What's new in Microsoft Defender for IoT?
This article describes features available in Microsoft Defender for IoT, across both OT and Enterprise IoT networks, both on-premises and in the Azure portal, and for versions released in the last nine months.
Features released earlier than nine months ago are described in the What's new archive for Microsoft Defender for IoT for organizations. For more information specific to OT monitoring software versions, see OT monitoring software release notes.
Note
Noted features listed below are in PREVIEW. The Azure Preview Supplemental Terms include other legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Note
This article discusses Microsoft Defender for IoT in the Azure portal.
If you're a Microsoft Defender customer looking for a unified IT/OT experience, see the documentation for Microsoft Defender for IoT in the Microsoft Defender portal (Preview) documentation.
Learn more about the Defender for IoT management portals.
October 2024
| Service area | Updates |
|---|---|
| OT networks | - Add wildcards to allowlist domain names - Added protocol - New sensor setting type Public addresses - Improved OT sensor onboarding |
Add wildcards allowlist domain names
When adding domain names to the FQDN allowlist use the * wildcard to include all sub-domains. For more information, see allow internet connections on an OT network.
Added protocol
We now support the OCPI protocol. See the updated protocol list.
New sensor setting type Public addresses
We're adding the Public addresses type to the sensor settings, that allows you to exclude public IP addresses that might have been used for internal use and shouldn't be tracked. For more information, see add sensor settings.
Improved OT sensor onboarding
If there are connection problems, during sensor onboarding, between the OT sensor and the Azure portal at the configuration stage, the process can't be completed until the connection problem is solved.
We now support completing the configuration process without the need to solve the communication problem, allowing you to continue the onboarding of your OT sensor quickly and solve the problem at a later time. For more information, see activate your OT sensor.
July 2024
| Service area | Updates |
|---|---|
| OT networks | - Security update |
Security update
This update resolves a CVE, which is listed in software version 24.1.4 feature documentation.
June 2024
| Service area | Updates |
|---|---|
| OT networks | - Malicious URL path alert - Newly supported protocols |
Malicious URL path alert
The new alert, Malicious URL path, allows users to identify malicious paths in legitimate URLs. The Malicious URL path alert expands Defender for IoT's threat identification to include generic URL signatures, crucial for countering a wide range of cyber threats.
For more information, this alert is described in the Malware engine alerts table.
Newly supported protocols
We now support the Open protocol. See the updated protocol list.
April 2024
| Service area | Updates |
|---|---|
| OT networks | - Single sign-on for the sensor console - Sensor time drift detection - Security update |
Single sign-on for the sensor console
You can set up single sign-on (SSO) for the Defender for IoT sensor console using Microsoft Entra ID. SSO allows simple sign in for your organization's users, allows your organization to meet regulation standards, and increases your security posture. With SSO, your users don't need multiple login credentials across different sensors and sites.
Using Microsoft Entra ID simplifies the onboarding and offboarding processes, reduces administrative overhead, and ensures consistent access controls across the organization.
For more information, see Set up single sign-on on for the sensor console.
Sensor time drift detection
This version introduces a new troubleshooting test in the connectivity tool feature, specifically designed to identify time drift issues.
One common challenge when connecting sensors to Defender for IoT in the Azure portal arises from discrepancies in the sensor’s UTC time, which can lead to connectivity problems. To address this issue, we recommend that you configure a Network Time Protocol (NTP) server in the sensor settings.
Security update
This update resolves six CVEs, which are listed in software version 24.1.3 feature documentation.
February 2024
| Service area | Updates |
|---|---|
| OT networks | Version 24.1.2: - Alert suppression rules from the Azure portal (Public preview) - Focused alerts in OT/IT environments - Alert ID now aligned on the Azure portal and sensor console - Newly supported protocols Cloud features - New license renewal reminder in the Azure portal - New OT appliance hardware profile - New fields for SNMP MIB OIDs |
Alert suppression rules from the Azure portal (Public preview)
Now you can configure alert suppression rules from the Azure portal to instruct your OT sensors to specified traffic on your network that would otherwise trigger an alert.
- Configure which alerts to suppress by specifying an alert title, IP/MAC address, hostname, subnet, sensor, or site.
- Set each suppression rule to be active always, or only during a predefined period, such as for a specific maintenance window.
Tip
If you're currently using exclusion rules on the on-premises management console, we recommend that you migrate them to suppression rules on the Azure portal. For more information, see Suppress irrelevant alerts.
Focused alerts in OT/IT environments
Organizations where sensors are deployed between OT and IT networks deal with many alerts, related to both OT and IT traffic. The number of alerts, some of which are irrelevant, can cause alert fatigue and affect overall performance.
To address these challenges, we've updated Defender for IoT's detection policy to automatically trigger alerts based on business impact and network context, and reduce low-value IT related alerts.
This update is available in sensor version 24.1.3 and later.
For more information, see Focused alerts in OT/IT environments.
Alert ID now aligned on the Azure portal and sensor console
The alert ID in the Id column on the Azure portal Alerts page now displays the same alert ID as the sensor console. Learn more about alerts on the Azure portal.
Note
If the alert was merged with other alerts from sensors that detected the same alert, the Azure portal displays the alert ID of the first sensor that generated the alerts.
Newly supported protocols
We now support these protocols:
- HART-IP
- FANUC FOCAS
- Dicom
- ABB NetConfig
- Rockwell AADvance Discover
- Rockwell AADvance SNCP/IXL
- Schneider NetManage
See the updated protocol list.
L60 hardware profile is no longer supported
The L60 hardware profile is no longer supported and is removed from support documentation. Hardware profiles now require a minimum of 100GB (the minimum hardware profile is now L100).
To migrate from the L60 profile to a supported profile follow the Back up and restore OT network sensor procedure.
New license renewal reminder in the Azure portal
When the license for one or more of your OT sites is about to expire, a note is visible at the top of Defender for IoT in the Azure portal, reminding you to renew your licenses. To continue to get security value from Defender for IoT, select the link in the note to renew the relevant licenses in the Microsoft 365 admin center. Learn more about Defender for IoT billing.
New OT appliance hardware profile
The DELL XE4 SFF appliance is now supported for OT sensors monitoring production lines. This is part of the L500 hardware profile, a Production line environment, with six cores, 8-GB RAM, and 512-GB disk storage.
For more information, see DELL XE4 SFF.
New fields for SNMP MIB OIDs
Additional standard, generic fields have been added to the SNMP MiB OIDs. For the full list of fields, see OT sensor OIDs for manual SNMP configurations.
January 2024
| Service area | Updates |
|---|---|
| OT networks | Sensor update in Azure portal now supports selecting a specific version |
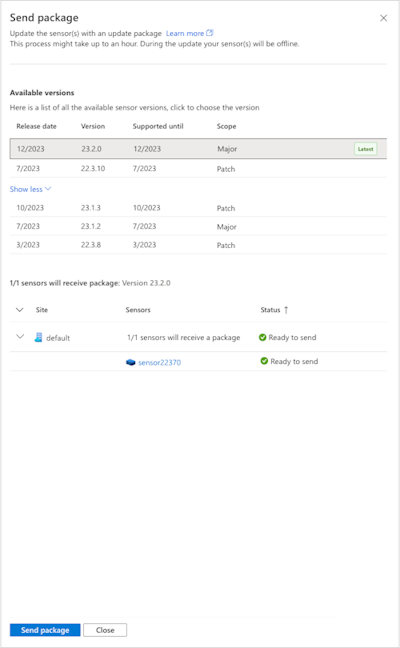
Sensor update in Azure portal now supports selecting a specific version
When you update the sensor in the Azure portal, you can now choose to update to any of the supported, previous versions (versions other than the latest version). Previously, sensors onboarded to Microsoft Defender for IoT on the Azure portal were automatically updated to the latest version.
You might want to update your sensor to a specific version for various reasons, such as for testing purposes, or to align all sensors to the same version.
For more information, see Update Defender for IoT OT monitoring software.
| OT networks |Version 24.1.0:
- Alert suppression rules from the Azure portal (Public preview)|
December 2023
| Service area | Updates |
|---|---|
| OT networks | New architecture for hybrid and air-gapped support Version 23.2.0: - OT network sensors now run on Debian 11 - Default privileged user is now admin instead of support Cloud features: - Live statuses for cloud-based sensor updates - Streamlined alert records in the SecurityAlert table |
OT network sensors now run on Debian 11
Sensor version 23.2.0 run on a Debian 11 operating system instead of Ubuntu. Debian is a Linux-based operating system that's widely used for servers and embedded devices, and is known for being leaner than other operating systems, and its stability, security, and extensive hardware support.
Using Debian as the base for our sensor software helps reduce the number of packages installed on the sensors, increasing efficiency and security of your systems.
Due to the operating system switch, the software update from your legacy version to version 23.2.0 might be longer and heavier than usual.
For more information, see Back up and restore OT network sensors from the sensor console and Update Defender for IoT OT monitoring software.
Default privileged user is now admin instead of support
Starting with version 23.2.0, the default, privileged user installed with new OT sensor installations is the admin user instead of the support user.
For example, use the privileged admin user in the following scenarios:
Signing into a new sensor for the first time after installation. For more information, see Configure and activate your OT sensor.
Using the Defender for IoT CLI. For more information, see Work with Defender for IoT CLI commands.
Accessing the sensor's Support page.
Important
If you're updating your sensor software from a previous version to version 23.2.0, the privileged support user is automatically renamed to admin. If you've saved your support credentials, such as in CLI scripts, you must update your scripts to use the new admin user instead.
The legacy support user is available and supported only on versions earlier than 23.2.0.
For more information, see On-premises users and roles for OT monitoring with Defender for IoT.
New architecture for hybrid and air-gapped support
Hybrid and air-gapped networks are common in many industries, such as government, financial services, or industrial manufacturing. Air-gapped networks are physically separated from other, unsecured external networks like enterprise networks or the internet, and are less vulnerable to cyber-attacks. However, air-gapped networks are still not completely secure, can still be breached, and must be secured and monitored carefully.
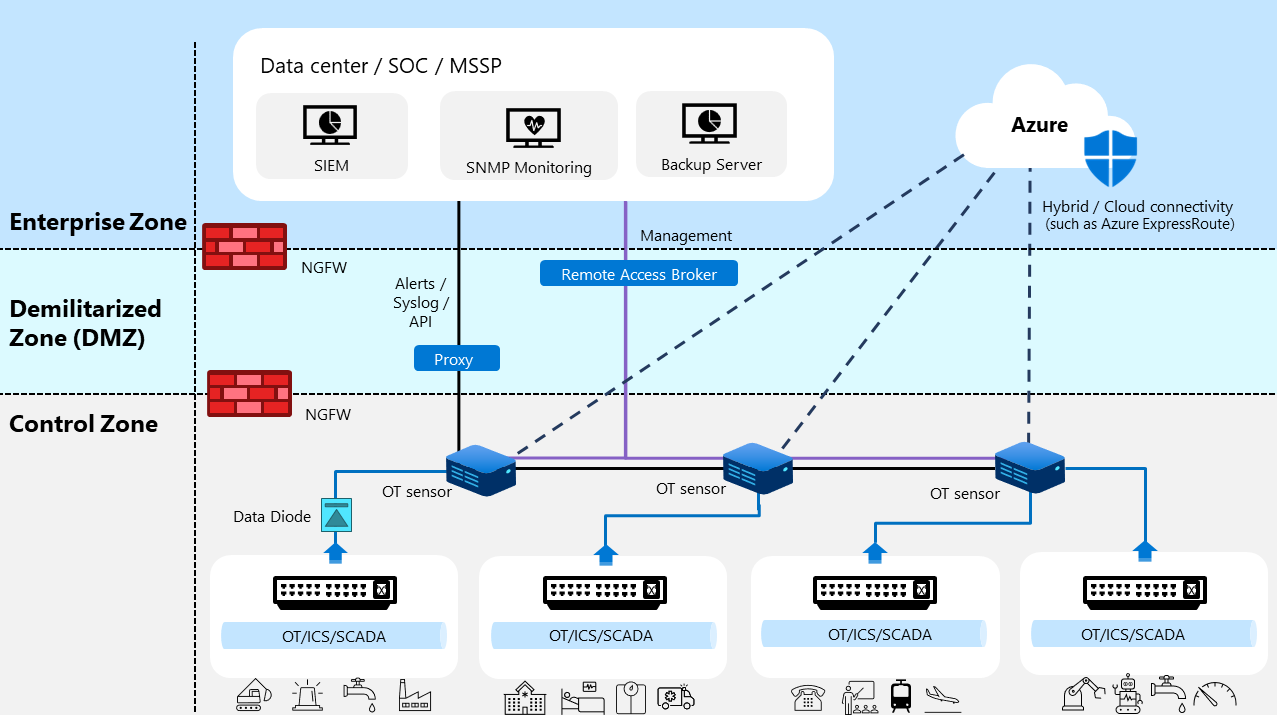
Defender for IoT now provides new guidance for connecting to and monitoring hybrid and air-gapped networks. The new architecture guidance is designed to add efficiency, security, and reliability to your SOC operations, with fewer components to maintain and troubleshoot. The sensor technology used in the new architecture allows for on-premises processing that keeps data within your own network, reducing the need for cloud resources and improving performance.
The following image shows a sample, high level architecture of our recommendations for monitoring and maintaining Defender for IoT systems, where each OT sensor connects to multiple security management systems in the cloud or on-premises.
In this sample image, communication for alerts, syslog messages, and APIs is shown in a solid black line. On-premises management communication is shown in a solid purple line, and cloud / hybrid management communication is shown in a dotted black line.
We recommend that existing customers who are currently using an on-premises management console to manage OT sensors transition to the updated architecture guidance.
For more information, see Deploy hybrid or air-gapped OT sensor management.
On-premises management console retirement
The legacy on-premises management console won't be available for download after January 1st, 2025. We recommend transitioning to the new architecture using the full spectrum of on-premises and cloud APIs before this date.
Sensor versions released after January 1, 2025 won't be able to be managed by an on-premises management console.
Sensor software versions released between January 1st, 2024 – January 1st, 2025 will continue to support an on-premises management console release.
Air-gapped sensors that cannot connect to the cloud can be managed directly via the sensor console or using REST APIs.
For more information, see:
- Transitioning from a legacy on-premises management console.
- Versioning and support for on-premises software versions
Live statuses for cloud-based sensor updates
When running a sensor update from the Azure portal, a new progress bar appears in the Sensor version column during the update process. As the update progresses the bar shows the percentage of the update completed, showing you that the process is ongoing, isn't stuck or has failed. For example:
For more information, see Update Defender for IoT OT monitoring software.
Streamlined alert records in the SecurityAlert table
When integrating with Microsoft Sentinel, the Microsoft Sentinel SecurityAlert table is now updated immediately only for changes in alert status and severity. Other changes in alerts, such as last detection of an existing alert, are aggregated over several hours and display only the latest change made.
For more information, see Understand multiple records per alert.
November 2023
| Service area | Updates |
|---|---|
| Enterprise IoT networks | Enterprise IoT protection now included in Microsoft 365 E5 and E5 Security licenses |
| OT networks | Updated security stack integration guidance |
Enterprise IoT protection now included in Microsoft 365 E5 and E5 Security licenses
Enterprise IoT (EIoT) security with Defender for IoT discovers unmanaged IoT devices and also provides added security value, including continuous monitoring, vulnerability assessments and tailored recommendations specifically designed for Enterprise IoT devices. Seamlessly integrated with Microsoft Defender XDR, Microsoft Defender Vulnerability Management, and Microsoft Defender for Endpoint on the Microsoft Defender Portal, it ensures a holistic approach to safeguarding an organization's network.
Defender for IoT EIoT monitoring is now automatically supported as part of the Microsoft 365 E5 (ME5) and E5 Security plans, covering up to five devices per user license. For example, if your organization possesses 500 ME5 licenses, you can use Defender for IoT to monitor up to 2500 EIoT devices. This integration represents a significant leap toward fortifying your IoT ecosystem within the Microsoft 365 environment.
Customers who have ME5 or E5 Security plans but aren't yet using Defender for IoT for their EIoT devices must toggle on support in the Microsoft Defender Portal.
New customers without an ME5 or E5 Security plan can purchase a standalone, Microsoft Defender for IoT - EIoT Device License - add-on license, as an add-on to Microsoft Defender for Endpoint P2. Purchase standalone licenses from the Microsoft admin center.
Existing customers with both legacy Enterprise IoT plans and ME5/E5 Security plans are automatically switched to the new licensing method. Enterprise IoT monitoring is now bundled into your license, at no extra charge, and with no action item required from you.
Customers with legacy Enterprise IoT plans and no ME5/E5 Security plans can continue to use their existing plans until the plans expire.
Trial licenses are available for Defender for Endpoint P2 customers as standalone licenses. Trial licenses support 100 number of devices.
For more information, see:
- Securing IoT devices in the enterprise
- Enable Enterprise IoT security with Defender for Endpoint
- Defender for IoT subscription billing
- Microsoft Defender for IoT Plans and Pricing
- Blog: Enterprise IoT security with Defender for IoT now included in Microsoft 365 E5 and E5 Security plans
Updated security stack integration guidance
Defender for IoT is refreshing its security stack integrations to improve the overall robustness, scalability, and ease of maintenance of various security solutions.
If you're integrating your security solution with cloud-based systems, we recommend that you use data connectors through Microsoft Sentinel. For on-premises integrations, we recommend that you either configure your OT sensor to forward syslog events), or use Defender for IoT APIs.
The legacy Aruba ClearPass, Palo Alto Panorama, and Splunk integrations are supported through October 2024 using sensor version 23.1.3, and won't be supported in upcoming major software versions.
