Events
17 Mar, 21 - 21 Mar, 10
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Azure DevOps Services
Learn how to add users to your organization and manage user access through direct assignment. For an overview of adding users and related concepts, see About organization management in Azure DevOps. Users can include human users, service accounts, and service principals.
The following types of users can join your Azure DevOps Services organization for free:
Need more users with Basic features?
Note
For information about inviting external users, see Add external user.
| Category | Requirements |
|---|---|
| Permissions | Member of the Project Collection Administrators group. Organization owners are automatically members of this group. |
| Organization | An organization. |
For an overview of the methods supported for adding users to an organization, see Add and manage user access.
Administrators can efficiently manage user access by adding users to an organization, granting them access to the appropriate tooling extensions and service access levels, and assigning them to relevant groups—all from a single view. This streamlined process ensures that new users have the necessary permissions and resources to start contributing immediately.
Note
If you have a Microsoft Entra ID-backed organization and need to add users who are external to Microsoft Entra ID, first add external users. On the Tell us about this user page, under Type of user, choose User with an existing Microsoft account. After completing those steps, follow these instructions to add the Microsoft Entra ID user to Azure DevOps.
You can add up to 50 users in a single transaction. When you add users, each user receives a notification email with a link to the organization page, allowing them to easily access and start using the organization's resources.
To give other users access to your organization, do the following steps:
Sign in to your organization (https://dev.azure.com/{yourorganization}).
Select ![]() Organization settings.
Organization settings.
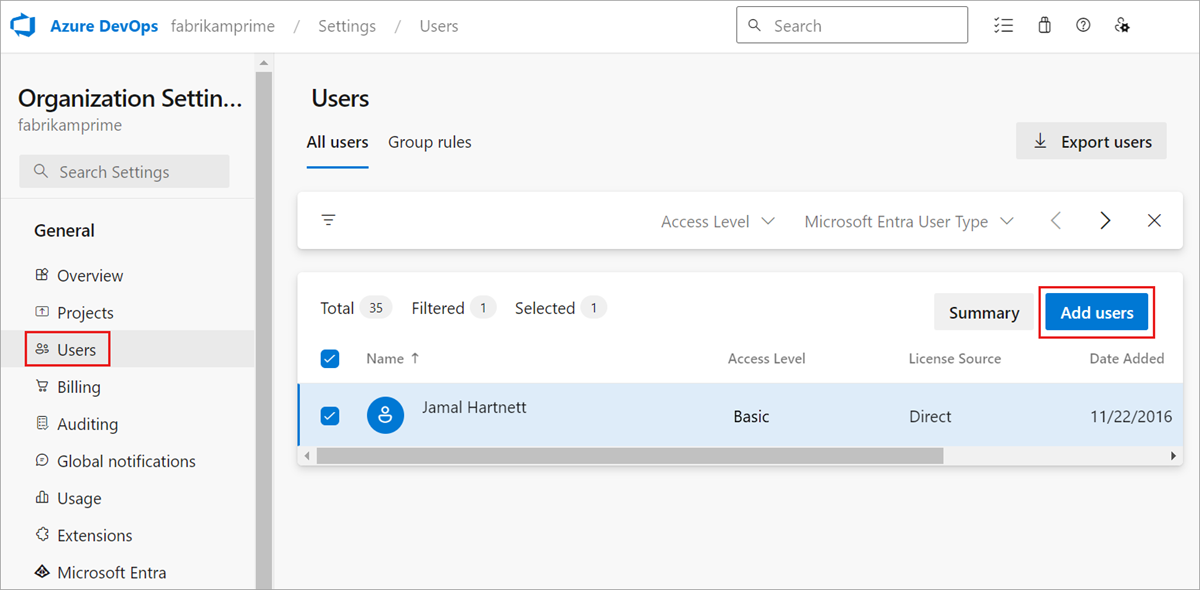
Select Users > Add users.
Enter the following information.
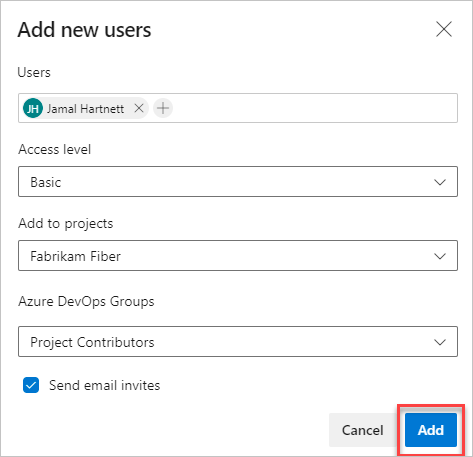
;. Accepted email addresses appear in red. For more information about GitHub authentication, see Connect to GitHub/FAQs. To add a service principal, enter the display name of the application or managed identity.
Note
Add email addresses for personal Microsoft accounts and IDs for GitHub accounts unless you plan to use Microsoft Entra ID to authenticate users and control organization access. If a user doesn't have a Microsoft or GitHub account, ask them to sign up for a Microsoft account or a GitHub account.
Select Add to complete your invitation.
For more information about user access, read about access levels.
Note
You can add people to projects instead of to your organization. Users are automatically assigned Basic features if your organization has seats available, or Stakeholder features if not. Learn how to add members to projects.
When a user no longer needs access to your organization, delete them from your organization.
From your web browser, you can view and edit certain user information. Using the Azure DevOps CLI, you can see details about a specific user and update their access level.
The Users view displays key information for each user in a table. In this view, you can:
Sign in to your organization (https://dev.azure.com/{yourorganization}).
Select ![]() Organization settings.
Organization settings.

Select Users.
Select a user or group of users. Then, select Actions ... at the end of the Name column to open the context menu.
