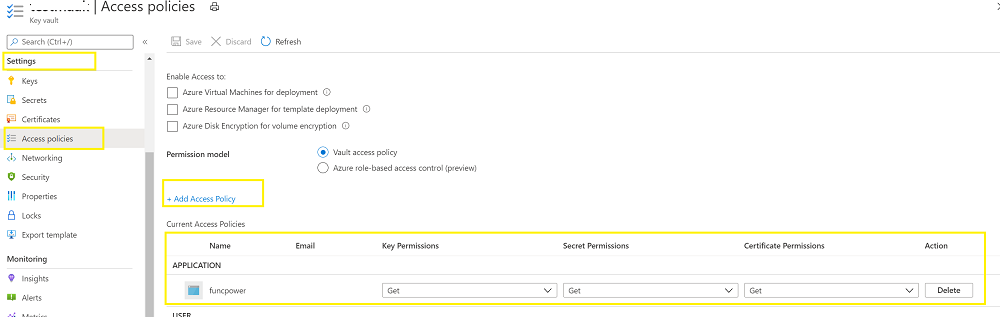
Once you have added the permission you can create a new application setting and define the value as @Microsoft.KeyVault(SecretUri)
Example : "@Microsoft.KeyVault(SecretUri=https://myvault.vault.azure.net/secrets/mysecret/ec96f02080254f109c51a1f14cdb1931")
You can see the green tick mark in the source column for your specified name as below and this confirmed that the setup is correct

I have used below powershell code to get the value of the secret in my function code:
using namespace System.Net
# Input bindings are passed in via param block.
param($Request, $TriggerMetadata)
# Write to the Azure Functions log stream.
Write-Host "PowerShell HTTP trigger function processed a request."
$result = ls env:APPSETTING_password
$pass = $result.value
# Associate values to output bindings by calling 'Push-OutputBinding'.
Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{
StatusCode = [HttpStatusCode]::OK
Body = $pass
})
You can customize the above code according to your requirement. I hope the above steps help you to resolve the issue. If not please share the steps and code that you are using.
Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community looking for help on similar topics.
