Enable and manage adaptive application controls
Microsoft Defender for Cloud's adaptive application controls provide a data-driven and intelligent automated solution that enhances your security by defining allowlists of known-safe applications for your machines. With this feature, organizations can manage collections of machines that routinely run the same processes. Using machine learning, Microsoft Defender for Cloud can analyze the applications running on your machines and create a list of known-safe software. These allowlists are based on your specific Azure workloads. You can further customize the recommendations using the instructions provided on this page.
On a group of machines
If Microsoft Defender for Cloud has identified groups of machines in your subscriptions that consistently run a similar set of applications, you'll be prompted with the following recommendation: Adaptive application controls for defining safe applications should be enabled on your machines.
Select the recommendation, or open the adaptive application controls page to view the list of suggested known-safe applications and groups of machines.
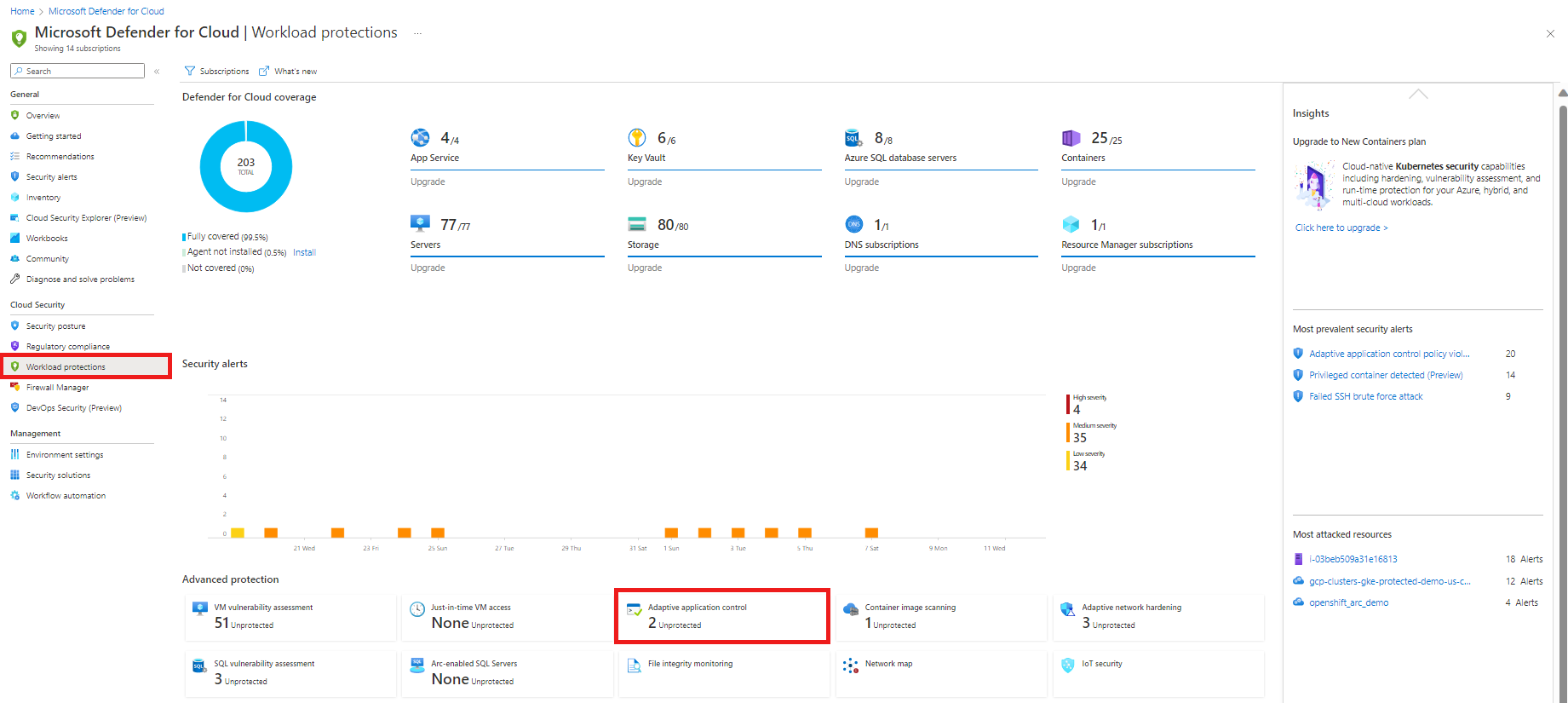
Open the Workload protections dashboard and from the advanced protection area, select Adaptive application controls.
