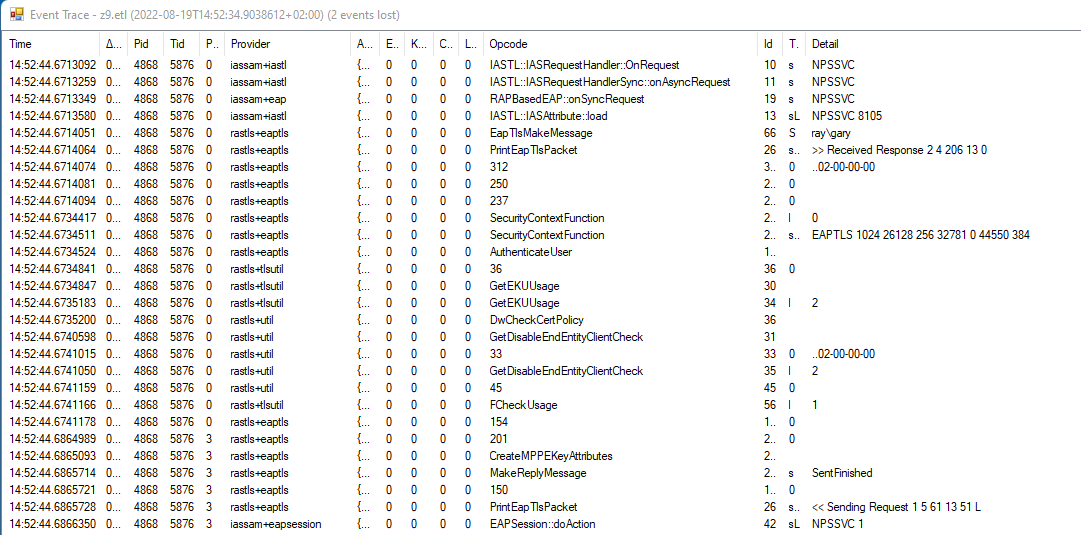
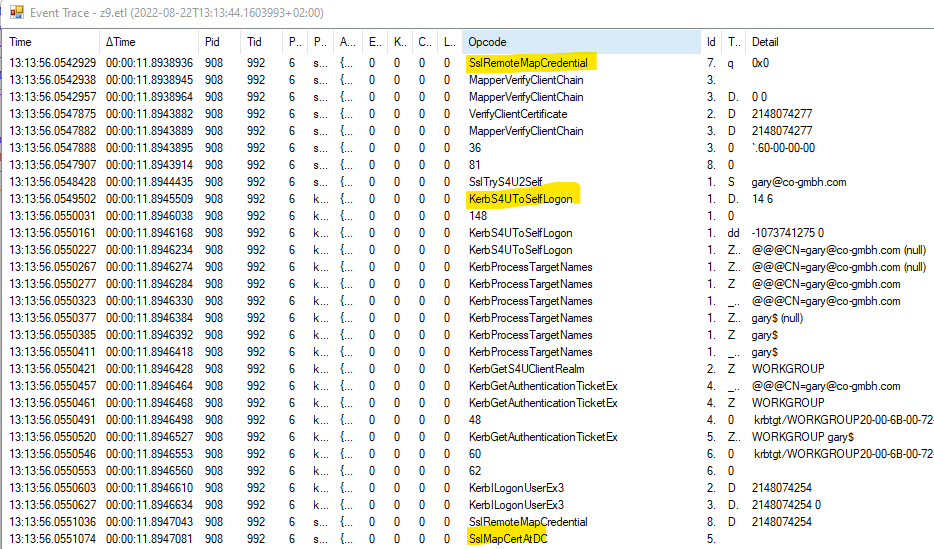
Hello @James Edmonds
Thank you for your heads up!
Here are my 2 cents about this case scenario described previously...
-For instance, A mismatch error perhaps does not make any sense when using certificate but I am wondering if you check the service provider on the registry so , you can double-check if there an active TLS 1.0 or TLS 1.1 when it has to be TLS 2.0.
- Furthermore, Try to compare cipher suites from a working computer as well as a non-working one by running this on PowerShell terminal:
***PS C:\Windows\system32> *Get-TlsCipherSuite | Format-Table -Property CipherSuite, Name****
**CipherSuite Name
4866 TLS_AES_256_GCM_SHA384
4865 TLS_AES_128_GCM_SHA256
0 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
49195 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
49200 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
49199 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
159 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
158 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
0 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
49187 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
49192 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
49191 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
49162 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
49161 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
49172 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
49171 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
157 TLS_RSA_WITH_AES_256_GCM_SHA384
156 TLS_RSA_WITH_AES_128_GCM_SHA256
61 TLS_RSA_WITH_AES_256_CBC_SHA256
60 TLS_RSA_WITH_AES_128_CBC_SHA256
53 TLS_RSA_WITH_AES_256_CBC_SHA
47 TLS_RSA_WITH_AES_128_CBC_SHA
10 TLS_RSA_WITH_3DES_EDE_CBC_SHA
59 TLS_RSA_WITH_NULL_SHA256
2 TLS_RSA_WITH_NULL_SHA
176 TLS_PSK_WITH_NULL_SHA256**
PS C:\Windows\system32>
-Have you checked if the Self-signed certificate or any other CA certificate used for this is on the Trusted Certificate Authority field on the PC's?
-Review the Certificate settings and compare it from a working machine by issuing this command below:
****PS C:\Windows\system32> Get-ChildItem -Path "Cert:\CurrentUser\My"
PSParentPath: Microsoft.PowerShell.Security\Certificate::CurrentUser\My
Thumbprint Subject
400D2B5390C57B1959EE2D1A405587263F943525 CN=P2SChildCert
3B0AFD934104CB339854AE09B7EE7948CACB512C CN=P2SRootCert
B2D4ABB99794207268853A8B29B741C2C85926E2 CN=P2SChildCert
EF3DBCB8BD97AC7B4515B88A24DC1788E7BD39ED CN=P2SRootCert01
CA5A5CA55E45A7A093CDE6272E62B9998F658BBF CN=P2SRootCert
PS C:\Windows\system32>****
-Check the server name or FQDN/CN used for this set up...
If you have any chance to share the logs for this issue will be appreciate it : )
I hope this can give you more details on where to take a look.
Cheers,
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.