For customers using legacy integration methods, we recommend moving your integrations to newly recommended methods. For more information, see:
- Integrate ClearPass with Microsoft Defender for IoT
- Integrate Palo Alto with Microsoft Defender for IoT
- Integrate Splunk with Microsoft Defender for IoT
- Integrations with Microsoft and partner services
September 2023
| Service area | Updates |
|---|---|
| OT networks | Version 23.1.3: - Troubleshoot OT sensor connectivity - Event timeline access for OT sensor Read Only users |
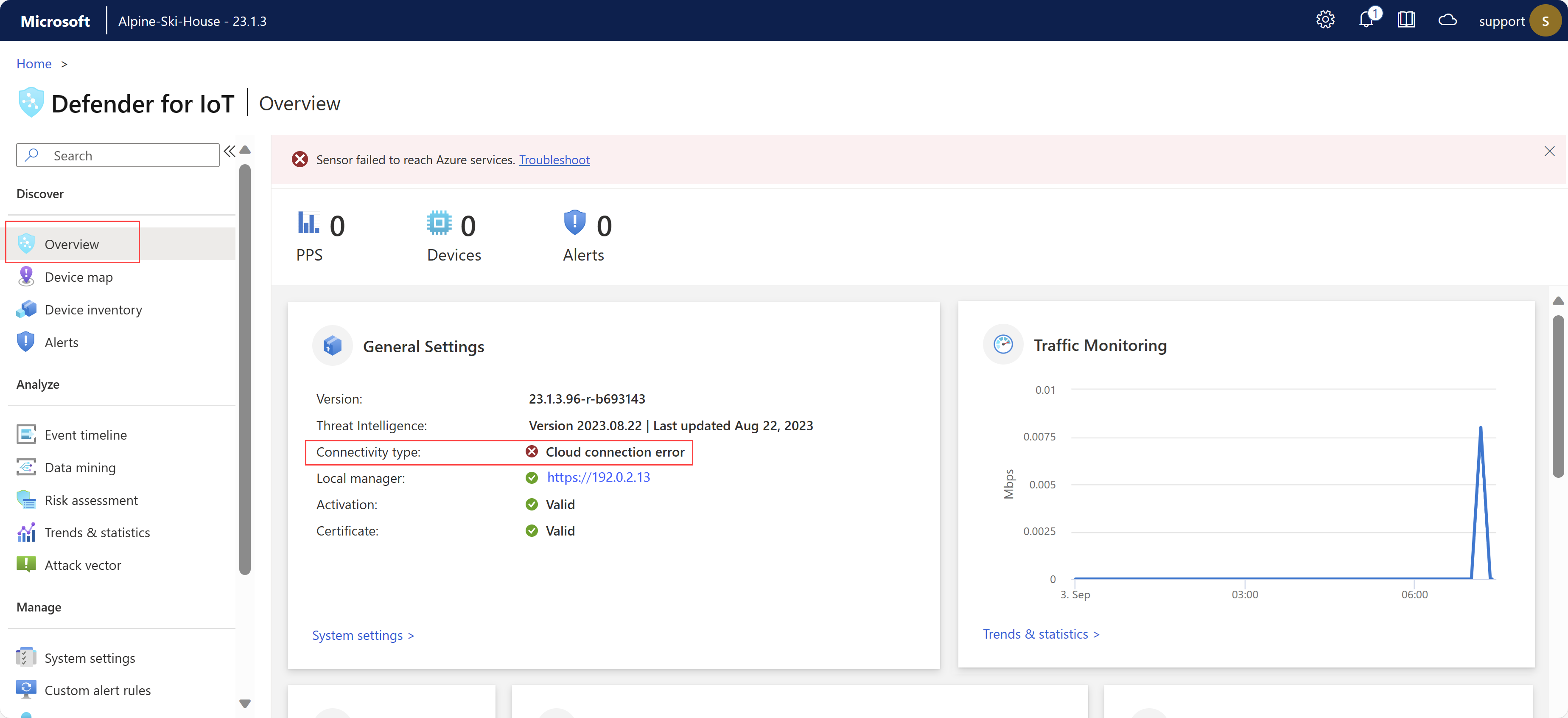
Troubleshoot OT sensor connectivity
Starting in version 23.1.3, OT sensors automatically help you troubleshoot connectivity issues with the Azure portal. If a cloud-managed sensor isn't connected, an error is indicated in the Azure portal on the Sites and sensors page, and on the sensor's Overview page.
For example:
From your sensor, do one of the following to open the Cloud connectivity troubleshooting pane, which provides details about the connectivity issues and mitigation steps:
- On the Overview page, select the Troubleshoot link at the top of the page
- Select System settings > Sensor management > Health and troubleshooting > Cloud connectivity troubleshooting
For more information, see Check sensor - cloud connectivity issues.
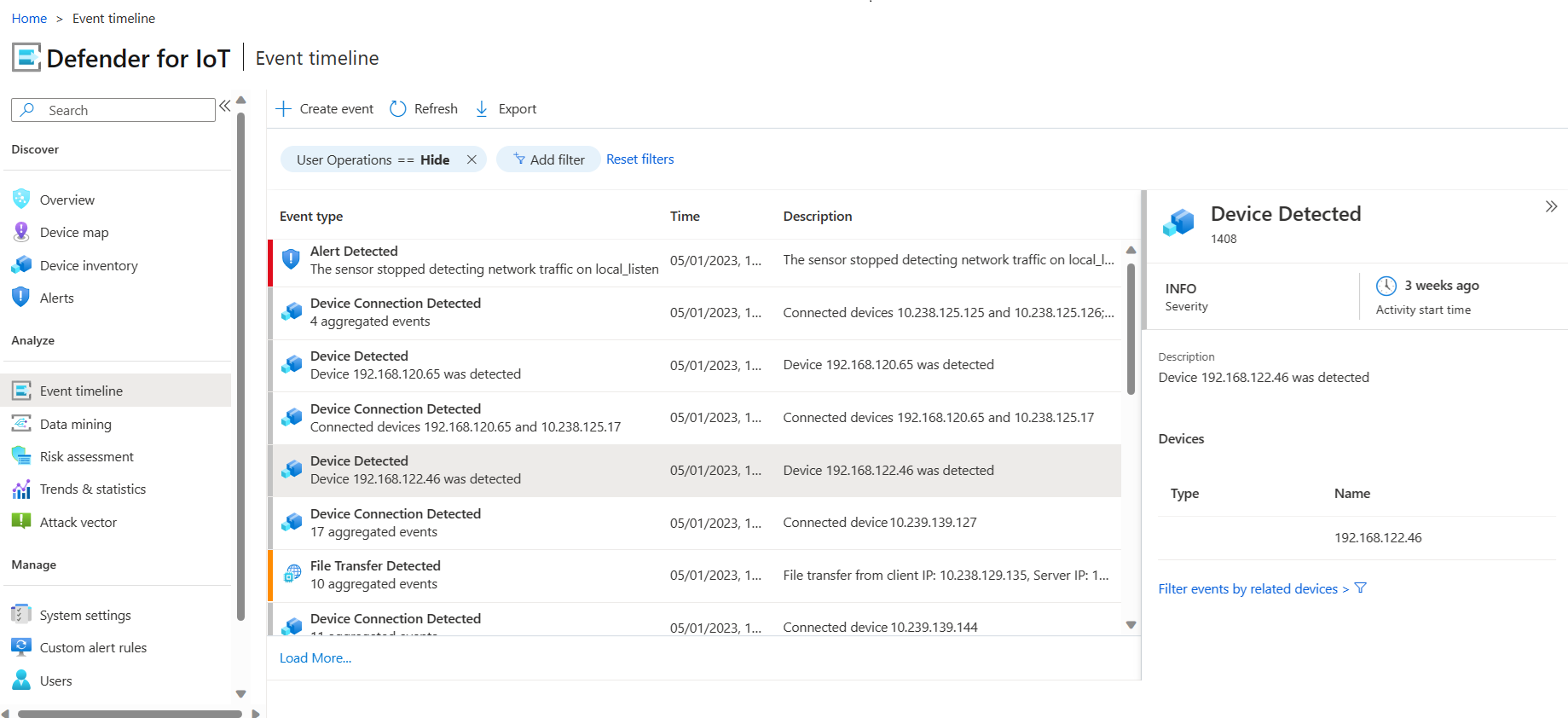
Event timeline access for OT sensor Read Only users
Starting in version 23.1.3, Read Only users on the OT sensor can view the Event Timeline page. For example:
For more information, see:
- Track network and sensor activity with the event timeline
- On-premises users and roles for OT monitoring with Defender for IoT
August 2023
| Service area | Updates |
|---|---|
| OT networks | Defender for IoT's CVEs align to CVSS v3 |
Defender for IoT's CVEs align to CVSS v3
CVE scores shown in the OT sensor and on the Azure portal are aligned with the National Vulnerability Database (NVD), and starting with Defender for IoT's August threat intelligence update, CVSS v3 scores are shown if they're relevant. If there's no CVSS v3 score relevant, the CVSS v2 score is shown instead.
View CVE data from the Azure portal, either on a Defender for IoT's device detail's Vulnerabilities tab, with resources available with the Microsoft Sentinel solution, or in a data mining query on your OT sensor. For more information, see:
- Maintain threat intelligence packages on OT network sensors
- View full device details
- Tutorial: Investigate and detect threats for IoT devices with Microsoft Sentinel
- Create data mining queries
July 2023
| Service area | Updates |
|---|---|
| OT networks | Version 23.1.2: - OT sensor installation and setup enhancements - Analyze and fine tune your deployment - Configure monitored interfaces via the sensor GUI - Simplified privileged users Migrate to site-based licenses |
OT sensor installation and setup enhancements
In version 23.1.2, we've updated the OT sensor installation and setup wizards to be quicker and more user-friendly. Updates include:
Installation wizard: If you're installing software on your own physical or virtual machines, the Linux installation wizard now goes directly through the installation process without requiring any input or details from you.
You can watch the installation run from a deployment workstation, but you might also choose to install the software without using a keyboard or screen, and let the installation run automatically. When it's done, access the sensor from the browser using the default IP address.
The installation uses default values for your network settings. Fine-tune these settings afterwards, either in the CLI as before, or in a new, browser-based wizard.
All sensors are installed with a default support user and password. Change the default password immediately with the first sign-in.
Configure initial setup in the browser: After installing software and configuring your initial network settings, continue with the same browser-based wizard to activate your sensor and define SSL/TLS certificate settings.
For more information, see Install and set up your OT sensor and Configure and activate your OT sensor.
Analyze and fine tune your deployment
After completing the installation and initial setup, analyze the traffic that the sensor detects by default from the sensor settings. On the sensor, select Sensor settings > Basic > Deployment to analyze the current detections.
You might find that you need to fine tune your deployment, such as changing the sensor's location in the network, or verifying that your monitoring interfaces are connected correctly. Select Analyze again after making any changes to see the updated monitoring state.
For more information, see Analyze your deployment.
Configure monitored interfaces via the sensor GUI
If you want to modify the interfaces used to monitor your traffic after the initial sensor setup, now you can use the new Sensor settings > Interface configurations page to update your settings instead of the Linux wizard accessed by CLI. For example:
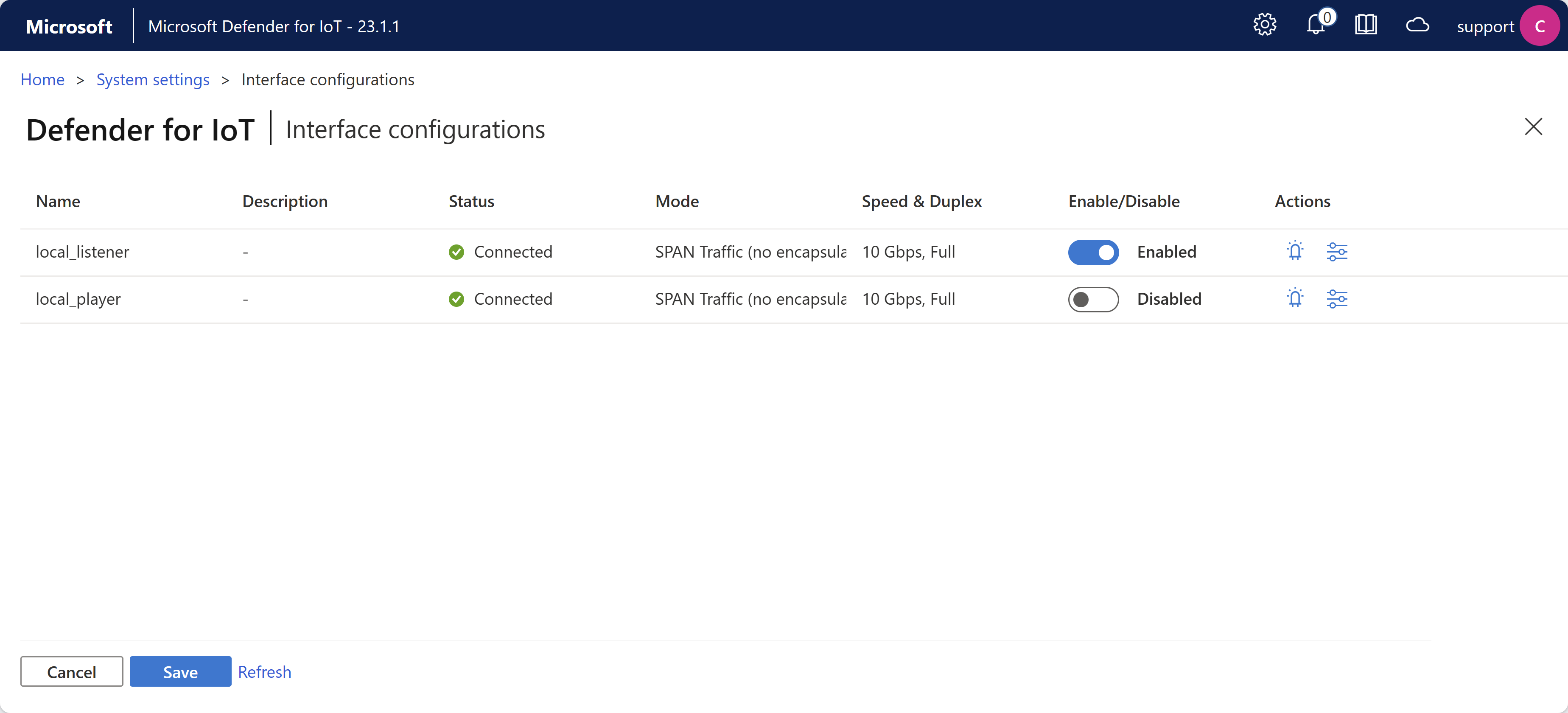
The Interface configurations page shows the same options as the Interface configurations tab in the initial setup wizard.
For more information, see Update a sensor's monitoring interfaces (configure ERSPAN).
Simplified privileged users
In new sensor installations of version 23.1.2, only the privileged support user is available by default. The cyberx and cyberx_host users are available, but are disabled by default. If you need to use these users, such as for Defender for IoT CLI access, change the user password.
In sensors that have been updated from previous versions to 23.1.2, the cyberx and cyberx_host users remain enabled as before.
Tip
To run CLI commands that are available only to the cyberx or cyberx_host users when signed in as the support user, make sure to first access the host machine's system root. For more information, see Access the system root as an admin user.
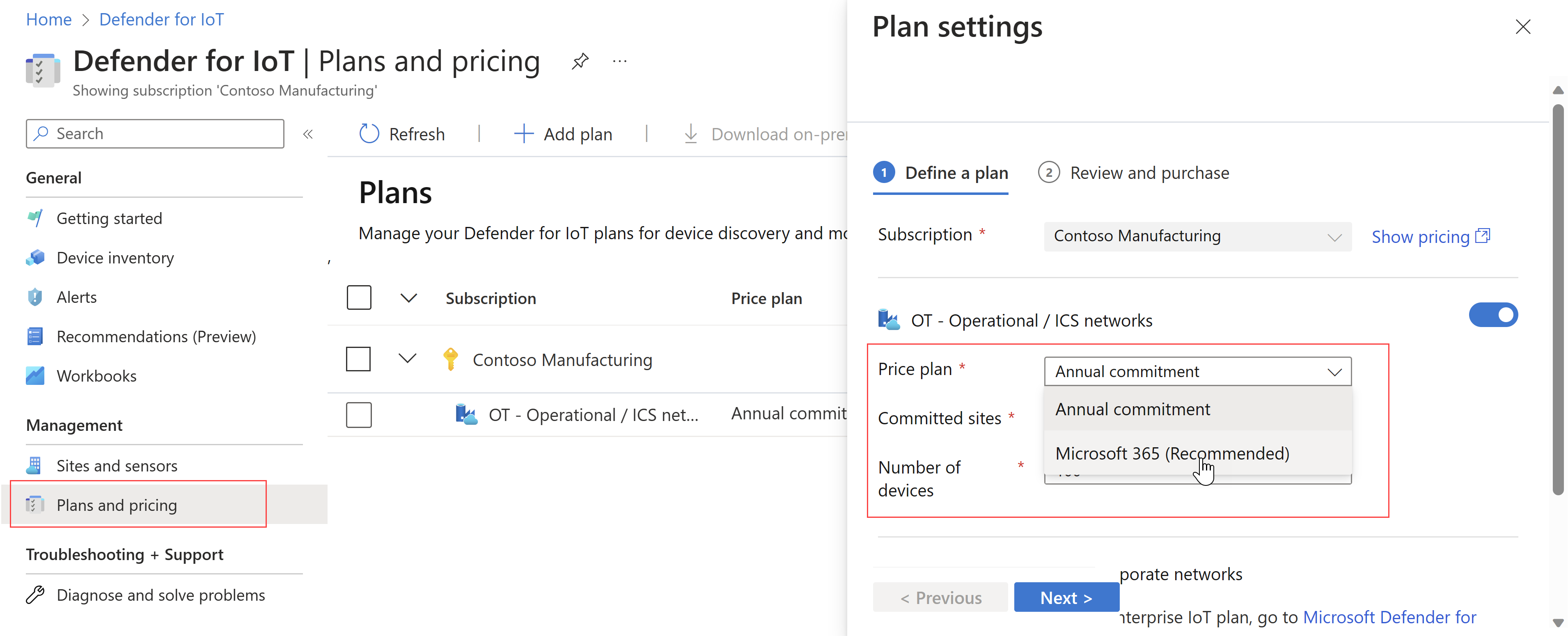
Migrate to site-based licenses
Existing customers can now migrate their legacy Defender for IoT purchasing plans to a Microsoft 365 plan, based on site-based, Microsoft 365 licenses.
On the Plans and pricing page, edit your plan and select the Microsoft 365 plan instead of your current monthly or annual plan. For example:
Make sure to edit any relevant sites to match your newly licensed site sizes. For example:
For more information, see Migrate from a legacy OT plan and Defender for IoT subscription billing.