The Adaptive application controls page opens with your VMs grouped into the following tabs:
Configured - Groups of machines that already have a defined allowlist of applications. For each group, the configured tab shows:
- the number of machines in the group
- recent alerts
Recommended - Groups of machines that consistently run the same applications, and don't have an allowlist configured. We recommend that you enable adaptive application controls for these groups.
Tip
If you see a group name with the prefix REVIEWGROUP, it contains machines with a partially consistent list of applications. Microsoft Defender for Cloud can't see a pattern but recommends reviewing this group to see whether you can manually define some adaptive application controls rules as described in Edit a group's adaptive application controls rule.
You can also move machines from this group to other groups as described in Move a machine from one group to another.
No recommendation - Machines without a defined allowlist of applications, and which don't support the feature. Your machine might be in this tab for the following reasons:
- It's missing a Log Analytics agent
- The Log Analytics agent isn't sending events
- It's a Windows machine with a pre-existing AppLocker policy enabled by either a GPO or a local security policy
- AppLocker isn't available (Windows Server Core installations)
Tip
Defender for Cloud needs at least two weeks of data to define the unique recommendations per group of machines. Machines that have recently been created, or which belong to subscriptions that were only recently protected by Microsoft Defender for Servers, will appear under the No recommendation tab.
Open the Recommended tab. The groups of machines with recommended allowlists appear.
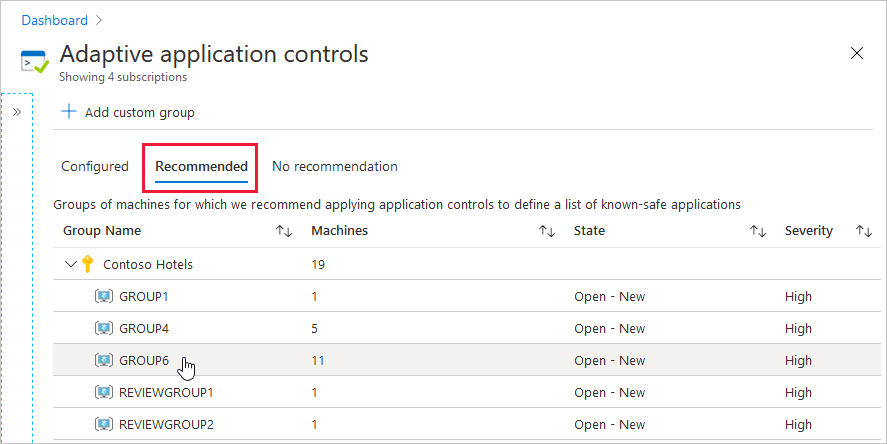
Select a group.
To configure your new rule, review the various sections of this Configure application control rules page and the contents, which will be unique to this specific group of machines:
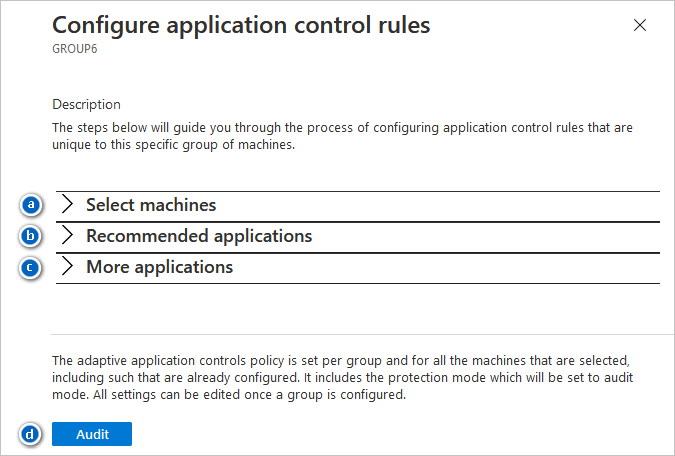
Select machines - By default, all machines in the identified group are selected. Unselect any to remove them from this rule.
