RADIUS - Configure NPS for vendor-specific attributes - P2S user groups
The following section describes how to configure Windows Server Network Policy Server (NPS) to authenticate users to respond to Access-Request messages with the Vendor Specific Attribute (VSA) used for user group support in Virtual WAN point-to-site-VPN. The following steps assume that your Network Policy Server is already registered to Active Directory. The steps might vary depending on the vendor/version of your NPS server.
The following steps describe setting up single Network Policy on the NPS server. The NPS server replies with the specified VSA for all users who match this policy, and the value of this VSA can be used on your point-to-site VPN gateway in Virtual WAN.
Configure
Open the Network Policy Server management console, and right click Network Policies -> New to create a new Network Policy.
In the wizard, select Access granted to ensure your RADIUS server can send Access-Accept messages after authenticating users. Then, click Next.
Name the policy and select Remote Access Server (VPN-Dial up) as the network access server type. Then, click Next.
On the Specify Conditions page, click Add to select a condition. Then, select User Groups as the condition and click Add. You can also use other Network Policy conditions that are supported by your RADIUS server vendor.
On the User Groups page, click Add Groups and select the Active Directory groups that will use this policy. Then, click OK and OK again. You'll see the groups you've added in the User Groups window. Click OK to return to the Specify Conditions page and click Next.
On the Specify Access Permission page, select Access granted to ensure your RADIUS server can send Access-Accept messages after authenticating users. Then, click Next.
For Configuration Authentication Methods, make any necessary changes, then click Next.
For Configure Constraints select any necessary settings. Then, click Next.
On the Configure Settings page, for RADIUS Attributes, highlight Vendor Specific and click Add.
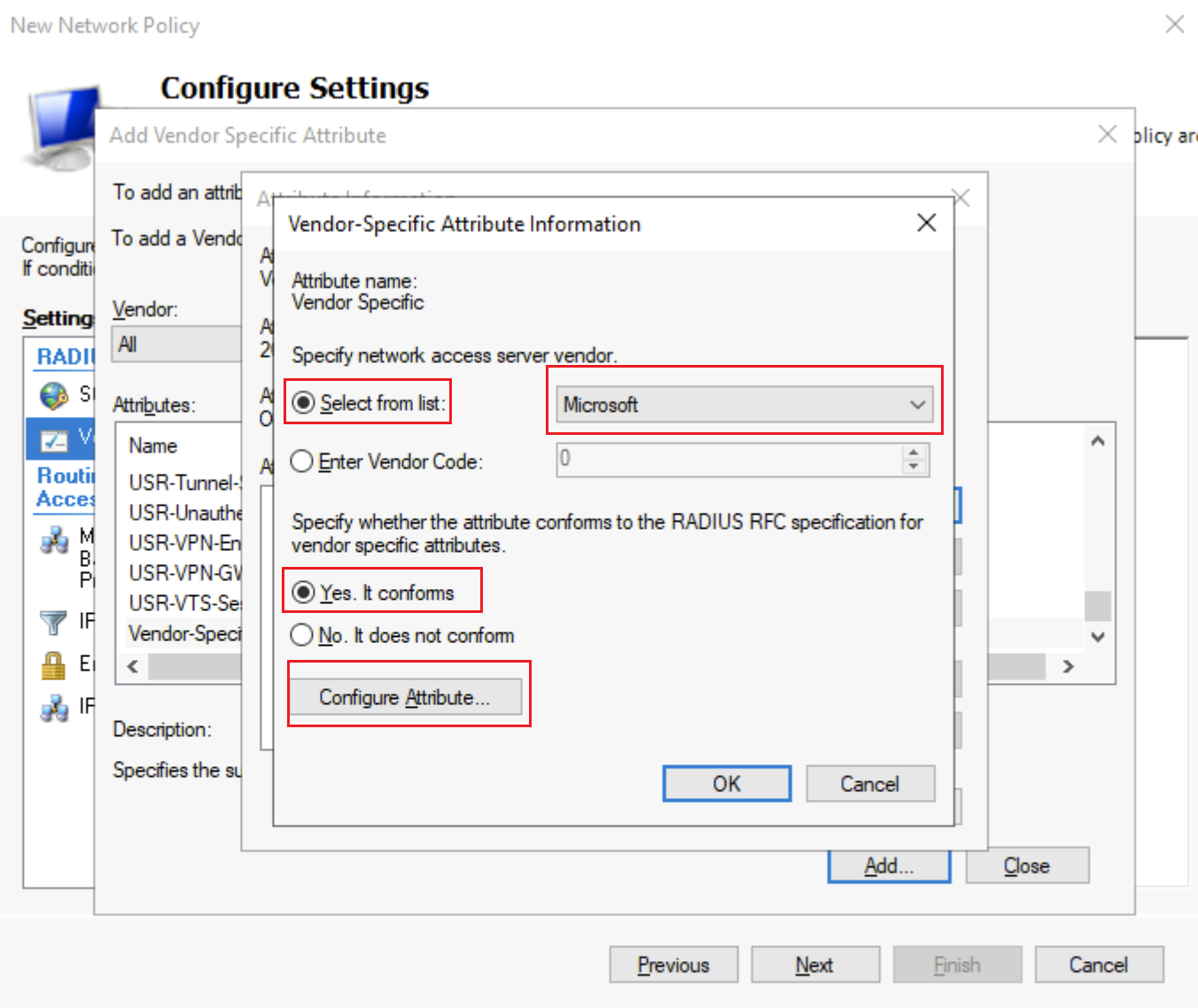
On the Add Vendor Specific Attribute page, scroll to select Vendor-Specific.
Click Add to open the Attribute Information page. Then, click Add to open the Vendor-Specific Attribute Information page. Select Select from list and select Microsoft. Select Yes. It conforms. Then, click Configure Attribute.
On the Configure VSA (RFC Compliant) page, select the following values:
- Vendor-assigned attribute number: 65
- Attribute format: Hexadecimal
- Attribute value: Set this to the VSA value you have configured on your VPN server configuration, such as 6a1bd08. The VSA value should begin with 6ad1bd.
Click OK and OK again to close the windows. On the Attribute Information page, you'll see the Vendor and Value listed that you just input. Click OK to close the window. Then, click Close to return to the Configure Settings page.
The Configure Settings now looks similar to the following screenshot:
Click Next and then Finish. You can create multiple network policies on your RADIUS server to send different Access-Accept messages to the Virtual WAN point-to-site VPN gateway based on Active Directory group membership or any other mechanism you would like to support.
Next steps
For more information about user groups, see About user groups and IP address pools for P2S User VPNs.
To configure user groups, see Configure user groups and IP address pools for P2S User VPNs.