June 2023
| Service area | Updates |
|---|---|
| OT networks | OT plans billed by site-based licenses Security recommendations for OT networks for insecure passwords and critical CVEs |
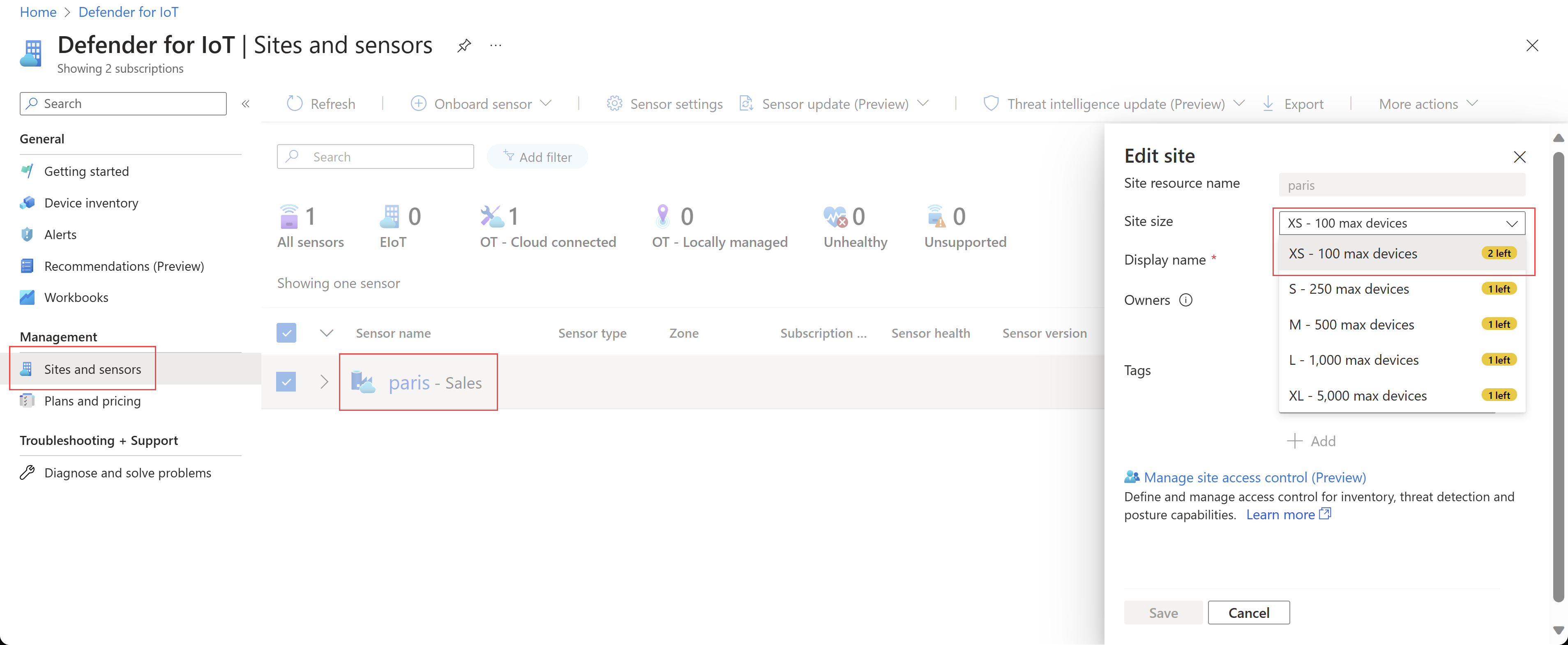
OT plans billed by site-based licenses
Starting June 1, 2023, Microsoft Defender for IoT licenses for OT monitoring are available for purchase only in the Microsoft 365 admin center.
Licenses are available for individual sites, based on the sizes of those respective sites. A trial license is also available, covering a Large site size for 60 days.
Any purchase of extra licenses is automatically updated in your OT plan in the Azure portal.
When you onboard a new sensor, you're now requested to assign your sensor to a site that's based on your licensed site sizes.
Existing customers can continue to use any legacy OT plan already onboarded to an Azure subscription, with no changes in functionality. However, you can't add a new plan to a new subscription without a corresponding license from the Microsoft 365 admin center.
Tip
A Defender for IoT site is a physical location, such as a facility, campus, office building, hospital, rig, and so on. Each site can contain any number of network sensors, which identify devices across detected network traffic.
For more information, see:
- Defender for IoT subscription billing
- Start a Microsoft Defender for IoT trial
- Manage OT plans on Azure subscriptions
- Onboard OT sensors to Defender for IoT
Security recommendations for OT networks for insecure passwords and critical CVEs
Defender for IoT now provides security recommendations for insecure passwords and for critical CVEs to help customers manage their OT/IoT network security posture.
You can see the following new security recommendations from the Azure portal for detected devices across your networks:
Secure your vulnerable devices: Devices with this recommendation are found with one or more vulnerabilities with a critical severity. We recommend that you follow the steps listed by the device vendor or CISA (Cybersecurity & Infrastructure Agency).
Set a secure password for devices with missing authentication: Devices with this recommendation are found without authentication based on successful sign-ins. We recommend that you enable authentication, and that you set a stronger password with minimum length and complexity.
Set a stronger password with minimum length and complexity: Devices with this recommendation are found with weak passwords based on successful sign-ins. We recommend that you change the device password to a stronger password with minimum length and complexity.
For more information, see Supported security recommendations.
May 2023
| Service area | Updates |
|---|---|
| OT networks | Sensor version 22.3.9: - Improved monitoring and support for OT sensor logs Sensor versions 22.3.x and higher: - Configure Active Directory and NTP settings in the Azure portal |
Improved monitoring and support for OT sensor logs
In version 22.3.9, we've added a new capability to collect logs from the OT sensor through a new endpoint. The extra data helps us troubleshoot customer issues, providing faster response times and more targeted solutions and recommendations. The new endpoint has been added to our list of required endpoints that connect your OT sensors to Azure.
After updating your OT sensors, download the latest list of endpoints and ensure that your sensors can access all endpoints listed.
For more information, see:
Configure Active Directory and NTP settings in the Azure portal
Now you can configure Active Directory and NTP settings for your OT sensors remotely from the Sites and sensors page in the Azure portal. These settings are available for OT sensor versions 22.3.x and higher.
For more information, see Sensor setting reference.
April 2023
| Service area | Updates |
|---|---|
| Documentation | End-to-end deployment guides |
| OT networks | Sensor version 22.3.8: - Proxy support for client SSL/TLS certificates - Enrich Windows workstation and server data with a local script (Public preview) - Automatically resolved OS notifications - UI enhancement when uploading SSL/TLS certificates |
End-to-end deployment guides
The Defender for IoT documentation now includes a new Deploy section, with a full set of deployment guides for the following scenarios:
- Standard deployment for OT monitoring
- Air-gapped deployment for OT monitoring with an on-premises sensor management
- Enterprise IoT deployment
For example, the recommended deployment for OT monitoring includes the following steps, which are all detailed in our new articles:
The step-by-step instructions in each section are intended to help customers optimize for success and deploy for Zero Trust. Navigational elements on each page, including flow charts at the top and Next steps links at the bottom, indicate where you are in the process, what you’ve completed, and what your next step should be. For example:
For more information, see Deploy Defender for IoT for OT monitoring.
Proxy support for client SSL/TLS certificates
A client SSL/TLS certificate is required for proxy servers that inspect SSL/TLS traffic, such as when using services like Zscaler and Palo Alto Prisma. Starting in version 22.3.8, you can upload a client certificate through the OT sensor console.
For more information, see Configure a proxy.
Enrich Windows workstation and server data with a local script (Public preview)
Use a local script, available from the OT sensor UI, to enrich Microsoft Windows workstation and server data on your OT sensor. The script runs as a utility to detect devices and enrich data, and can be run manually or using standard automation tools.
For more information, see Enrich Windows workstation and server data with a local script.
Automatically resolved OS notifications
After you've updated your OT sensor to version 22.3.8, no new device notifications for Operating system changes are generated. Existing Operating system changes notifications are automatically resolved if they aren't dismissed or otherwise handled within 14 days.
For more information, see Device notification responses
UI enhancement when uploading SSL/TLS certificates
The OT sensor version 22.3.8 has an enhanced SSL/TLS Certificates configuration page for defining your SSL/TLS certificate settings and deploying a CA-signed certificate.
For more information, see Manage SSL/TLS certificates.
March 2023
| Service area | Updates |
|---|---|
| OT networks | Sensor version 22.3.6/22.3.7: - Support for transient devices - Learn DNS traffic by configuring allowlists - Device data retention updates - UI enhancements when uploading SSL/TLS certificates - Activation files expiration updates - UI enhancements for managing the device inventory - Updated severity for all Suspicion of Malicious Activity alerts - Automatically resolved device notifications Version 22.3.7 includes the same features as 22.3.6. If you have version 22.3.6 installed, we strongly recommend that you update to version 22.3.7, which also includes important bug fixes. Cloud features: - New Microsoft Sentinel incident experience for Defender for IoT |
Support for transient devices
Defender for IoT now identifies transient devices as a unique device type that represents devices that were detected for only a short time. We recommend investigating these devices carefully to understand their impact on your network.
For more information, see Defender for IoT device inventory and Manage your device inventory from the Azure portal.
Learn DNS traffic by configuring allowlists
The support user can now decrease the number of unauthorized internet alerts by creating an allowlist of domain names on your OT sensor.
When a DNS allowlist is configured, the sensor checks each unauthorized internet connectivity attempt against the list before triggering an alert. If the domain's FQDN is included in the allowlist, the sensor doesn’t trigger the alert and allows the traffic automatically.
All OT sensor users can view the list of allowed DNS domains and their resolved IP addresses in data mining reports.
For example:
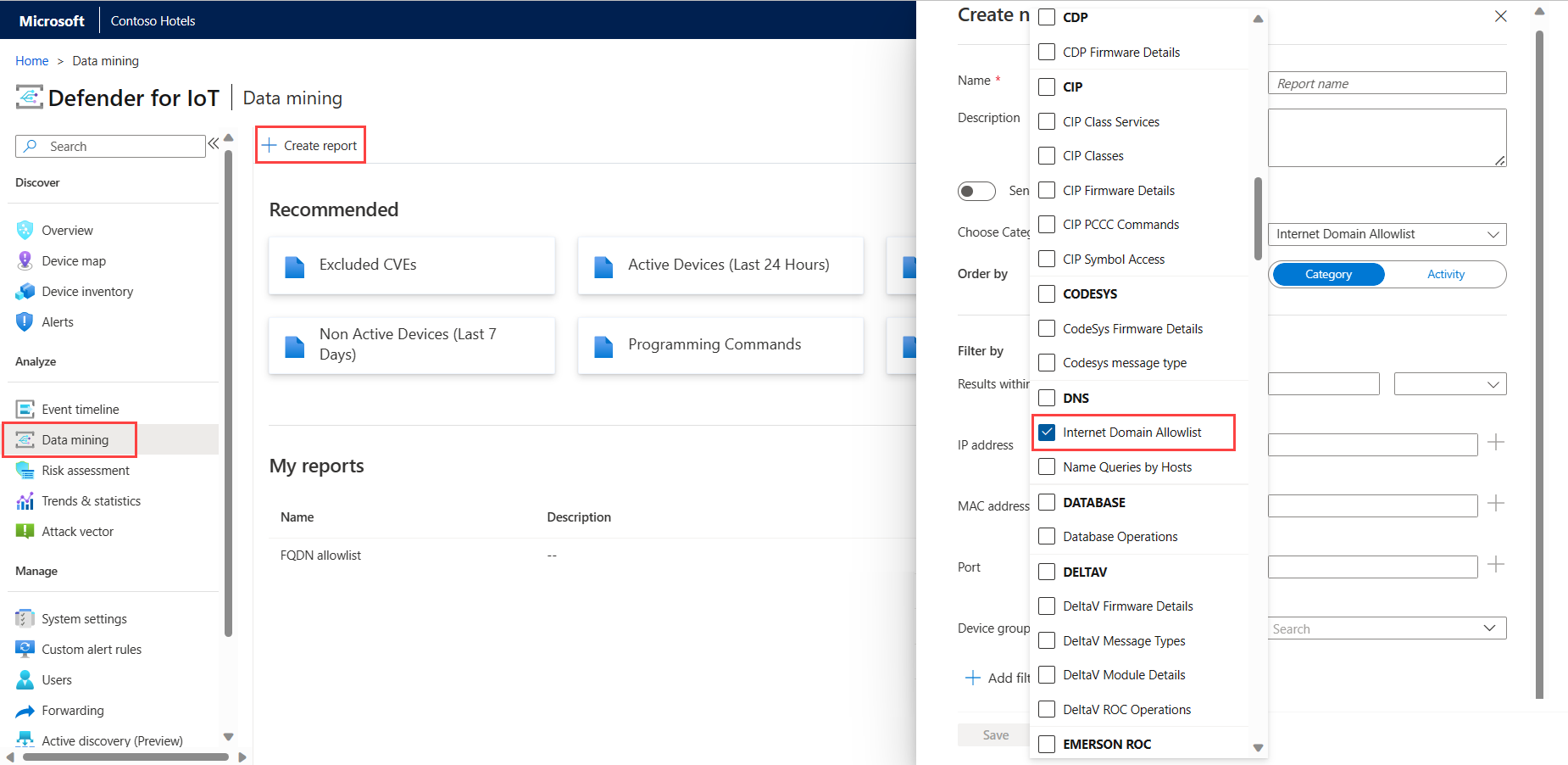
For more information, see Allow internet connections on an OT network and Create data mining queries.
Device data retention updates
The device data retention period on the OT sensor and on-premises management console has been updated to 90 days from the date of the Last activity value.
For more information, see Device data retention periods.
UI enhancements when uploading SSL/TLS certificates
The OT sensor version 22.3.6 has an enhanced SSL/TLS Certificates configuration page for defining your SSL/TLS certificate settings and deploying a CA-signed certificate.
For more information, see Manage SSL/TLS certificates.
Activation files expiration updates
Activation files on locally managed OT sensors now remain activated for as long as your Defender for IoT plan is active on your Azure subscription, just like activation files on cloud-connected OT sensors.
You only need to update your activation file if you're updating an OT sensor from a recent version or switching the sensor management mode, such as moving from locally managed to cloud-connected.
For more information, see Manage individual sensors.
UI enhancements for managing the device inventory
The following enhancements were added to the OT sensor's device inventory in version 22.3.6:
- A smoother process for editing device details on the OT sensor. Edit device details directly from the device inventory page on the OT sensor console using the new Edit button in the toolbar at the top of the page.
- The OT sensor now supports deleting multiple devices simultaneously.
- The procedures for merging and deleting devices now include confirmation messages that appear when the action has completed.
For more information, see Manage your OT device inventory from a sensor console.
Updated severity for all Suspicion of Malicious Activity alerts
All alerts with the Suspicion of Malicious Activity category now have a severity of Critical.
For more information, see Malware engine alerts.
Automatically resolved device notifications
Starting in version 22.3.6, selected notifications on the OT sensor's Device map page are now automatically resolved if they aren't dismissed or otherwise handled within 14 days.
After you've updated your sensor version, the Inactive devices and New OT devices notifications no longer appear. While any Inactive devices notifications that are left over from before the update are automatically dismissed, you might still have legacy New OT devices notifications to handle. Handle these notifications as needed to remove them from your sensor.
For more information, see Manage device notifications.
New Microsoft Sentinel incident experience for Defender for IoT
Microsoft Sentinel's new incident experience includes specific features for Defender for IoT customers. SOC analysts who are investigating OT/IoT-related can now use the following enhancements on incident details pages:
View related sites, zones, sensors, and device importance to better understand an incident's business impact and physical location.
Review an aggregated timeline of affected devices and related device details, instead of investigating on separate entity details pages for the related devices
Review OT alert remediation steps directly on the incident details page
For more information, see Tutorial: Investigate and detect threats for IoT devices and Navigate and investigate incidents in Microsoft Sentinel.
February 2023
| Service area | Updates |
|---|---|
| OT networks | Cloud features: - Microsoft Sentinel: Microsoft Defender for IoT solution version 2.0.2 - Download updates from the Sites and sensors page (Public preview) - Alerts page GA in the Azure portal - Device inventory GA in the Azure portal - Device inventory grouping enhancements (Public preview) - Focused inventory in the Azure device inventory (Public preview) Sensor version 22.2.3: Configure OT sensor settings from the Azure portal (Public preview) |
| Enterprise IoT networks | Cloud features: Alerts page GA in the Azure portal |
Microsoft Sentinel: Microsoft Defender for IoT solution version 2.0.2
Version 2.0.2 of the Microsoft Defender for IoT solution is now available in the Microsoft Sentinel content hub, with improvements in analytics rules for incident creation, an enhanced incident details page, and performance improvements for analytics rule queries.
For more information, see:
- Tutorial: Investigate and detect threats for IoT devices
- Microsoft Defender for IoT solution versions in Microsoft Sentinel
Download updates from the Sites and sensors page (Public preview)
If you're running a local software update on your OT sensor or on-premises management console, the Sites and sensors page now provides a new wizard for downloading your update packages, accessed via the Sensor update (Preview) menu.
For example:
Threat intelligence updates are also now available only from the Sites and sensors page > Threat intelligence update (Preview) option.
Update packages for the on-premises management console are also available from the Getting started > On-premises management console tab.