Recommended applications - Review this list of applications that are common to the machines within this group, and recommended to be allowed to run.
More applications - Review this list of applications that are either seen less frequently on the machines within this group, or are known to be exploitable. A warning icon indicates that a specific application could be used by an attacker to bypass an application allowlist. We recommend that you carefully review these applications.
Tip
Both application lists include the option to restrict a specific application to certain users. Adopt the principle of least privilege whenever possible.
Applications are defined by their publishers. If an application doesn't have publisher information (it's unsigned), a path rule is created for the full path of the specific application.
To apply the rule, select Audit.
Edit a group's adaptive application controls rule
You might decide to edit the allowlist for a group of machines because of known changes in your organization.
To edit the rules for a group of machines:
Open the Workload protections dashboard and from the advanced protection area, select Adaptive application controls.
From the Configured tab, select the group with the rule you want to edit.
Review the various sections of the Configure application control rules page as described in On a group of machines.
Optionally, add one or more custom rules:
- Select Add rule.
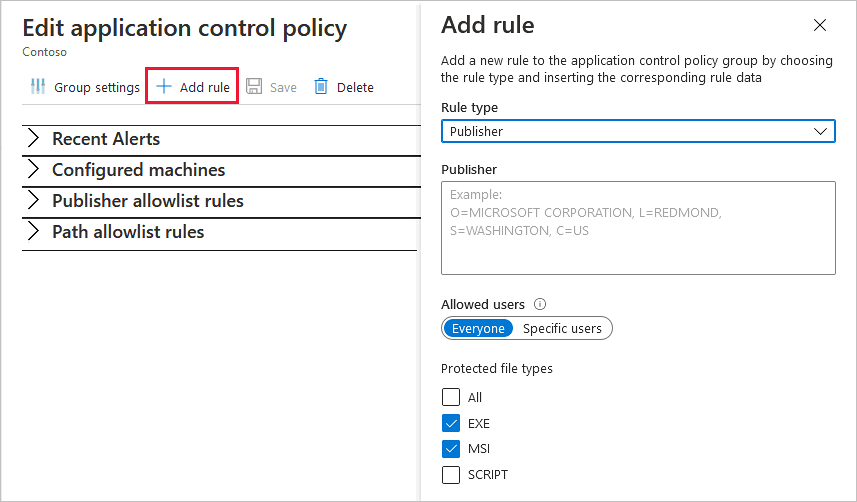
If you're defining a known safe path, change the Rule type to 'Path' and enter a single path. You can include wildcards in the path. The following screens show some examples of how to use wildcards.
Tip
Some scenarios for which wildcards in a path might be useful:
- Using a wildcard at the end of a path to allow all executables within this folder and sub-folders.
- Using a wildcard in the middle of a path to enable a known executable name with a changing folder name (for example, personal user folders containing a known executable, automatically generated folder names, etc).
Define the allowed users and protected file types.
When you've finished defining the rule, select Add.
To apply the changes, select Save.
Review and edit a group's settings
To view the details and settings of your group, select Group settings.
This pane shows the name of the group (which can be modified), the OS type, the location, and other relevant details.
Optionally, modify the group's name or file type protection modes.
Select Apply and Save.
Respond to the "Allowlist rules in your adaptive application control policy should be updated" recommendation
You'll see this recommendation when Defender for Cloud's machine learning identifies potentially legitimate behavior that hasn't previously been allowed. The recommendation suggests new rules for your existing definitions to reduce the number of false positive alerts.
To remediate the issues:
From the recommendations page, select the Allowlist rules in your adaptive application control policy should be updated recommendation to see groups with newly identified, potentially legitimate behavior.
Select the group with the rule you want to edit.
Review the various sections of the Configure application control rules page as described in On a group of machines.
To apply the changes, select Audit.
Audit alerts and violations
Open the Workload protections dashboard and from the advanced protection area, select Adaptive application controls.
To see groups with machines that have recent alerts, review the groups listed in the Configured tab.
To investigate further, select a group.
