Set up a force password reset flow in Azure Active Directory B2C
Before you begin, use the Choose a policy type selector at the top of this page to choose the type of policy you’re setting up. Azure Active Directory B2C offers two methods to define how users interact with your applications: through predefined user flows or through fully configurable custom policies. The steps required in this article are different for each method.
Overview
As an administrator, you can reset a user's password if the user forgets their password. Or you would like to force them to reset the password. In this article, you'll learn how to force a password reset in these scenarios.
When an administrator resets a user's password via the Azure portal, the value of the forceChangePasswordNextSignIn attribute is set to true. The sign-in and sign-up journey checks the value of this attribute. After the user completes the sign-in, if the attribute is set to true, the user must reset their password. Then the value of the attribute is set to back false.
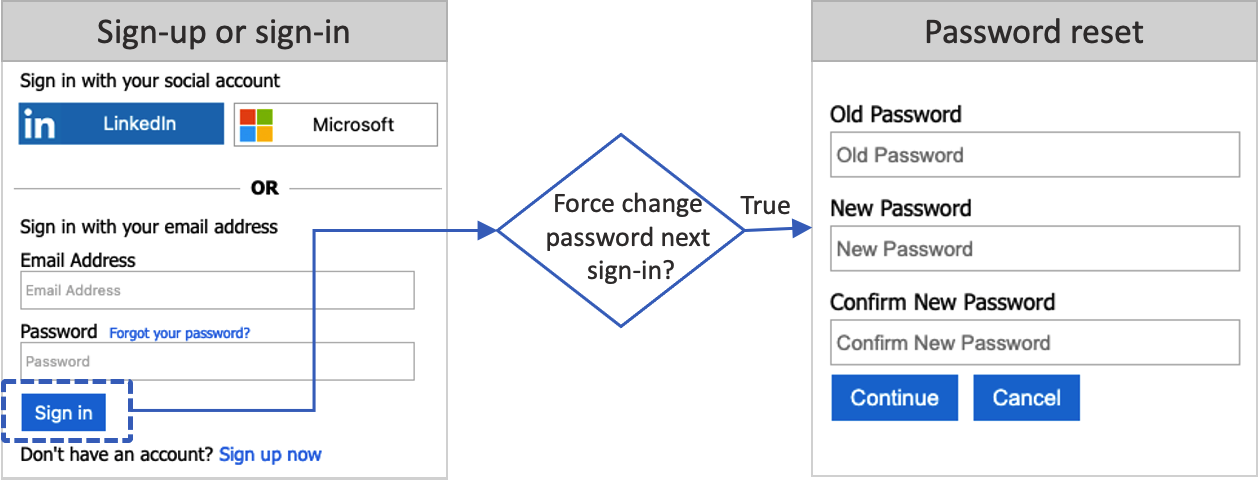
The password reset flow is applicable to local accounts in Azure AD B2C that use an email address or username with a password for sign-in.
Prerequisites
- Create a user flow so users can sign up and sign in to your application.
- Register a web application.
- Complete the steps in Get started with custom policies in Active Directory B2C. This tutorial guides you how to update custom policy files to use your Azure AD B2C tenant configuration.
- Register a web application.
Configure your user flow
To enable the Forced password reset setting in a sign-up or sign-in user flow:
- Sign in to the Azure portal.
- If you have access to multiple tenants, select the Settings icon in the top menu to switch to your Azure AD B2C tenant from the Directories + subscriptions menu.
- In the Azure portal, search for and select Azure AD B2C.
- Select User flows.
- Select the sign-up and sign-in, or sign-in user flow (of type Recommended) that you want to customize.
- In the left menu under Settings, select Properties.
- Under Password configuration, select Forced password reset.
- Select Save.
Test the user flow
- Sign in to the Azure portal as a user administrator or a password administrator. For more information about the available roles, see Assigning administrator roles in Microsoft Entra ID.
- If you have access to multiple tenants, select the Settings icon in the top menu to switch to your Azure AD B2C tenant from the Directories + subscriptions menu.
- In the Azure portal, search for and select Azure AD B2C.