For more information, see:
- Update Defender for IoT OT monitoring software
- Update threat intelligence packages
- OT monitoring software versions
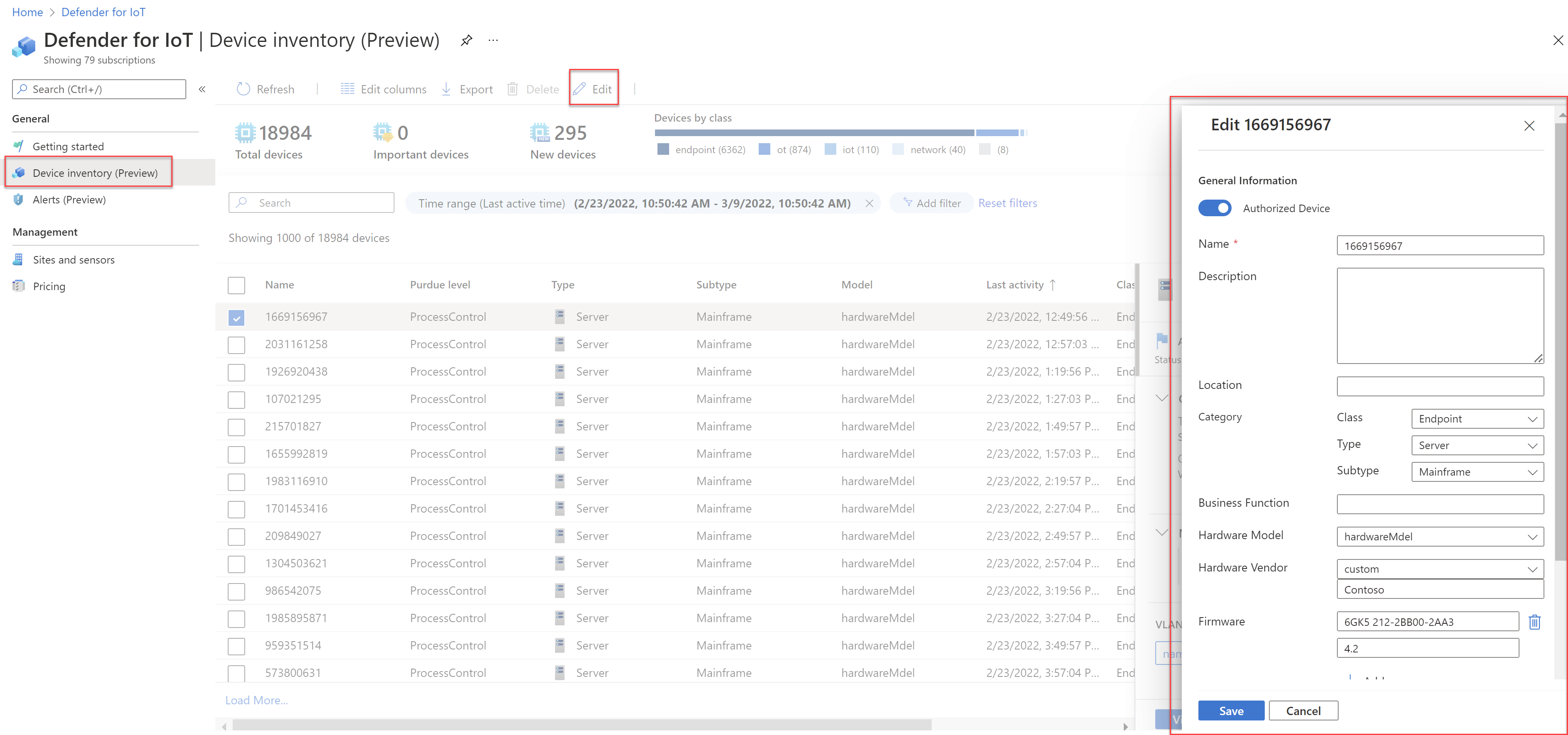
Device inventory GA in the Azure portal
The Device inventory page in the Azure portal is now Generally Available (GA), providing a centralized view across all your detected devices, at scale.
Defender for IoT's device inventory helps you identify details about specific devices, such as manufacturer, type, serial number, firmware, and more. Gathering details about your devices helps your teams proactively investigate vulnerabilities that can compromise your most critical assets.
Manage all your IoT/OT devices by building up-to-date inventory that includes all your managed and unmanaged devices
Protect devices with risk-based approach to identify risks such as missing patches, vulnerabilities and prioritize fixes based on risk scoring and automated threat modeling
Update your inventory by deleting irrelevant devices and adding organization-specific information to emphasize your organization preferences
The Device inventory GA includes the following UI enhancements:
| Enhancement | Description |
|---|---|
| Grid-level enhancements | - Export the entire device inventory to review offline and compare notes with your teams - Delete irrelevant devices that no longer exist or are no longer functional - Merge devices to fine-tune the device list if the sensor has discovered separate network entities that are associated with a single, unique device. For example, a PLC with four network cards, a laptop with both WiFi and a physical network card, or a single workstation with multiple network cards. - Edit your table views to reflect only the data you're interested in viewing |
| Device-level enhancements | - Edit device details by annotating organization-specific contextual details, such as relative importance, descriptive tags, and business function information |
| Filter and search enhancements | - Run deep searches on any device inventory field to quickly find the devices that matter most - Filter the device inventory by any field. For example, filter by Type to identify Industrial devices, or time fields to determine active and inactive devices. |
Rich security, governance and admin controls also provide the ability to assign admins, restricting who can merge, delete and edit devices on an owner’s behalf.
Device inventory grouping enhancements (Public preview)
The Device inventory page on the Azure portal supports new grouping categories. Now you can group your device inventory by class, data source, location, Purdue level, site, type, vendor, and zone. For more information, see View full device details.
Focused inventory in the Azure device inventory (Public preview)
The Device inventory page on the Azure portal now includes a network location indication for your devices, to help focus your device inventory on the devices within your IoT/OT scope.
See and filter which devices are defined as local or routed, according to your configured subnets. The Network location filter is on by default. Add the Network location column by editing the columns in the device inventory. Configure your subnets either on the Azure portal or on your OT sensor. For more information, see:
- Manage your device inventory from the Azure portal
- Configure OT sensor settings from the Azure portal
- Fine tune your subnet list
Configure OT sensor settings from the Azure portal (Public preview)
For sensor versions 22.2.3 and higher, you can now configure selected settings for cloud-connected sensors using the new Sensor settings (Preview) page, accessed via the Azure portal's Sites and sensors page. For example:
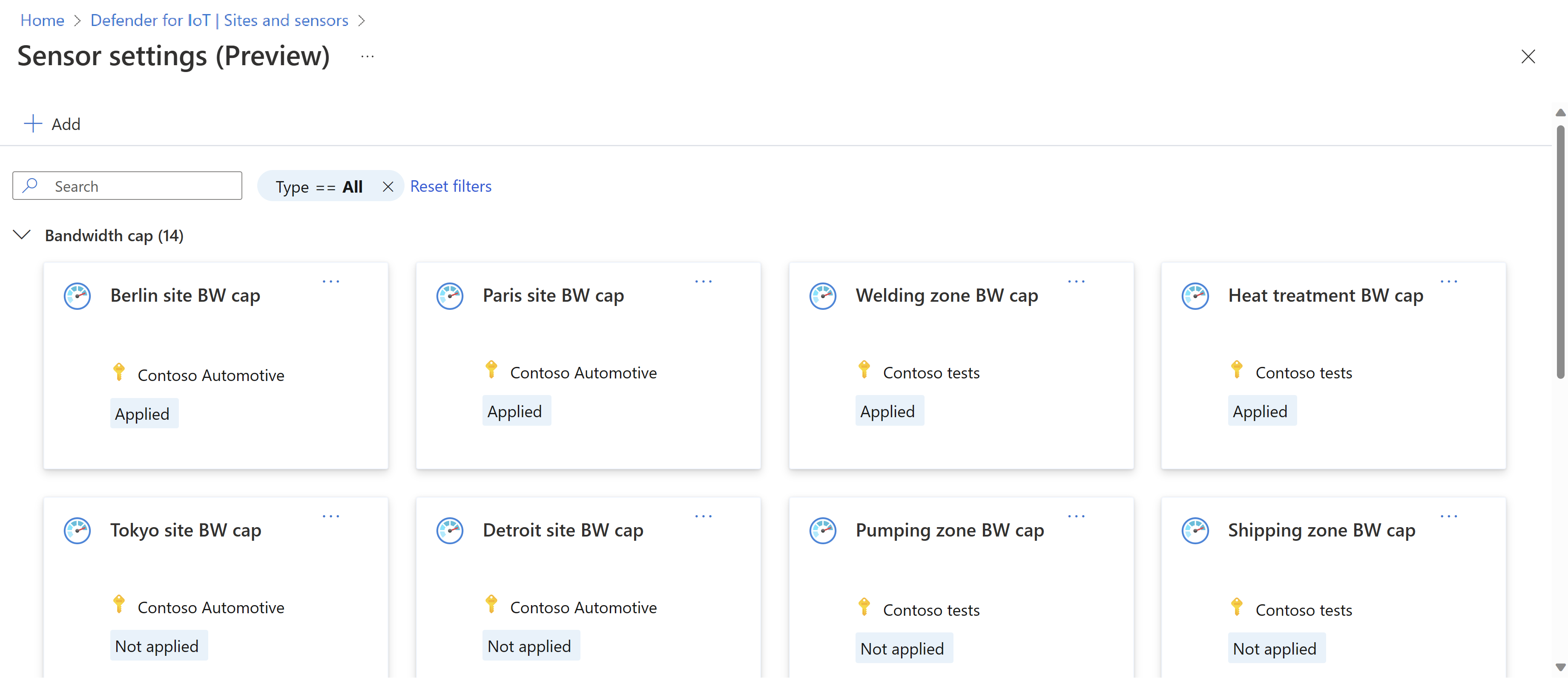
For more information, see Define and view OT sensor settings from the Azure portal (Public preview).
Alerts GA in the Azure portal
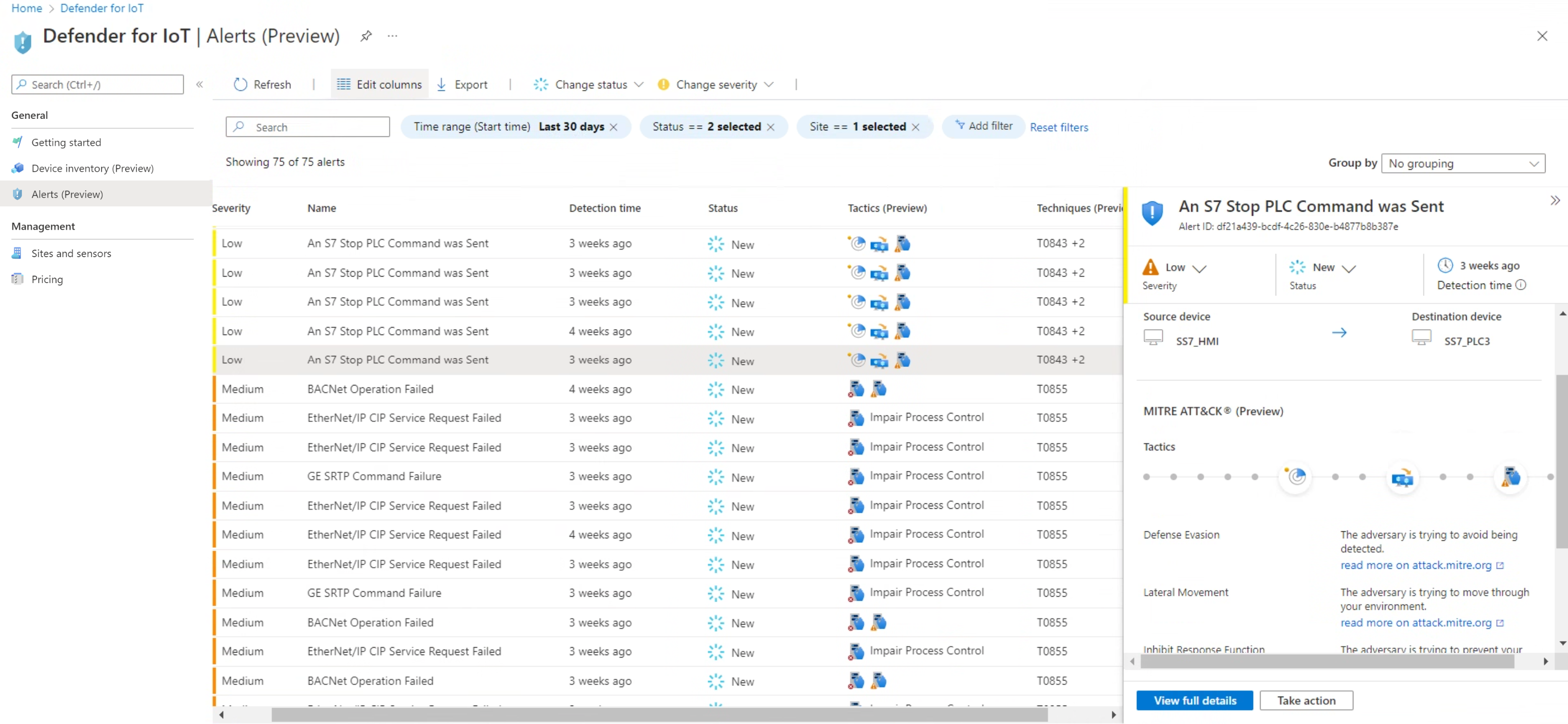
The Alerts page in the Azure portal is now out for General Availability. Microsoft Defender for IoT alerts enhance your network security and operations with real-time details about events detected in your network. Alerts are triggered when OT or Enterprise IoT network sensors, or the Defender for IoT micro agent, detect changes or suspicious activity in network traffic that needs your attention.
Specific alerts triggered by the Enterprise IoT sensor currently remain in public preview.
For more information, see:
- View and manage alerts from the Azure portal
- Investigate and respond to an OT network alert
- OT monitoring alert types and descriptions
January 2023
| Service area | Updates |
|---|---|
| OT networks | Sensor version 22.3.4: Azure connectivity status shown on OT sensors Sensor version 22.2.3: Update sensor software from the Azure portal |
Update sensor software from the Azure portal (Public preview)
For cloud-connected sensor versions 22.2.3 and higher, now you can update your sensor software directly from the new Sites and sensors page on the Azure portal.
For more information, see Update your sensors from the Azure portal.
Azure connectivity status shown on OT sensors
Details about Azure connectivity status are now shown on the Overview page in OT network sensors, and errors are shown if the sensor's connection to Azure is lost.
For example:
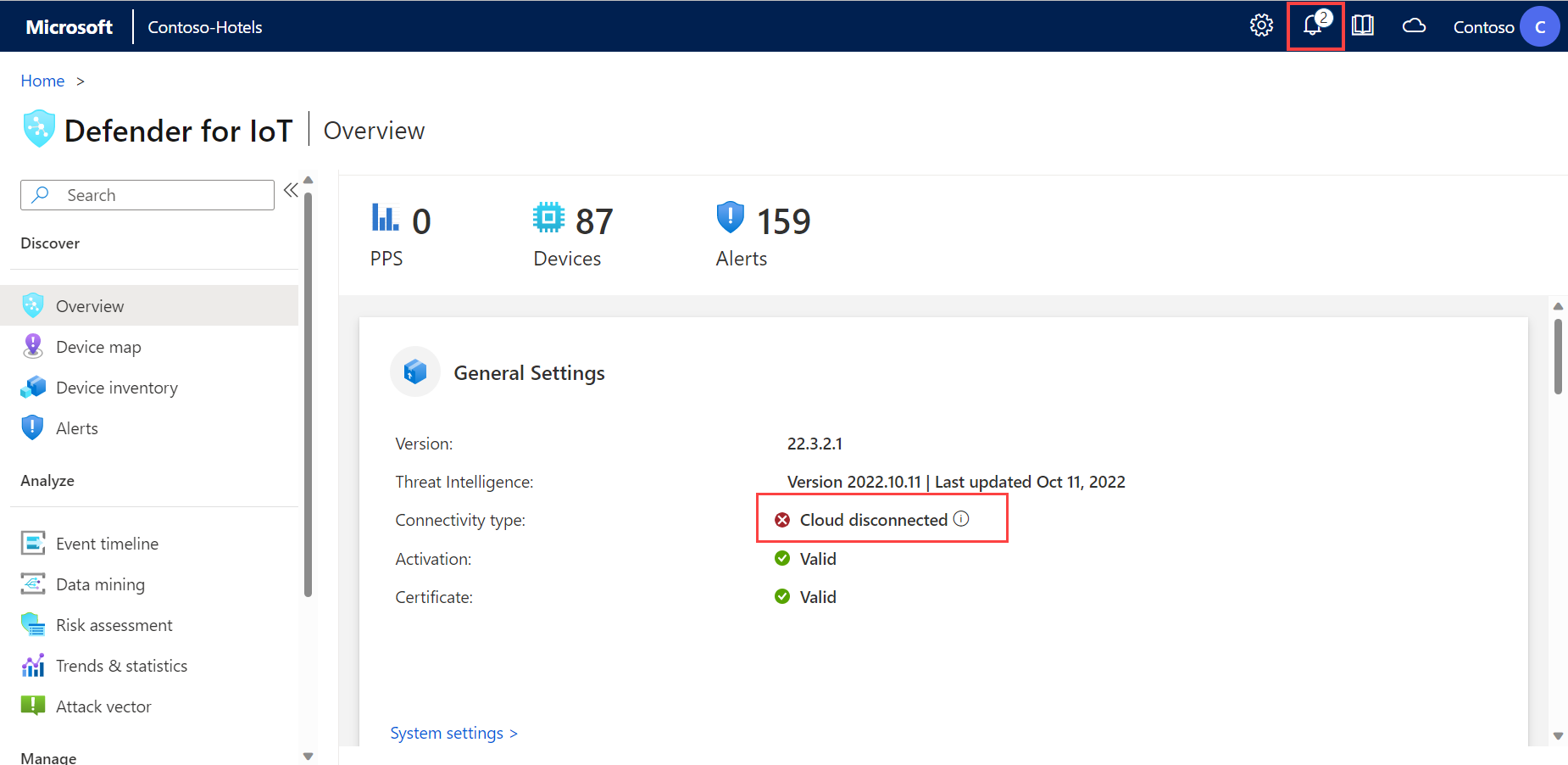
For more information, see Manage individual sensors and Onboard OT sensors to Defender for IoT.
December 2022
| Service area | Updates |
|---|---|
| OT networks | New purchase experience for OT plans |
| Enterprise IoT networks | Enterprise IoT sensor alerts and recommendations (Public Preview) |
Enterprise IoT sensor alerts and recommendations (Public Preview)
The Azure portal now provides the following extra security data for traffic detected by Enterprise IoT network sensors:
| Data type | Description |
|---|---|
| Alerts | The Enterprise IoT network sensor now triggers the following alerts: - Connection Attempt to Known Malicious IP - Malicious Domain Name Request |
| Recommendations | The Enterprise IoT network sensor now triggers the following recommendation for detected devices, as relevant: Disable insecure administration protocol |
For more information, see:
- Malware engine alerts
- View and manage alerts from the Azure portal
- Enhance security posture with security recommendations
- Discover Enterprise IoT devices with an Enterprise IoT network sensor (Public preview)
New purchase experience for OT plans
The Plans and pricing page in the Azure portal now includes a new enhanced purchase experience for Defender for IoT plans for OT networks. Edit your OT plan in the Azure portal, for example to change your plan from a trial to a monthly or annual commitment, or update the number of devices or sites.
