I got my WIF working with GCP -> Azure using help from a Microsoft Engineer per the post made by me here: https://learn.microsoft.com/en-us/answers/questions/2235923/wif-still-requires-client-secret?page=1&orderby=Helpful&comment=answer-2017150&translated=false
But my problem now is moving the process from instead a development GCP VM to the Composer (Airflow)'s worker VM. I have this error:
{'error': 'invalid_client', 'error_description': "AADSTS700213: No matching federated identity record found for presented assertion subject '103432211958501047059'. Check your federated identity credential Subject, Audience and Issuer against the presented assertion. https://learn.microsoft.com/entra/workload-id/workload-identity-federation Trace ID: b74d6477-82ea-4764-8f92-0f9435ed4000 Correlation ID: f27b9148-efae-44e2-881b-7d88cff88df1 Timestamp: 2025-04-03 22:48:10Z", 'error_codes': [700213], 'timestamp': '2025-04-03 22:48:10Z', 'trace_id': 'b74d6477-82ea-4764-8f92-0f9435ed4000', 'correlation_id': 'f27b9148-efae-44e2-881b-7d88cff88df1', 'error_uri': 'https://login.microsoftonline.com/error?code=700213'}
I have specifically double-checked from the GCP token the following:
- service account, which is "******@developer.gserviceaccount.com",
- issuer (iss: "https://accounts.google.com"),
- sub, or azp ("103432211958501047059"),
- aud or audience ("//iam.googleapis.com/projects/3xxxxxxxxxx9/locations/global/workloadIdentityPools/azure-ad-pool-1/providers/azure-ad-provider-1)
And I have created a new Credential for the same app - so the azure app registration has 2 credentials, 1 for previous development VM which WORKED as discussed in the Q&A link above, 1 for the new airflow VM:
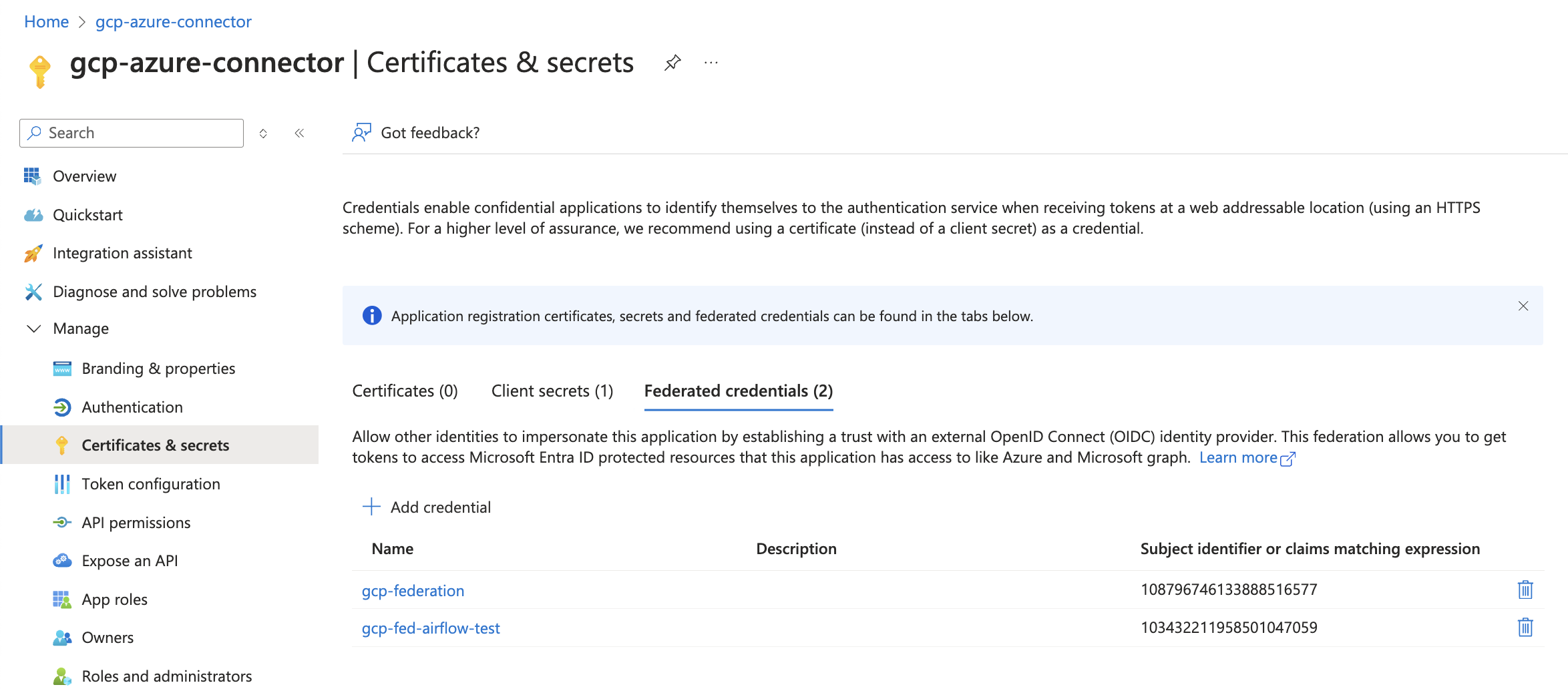
And I have permissioned properly the service account with IAM role, just like I did with the previous development GCP VM:
gcloud iam service-accounts add-iam-policy-binding \
******@developer.gserviceaccount.com \
--member="principal://iam.googleapis.com/projects/3xxxxxxxxxx9/locations/global/workloadIdentityPools/azure-ad-pool-1/subject/103432211958501047059" \
--role="roles/iam.workloadIdentityUser" \
--project=azure-federation-playground
Yet the error is saying as if I didn't create a working new Credential, or Azure is not recognizing the service account to auth against. I'm using the same script that your engineer provided me in the last comment of that Q&A link that I accepted as answer, so I don't think the script is the problem there, but just in case:
import datetime
from airflow import models
from airflow.operators.bash import BashOperator
from airflow.operators.python import PythonOperator
import requests
import logging
default_dag_args = {
"start_date": datetime.datetime(2025, 4, 1),
'retries': 3,
'retry_delay': datetime.timedelta(minutes=5),
}
with models.DAG(
"federation_auth_testing",
schedule_interval=datetime.timedelta(days=1),
default_args=default_dag_args,
max_active_runs=1,
catchup=False,
dagrun_timeout=datetime.timedelta(minutes=5),
) as dag:
def gcp_azure_list_subs():
# Get GCP token
metadata_url = "http://metadata.google.internal/computeMetadata/v1/instance/service-accounts/default/identity"
audience = "//iam.googleapis.com/projects/3xxxxxxxxxx9/locations/global/workloadIdentityPools/azure-ad-pool-1/providers/azure-ad-provider-1"
gcp_response = requests.get(f"{metadata_url}?audience={audience}", headers={"Metadata-Flavor": "Google"})
if gcp_response.status_code != 200:
logging.exception(f"Error getting GCP token: {gcp_response.text}")
exit(1)
gcp_token = gcp_response.text
logging.exception(f"DEBUG GCP TOKEN: {gcp_token}")
# Exchange GCP token for Azure token
azure_token_url = "https://login.microsoftonline.com/9b3d5632-d903-43e8-8e6f-3ef7d5079cab/oauth2/v2.0/token"
azure_client_id = "