Access policies in Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps access policies enable real-time monitoring and control over access to cloud apps based on user, location, device, and app. You can create access policies for any device, including devices that aren't Microsoft Entra hybrid join and not managed by Microsoft Intune, by rolling out client certificates to managed devices or using existing certificates, such as third-party MDM certificates. For example, you can deploy client certificates to managed devices and then block access from devices without a certificate.
Note
- Instead of allowing or blocking access completely, with session policies you can allow access while monitoring the session and/or limit specific session activities.
- There's no connection between a policy that you create for a host app and any related resource apps. For example, access policies that you create for Teams, Exchange, or Gmail, are not connected to Sharepoint, OneDrive, or Google Drive. If you need a policy for the resource app in addition to the host app, create a separate policy.
Prerequisites to using access policies
- Microsoft Entra ID P1 license, or the license required by your identity provider (IdP) solution
- The relevant apps should be deployed with Conditional Access App Control
- Make sure you have configured your IdP solution to work with Defender for Cloud Apps, as follows:
- For Microsoft Entra Conditional Access, see Configure integration with Microsoft Entra ID
- For other IdP solutions, see Configure integration with other IdP solutions
Create a Defender for Cloud Apps access policy
To create a new access policy, follow this procedure:
In the Microsoft Defender Portal, under Cloud Apps, go to Policies -> Policy management. Then select the Conditional access tab.
Select Create policy and then select Access policy.
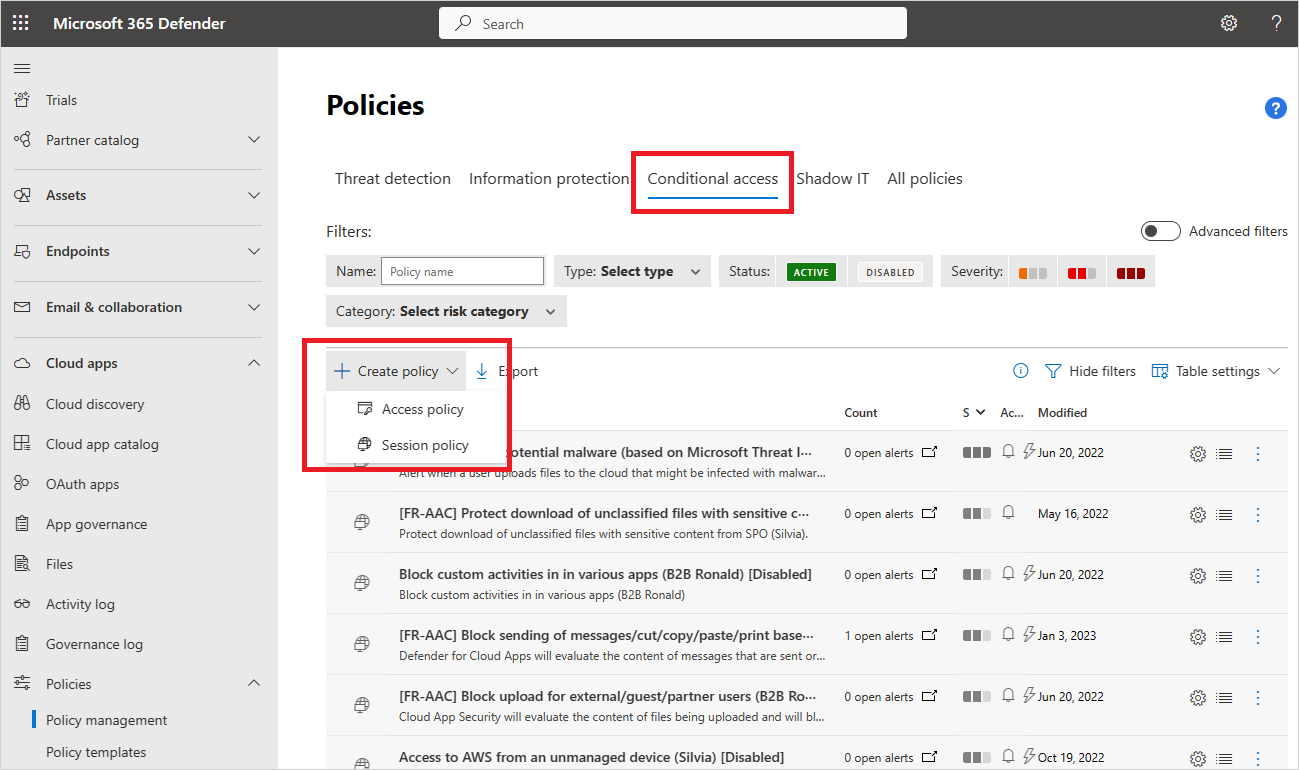
In the Access policy window, assign a name for your policy, such as Block access from unmanaged devices.
In the Activities matching all of the following section, select additional activity filters to apply to the policy. Filters include the following options:
Device tags: Use this filter to identify unmanaged devices.
Location: Use this filter to identify unknown (and therefore risky) locations.
IP address: Use this filter to filter per IP address or use previously assigned IP address tags.
User agent tag: Use this filter to enable the heuristic to identify mobile and desktop apps. This filter can be set to equal or not equal. The values should be tested against your mobile and desktop apps for each cloud app.
Under Actions, select one of the following options:
Test: Set this action to allow access according to the policy filters you set explicitly.
Block: Set this action to block access according to the policy filters you set explicitly.
You can Create an alert for each matching event with the policy's severity, set an alert limit, and select whether you want the alert as an email, a text message, or both.
Related videos
Next steps
See also
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for