Microsoft Entra pass-through authentication: Technical deep dive
This article is an overview of how Microsoft Entra pass-through authentication works. For deep technical and security information, see the Security deep dive article.
How does Microsoft Entra pass-through authentication work?
Note
As a pre-requisite for Pass-through Authentication to work, users need to be provisioned into Microsoft Entra ID from on-premises Active Directory using Microsoft Entra Connect. Pass-through Authentication does not apply to cloud-only users.
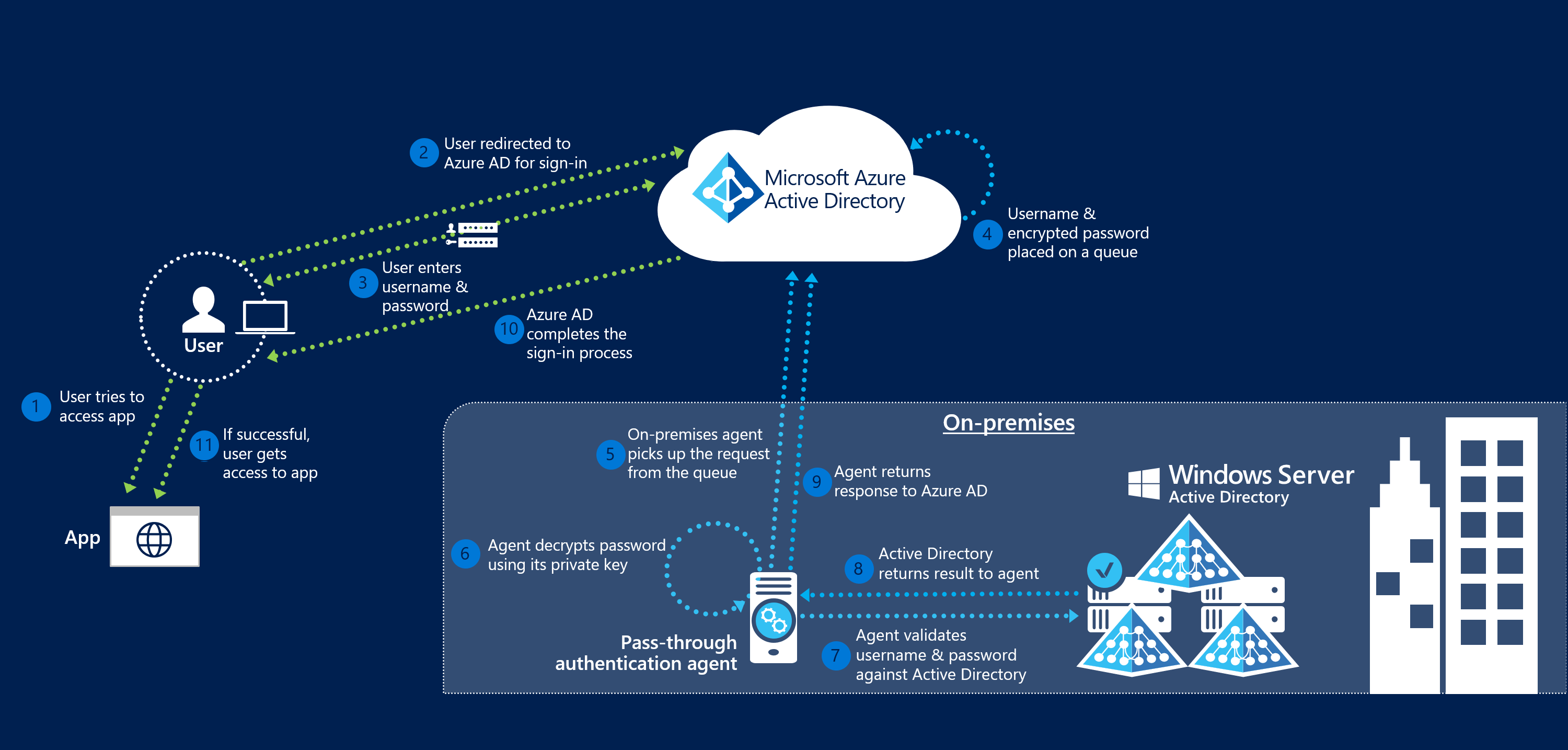
When a user tries to sign in to an application secured by Microsoft Entra ID, and if Pass-through Authentication is enabled on the tenant, the following steps occur:
- The user tries to access an application, for example, Outlook Web App.
- If the user is not already signed in, the user is redirected to the Microsoft Entra ID User Sign-in page.
- The user enters their username into the Microsoft Entra sign-in page, and then selects the Next button.
- The user enters their password into the Microsoft Entra sign-in page, and then selects the Sign in button.
- Microsoft Entra ID, on receiving the request to sign in, places the username and password (encrypted by using the public key of the Authentication Agents) in a queue.
- An on-premises Authentication Agent retrieves the username and encrypted password from the queue. Note that the Agent doesn't frequently poll for requests from the queue, but retrieves requests over a pre-established persistent connection.
- The agent decrypts the password by using its private key.
- The agent validates the username and password against Active Directory by using standard Windows APIs, which is a similar mechanism to what Active Directory Federation Services (AD FS) uses. The username can be either the on-premises default username, usually
userPrincipalName, or another attribute configured in Microsoft Entra Connect (known asAlternate ID). - The on-premises Active Directory domain controller (DC) evaluates the request and returns the appropriate response (success, failure, password expired, or user locked out) to the agent.
- The Authentication Agent, in turn, returns this response back to Microsoft Entra ID.
- Microsoft Entra ID evaluates the response and responds to the user as appropriate. For example, Microsoft Entra ID either signs the user in immediately or requests for Microsoft Entra multifactor authentication.
- If the user sign-in is successful, the user can access the application.
The following diagram illustrates all the components and the steps involved:
Next steps
- Current limitations: Learn which scenarios are supported and which ones are not.
- Quick Start: Get up and running on Microsoft Entra pass-through authentication.
- Migrate your apps to Microsoft Entra ID: Resources to help you migrate application access and authentication to Microsoft Entra ID.
- Smart Lockout: Configure the Smart Lockout capability on your tenant to protect user accounts.
- Frequently Asked Questions: Find answers to frequently asked questions.
- Troubleshoot: Learn how to resolve common problems with the Pass-through Authentication feature.
- Security Deep Dive: Get deep technical information on the Pass-through Authentication feature.
- Microsoft Entra hybrid join: Configure Microsoft Entra hybrid join capability on your tenant for SSO across your cloud and on-premises resources.
- Microsoft Entra seamless SSO: Learn more about this complementary feature.
- UserVoice: Use the Microsoft Entra Forum to file new feature requests.