For more information, see Manage OT plans on Azure subscriptions.
November 2022
| Service area | Updates |
|---|---|
| OT networks | - Sensor versions 22.x and later: Site-based access control on the Azure portal (Public preview) - All OT sensor versions: New OT monitoring software release notes |
Site-based access control on the Azure portal (Public preview)
For sensor software versions 22.x, Defender for IoT now supports site-based access control, which allows customers to control user access to Defender for IoT features on the Azure portal at the site level.
For example, apply the Security Reader, Security Admin, Contributor, or Owner roles to determine user access to Azure resources such as the Alerts, Device inventory, or Workbooks pages.
To manage site-based access control, select the site in the Sites and sensors page, and then select the Manage site access control (Preview) link. For example:
For more information, see Manage OT monitoring users on the Azure portal and Azure user roles for OT and Enterprise IoT monitoring.
Note
Sites, and therefore site-based access control, are relevant only for OT network monitoring.
New OT monitoring software release notes
Defender for IoT documentation now has a new release notes page dedicated to OT monitoring software, with details about our version support models and update recommendations.
We continue to update this article, our main What's new page, with new features and enhancements for both OT and Enterprise IoT networks. New items listed include both on-premises and cloud features, and are listed per month.
In contrast, the new OT monitoring software release notes lists only OT network monitoring updates that require you to update your on-premises software. Items are listed per major and patch versions, with an aggregated table of versions, dates, and scope.
For more information, see OT monitoring software release notes.
October 2022
| Service area | Updates |
|---|---|
| OT networks | Enhanced OT monitoring alert reference |
Enhanced OT monitoring alert reference
Our alert reference article now includes the following details for each alert:
Alert category, helpful when you want to investigate alerts that are aggregated by a specific activity or configure SIEM rules to generate incidents based on specific activities
Alert threshold, for relevant alerts. Thresholds indicate the specific point at which an alert is triggered. The cyberx user can modify alert thresholds as needed from the sensor's Support page.
For more information, see OT monitoring alert types and descriptions, and Supported alert categories.
September 2022
| Service area | Updates |
|---|---|
| OT networks | All supported OT sensor software versions: - Device vulnerabilities from the Azure portal - Security recommendations for OT networks All OT sensor software versions 22.x: Updates for Azure cloud connection firewall rules Sensor software version 22.2.7: - Bug fixes and stability improvements Sensor software version 22.2.6: - Bug fixes and stability improvements - Enhancements to the device type classification algorithm Microsoft Sentinel integration: - Investigation enhancements with IoT device entities - Updates to the Microsoft Defender for IoT solution |
Security recommendations for OT networks (Public preview)
Defender for IoT now provides security recommendations to help customers manage their OT/IoT network security posture. Defender for IoT recommendations help users form actionable, prioritized mitigation plans that address the unique challenges of OT/IoT networks. Use recommendations for lower your network's risk and attack surface.
You can see the following security recommendations from the Azure portal for detected devices across your networks:
Review PLC operating mode. Devices with this recommendation are found with PLCs set to unsecure operating mode states. We recommend setting PLC operating modes to the Secure Run state if access is no longer required to the PLC to reduce the threat of malicious PLC programming.
Review unauthorized devices. Devices with this recommendation must be identified and authorized as part of the network baseline. We recommend taking action to identify any indicated devices. Disconnect any devices from your network that remain unknown even after investigation to reduce the threat of rogue or potentially malicious devices.
Access security recommendations from one of the following locations:
The Recommendations page, which displays all current recommendations across all detected OT devices.
The Recommendations tab on a device details page, which displays all current recommendations for the selected device.
From either location, select a recommendation to drill down further and view lists of all detected OT devices that are currently in a healthy or unhealthy state, according to the selected recommendation. From the Unhealthy devices or Healthy devices tab, select a device link to jump to the selected device details page. For example:
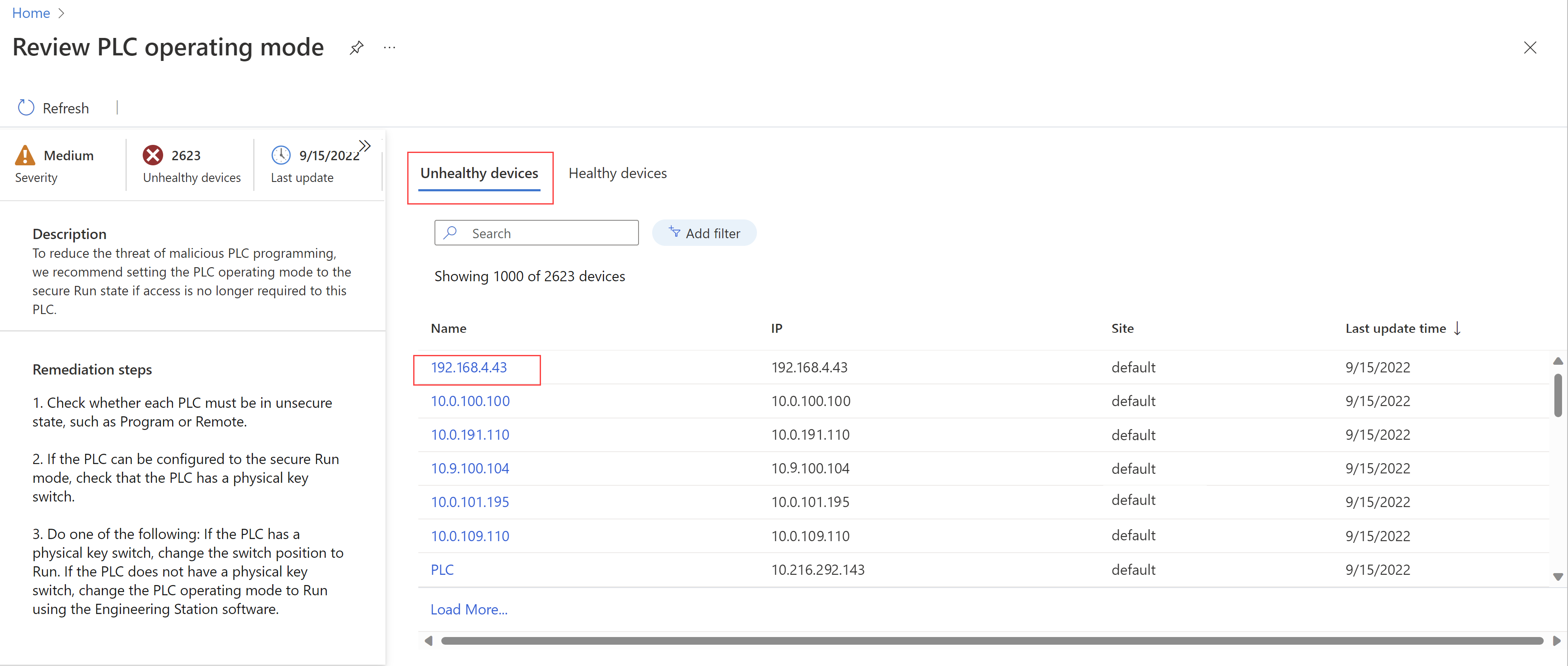
For more information, see View the device inventory and Enhance security posture with security recommendations.
Device vulnerabilities from the Azure portal (Public preview)
Defender for IoT now provides vulnerability data in the Azure portal for detected OT network devices. Vulnerability data is based on the repository of standards based vulnerability data documented at the US government National Vulnerability Database (NVD).
Access vulnerability data in the Azure portal from the following locations:
On a device details page, select the Vulnerabilities tab to view current vulnerabilities on the selected device. For example, from the Device inventory page, select a specific device and then select Vulnerabilities.
For more information, see View the device inventory.
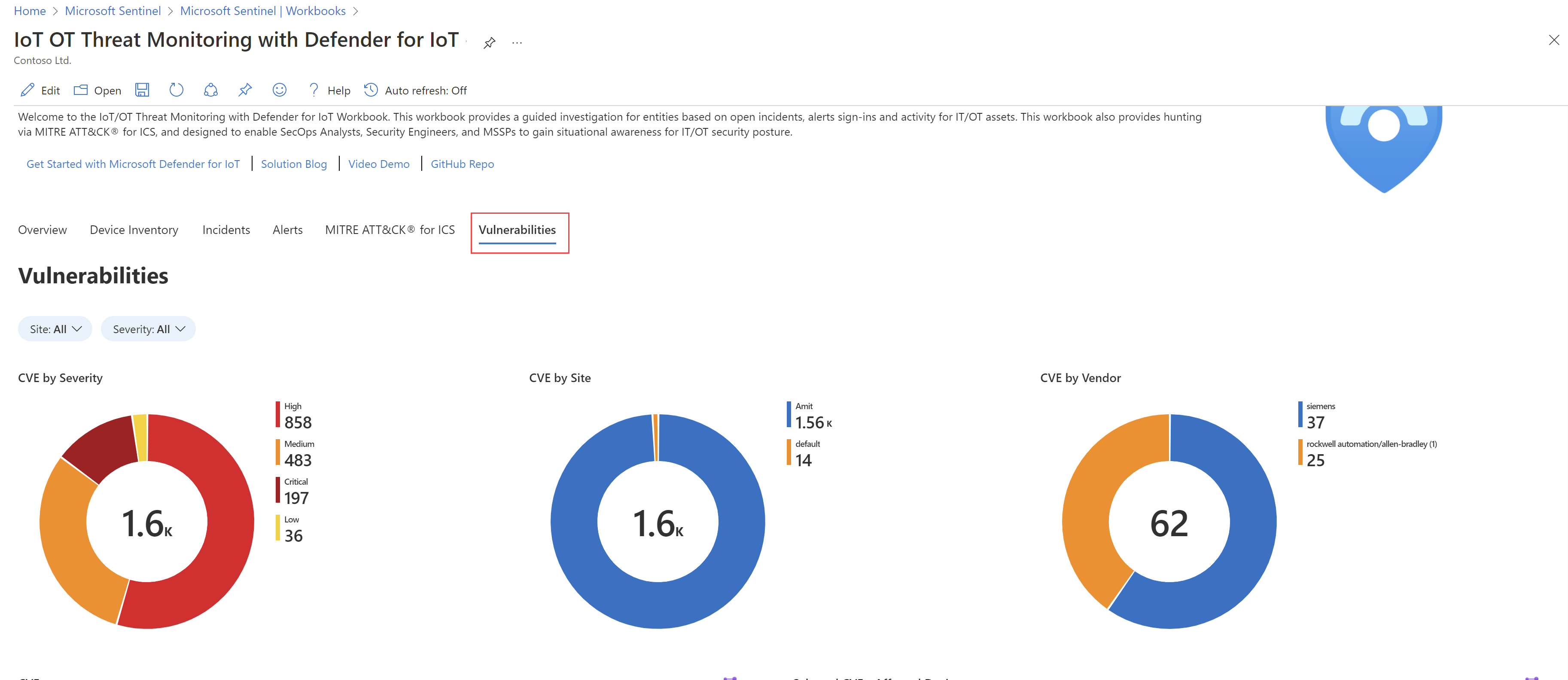
A new Vulnerabilities workbook displays vulnerability data across all monitored OT devices. Use the Vulnerabilities workbook to view data like CVE by severity or vendor, and full lists of detected vulnerabilities and vulnerable devices and components.
Select an item in the Device vulnerabilities, Vulnerable devices, or Vulnerable components tables to view related information in the tables on the right.
For example:
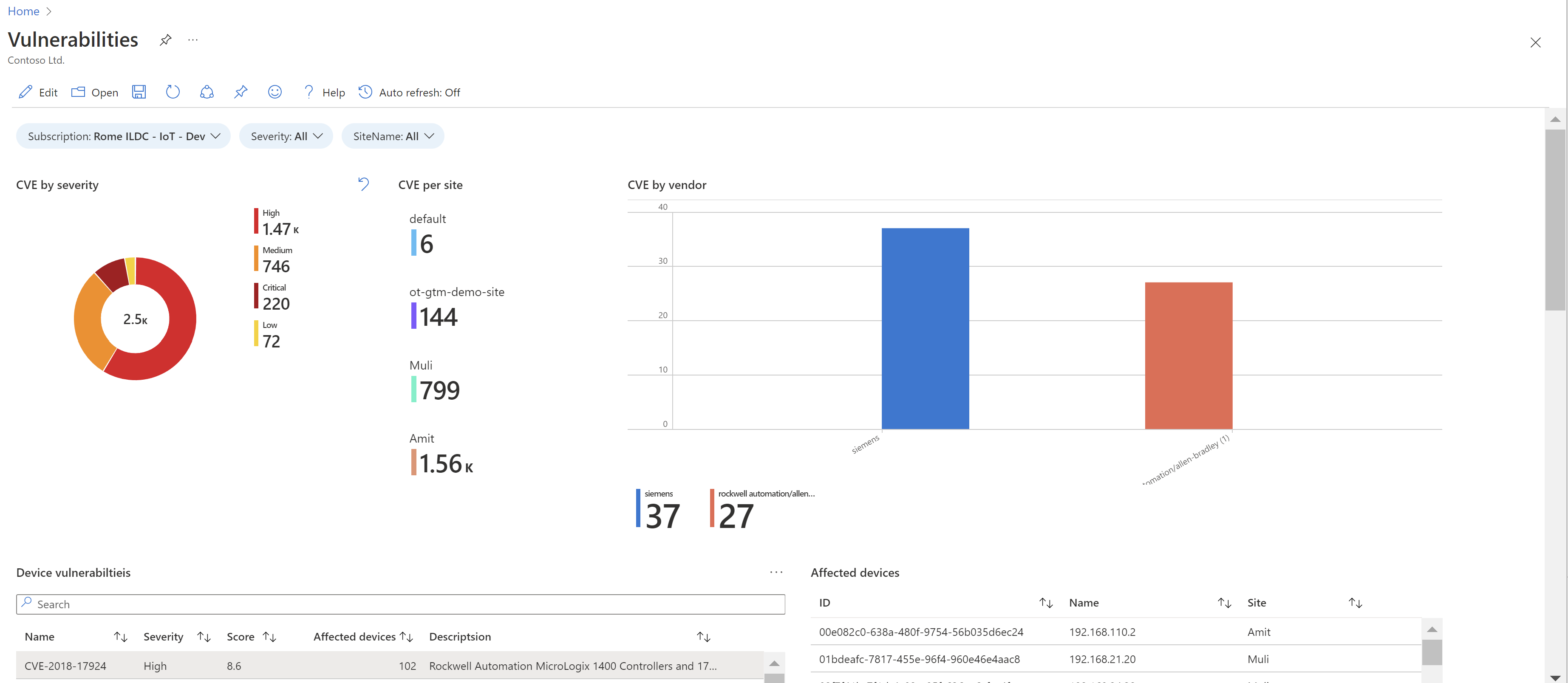
For more information, see Use Azure Monitor workbooks in Microsoft Defender for IoT.
Updates for Azure cloud connection firewall rules (Public preview)
OT network sensors connect to Azure to provide alert and device data and sensor health messages, access threat intelligence packages, and more. Connected Azure services include IoT Hub, Blob Storage, Event Hubs, and the Microsoft Download Center.
For OT sensors with software versions 22.x and higher, Defender for IoT now supports increased security when adding outbound allow rules for connections to Azure. Now you can define your outbound allow rules to connect to Azure without using wildcards.
When defining outbound allow rules to connect to Azure, you need to enable HTTPS traffic to each of the required endpoints on port 443. Outbound allow rules are defined once for all OT sensors onboarded to the same subscription.
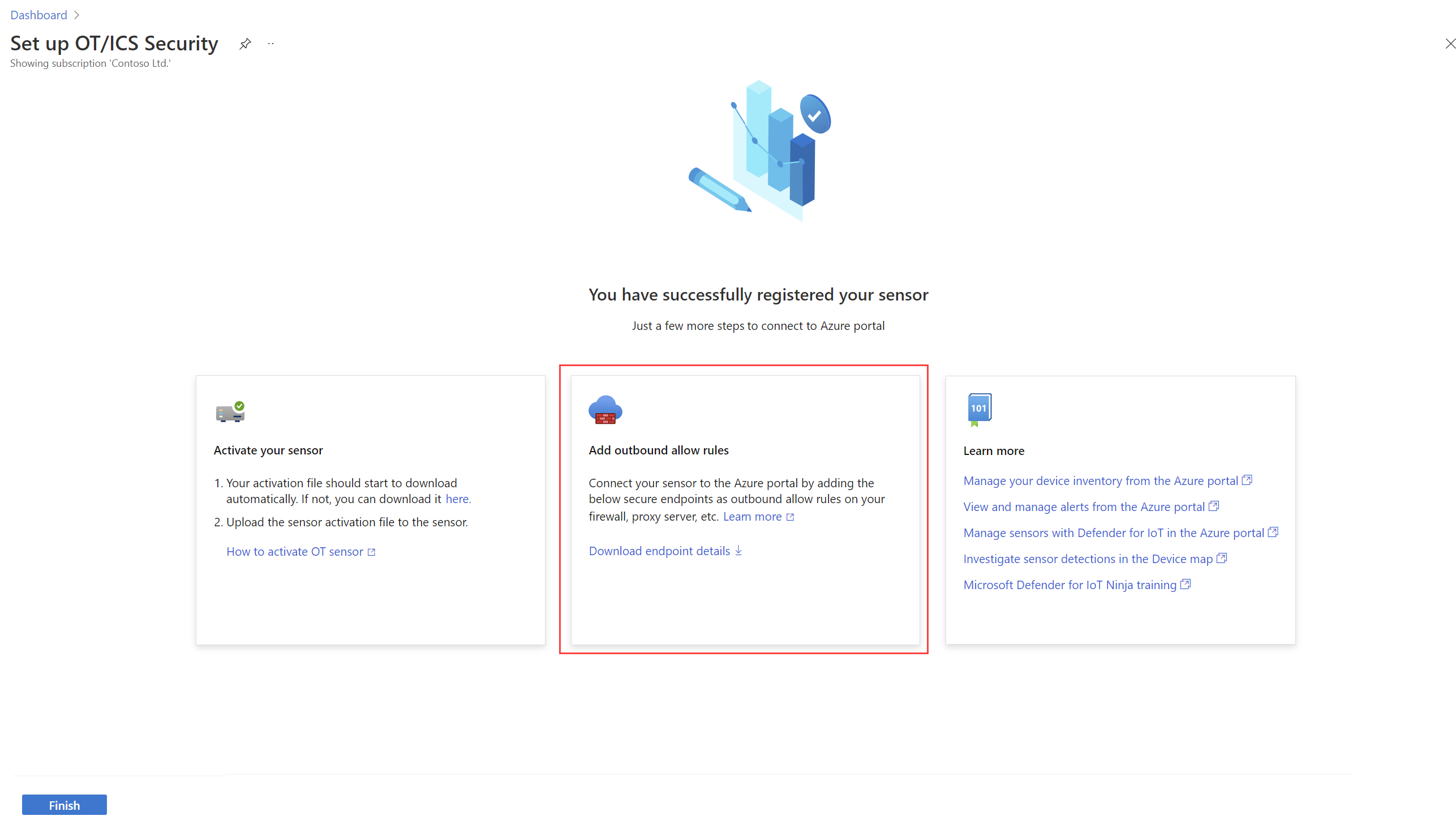
For supported sensor versions, download the full list of required secure endpoints from the following locations in the Azure portal:
A successful sensor registration page: After onboarding a new OT sensor with version 22.x, the successful registration page now provides instructions for next steps, including a link to the endpoints you'll need to add as secure outbound allow rules on your network. Select the Download endpoint details link to download the JSON file.
