Pull images from a container registry to an AKS cluster in a different Microsoft Entra tenant
In some cases, you might have your Azure AKS cluster in one Microsoft Entra tenant and your Azure container registry in a different tenant. This article walks through the steps to enable cross-tenant authentication using the AKS service principal credential to pull from the container registry.
Note
You can't attach the registry and authenticate using an AKS managed identity when the cluster and the container registry are in different tenants.
Scenario overview
Assumptions for this example:
- The AKS cluster is in Tenant A and the Azure container registry is in Tenant B.
- The AKS cluster is configured with service principal authentication in Tenant A. Learn more about how to create and use a service principal for your AKS cluster.
You need at least the Contributor role in the AKS cluster's subscription and the Owner role in the container registry's subscription.
You use the following steps to:
- Create a new multitenant app (service principal) in Tenant A.
- Provision the app in Tenant B.
- Configure the service principal to pull from the registry in Tenant B
- Update the AKS cluster in Tenant A to authenticate using the new service principal
Step-by-step instructions
Step 1: Create multitenant Microsoft Entra application
Sign in to the Azure portal in Tenant A.
Search for and select Microsoft Entra ID.
Under Manage, select App registrations > + New registration.
In Supported account types, select Accounts in any organizational directory.
In Redirect URI, enter https://www.microsoft.com.
Select Register.
On the Overview page, take note of the Application (client) ID. It will be used in Step 2 and Step 4.
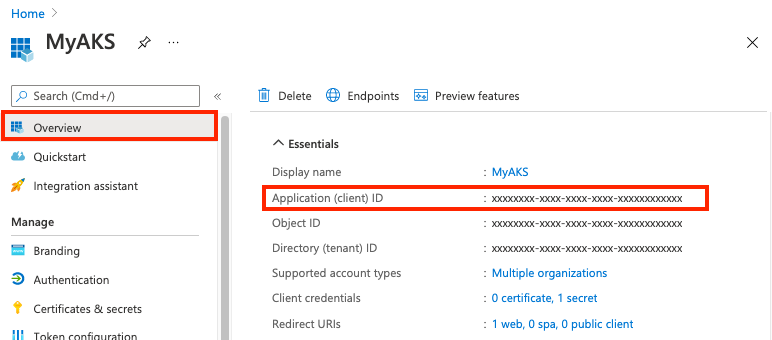
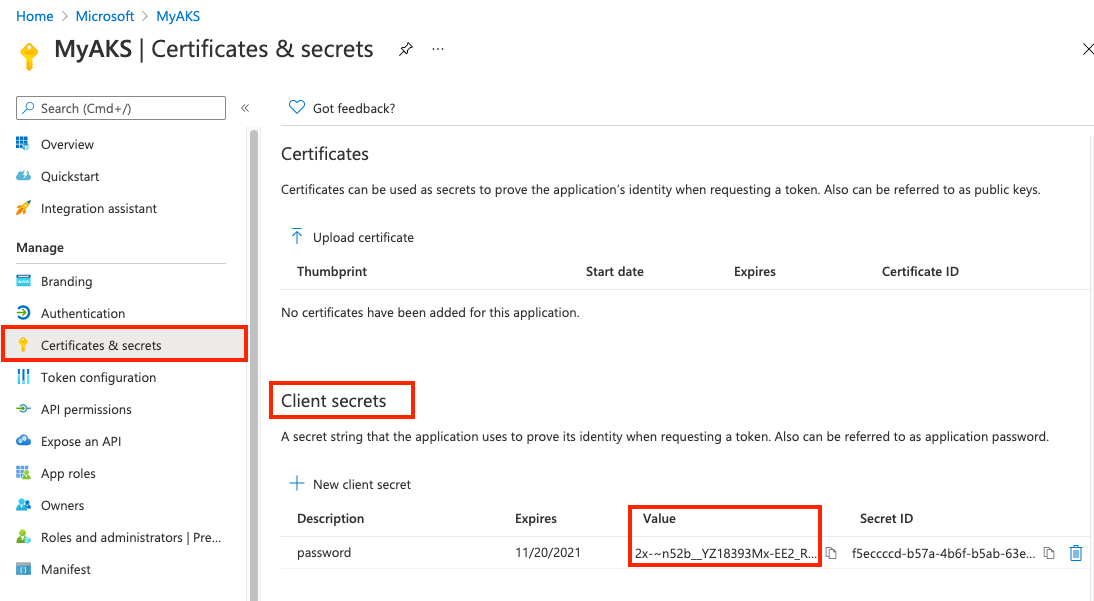
In Certificates & secrets, under Client secrets, select + New client secret.
