Hi,
We have an Asp.net web application hosted in an Azure App Service with multiple instances. SessionState is stored "InProc". Load balancing between instances is managed by the built-in ARR module.
For business reasons, some of our partners use this application inside an iFrame, which is comparable as cross-site scenario.
Since last Chrome version we encountered some problems because Chrome, by default in cross-site scenarios, refused cookies that don't have "SameSite=none" and "secure" attributes.
The "ARRAffinity" cookie emited by ARR module does not have these attributes.
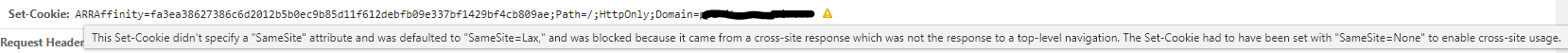
I found a workaround for all other cookies emited by the application that were in the same situation by using <rewrite> section in web.config but it seems ARRAfinity is not affected by my rules, meaning cookie is probably managed later in the request lifecyle, by the load balancer.
Is there a way to configure/force this cookie to have SameSite=none and Secure attributes ?
Thanks for help