For example:
The Sites and sensors page: Select an OT sensor with software versions 22.x or higher, or a site with one or more supported sensor versions. Then, select More actions > Download endpoint details to download the JSON file. For example:
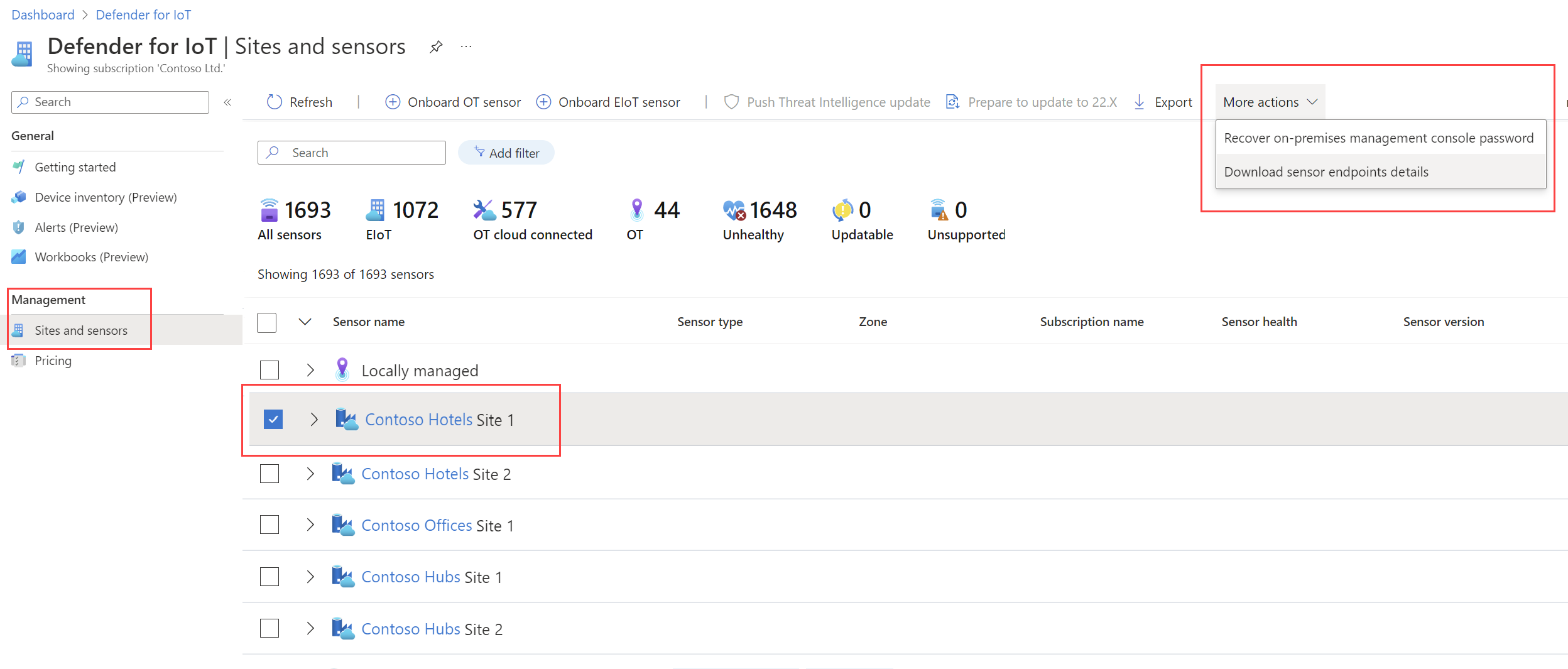
For more information, see:
- Tutorial: Get started with Microsoft Defender for IoT for OT security
- Manage sensors with Defender for IoT in the Azure portal
- Networking requirements
Investigation enhancements with IoT device entities in Microsoft Sentinel
Defender for IoT's integration with Microsoft Sentinel now supports an IoT device entity page. When investigating incidents and monitoring IoT security in Microsoft Sentinel, you can now identify your most sensitive devices and jump directly to more details on each device entity page.
The IoT device entity page provides contextual device information about an IoT device, with basic device details and device owner contact information. Device owners are defined by site in the Sites and sensors page in Defender for IoT.
The IoT device entity page can help prioritize remediation based on device importance and business impact, as per each alert's site, zone, and sensor. For example:
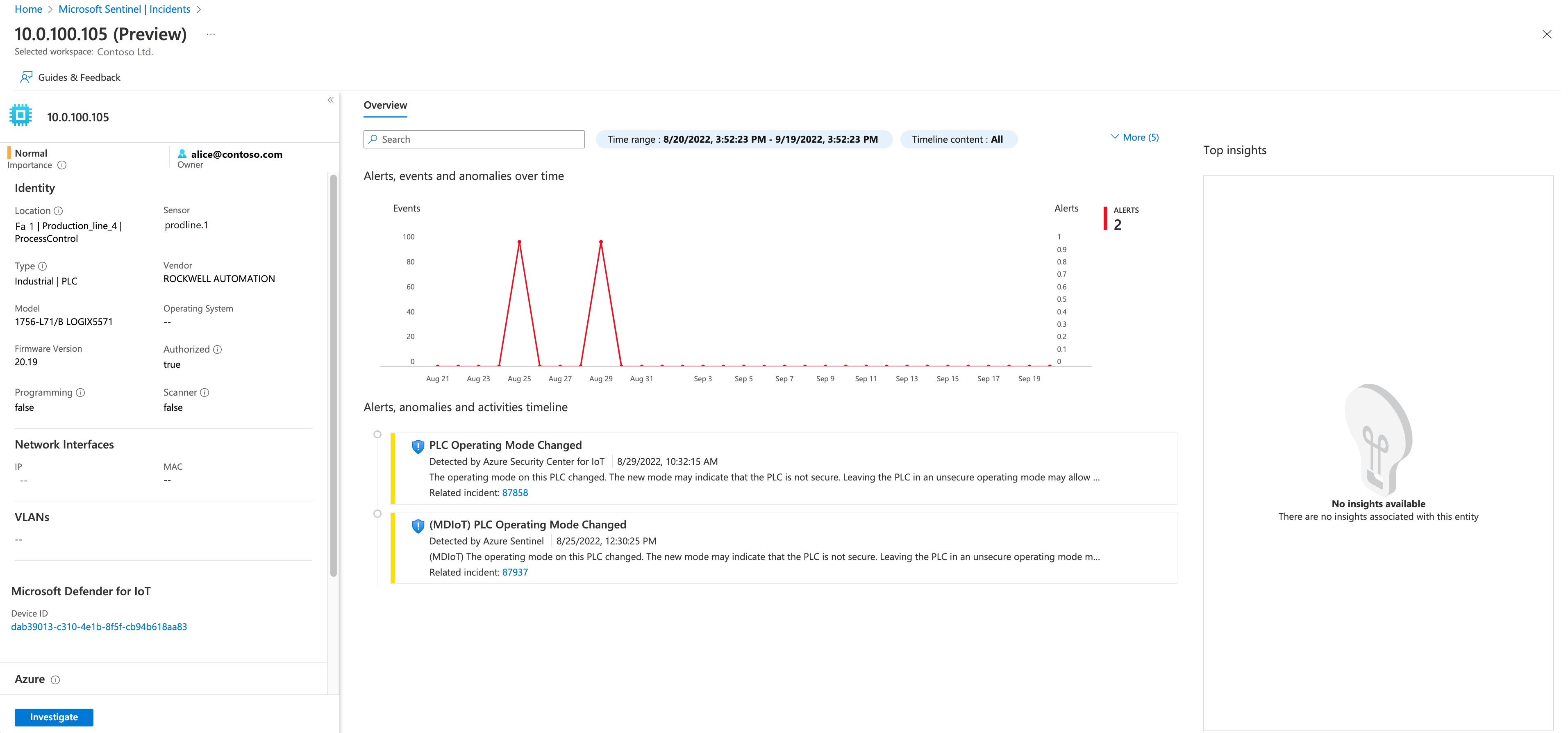
You can also now hunt for vulnerable devices on the Microsoft Sentinel Entity behavior page. For example, view the top five IoT devices with the highest number of alerts, or search for a device by IP address or device name:
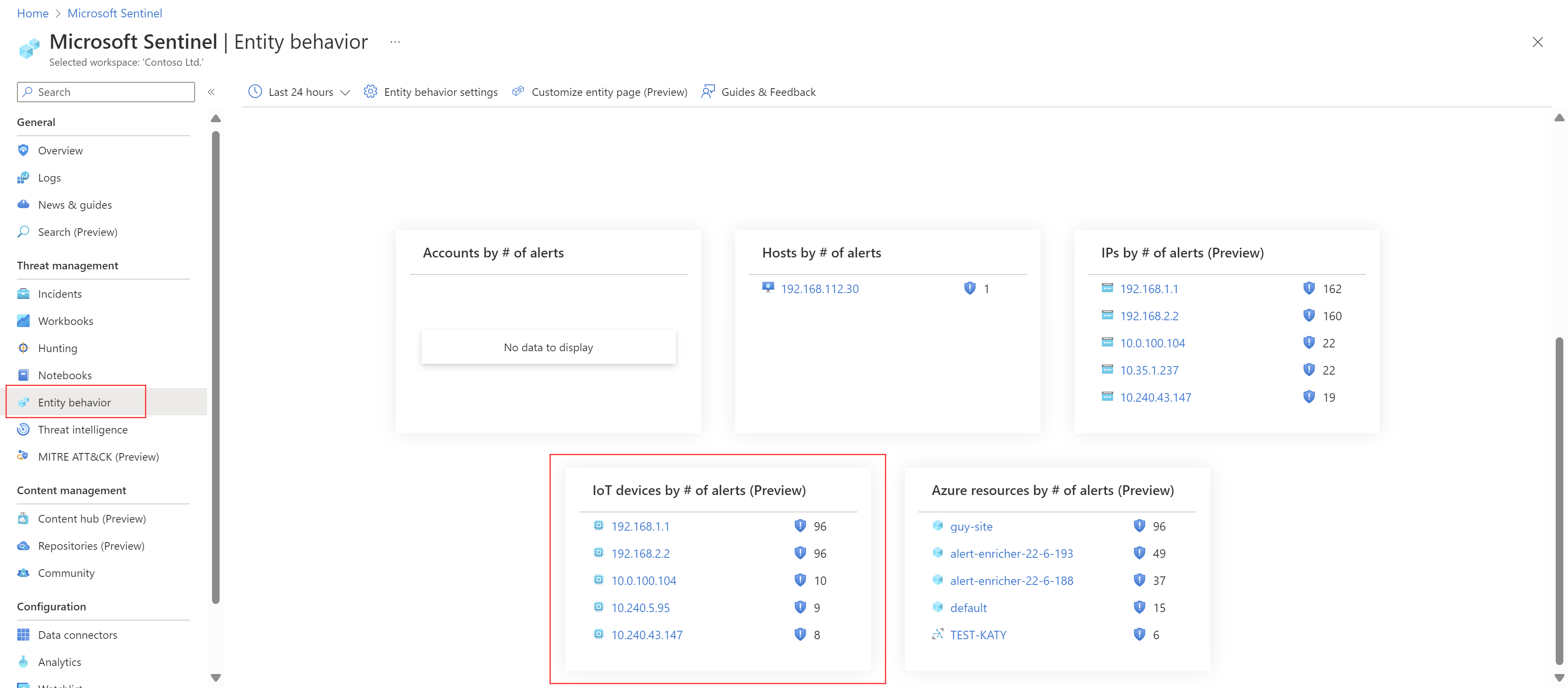
For more information, see Investigate further with IoT device entities and Site management options from the Azure portal.
Updates to the Microsoft Defender for IoT solution in Microsoft Sentinel's content hub
This month, we've released version 2.0 of the Microsoft Defender for IoT solution in Microsoft Sentinel's content hub, previously known as the IoT/OT Threat Monitoring with Defender for IoT solution.
Updates in this version of the solution include:
A name change. If you'd previously installed the IoT/OT Threat Monitoring with Defender for IoT solution in your Microsoft Sentinel workspace, the solution is automatically renamed to Microsoft Defender for IoT, even if you don't update the solution.
Workbook improvements: The Defender for IoT workbook now includes:
A new Overview dashboard with key metrics on the device inventory, threat detection, and security posture. For example:
A new Vulnerabilities dashboard with details about CVEs shown in your network and their related vulnerable devices. For example:
Improvements on the Device inventory dashboard, including access to device recommendations, vulnerabilities, and direct links to the Defender for IoT device details pages. The Device inventory dashboard in the IoT/OT Threat Monitoring with Defender for IoT workbook is fully aligned with the Defender for IoT device inventory data.
Playbook updates: The Microsoft Defender for IoT solution now supports the following SOC automation functionality with new playbooks:
Automation with CVE details: Use the AD4IoT-CVEAutoWorkflow playbook to enrich incident comments with CVEs of related devices based on Defender for IoT data. The incidents are triaged, and if the CVE is critical, the asset owner is notified about the incident by email.
Automation for email notifications to device owners. Use the AD4IoT-SendEmailtoIoTOwner playbook to have a notification email automatically sent to a device's owner about new incidents. Device owners can then reply to the email to update the incident as needed. Device owners are defined at the site level in Defender for IoT.
Automation for incidents with sensitive devices: Use the AD4IoT-AutoTriageIncident playbook to automatically update an incident's severity based on the devices involved in the incident, and their sensitivity level or importance to your organization. For example, any incident involving a sensitive device can be automatically escalated to a higher severity level.
For more information, see Investigate Microsoft Defender for IoT incidents with Microsoft Sentinel.
August 2022
| Service area | Updates |
|---|---|
| OT networks | Sensor software version 22.2.5: Minor version with stability improvements Sensor software version 22.2.4: New alert columns with timestamp data Sensor software version 22.1.3: Sensor health from the Azure portal (Public preview) |
New alert columns with timestamp data
Starting with OT sensor version 22.2.4, Defender for IoT alerts in the Azure portal and the sensor console now show the following columns and data:
Last detection. Defines the last time the alert was detected in the network, and replaces the Detection time column.
First detection. Defines the first time the alert was detected in the network.
Last activity. Defines the last time the alert was changed, including manual updates for severity or status, or automated changes for device updates or device/alert deduplication.
The First detection and Last activity columns aren't displayed by default. Add them to your Alerts page as needed.
Tip
If you're also a Microsoft Sentinel user, you'll be familiar with similar data from your Log Analytics queries. The new alert columns in Defender for IoT are mapped as follows:
- The Defender for IoT Last detection time is similar to the Log Analytics EndTime
- The Defender for IoT First detection time is similar to the Log Analytics StartTime
- The Defender for IoT Last activity time is similar to the Log Analytics TimeGenerated For more information, see:
- View alerts on the Defender for IoT portal
- View alerts on your sensor
- OT threat monitoring in enterprise SOCs
Sensor health from the Azure portal (Public preview)
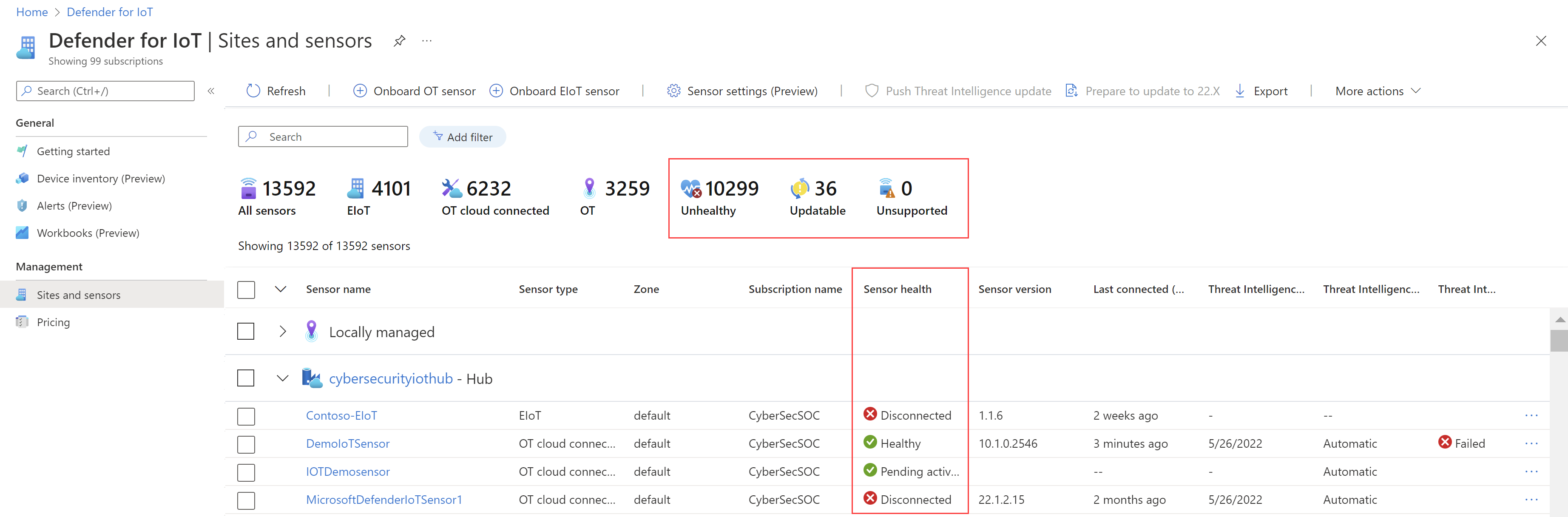
For OT sensor versions 22.1.3 and higher, you can use the new sensor health widgets and table column data to monitor sensor health directly from the Sites and sensors page on the Azure portal.
