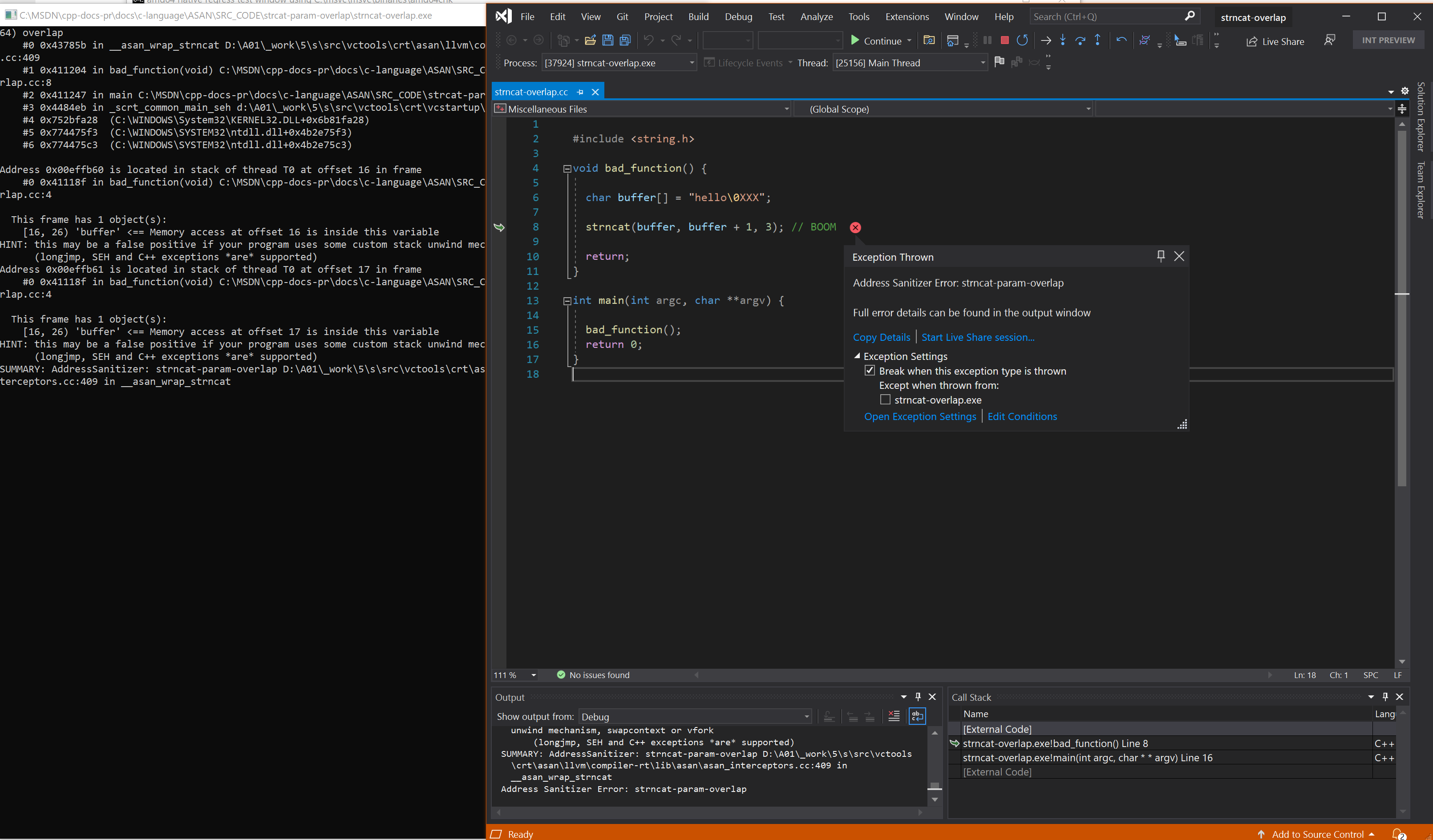
Error: strncat-param-overlap
Address Sanitizer Error: strncat-param-overlap
Code that moves memory in overlapping buffer can cause hard-to-diagnose errors.
Example
This example shows how AddressSanitizer can catch errors caused by overlapped parameters to CRT functions.
(Based on llvm-project/compiler-rt/test/asan/TestCases/strncat-overlap.cpp.)
// example1.cpp
// strncat-param-overlap error
#include <string.h>
void bad_function() {
char buffer[] = "hello\0XXX";
strncat(buffer, buffer + 1, 3); // BOOM
return;
}
int main(int argc, char **argv) {
bad_function();
return 0;
}
To build and test this example, run these commands in a Visual Studio 2019 version 16.9 or later developer command prompt:
cl example1.cpp /fsanitize=address /Zi
devenv /debugexe example1.exe
Resulting error
See also
AddressSanitizer overview
AddressSanitizer known issues
AddressSanitizer build and language reference
AddressSanitizer runtime reference
AddressSanitizer shadow bytes
AddressSanitizer cloud or distributed testing
AddressSanitizer debugger integration
AddressSanitizer error examples