In the context menu, choose one of the following options:
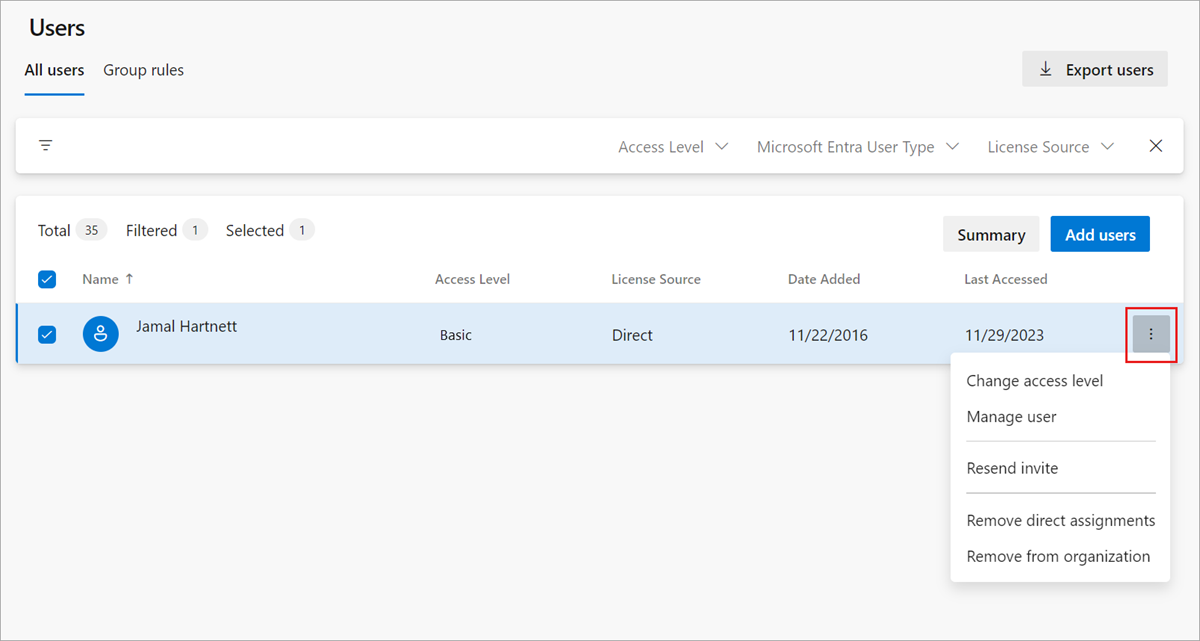
To restrict certain users' access to organizational information, enable the Limit user visibility and collaboration to specific projects preview feature and add the users to the Project-Scoped Users group. Once added, users in that group can't access projects that they aren't explicitly added to.
Note
Users and groups added to the Project-Scoped Users group have limited access to project and organization information. They also have restricted access to specific identities through the people picker. For more information, see Limit user visibility for projects, and more.
To add users to the new Project-Scoped Users group, do the following steps:
Sign in to your organization (https://dev.azure.com/{yourorganization}).
Turn on the Limit user visibility and collaboration to specific projects preview feature for the organization. For more information, see Manage preview features.
Tip
The Project-Scoped Users group only appears under Permissions > Groups once Limit user visibility and collaboration to specific projects preview feature gets enabled.
Add users or groups to your project by following the steps in Add users to a project or team. When you add users to a team, they automatically get added to both the project and the team group.
Select ![]() Organization settings.
Organization settings.

Select Security > Permissions > Project-Scoped Users.
Choose the Members tab.
Add all users and groups that you want to scope to the project you added them to.
For more information, see Add or remove users or groups, manage security groups.
Warning
Consider the following limitations when using this preview feature:
azure devops CLI commands, project members can access the restricted data.A:
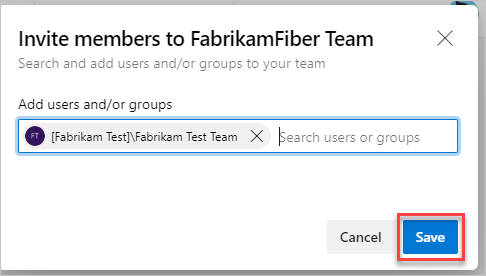
After you add members to your project, each member receives an invitation email with a link to your organization. They can use this link to sign in and access your project. First-time members might get asked for more details when they sign in to personalize their experience.
A:
For Organizations connected to Microsoft Entra ID: If you're inviting users from outside your Microsoft Entra ID, they must use their email. Removing users from the organization removes both their access and their license. However, any artifacts assigned to them remain unchanged. You can always invite users back into the organization if they exist in the Microsoft Entra tenant. After they're removed from Microsoft Entra ID, you can't assign any new artifacts (work items, pull requests, and so on) to them. The history of artifacts already assigned to the users is preserved.
For Organizations with Microsoft accounts: You can send a link to the project page, included in the invitation email, to new team members. Removing users from the organization removes both their access and their licenses. You can no longer assign any new artifacts (work items, pull requests, and so on) to these users. However, any artifacts previously assigned to them remain unchanged.
A: See Q: Why can't I add any more members to my project?.
A: Access levels determine a user's access to specific web portal features based on their subscription. Permissions control a user's ability to perform specific operations, which get governed by security group membership or specific Access Control Level (ACL) assignments made to a user or group.
Events
17 Mar, 21 - 21 Mar, 10
Join the meetup series to build scalable AI solutions based on real-world use cases with fellow developers and experts.
Register nowTraining
Module
Manage access for external users. - Training
Work with external users in Teams and the access controls from different places, including Microsoft Entra ID, Microsoft 365, Teams, and SharePoint admin centers.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.