We've also added a sensor details page, where you drill down to a specific sensor from the Azure portal. On the Sites and sensors page, select a specific sensor name. The sensor details page lists basic sensor data, sensor health, and any sensor settings applied.
For more information, see Understand sensor health and Sensor health message reference.
July 2022
| Service area | Updates |
|---|---|
| Enterprise IoT networks | - Enterprise IoT and Defender for Endpoint integration in GA |
| OT networks | Sensor software version 22.2.4: - Device inventory enhancements - Enhancements for the ServiceNow integration API Sensor software version 22.2.3: - OT appliance hardware profile updates - PCAP access from the Azure portal - Bi-directional alert synch between sensors and the Azure portal - Sensor connections restored after certificate rotation - Support diagnostic log enhancements - Sensor names shown in browser tabs Sensor software version 22.1.7: - Same passwords for cyberx_host and cyberx users |
| Cloud-only features | - Microsoft Sentinel incident synch with Defender for IoT alerts |
Enterprise IoT and Defender for Endpoint integration in GA
The Enterprise IoT integration with Microsoft Defender for Endpoint is now in General Availability (GA). With this update, we've made the following updates and improvements:
Onboard an Enterprise IoT plan directly in Defender for Endpoint. For more information, see Manage your subscriptions and the Defender for Endpoint documentation.
Seamless integration with Microsoft Defender for Endpoint to view detected Enterprise IoT devices, and their related alerts, vulnerabilities, and recommendations in the Microsoft 365 Security portal. For more information, see the Enterprise IoT tutorial and the Defender for Endpoint documentation. You can continue to view detected Enterprise IoT devices on the Defender for IoT Device inventory page in the Azure portal.
All Enterprise IoT sensors are now automatically added to the same site in Defender for IoT, named Enterprise network. When onboarding a new Enterprise IoT device, you only need to define a sensor name and select your subscription, without defining a site or zone.
Note
The Enterprise IoT network sensor and all detections remain in Public Preview.
Same passwords for cyberx_host and cyberx users
During OT monitoring software installations and updates, the cyberx user is assigned a random password. When you update from version 10.x.x to version 22.1.7, the cyberx_host password is assigned with an identical password to the cyberx user.
For more information, see Install OT agentless monitoring software and Update Defender for IoT OT monitoring software.
Device inventory enhancements
Starting in OT sensor versions 22.2.4, you can now take the following actions from the sensor console's Device inventory page:
Merge duplicate devices. You might need to merge devices if the sensor has discovered separate network entities that are associated with a single, unique device. Examples of this scenario might include a PLC with four network cards, a laptop with both WiFi and a physical network card, or a single workstation with multiple network cards.
Delete single devices. Now, you can delete a single device that hasn't communicated for at least 10 minutes.
Delete inactive devices by admin users. Now, all admin users, in addition to the cyberx user, can delete inactive devices.
Also starting in version 22.2.4, in the sensor console's Device inventory page, the Last seen value in the device details pane is replaced by Last activity. For example:
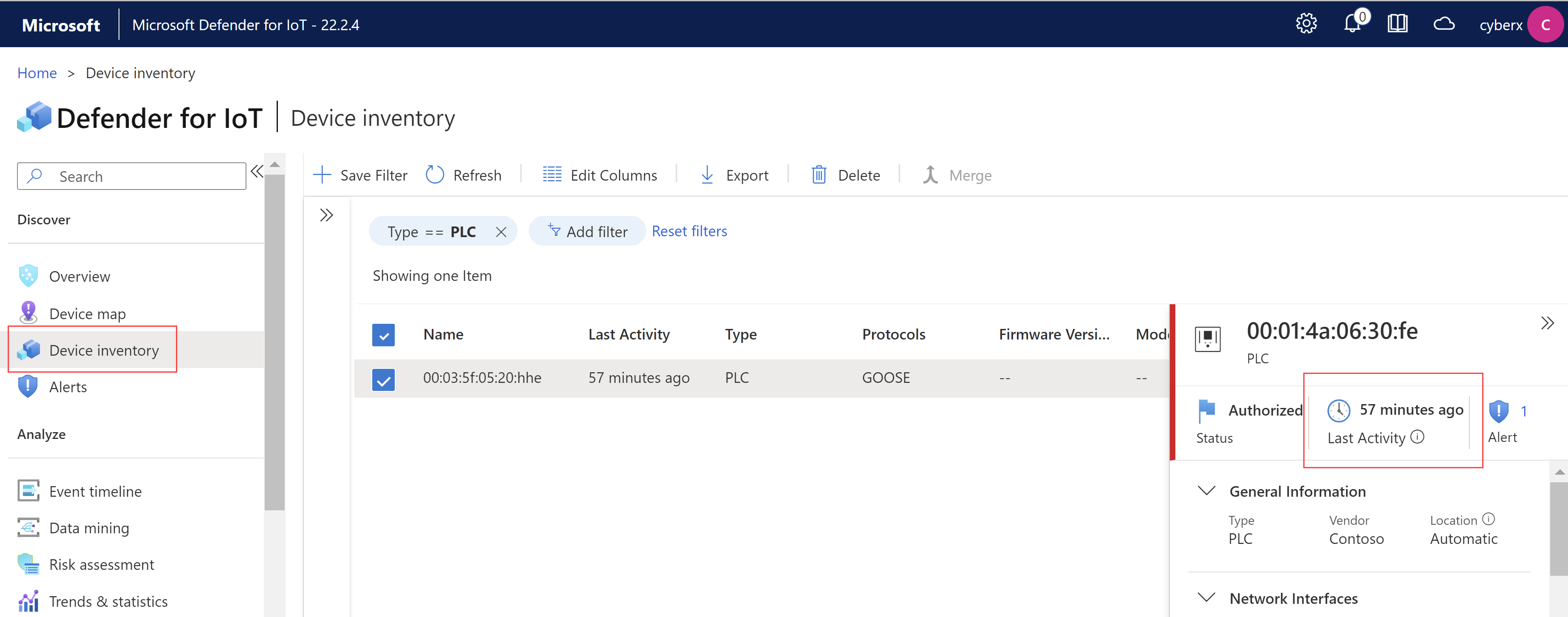
For more information, see Manage your OT device inventory from a sensor console.
Enhancements for the ServiceNow integration API
OT sensor version 22.2.4 provides enhancements for the devicecves API, which gets details about the CVEs found for a given device.
Now you can add any of the following parameters to your query to fine tune your results:
- “sensorId” - Shows results from a specific sensor, as defined by the given sensor ID.
- “score” - Determines a minimum CVE score to be retrieved. All results have a CVE score equal to or higher than the given value. Default = 0.
- “deviceIds” - A comma-separated list of device IDs from which you want to show results. For example: 1232,34,2,456
For more information, see Integration API reference for on-premises management consoles (Public preview).
OT appliance hardware profile updates
We've refreshed the naming conventions for our OT appliance hardware profiles for greater transparency and clarity.
The new names reflect both the type of profile, including Corporate, Enterprise, and Production line, and also the related disk storage size.
Use the following table to understand the mapping between legacy hardware profile names and the current names used in the updated software installation:
| Legacy name | New name | Description |
|---|---|---|
| Corporate | C5600 | A Corporate environment, with: 16 Cores 32-GB RAM 5.6-TB disk storage |
| Enterprise | E1800 | An Enterprise environment, with: Eight Cores 32-GB RAM 1.8-TB disk storage |
| SMB | L500 | A Production line environment, with: Four Cores 8-GB RAM 500-GB disk storage |
| Office | L100 | A Production line environment, with: Four Cores 8-GB RAM 100-GB disk storage |
| Rugged | L64 | A Production line environment, with: Four Cores 8-GB RAM 64-GB disk storage |
We also now support new enterprise hardware profiles, for sensors supporting both 500 GB and 1-TB disk sizes.
For more information, see Which appliances do I need?
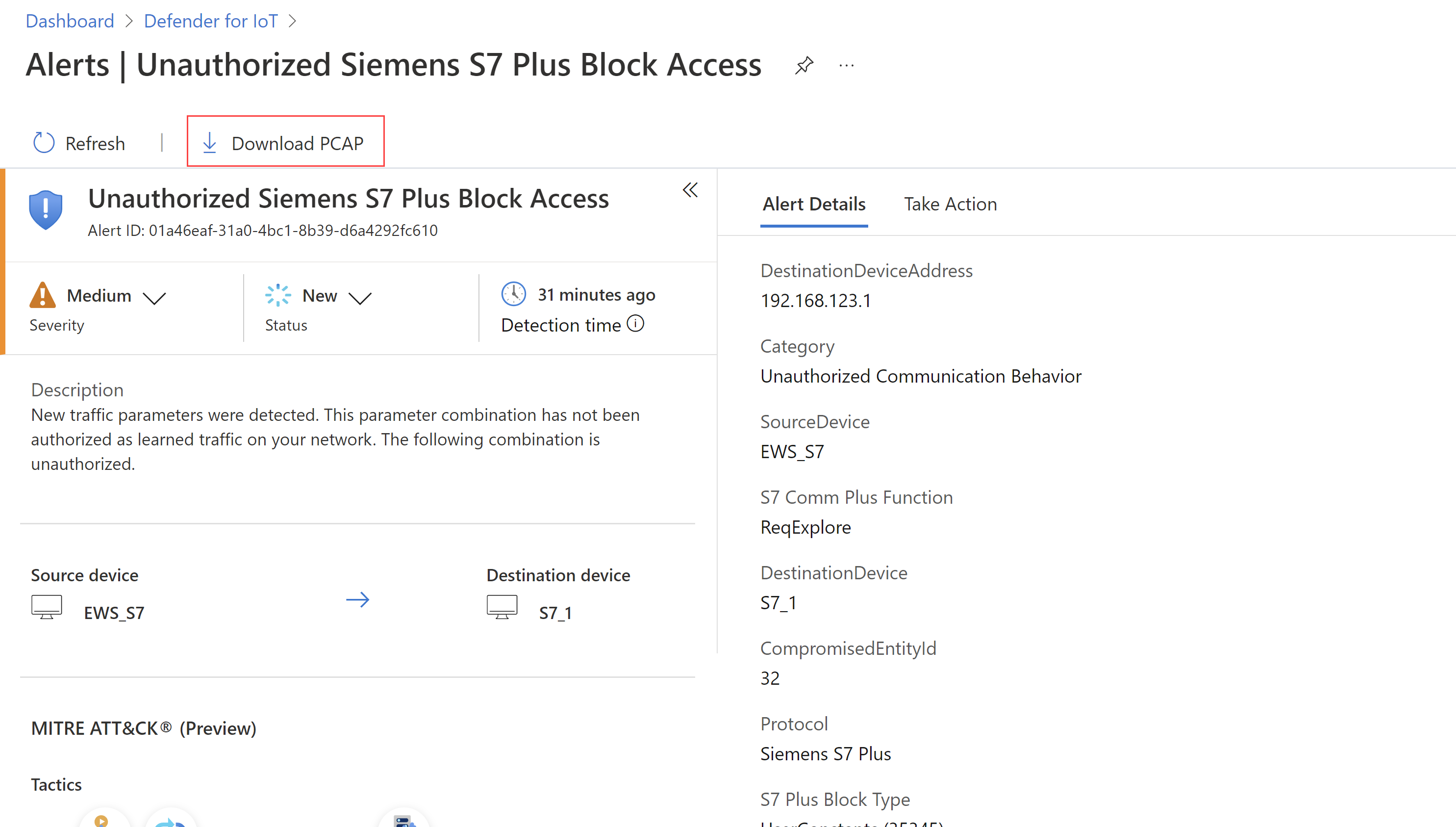
PCAP access from the Azure portal (Public preview)
Now you can access the raw traffic files, known as packet capture files or PCAP files, directly from the Azure portal. This feature supports SOC or OT security engineers who want to investigate alerts from Defender for IoT or Microsoft Sentinel, without having to access each sensor separately.
PCAP files are downloaded to your Azure storage.
For more information, see View and manage alerts from the Azure portal.
Bi-directional alert synch between sensors and the Azure portal (Public preview)
For sensors updated to version 22.2.1, alert statuses and learn statuses are now fully synchronized between the sensor console and the Azure portal. For example, this means that you can close an alert on the Azure portal or the sensor console, and the alert status is updated in both locations.
Learn an alert from either the Azure portal or the sensor console to ensure that it's not triggered again the next time the same network traffic is detected.
The sensor console is also synchronized with an on-premises management console, so that alert statuses and learn statuses remain up-to-date across your management interfaces.
For more information, see:
- View and manage alerts from the Azure portal
- View and manage alerts on your sensor
- Work with alerts on the on-premises management console
Sensor connections restored after certificate rotation
Starting in version 22.2.3, after rotating your certificates, your sensor connections are automatically restored to your on-premises management console, and you don't need to reconnect them manually.
For more information, see Create SSL/TLS certificates for OT appliances and Manage SSL/TLS certificates.
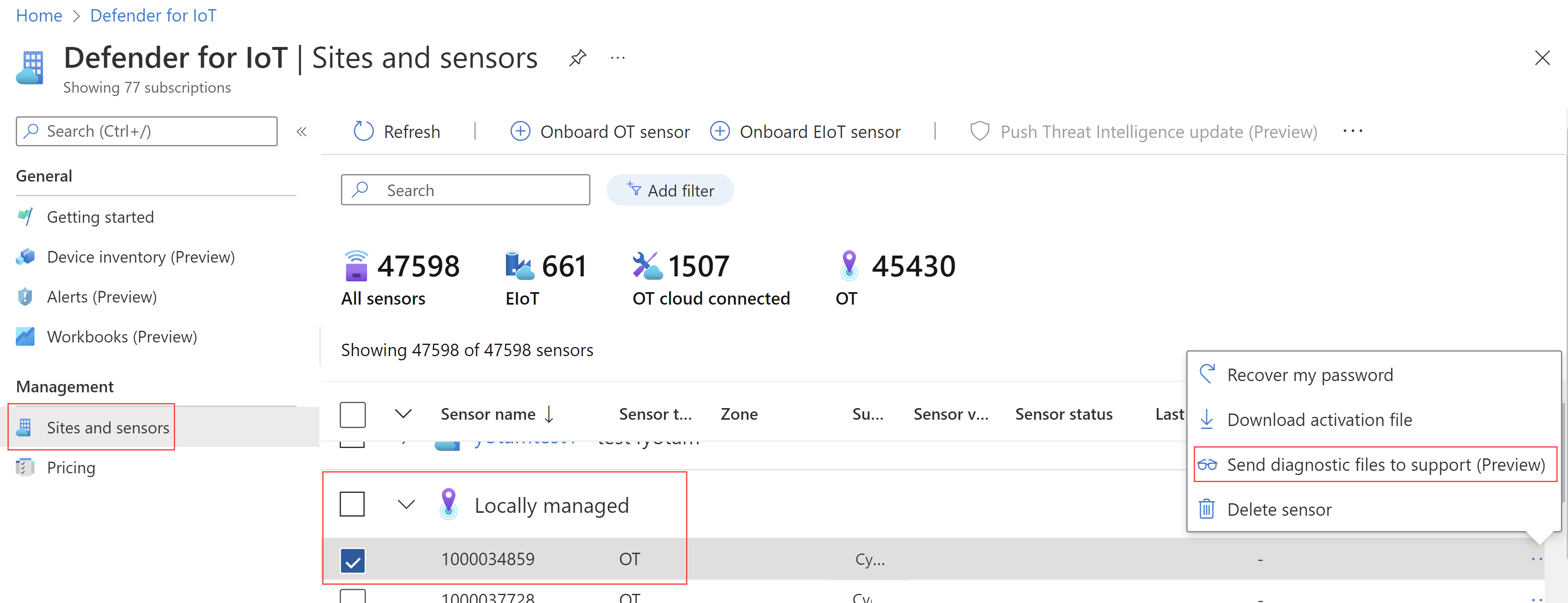
Support diagnostic log enhancements (Public preview)
Starting in sensor version 22.1.1, you've been able to download a diagnostic log from the sensor console to send to support when you open a ticket.
Now, for locally managed sensors, you can upload that diagnostic log directly on the Azure portal.
Tip
For cloud-connected sensors, starting from sensor version 22.1.3, the diagnostic log is automatically available to support when you open the ticket.
For more information, see:
Sensor names shown in browser tabs
Starting in sensor version 22.2.3, your sensor's name is displayed in the browser tab, making it easier for you to identify the sensors you're working with.
For example:
For more information, see Manage individual sensors.
Microsoft Sentinel incident synch with Defender for IoT alerts
The IoT OT Threat Monitoring with Defender for IoT solution now ensures that alerts in Defender for IoT are updated with any related incident Status changes from Microsoft Sentinel.
This synchronization overrides any status defined in Defender for IoT, in the Azure portal or the sensor console, so that the alert statuses match that of the related incident.
Update your IoT OT Threat Monitoring with Defender for IoT solution to use the latest synchronization support, including the new AD4IoT-AutoAlertStatusSync playbook. After updating the solution, make sure that you also take the required steps to ensure that the new playbook works as expected.
For more information, see:
- Tutorial: Integrate Defender for IoT and Sentinel
- View and manage alerts on the Defender for IoT portal (Preview)
- View alerts on your sensor
June 2022
Sensor software version 22.1.6: Minor version with maintenance updates for internal sensor components
Sensor software version 22.1.5: Minor version to improve TI installation packages and software updates
We've also recently optimized and enhanced our documentation as follows:
- Updated appliance catalog for OT environments
- Documentation reorganization for end-user organizations
Updated appliance catalog for OT environments
We've refreshed and revamped the catalog of supported appliances for monitoring OT environments. These appliances support flexible deployment options for environments of all sizes and can be used to host both the OT monitoring sensor and on-premises management consoles.