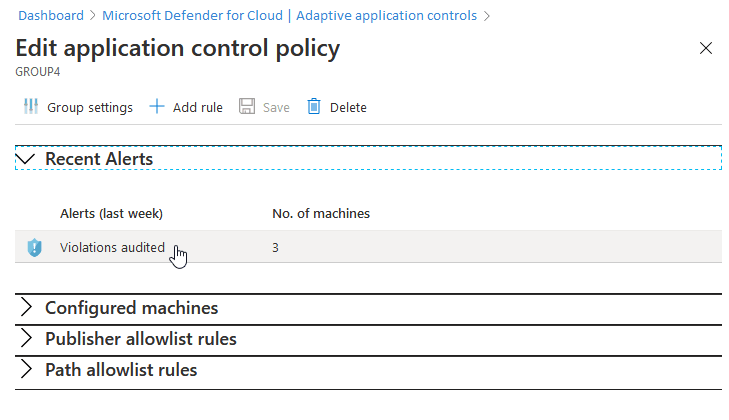
For further details, and the list of affected machines, select an alert.
The security alerts page shows more details of the alerts and provides a Take action link with recommendations of how to mitigate the threat.
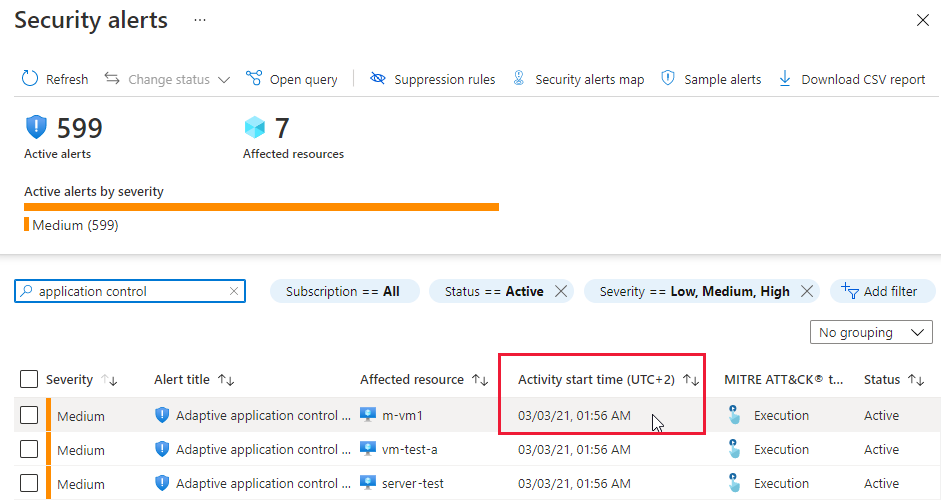
Note
Adaptive application controls calculates events once every twelve hours. The "activity start time" shown in the security alerts page is the time that adaptive application controls created the alert, not the time that the suspicious process was active.
Move a machine from one group to another
When you move a machine from one group to another, the application control policy applied to it changes to the settings of the group that you moved it to. You can also move a machine from a configured group to a non-configured group, which removes any application control rules that were applied to the machine.
Open the Workload protections dashboard and from the advanced protection area, select Adaptive application controls.
From the Adaptive application controls page, from the Configured tab, select the group containing the machine to be moved.
Open the list of Configured machines.
Open the machine's menu from three dots at the end of the row, and select Move. The Move machine to a different group pane opens.
Select the destination group, and select Move machine.
To save your changes, select Save.
Manage application controls via the REST API
To manage your adaptive application controls programmatically, use our REST API.
The relevant API documentation is available in the Adaptive application Controls section of Defender for Cloud's API docs.
Some of the functions available from the REST API include:
List retrieves all your group recommendations and provides a JSON with an object for each group.
Get retrieves the JSON with the full recommendation data (that is, list of machines, publisher/path rules, and so on).
Put configures your rule (use the JSON you retrieved with Get as the body for this request).
Important
The Put function expects fewer parameters than the JSON returned by the Get command contains.
Remove the following properties before using the JSON in the Put request: recommendationStatus, configurationStatus, issues, location, and sourceSystem.
Related content
On this page, you learned how to use adaptive application control in Microsoft Defender for Cloud to define allowlists of applications running on your Azure and non-Azure machines. To learn more about some other cloud workload protection features, see:
- Understanding just-in-time (JIT) VM access
- Securing your Azure Kubernetes clusters
- View common question about Adaptive application controls
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for