Enter a Description such as Password and select Add.
In Client secrets, take note of the value of the client secret. You use it to update the AKS cluster's service principal in Step 4.
Step 2: Provision the service principal in the ACR tenant
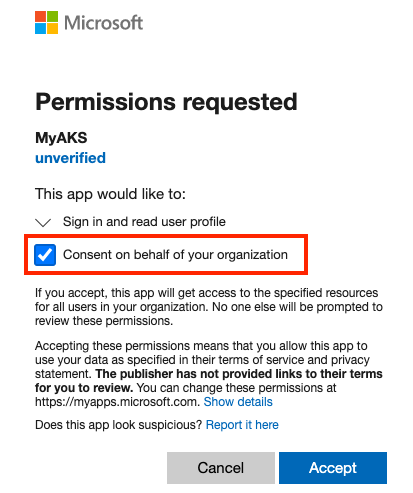
Open the following link using an admin account in Tenant B. Where indicated, insert the ID of Tenant B and the application ID (client ID) of the multitenant app.
https://login.microsoftonline.com/<Tenant B ID>/oauth2/authorize?client_id=<Multitenant application ID>&response_type=code&redirect_uri=<redirect url>Select Consent on behalf of your organization and then Accept.
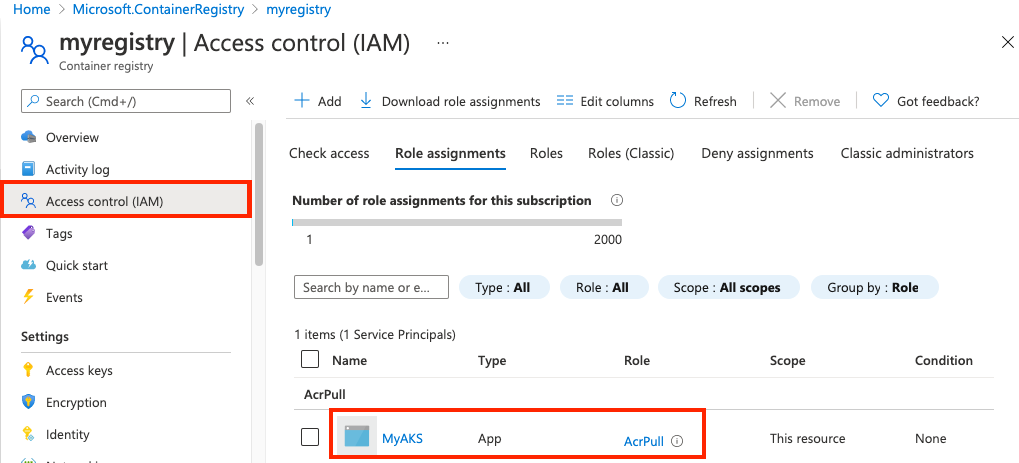
Step 3: Grant service principal permission to pull from registry
In Tenant B, assign the AcrPull role to the service principal, scoped to the target container registry. You can use the Azure portal or other tools to assign the role. For example steps using the Azure CLI, see Azure Container Registry authentication with service principals.
Step 4: Update AKS with the Microsoft Entra application secret
Use the multitenant application (client) ID and client secret collected in Step 1 to update the AKS service principal credential.
Updating the service principal can take several minutes.
Next steps
- Learn more Azure Container Registry authentication with service principals
- Learn more about image pull secrets in the Kubernetes documentation
- Learn about Application and service principal objects in Microsoft Entra ID
- Learn more about scenarios to authenticate with Azure Container Registry from a Kubernetes cluster