Use the new pages as follows:
Understand which hardware model best fits your organization's needs. For more information, see Which appliances do I need?
Learn about the preconfigured hardware appliances that are available to purchase, or system requirements for virtual machines. For more information, see Preconfigured physical appliances for OT monitoring and OT monitoring with virtual appliances.
For more information about each appliance type, use the linked reference page, or browse through our new Reference > OT monitoring appliances section.
Reference articles for each appliance type, including virtual appliances, include specific steps to configure the appliance for OT monitoring with Defender for IoT. Generic software installation and troubleshooting procedures are still documented in Defender for IoT software installation.
Documentation reorganization for end-user organizations
We recently reorganized our Defender for IoT documentation for end-user organizations, highlighting a clearer path for onboarding and getting started.
Check out our new structure to follow through viewing devices and assets, managing alerts, vulnerabilities and threats, integrating with other services, and deploying and maintaining your Defender for IoT system.
New and updated articles include:
- Welcome to Microsoft Defender for IoT for organizations
- Microsoft Defender for IoT architecture
- Quickstart: Get started with Defender for IoT
- Tutorial: Microsoft Defender for IoT trial setup
- Tutorial: Get started with Enterprise IoT
Note
To send feedback on docs via GitHub, scroll to the bottom of the page and select the Feedback option for This page. We'd be glad to hear from you!
April 2022
Extended device property data in the Device inventory
Sensor software version: 22.1.4
Starting for sensors updated to version 22.1.4, the Device inventory page on the Azure portal shows extended data for the following fields:
- Description
- Tags
- Protocols
- Scanner
- Last Activity
For more information, see Manage your device inventory from the Azure portal.
March 2022
Sensor version: 22.1.3
- Use Azure Monitor workbooks with Microsoft Defender for IoT
- IoT OT Threat Monitoring with Defender for IoT solution GA
- Edit and delete devices from the Azure portal
- Key state alert updates
- Sign out of a CLI session
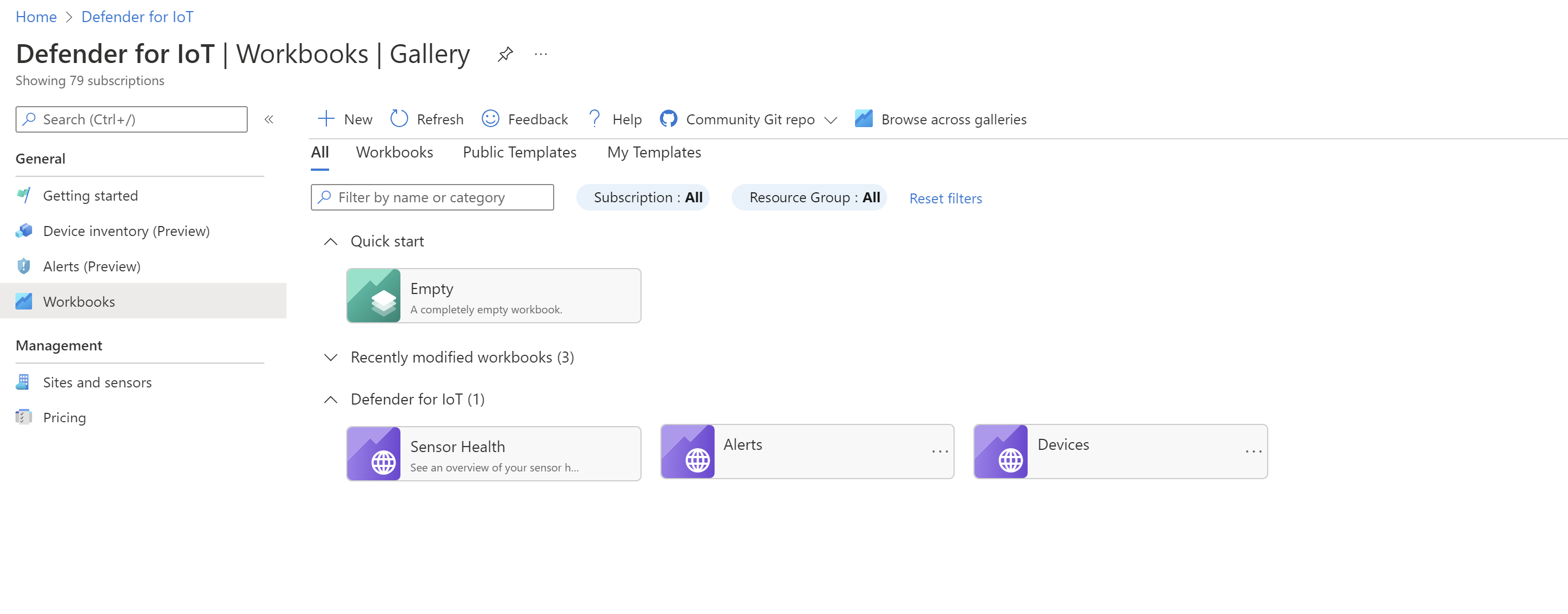
Use Azure Monitor workbooks with Microsoft Defender for IoT (Public preview)
Azure Monitor workbooks provide graphs and dashboards that visually reflect your data, and are now available directly in Microsoft Defender for IoT with data from Azure Resource Graph.
In the Azure portal, use the new Defender for IoT Workbooks page to view workbooks created by Microsoft and provided out-of-the-box, or create custom workbooks of your own.
For more information, see Use Azure Monitor workbooks in Microsoft Defender for IoT.
IoT OT Threat Monitoring with Defender for IoT solution GA
The IoT OT Threat Monitoring with Defender for IoT solution in Microsoft Sentinel is now GA. In the Azure portal, use this solution to help secure your entire OT environment, whether you need to protect existing OT devices or build security into new OT innovations.
For more information, see OT threat monitoring in enterprise SOCs and Tutorial: Integrate Defender for IoT and Sentinel.
Edit and delete devices from the Azure portal (Public preview)
The Device inventory page in the Azure portal now supports the ability to edit device details, such as security, classification, location, and more:
For more information, see Edit device details.
You can only delete devices from Defender for IoT if they've been inactive for more than 14 days. For more information, see Delete a device.
Key state alert updates (Public preview)
Defender for IoT now supports the Rockwell protocol for PLC operating mode detections.
For the Rockwell protocol, the Device inventory pages in both the Azure portal and the sensor console now indicate the PLC operating mode key and run state, and whether the device is currently in a secure mode.
If the device's PLC operating mode is ever switched to an unsecured mode, such as Program or Remote, a PLC Operating Mode Changed alert is generated.
For more information, see Manage your IoT devices with the device inventory for organizations.
Sign out of a CLI session
Starting in this version, CLI users are automatically signed out of their session after 300 inactive seconds. To sign out manually, use the new logout CLI command.
For more information, see Work with Defender for IoT CLI commands.
February 2022
Sensor software version: 22.1.1
- New sensor installation wizard
- Sensor redesign and unified Microsoft product experience
- Enhanced sensor Overview page
- New support diagnostics log
- Alert updates
- Custom alert updates
- CLI command updates
- Update to version 22.1.x
- New connectivity model and firewall requirements
- Protocol improvements
- Modified, replaced, or removed options and configurations
New sensor installation wizard
Previously, you needed to use separate dialogs to upload a sensor activation file, verify your sensor network configuration, and configure your SSL/TLS certificates.
Now, when installing a new sensor or a new sensor version, our installation wizard provides a streamlined interface to do all these tasks from a single location.
For more information, see Defender for IoT installation.
Sensor redesign and unified Microsoft product experience
The Defender for IoT sensor console has been redesigned to create a unified Microsoft Azure experience and enhance and simplify workflows.
These features are now Generally Available (GA). Updates include the general look and feel, drill-down panes, search and action options, and more. For example:
Simplified workflows include:
The Device inventory page now includes detailed device pages. Select a device in the table and then select View full details on the right.
Properties updated from the sensor's inventory are now automatically updated in the cloud device inventory.
The device details pages, accessed either from the Device map or Device inventory pages, is shown as read only. To modify device properties, select Edit properties on the bottom-left.
The Data mining page now includes reporting functionality. While the Reports page was removed, users with read-only access can view updates on the Data mining page without the ability to modify reports or settings.
For admin users creating new reports, you can now toggle on a Send to CM option to send the report to a central management console as well. For more information, see Create a report
The System settings area has been reorganized in to sections for Basic settings, settings for Network monitoring, Sensor management, Integrations, and Import settings.
The sensor online help now links to key articles in the Microsoft Defender for IoT documentation.
Defender for IoT maps now include:
A new Map View is now shown for alerts and on the device details pages, showing where in your environment the alert or device is found.
Right-click a device on the map to view contextual information about the device, including related alerts, event timeline data, and connected devices.
Select Disable Display IT Networks Groups to prevent the ability to collapse IT networks in the map. This option is turned on by default.
The Simplified Map View option has been removed.
We've also implemented global readiness and accessibility features to comply with Microsoft standards. In the on-premises sensor console, these updates include both high contrast and regular screen display themes and localization for over 15 languages.
For example:
Access global readiness and accessibility options from the Settings icon at the top-right corner of your screen:
Enhanced sensor Overview page
The Defender for IoT sensor portal's Dashboard page has been renamed as Overview, and now includes data that better highlights system deployment details, critical network monitoring health, top alerts, and important trends and statistics.
The Overview page also now serves as a black box to view your overall sensor status in case your outbound connections, such as to the Azure portal, go down.
Create more dashboards using the Trends & Statistics page, located under the Analyze menu on the left.
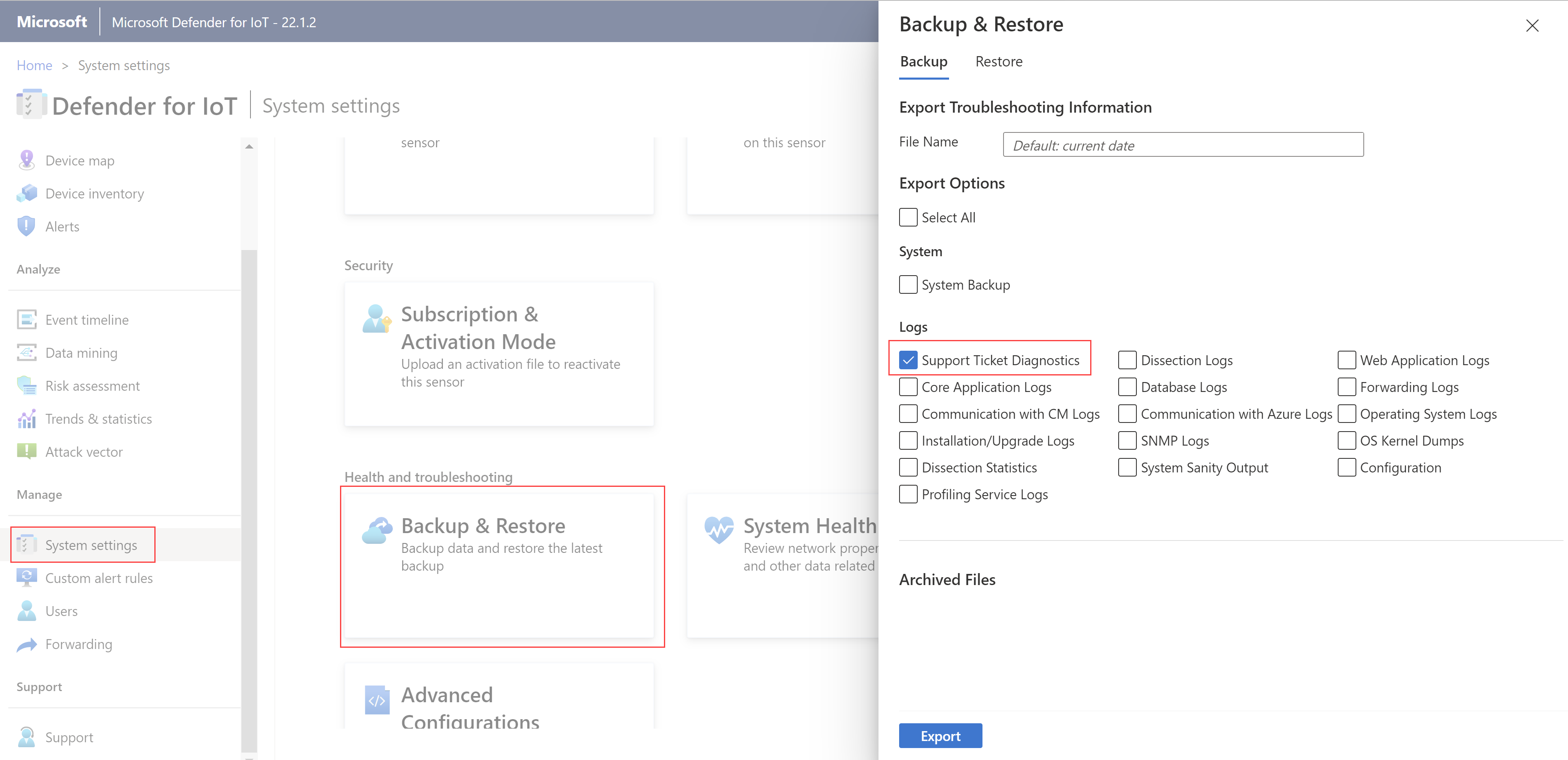
New support diagnostics log
Now you can get a summary of the log and system information that gets added to your support tickets. In the Backup and Restore dialog, select Support Ticket Diagnostics.
For more information, see Download a diagnostics log for support
Alert updates
In the Azure portal:
Alerts are now available in Defender for IoT in the Azure portal. Work with alerts to enhance the security and operation of your IoT/OT network.
The new Alerts page is currently in Public Preview, and provides:
- An aggregated, real-time view of threats detected by network sensors.
- Remediation steps for devices and network processes.
- Streaming alerts to Microsoft Sentinel and empower your SOC team.
- Alert storage for 90 days from the time they're first detected.
- Tools to investigate source and destination activity, alert severity and status, MITRE ATT&CK information, and contextual information about the alert.
For example:
On the sensor console:
On the sensor console, the Alerts page now shows details for alerts detected by sensors that are configured with a cloud-connection to Defender for IoT on Azure. Users working with alerts in both Azure and on-premises should understand how alerts are managed between the Azure portal and the on-premises components.
Other alert updates include:
Access contextual data for each alert, such as events that occurred around the same time, or a map of connected devices. Maps of connected devices are available for sensor console alerts only.
Alert statuses are updated, and, for example, now include a Closed status instead of Acknowledged.
Alert storage for 90 days from the time that they're first detected.
The Backup Activity with Antivirus Signatures Alert. This new alert warning is triggered for traffic detected between a source device and destination backup server, which is often legitimate backup activity. Critical or major malware alerts are no longer triggered for such activity.
During upgrades, sensor console alerts that are currently archived are deleted. Pinned alerts are no longer supported, so pins are removed for sensor console alerts as relevant.
For more information, see View alerts on your sensor.
Custom alert updates
The sensor console's Custom alert rules page now provides:
Hit count information in the Custom alert rules table, with at-a-glance details about the number of alerts triggered in the last week for each rule you've created.
The ability to schedule custom alert rules to run outside of regular working hours.
The ability to alert on any field that can be extracted from a protocol using the DPI engine.
Complete protocol support when creating custom rules, and support for an extensive range of related protocol variables.
For more information, see Create custom alert rules on an OT sensor.
CLI command updates
The Defender for IoT sensor software installation is now containerized. With the now-containerized sensor, you can use the cyberx_host user to investigate issues with other containers or the operating system, or to send files via FTP.
This cyberx_host user is available by default and connects to the host machine. If you need to, recover the password for the cyberx_host user from the Sites and sensors page in Defender for IoT.
As part of the containerized sensor, the following CLI commands have been modified:
| Legacy name | Replacement |
|---|---|
cyberx-xsense-reconfigure-interfaces |
sudo dpkg-reconfigure iot-sensor |
cyberx-xsense-reload-interfaces |
sudo dpkg-reconfigure iot-sensor |
cyberx-xsense-reconfigure-hostname |
sudo dpkg-reconfigure iot-sensor |
cyberx-xsense-system-remount-disks |
sudo dpkg-reconfigure iot-sensor |
The sudo cyberx-xsense-limit-interface-I eth0 -l value CLI command was removed. This command was used to limit the interface bandwidth that the sensor uses for day-to-day procedures, and is no longer supported.
For more information, see Defender for IoT installation, Work with Defender for IoT CLI commands, and CLI command reference from OT network sensors.
Update to version 22.1.x
To use all of Defender for IoT's latest features, make sure to update your sensor software versions to 22.1.x.
If you're on a legacy version, you might need to run a series of updates in order to get to the latest version. You'll also need to update your firewall rules and reactivate your sensor with a new activation file.
After you've upgraded to version 22.1.x, the new upgrade log can be found at the following path, accessed via SSH and the cyberx_host user: /opt/sensor/logs/legacy-upgrade.log.
For more information, see Update OT system software.
Note
Upgrading to version 22.1.x is a large update, and you should expect the update process to require more time than previous updates.
New connectivity model and firewall requirements
Defender for IoT version 22.1.x supports a new set of sensor connection methods that provide simplified deployment, improved security, scalability, and flexible connectivity.
In addition to migration steps, this new connectivity model requires that you open a new firewall rule. For more information, see:
- New firewall requirements: Sensor access to Azure portal.
- Architecture: Sensor connection methods
- Connection procedures: Connect your sensors to Microsoft Defender for IoT
Protocol improvements
This version of Defender for IoT provides improved support for:
- Profinet DCP
- Honeywell
- Windows endpoint detection
For more information, see Microsoft Defender for IoT - supported IoT, OT, ICS, and SCADA protocols.
Modified, replaced, or removed options and configurations
The following Defender for IoT options and configurations have been moved, removed, and/or replaced:
Reports previously found on the Reports page are now shown on the Data Mining page instead. You can also continue to view data mining information directly from the on-premises management console.
Changing a locally managed sensor name is now supported only by onboarding the sensor to the Azure portal again with the new name. Sensor names can no longer be changed directly from the sensor. For more information, see Upload a new activation file.