Surface custom event details in alerts in Microsoft Sentinel
Scheduled query analytics rules analyze events from data sources connected to Microsoft Sentinel, and produce alerts when the contents of these events are significant from a security perspective. These alerts are further analyzed, grouped, and filtered by Microsoft Sentinel's various engines and distilled into incidents that warrant a SOC analyst's attention. However, when the analyst views the incident, only the properties of the component alerts themselves are immediately visible. Getting to the actual content - the information contained in the events - requires doing some digging.
Using the custom details feature in the analytics rule wizard, you can surface event data in the alerts that are constructed from those events, making the event data part of the alert properties. In effect, this gives you immediate event content visibility in your incidents, enabling you to triage, investigate, draw conclusions, and respond with much greater speed and efficiency.
The procedure detailed below is part of the analytics rule creation wizard. It's treated here independently to address the scenario of adding or changing custom details in an existing analytics rule.
Important
Microsoft Sentinel is generally available within Microsoft's unified security operations platform in the Microsoft Defender portal. For preview, Microsoft Sentinel is available in the Defender portal without Microsoft Defender XDR or an E5 license. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
How to surface custom event details
Enter the Analytics page in the portal through which you access Microsoft Sentinel:
From the Configuration section of the Microsoft Sentinel navigation menu, select Analytics.
Select a scheduled query rule and click Edit. Or create a new rule by clicking Create > Scheduled query rule at the top of the screen.
Click the Set rule logic tab.
In the Alert enrichment section, expand Custom details.
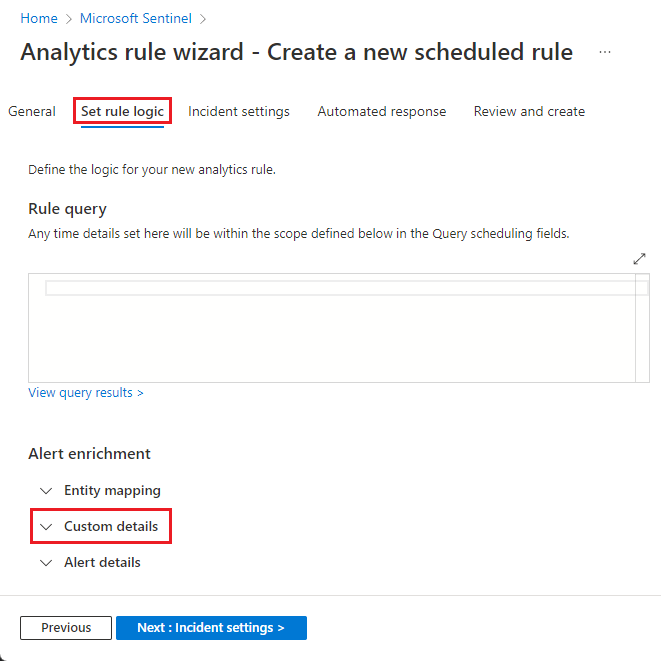
In the now-expanded Custom details section, add key-value pairs corresponding to the details you want to surface:
In the Key field, enter a name of your choosing that will appear as the field name in alerts.
In the Value field, choose the event parameter you wish to surface in the alerts from the drop-down list. This list will be populated by values corresponding to the fields in the tables that are the subject of the rule query.
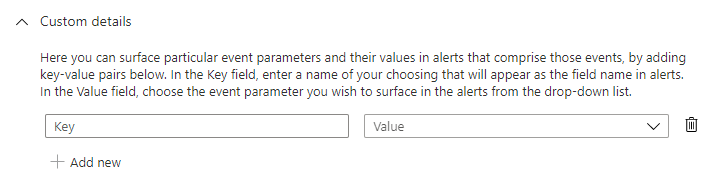
Click Add new to surface more details, repeating the last steps to define key-value pairs.
If you change your mind, or if you made a mistake, you can remove a custom detail by clicking the trash can icon next to the Value drop-down list for that detail.
When you have finished defining custom details, click the Review and create tab. Once the rule validation is successful, click Save.
Note
Service limits
You can define up to 20 custom details in a single analytics rule. Each custom detail can contain up to 50 values.
The combined size limit for all custom details and their values in a single alert is 2 KB. Values in excess of this limit are dropped.
Next steps
In this document, you learned how to surface custom details in alerts using Microsoft Sentinel analytics rules. To learn more about Microsoft Sentinel, see the following articles:
- Explore the other ways to enrich your alerts:
- Get the complete picture on scheduled query analytics rules.
- Learn more about entities in Microsoft Sentinel.