- Select Users. Search for and select the user you'll use to test the password reset, and then select Reset Password.
- In the Azure portal, search for and select Azure AD B2C.
- Select User flows.
- Select a sign-up or sign-in user flow (of type Recommended) that you want to test.
- Select Run user flow.
- For Application, select the web application named webapp1 that you previously registered. The Reply URL should show
https://jwt.ms. - Select Run user flow.
- Sign in with the user account for which you reset the password.
- You now must change the password for the user. Change the password and select Continue. The token is returned to
https://jwt.msand should be displayed to you.
Configure your custom policy
Get the example of the force password reset policy on GitHub. In each file, replace the string yourtenant with the name of your Azure AD B2C tenant. For example, if the name of your B2C tenant is contosob2c, all instances of yourtenant.onmicrosoft.com become contosob2c.onmicrosoft.com.
Upload and test the policy
- Sign in to the Azure portal.
- If you have access to multiple tenants, select the Settings icon in the top menu to switch to your Azure AD B2C tenant from the Directories + subscriptions menu.
- Choose All services in the top-left corner of the Azure portal, and then search for and select Azure AD B2C.
- Select Identity Experience Framework.
- In Custom Policies, select Upload Policy.
- Select the TrustFrameworkExtensionsCustomForcePasswordReset.xml file.
- Select Upload.
- Repeat steps 6 through 8 for the relying party file TrustFrameworkExtensionsCustomForcePasswordReset.xml.
Run the policy
- Open the policy that you uploaded B2C_1A_TrustFrameworkExtensions_custom_ForcePasswordReset.
- For Application, select the application that you registered earlier. To see the token, the Reply URL should show
https://jwt.ms. - Select Run now.
- Sign in with the user account for which you reset the password.
- You now must change the password for the user. Change the password and select Continue. The token is returned to
https://jwt.msand should be displayed to you.
Force password reset on next login
To force reset the password on next login, update the account password profile using MS Graph Update user operation. To do this, you need to assign your Microsoft Graph application the User administrator role. Follow the steps in Grant user administrator role to assign your Microsoft Graph application a User administrator role.
The following example updates the password profile forceChangePasswordNextSignIn attribute to true, which forces the user to reset the password on next login.
PATCH https://graph.microsoft.com/v1.0/users/<user-object-ID>
Content-type: application/json
{
"passwordProfile": {
"forceChangePasswordNextSignIn": true
}
}
Once the account password profile has been set, you must also configure force password reset flow, as described in this article.
Force a password reset after 90 days
As an administrator, you can set a user's password expiration to 90 days, using MS Graph. After 90 days, the value of forceChangePasswordNextSignIn attribute is automatically set to true. To force a password reset after 90 days, remove the DisablePasswordExpiration value from the user's profile Password policy attribute.
The following example updates the password policy to None, which forces a password reset after 90 days:
PATCH https://graph.microsoft.com/v1.0/users/<user-object-ID>
Content-type: application/json
{
"passwordPolicies": "None"
}
If you disabled the strong password complexity, update the password policy to DisableStrongPassword:
Note
After the user resets their password, the passwordPolicies will be changed back to DisablePasswordExpiration
PATCH https://graph.microsoft.com/v1.0/users/<user-object-ID>
Content-type: application/json
{
"passwordPolicies": "DisableStrongPassword"
}
Once a password expiration policy has been set, you must also configure force password reset flow, as described in this article.
Password expiry duration
By default, the password is set not to expire. However, the value is configurable by using the Update-MgDomain cmdlet from the Microsoft Graph PowerShell module. This command updates the tenant so that all users' passwords expire after a number of days you configure. For example:
Import-Module Microsoft.Graph.Identity.DirectoryManagement
Connect-MgGraph -Scopes 'Domain.ReadWrite.All'
$domainId = "contoso.com"
$params = @{
passwordValidityPeriodInDays = 90
}
Update-MgDomain -DomainId $domainId -BodyParameter $params
passwordValidityPeriodInDaysis the length of time in days that a password remains valid before it must be changed.
Related content
Set up a self-service password reset.