Events
9 Apr, 15 - 10 Apr, 12
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Before combined registration, users registered authentication methods for Microsoft Entra multifactor authentication and self-service password reset (SSPR) separately. Users were confused that similar methods were used for Microsoft Entra multifactor authentication and SSPR but they had to register for both features. Now, with combined registration, users can register once and get the benefits of both Microsoft Entra multifactor authentication and SSPR.
To help you understand the functionality and effects of the new experience, see the Combined security information registration concepts.
To secure when and how users register for Microsoft Entra multifactor authentication and self-service password reset, you can use user actions in Conditional Access policy. This functionality may be enabled in organizations that want users to register for Microsoft Entra multifactor authentication and SSPR from a central location, such as a trusted network location during HR onboarding.
Note
This policy applies only when a user accesses a combined registration page. This policy doesn't enforce MFA enrollment when a user accesses other applications.
You can create an MFA registration policy by using Microsoft Entra ID Protection - Configure MFA Policy.
For more information about creating trusted locations in Conditional Access, see What is the location condition in Microsoft Entra Conditional Access?.
Complete the following steps to create a policy that applies to all selected users that attempt to register using the combined registration experience, and requires users connected on a non-trusted network to either perform MFA or sign in using a Temporary Access Pass (TAP) to register for MFA or reset their password using SSPR:
Sign in to the Microsoft Entra admin center as at least an Conditional Access Administrator.
Browse to Protection > Conditional Access.
Select + New policy.
Enter a name for this policy, such as Combined Security Info Registration on Trusted Networks.
Under Assignments, select Users. Choose the users and groups you want this policy to apply to.
Warning
Users must be enabled for combined registration.
Under Cloud apps or actions, select User actions. Check Register security information, then select Done.
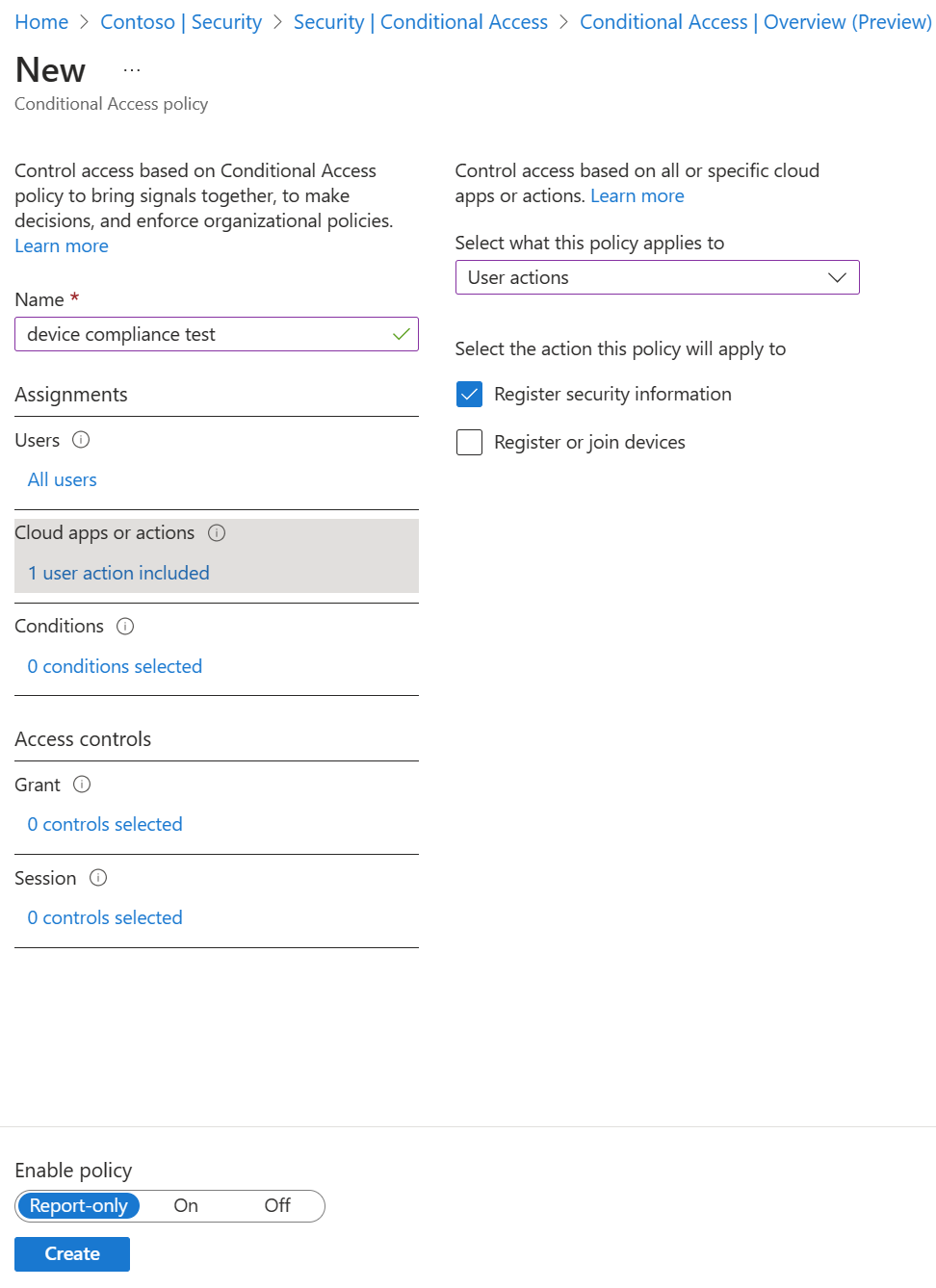
Under Conditions > Locations, configure the following options:
Under Access controls > Grant, choose Require multifactor authentication, then Select.
Set Enable policy to On.
To finalize the policy, select Create.
If you need help, see troubleshoot combined security info registration or learn What is the location condition in Microsoft Entra Conditional Access?
Review how you can enable self-service password reset and enable Microsoft Entra multifactor authentication in your tenant.
If needed, learn how to force users to re-register authentication methods.
Events
9 Apr, 15 - 10 Apr, 12
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowTraining
Module
Register apps using Microsoft Entra ID - Training
In this module, we explore the process of creating an app registration in Microsoft Entra ID. Then explore the settings and configuration options. You create a single page app, register multitenant app, and other options. As part of this process, we dig into granting user access to apps and configure how and when they can use the app and its data.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.